
"Do Not Disturb" Does Not Apply to In-room tablets
Hotels, Restaurants and Airports used to offer customers free tablets while using their facilities. Recently while attending an event and staying in one such hotel, I had the chance to use a free iPad especially installed in my room.
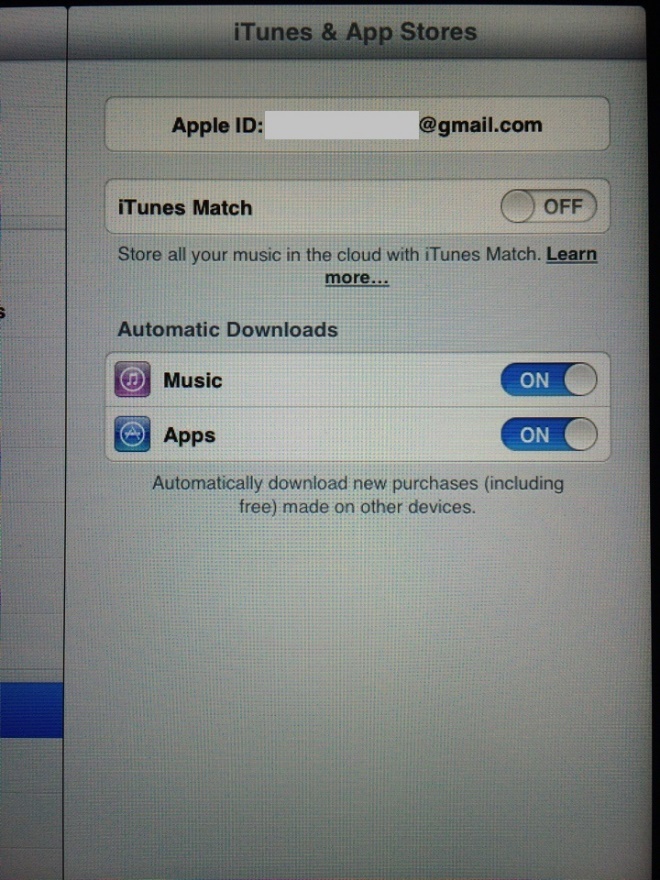
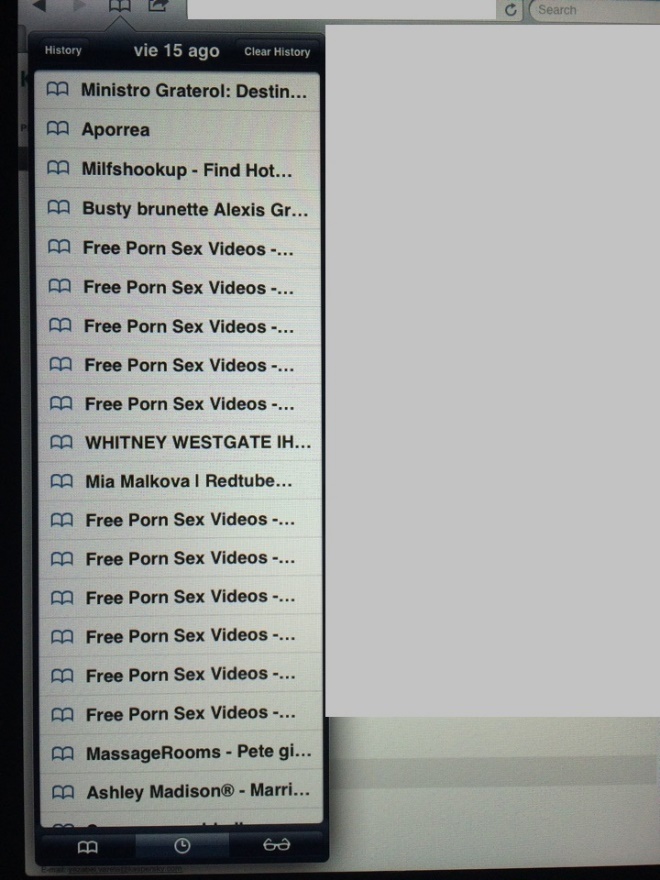
To my surprise, it not only contained the event agenda and provided a free WiFi connection, but also included a lot of private personal information from previous guests who had stayed in the same room.
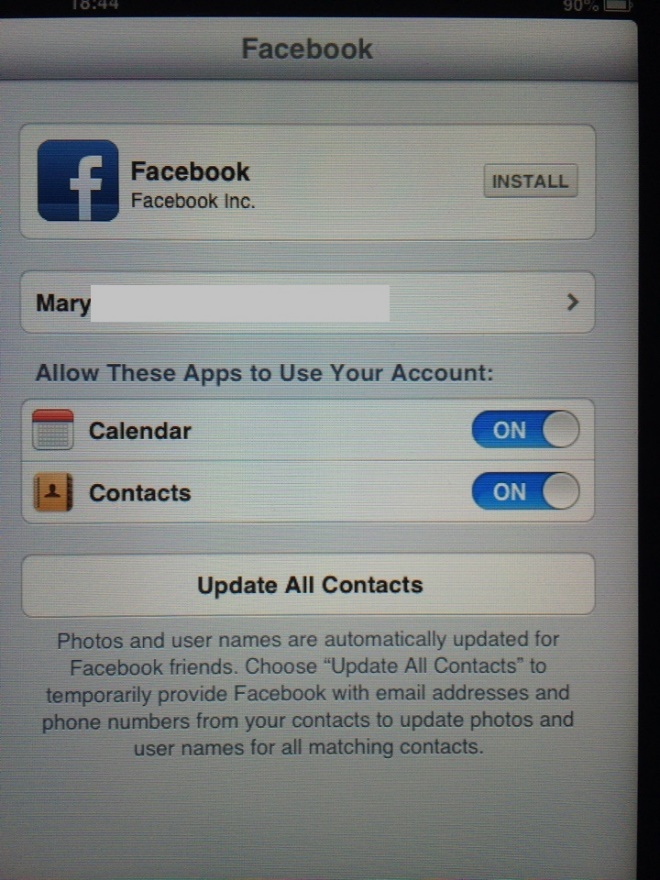
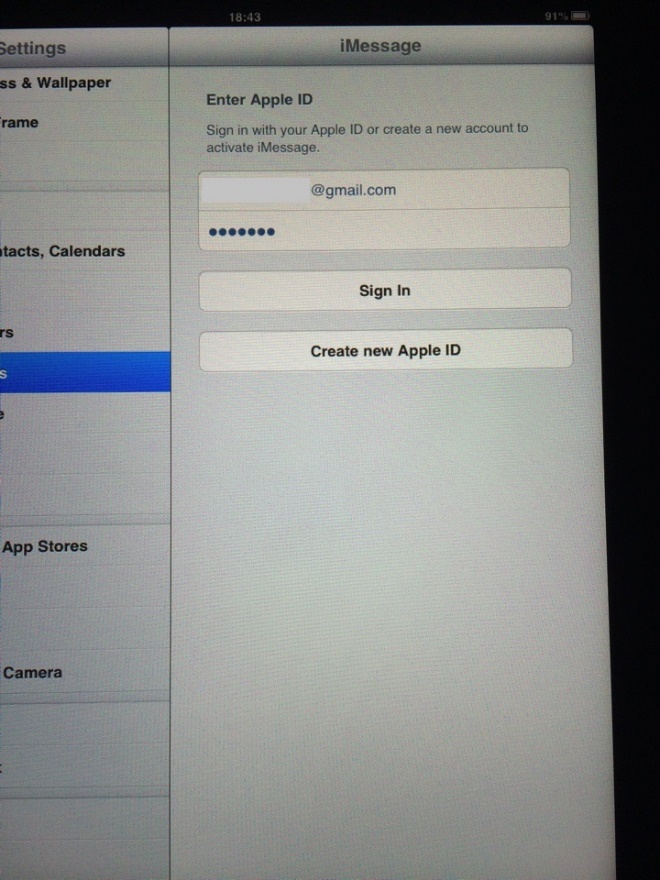
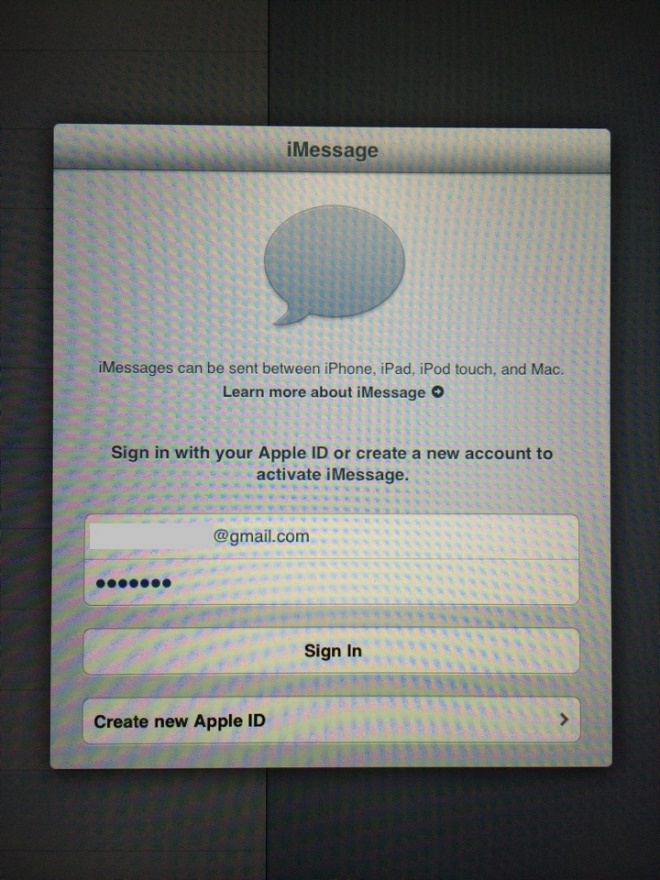
When I speak about private personal information, I mean accounts with pre-saved passwords, authorized sessions on social networks, search results from the browser (mostly pornographic content), full contacts automatically saved into the address book, iMessages and even a pregnancy calculator with real information. It was not hard even to figure out that the identity of the woman who had used it, since she also left her personal contact information on the device:
|
|
|

|

|
|
|

|
Having full names and email addresses cached on the device, it was not hard to Google a little bit and find out that some of the users were very public people working for the government of the country where I was staying.
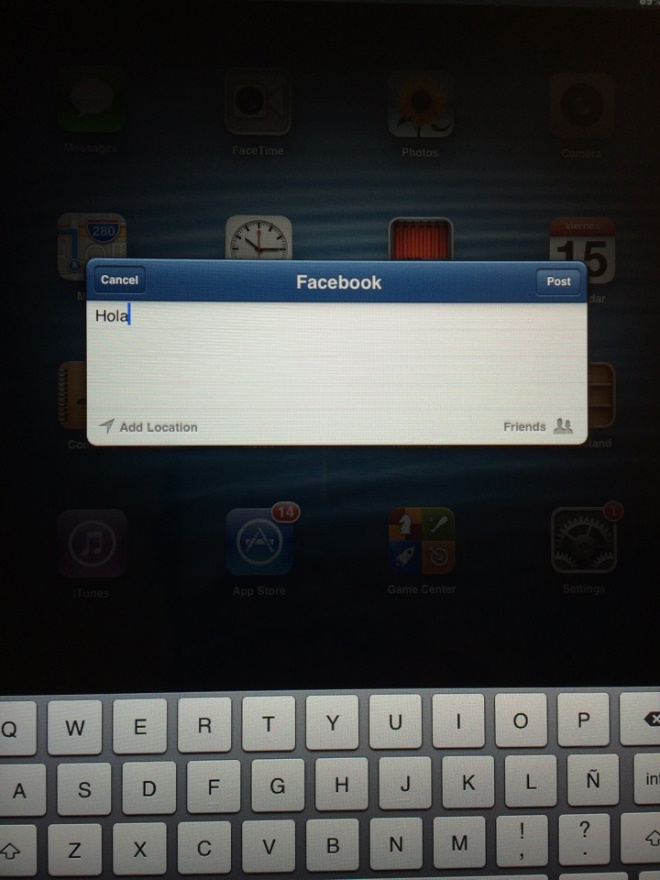
Most of sessions were still open, even allowing the posting / sending of messages in the name of the user:
This is completely unacceptable, from a security perspective. Basically a potential attacker had the chance not only read sent and received messages but also to impersonate the victim by sending messages in their name.
I also see this scenario as a perfect personal data collector for high profile spear phishing campaigns. On the other hand, if a potential attacker came from a classic cybercrime sphere, they might blackmail their victims. Moreover, it would be extremely easy for the criminal to do this, since they would have all kinds of data of the victims, including the name of pornographic movies watched on each specific date and time. Bearing in mind that some of the potential victims are public people and work for the government, most probably such blackmail would be successful.
So, what’s wrong here? Well, I would say everything. First, it is unwise to use a free public device for personal and private communication. You just never know if the device is backdoored or who might be behind such hospitality? Second, if a public facility wants to offer its guests free portable devices for the duration of their stay, it’s important that such devices are a properly configured first, to apply sensible security policies such as not storing personal information, not saving passwords and so on.
Maybe I’m too suspicious, but having an unknown and untrusted device like a tablet in my room, which is equipped with an embedded camera and a mic, I just preferred to switch it off and store it inside a drawer. I had to do this every afternoon since the cleaning staff put it back on the desk every day I was at the hotel.
You have also remember that, even if such a free device is properly configured and does not visibly store any private information, you can’t be sure that the next guest is not an expert in forensic analysis, in which case they could just take an image of the whole device and then recover your personal information step by step.
You may follow me on twitter: @dimitribest
Leave your passwords at the Checkout Desk





















Sandra
This is not really a new issue. You have this problem in each Internet cafe or hotel business center.