
It has been three years since we published Lock, stock and two smoking Trojans in our blog. The article describes the first piece of malware designed to attack users of online banking software developed by a company called BIFIT. There are now several malicious programs with similar functionality, including:
- Trojan-Spy.Win32.Lurk
- Trojan-Banker.Win32.iBank
- Trojan-Banker.Win32.Oris
- Trojan-Spy.Win32.Carberp
- Trojan-Banker.Win32.BifiBank
- Trojan-Banker.Win32.BifitAgent
In spite of its functionality no longer being unique, the last program on the list caught our attention.
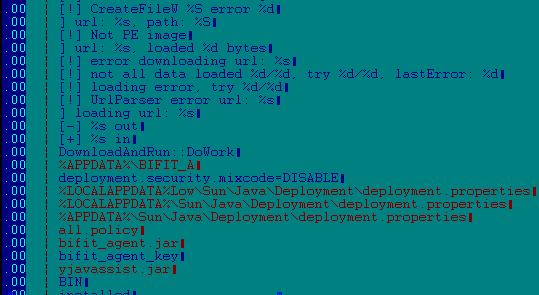
Words and strings used by Trojan-Banker.Win32.BifitAgent
This particular piece of malware has a number of features that set it apart from other similar programs.
Architecture
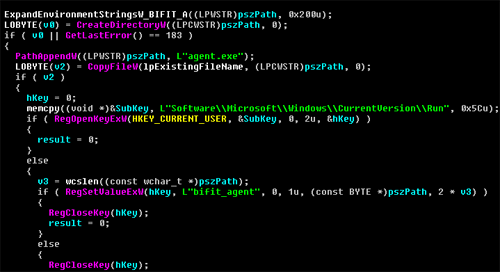
The malware runs two main modules on the victim-s computer: an executable file and a JAVA archive. During installation, it creates the folder C:DOCUMENTS AND SETTINGSADMINISTRATORAPPLICATION DATABIFIT_A, to which the following files are copied:
- AGENT.EXE v the main executable module responsible for communicating with the command server. The module is capable of updating itself, managing processes, executing commands using CMD.exe, and downloading and executing any files, all following commands from the command server.
- ALL.POLICY v a JAVA configuration file, which removes any JAVA security-related restrictions.
- BIFIT_A.CFG v the malicious program-s configuration file, which includes the infected system-s identification number and the command server-s address.
- BIFIT_AGENT.JAR v a JAVA archive containing code for interacting with BIFIT systems.
- JAVASSIST.JAR v a JAVA archive which includes additional functions required by BIFIT_AGENT.JAR.
The Trojan-Banker.Win32.BifitAgent code fragment responsible for installing and autostarting
modules on an infected system
In the course of its operation, the malware also creates several named pipes.
- \.\pipe10c86ecd42 v used for identification.
- \.\pipe10c86ecd51 v used to log its own activity.
- \.\pipe10c86ecd52 v used to communicate with BIFIT_AGENT.JAR.
As a result, during the operation of the malicious program the main executable module, which is responsible for communicating with the command server, functions simultaneously with the malicious JAR files, enabling the attackers to instantly modify any code running under JAVA while banking transactions are being carried out.
BIFIT_AGENT.JAR
By default, BIFIT_AGENT.JAR, which contains code providing interaction with BIFIT systems, is heavily obfuscated and all the classes in it are broken up into 156 files randomly divided into subfolders.
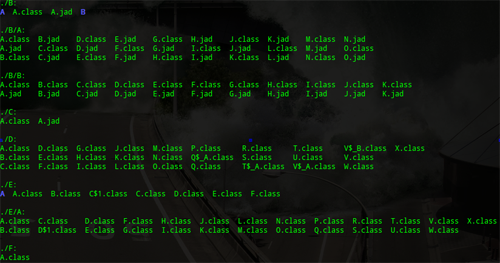
Obfuscated contents of BIFIT_AGENT.JAR v an example
Obfuscation makes analyzing the file-s interaction with BIFIT systems much more difficult, but it is nevertheless possible to reconstruct the malicious program-s actions because the file has extensive capabilities related to logging its own activity.
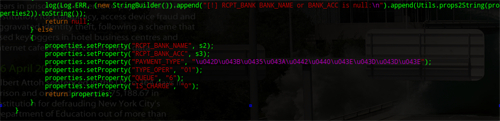
The part of the BIFIT_AGENT.JAR functionality which is responsible for intercepting banking transactions
carried out via BIFIT systems
Analysis of the functionality included in BIFIT_AGENT.JAR demonstrates that the JAR file-s main function is to spoof the data used in banking transactions carried out from infected computers. This is completely transparent to the user, since it is the data sent to the bank, rather than the data shown to the user, that is spoofed. The use of a USB token in the transaction in no way hinders the attackers, since the token signs a transaction only after the data has been spoofed.
Unfortunately, the command servers that return the account numbers to which the stolen funds should be transferred were no longer available by the time of writing.
Signature
The distinguishing features of Trojan-Banker.Win32.BifitAgent include a digital signature. At the time or writing (April 16, 2013), Kaspersky Lab-s malware collection included about ten variants of the malware, all of which have a valid signature issued to ?Accurate CNC.
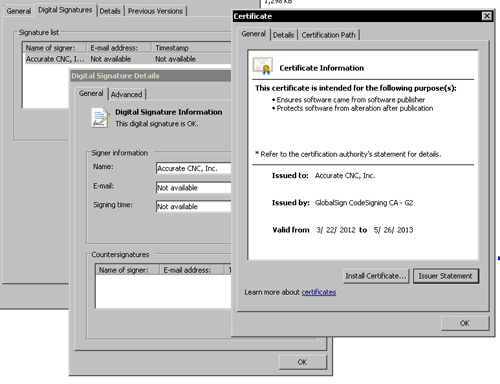
Digital signature of Trojan-Banker.Win32.BifitAgent
Accurate CNC is a company which really exists. It has a website (http://www.accuratecnc.com/) and offers equipment and software for designing electronics. It is worth noting that the publicly available demo version of their program, PhCNC Demo v3.26.4, is signed with the same certificate as the malicious program.
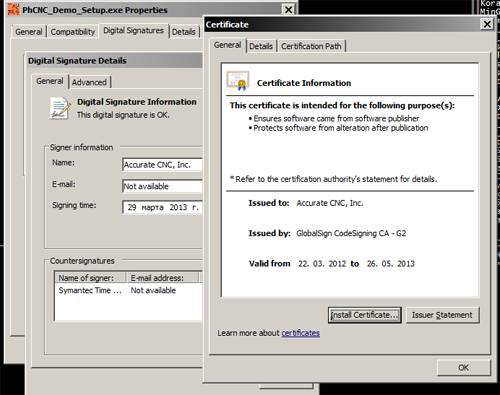
Digital signature of Accurate CNC-s program PhCNC Demo v3.26.4
In other words, we are dealing with a stolen digital signature, which is used by cybercriminals to sign malware.
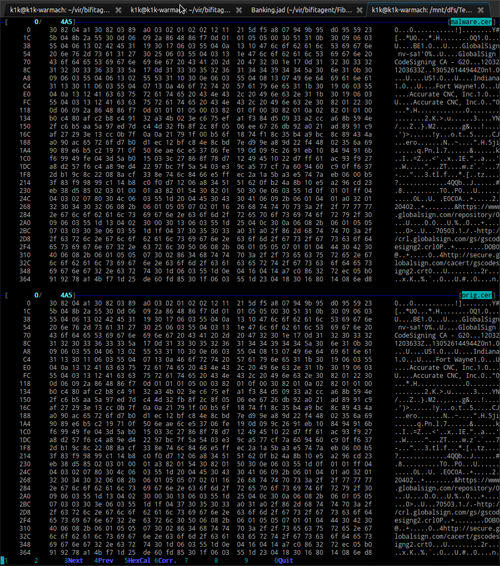
Comparison of certificates used to sign Trojan-Banker.Win32.BifitAgent and Accurate CNC-s PhCNC Demo v3.26.4
We got in touch with representatives of GlobalSign and the certificate was revoked.
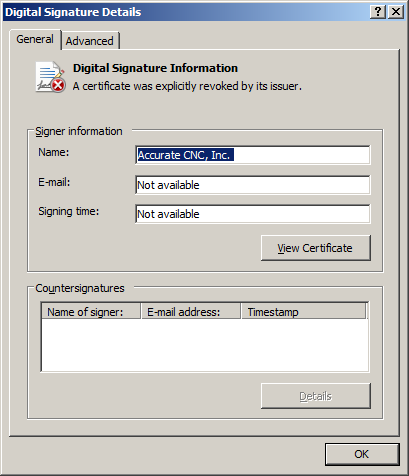
Conclusion
We have been detecting installations of Trojan-Banker.Win32.BifitAgent on machines that are part of botnets created using such malware as Trojan.Win32.DNSChanger, Backdoor.Win32.Shiz, Virus.Win32.Sality etc. No distribution via exploits has been detected.
It can be surmised from the selectiveness of infections that cybercriminals -sell- infected computers on which the use of BIFIT banking systems have been detected to other cybercriminals who install Trojan-Banker.Win32.BifitAgent on such machines.
According to KSN data, about 100 Kaspersky Lab users have been attacked by the malware since the beginning of April. It should be noted that the number of attacks per user is growing daily.
To summarize, the cybercriminals take advantage of the malicious program-s architecture, the stolen certificate and the targeted nature of the attacks to gradually increase the number of infected users. This translates to growing amounts in the cybercriminals- bank accounts.





















Lock, stock and two smoking Trojans-2