
E-mail scammers typically combine social engineering with technical skills to bypass spam filters and persuade the recipient to reply. But there is a specific class of attacks that is technically stuck somewhere in the late 90s/early 00s, in the era of CRT monitors and sluggish internet: we are talking about text-based fraud. Attackers of this kind do not carefully imitate the appearance of e-mails from major companies, do not redirect the victim to a fake site, do not obfuscate links and do not even use them. Their main tool and method of persuasion is old-fashioned text. And it works surprisingly often.
Types of text-based fraud
In terms of topics and techniques, text-based fraud can be divided into several types:
- Dating scams
- 419 scams
- Blackmailing and extortion
- Vishing
Let’s take a look at these types of scams and see why they work.
Dating scams
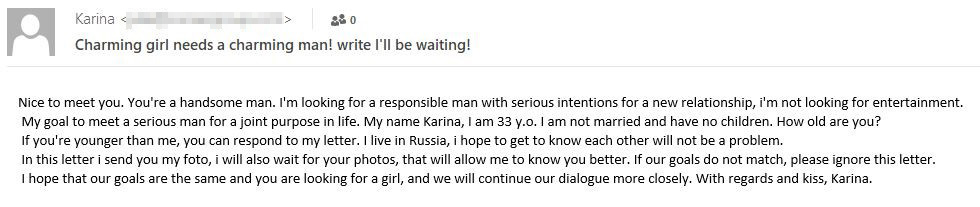
This category includes messages seemingly from attractive women (more rarely men) looking for a “serious relationship.” For extra plausibility, scammers add biographical details and/or photographs of their bait, including immodest ones. The latter are usually downloaded from open sources.
Example of a dating scam e-mail
Attackers can also create fake profiles in social networks and instant messengers to make the scheme more persuasive. If the potential victim responds, they are added as friends and start to receive individual treatment. The interaction can last from several days to several months, and includes not only messages, but also phone and even video calls.
Fraudsters can monetize their lonely-heart character in several ways. For instance, early on in the communication, they might ask for small amounts of money or gifts as a sign of commitment. Another variant is, after a long virtual communication, to ask for a large sum to visit the victim, have an urgent surgery, etc. One more scheme, quite common lately, is when the “partner” promises to send the victim an expensive gift or cash by courier from abroad. After some time, the “courier” gets in touch and asks the victim to pay for shipping, customs duties, etc.
Note that scammers get acquainted with victims not only by e-mail. These schemes are utilized on dating sites, social networks and instant messengers. Moreover, the latter two are often the main channel for communicating with the victim, regardless of how contact was initially made. But mass mailings are still more convenient to send out by e-mail, since accounts in social networks, messengers, etc., are quickly blocked due to spam.
Statistics
Dating scams are the least common type of message-based fraud. From March to June 2022, we found 49,536 messages from people “looking for a relationship,” dropping to 1998 e-mails for the whole June. This may be because scammers actively use other communication channels to get to know their victims and establish a trusting relationship.
Number of detected messages offering to date, March–June 2022 (download)
419 scams: “rich uncles” and Covid payments
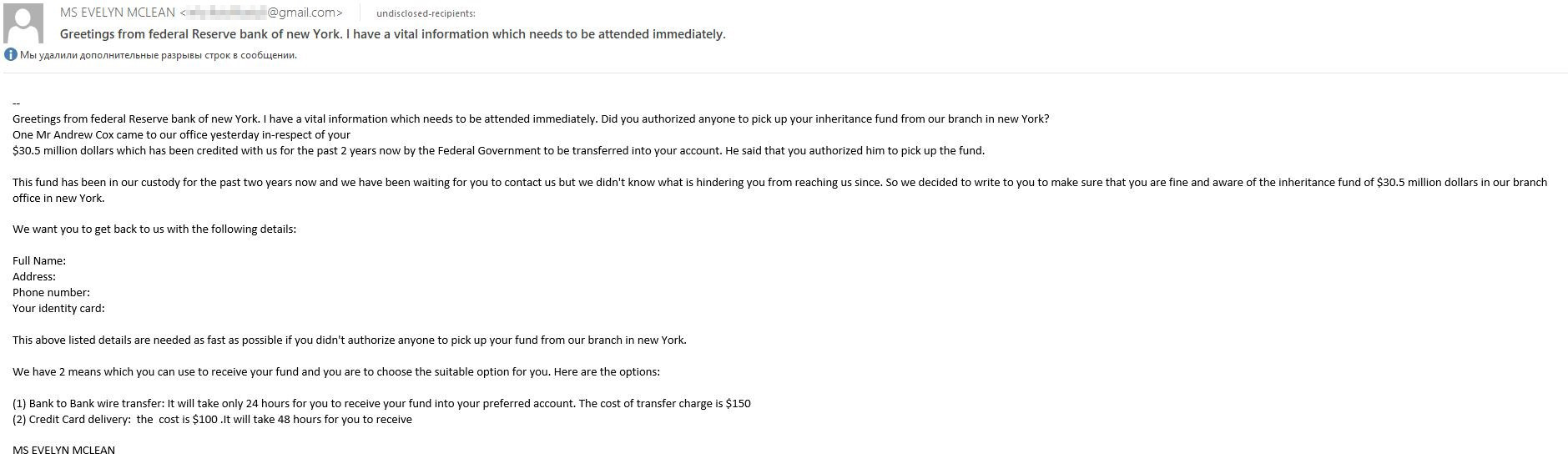
419 scams are one of the oldest types of text-based fraud. In the classic 419 letter, the recipient is informed by a “lawyer” or other “official” that a deceased relative or dying benefactor has bequeathed a huge fortune to them. All the victim needs to do is fill out a short questionnaire, pay a fee for administration and other formalities, and claim their millions. Often, the scammers do not mention the fee straight up but invite the victim to make contact by replying to the e-mail to find out more about their “inheritance.” In any case, once the fee is paid, they vanish.
419 e-mails are often crawling with grammar and spelling mistakes. This may be to mask words and expressions that could activate spam filters, or it could be that the attackers have a poor grasp of the victim’s language.
Classical 419 scam with inheritance
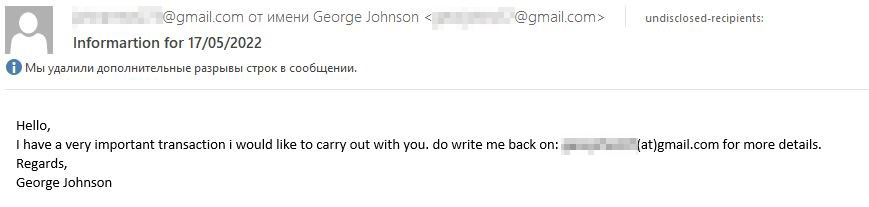
419 letters are still popular with attackers, who send them regularly and in large numbers: our solutions detect hundreds of thousands of such messages every month. Often instead of deceased rich relatives they exploit more relevant topics. For example, alongside with the increased attention to the Syrian war, cybercriminals were sending e-mails supposedly from people inside the country wanting to transfer large sums abroad.
419 scam with transactions
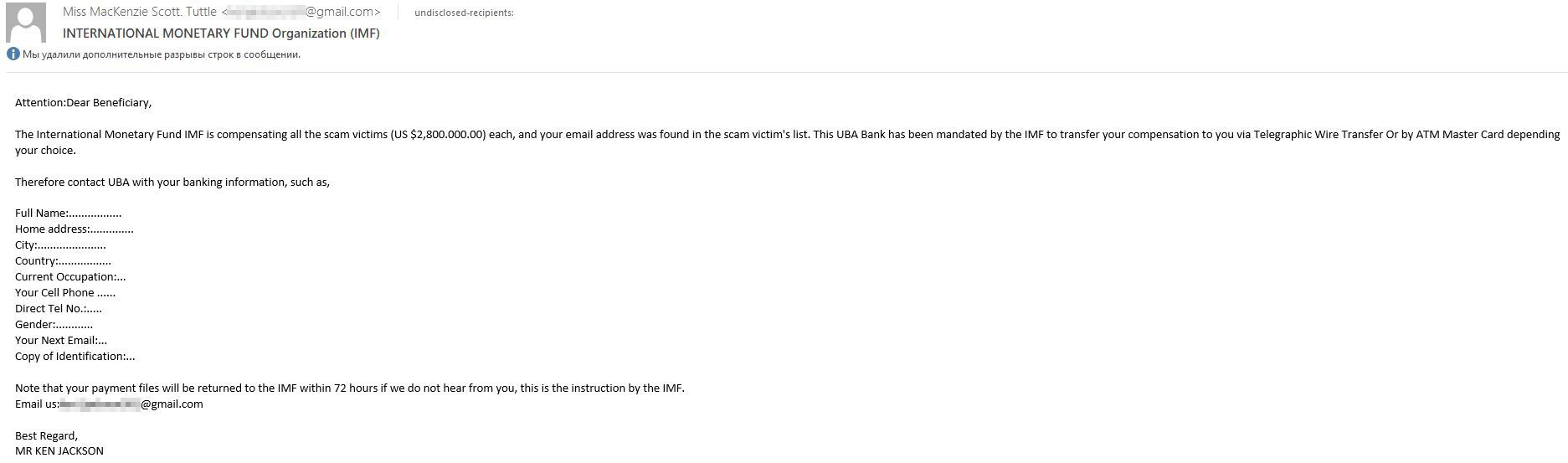
Lately, unexpected transactions have been doing the rounds, as well as payments to victims — of Covid, the Ukraine crisis and, ironically, frauds.
419 scam with compensation
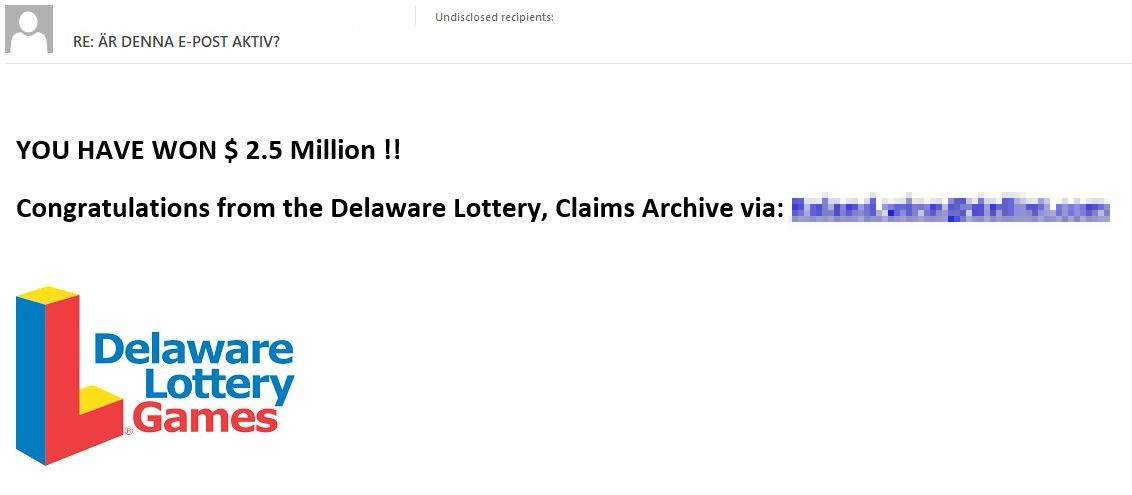
Another subspecies of the 419 scam is lottery winnings in which the “winner” did not participate. To make the scheme more credible, scammers usually claim that, say, a giveaway was held for taxpayers in a particular region or country, for owners of a particular e-mail domain, etc. Unlike Covid-19 compensation, such mailings are not new but they never lose popularity.
Lottery fraud
From a technical standpoint, not much has changed in the 419 scam — for the most part, messages are sent from free webmail accounts (Google Mail, Yahoo Mail, etc.).
To ask for details, send a form, etc., attackers usually encourage victims to contact them by mail. As soon as mail services can block addresses known as spam sources, they often give a different address for replies, one that is not flagged.
Statistics
From February to June, our solutions detected 1.8 million 419 scam e-mails. Their number began to rise in late February, peaking at 657,014 in March. In April, on the contrary, spammer activity decreased by more than half.
Number of 419 e-mails detected, February–June 2022 (download)
Blackmail scam
Whereas scammers use the above methods to exploit victims’ greed, blackmailers play on their fear. Typically, cybercriminals claim that they have come into possession of the target’s personal information, which, for a modest payment, they promise not to send to family members or post online. As a rule, they do not provide any actual evidence of data theft, since they did not in fact steal anything — this is how scammers differ from ransomware groups, which do indeed steal or encrypt files using malware.
Blackmail scams really came into their own with the popularization of cryptocurrencies: the blockchain’s anonymity eliminates the need for complex money-laundering chains.
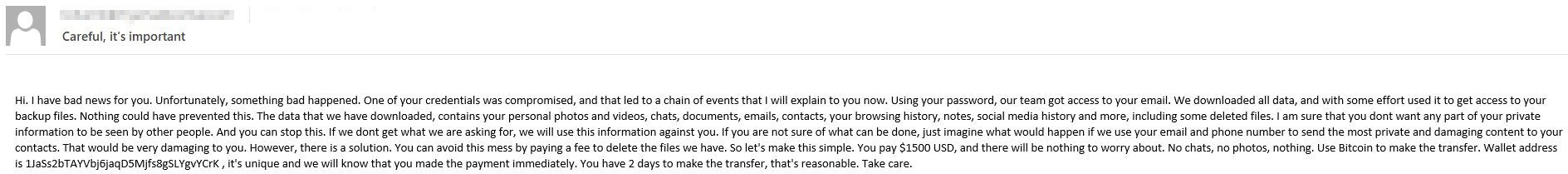
Extortion e-mail: the scammer claims to have hacked into the recipient’s mailbox
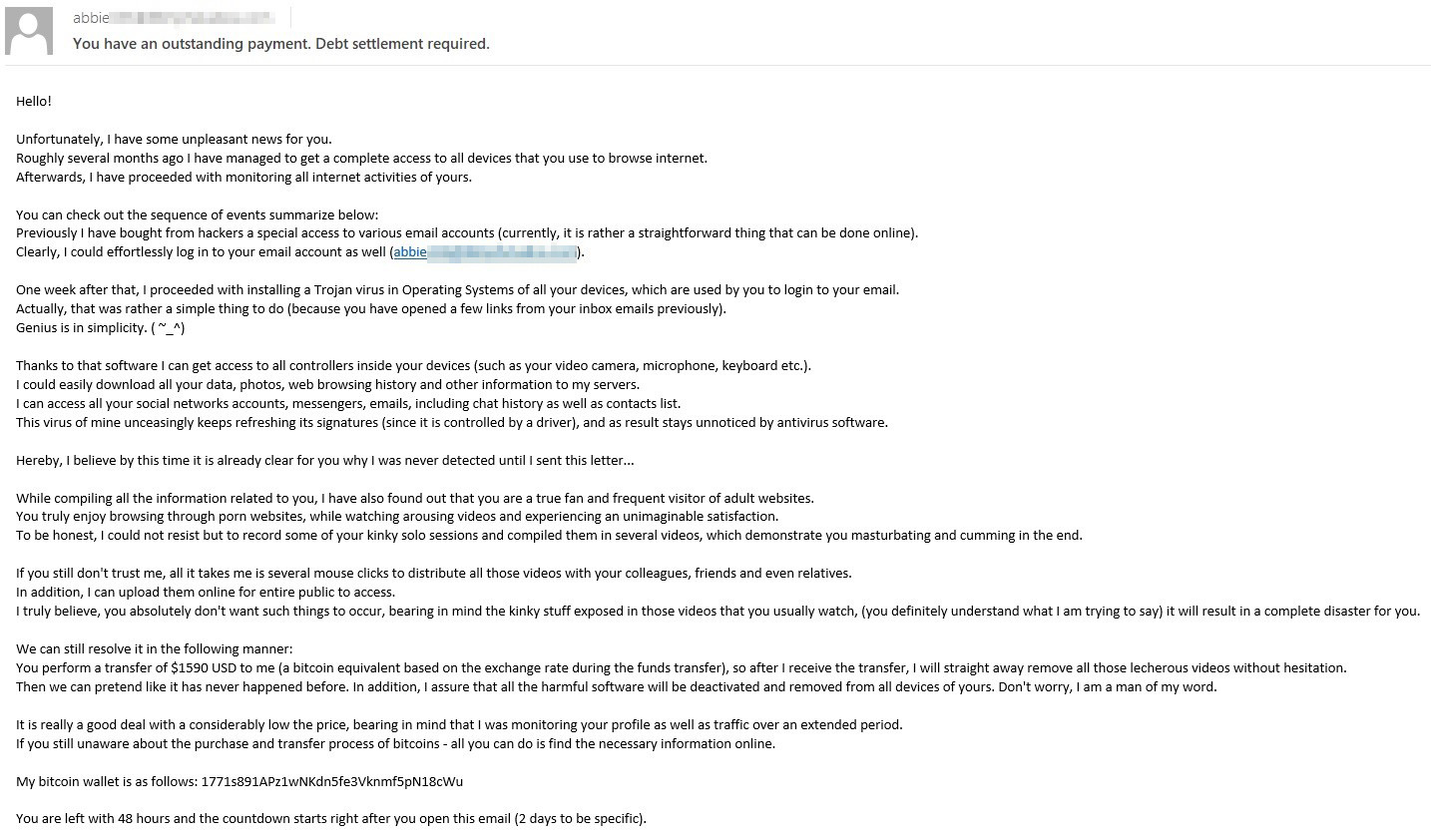
Extortionists attack both individuals and companies but employ different approaches. Individuals are most often threatened with publication of personal data allegedly stolen by hacking into their computer or mailbox. Scammers might also mention intimate photos or videos that they claim to have recorded through the device’s webcam. It’s quite possible they pinched this idea from the episode of Black Mirror.
Extortion e-mail threatening to post “intimate” content allegedly stolen from the user and containing their e-mail address in the From header
From a technical point of view, this type of fraud typically features e-mail address spoofing. Attackers substitute the recipient’s address in the From header, seemingly confirming mailbox hacking.
E-mails targeting individuals may also threaten administrative or criminal penalties, although such messages are far less common than ones about hacking.
Companies, meanwhile, can be threatened with bomb scare messages. In 2020 and 2021, extortionists actively sent out e-mails in the name of renowned APT and ransomware groups, promising to carry out an attack unless payment was forthwith. Unlike the majority of promises, attackers sometimes implement this one.
Statistics
There are significantly more extortion e-mails in mail traffic than other forms of text-based scam. For instance, from March to June, we detected more than 12 million blackmail messages.
Number of extortionate e-mails detected, March–June 2022 (download)
Vishing: scammers’ hotline
Vishing is short for voice phishing. As you might guess from the name, this is when attackers make contact with the potential victim via voice communication. How does this relate to text-based scams? In the past few years, vishers have been sending out mass e-mails asking the recipient to call back on their phone number, that is, spamming is the first step of the operation.
Vishing can target both individuals and companies. From the former, scammers try to extract confidential data, persuade them to install software for remote access, or to transfer money to the scammers’ account. And as for the target company employee, attackers can convince them to transfer money to a specific bank account or grant access to a corporate account.
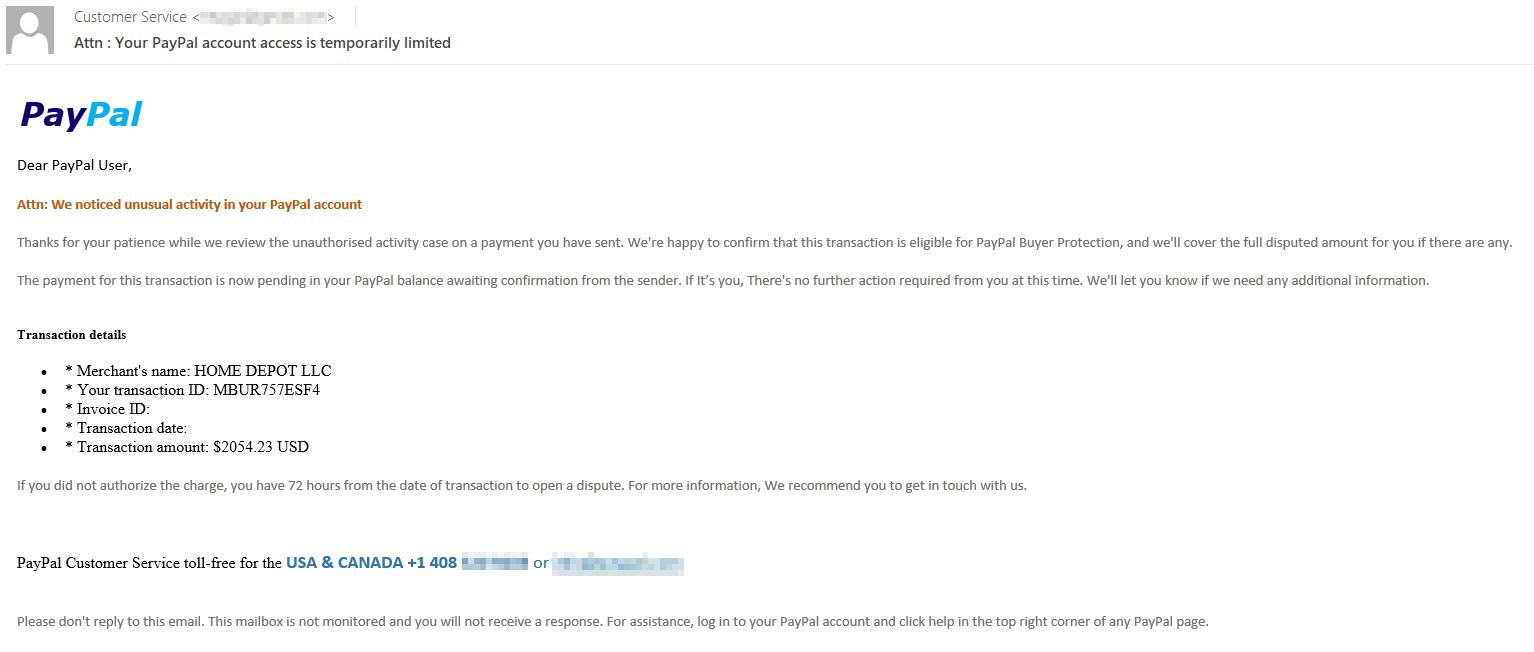
Fake PayPal notification about a large purchase. To cancel the order, the victim is asked to urgently write or call the support service
Most often, vishing e-mails masquerade as notifications from some service: this can be a large online store, a payment system, or, for example, subscription-based software.
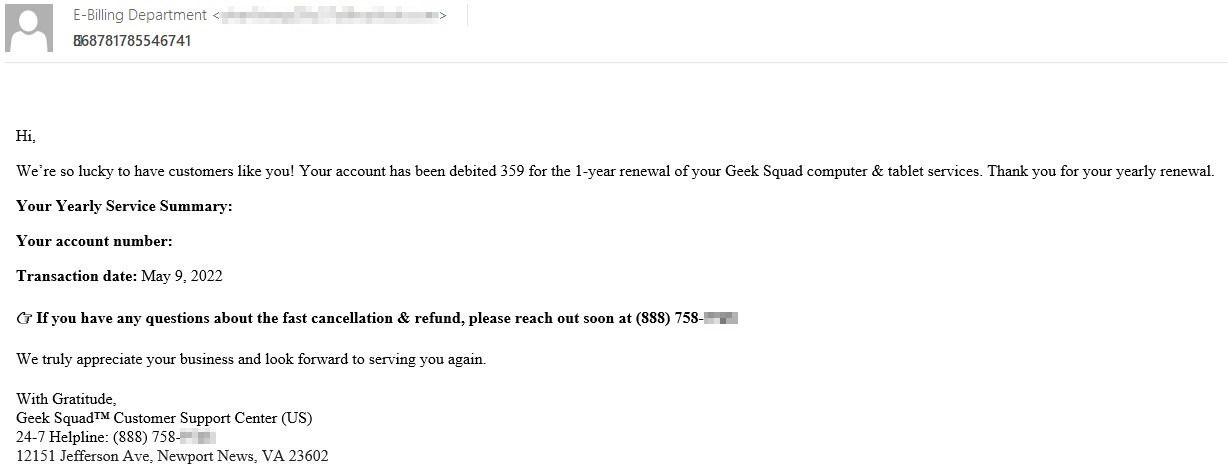
Fake Geek Squad notification. For more information, the victim is asked to call the specified number
Typically, the e-mails are composed so as to create the impression of being generated automatically. Most likely, this is so that the victim does not try to reply to the message but uses the vishers’ contact details.
To find out exactly how attackers achieve their goal, that is, to fish (or vish) out data or money, I called a couple of numbers provided in such e-mails. In both cases, after a short introductory dialog, a confident voice at the other end asked me to open a browser window and spelled out a URL (anydesk.com) for me to download the Anydesk remote access program. In response to my question about such a long unsubscribing process, the first scammer, absolutely unfazed, replied that they needed to log in to my bank account to confirm and then cancel the transaction. When I replied that I did not use online banking, the scammer hung up. The second turned out to be less talkative and did not give any interesting details.
On the one hand, this scheme seems too clunky to be widely used. On the other, communication via various channels and the attackers’ imitation of expertise can inspire more trust in the user than just an e-mail with a phishing link.
Statistics
From March to June 2022, we found 347,141 e-mails prompting the recipient to call the scammers back by phone. We saw a slight drop in this type of scam in April, after which the number of e-mails began to grow again.
Number of detected vishing e-mails, March–June 2022 (download)
Conclusion
Despite the existence of instant messengers, social networks and video chats, cybercriminals continue to use e-mail as the first point of contact with the victim, even if they switch to other channels afterwards. It is mainly the topics of the e-mails that change: attackers actively exploit current events to attract the potential victims’ attention. This suggests that despite users’ general awareness of cybercriminals’ basic methods, techniques such as intimidation and the promise of a free lunch, coupled with a willingness to spend time building trust, continue to reap rewards. The aim of these e-mails is to knock the user off balance and get them to act without thinking. Therefore, it is important not only to be aware of intruders’ techniques, but to make it a habit to respond to e-mails in a calm state of mind — or not to respond at all.
On the ISP side, solutions that employ machine learning and heuristics to recognize fraudulent e-mails can help filter out such spam.




















Text-based fraud: from 419 scams to vishing