
Almost a year ago, we wrote our first blog about the mobile Trojan Svpeng. Back then, the first impression was that it was a standard Trojan-SMS class malicious program that stole money from SMS banking accounts.
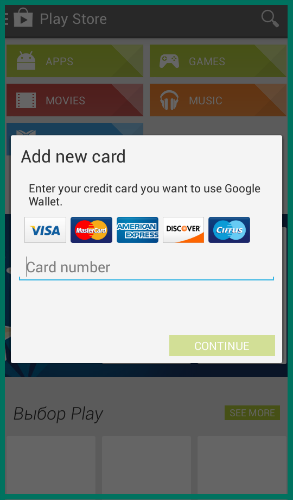
Later we discovered that the cybercriminals had perfected the Trojan’s functionality and it had begun attacking mobile banking users, in particular, customers of three of Russia’s biggest banks. Svpeng would wait until the user opened an online banking app and then replace it with its own in an attempt to obtain the victim’s login and password. The Trojan also attempted to steal bank card details by displaying its own window on top of the Google Play app and requesting the information the criminals wanted.
Then, at the beginning of 2014, we detected a new modification of Svpeng with ransomware capabilities. When instructed by its server, the malware attempted to block the user’s phone and display a message demanding payment of a $500 “fee” for alleged criminal activity.
However, that functionality quickly disappeared from the new version of Svpeng. It turned out that the cybercriminals behind the malware had decided to enhance it and release it as a separate Trojan. During this time the original version of Svpeng continued to develop and infect new users, with Russian mobile banking customers remaining the target.
But at the beginning of June we identified a new spin-off version of the Trojan. While the main version targeted Russia, 91% of those infected by the new version were in the US. The malware also attacked users in the UK, Switzerland, Germany, India and Russia.
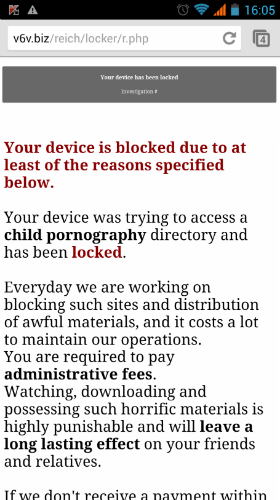
This new Svpeng is a typical piece of ransomware. After launching, it imitates a scan of the phone…
…and, of course, it finds some prohibited content.
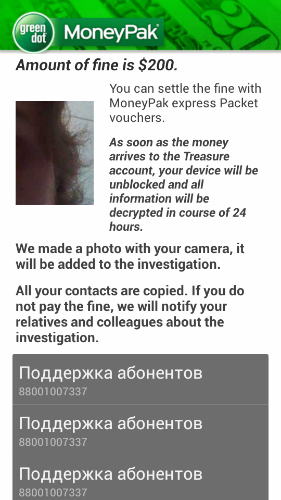
The malware then blocks the phone and demands a payment of $200 to unblock it. It also displays a photo of the user taken by the phone’s front camera, in behavior that is almost identical to that of the recently detected Trojan-Ransom.AndroidOS.Pletor.a.
The creators of the Trojan accept MoneyPak vouchers for the ransom payments – Svpeng helpfully informs victims where they can be bought in the US.
When it comes to ransomware Trojans, the new modification of Svpeng stands out for its wholly new implementation of standard features – it completely blocks the mobile device, even making it impossible to invoke the menu to switch off or reload the device. The victim can turn off the device by pressing the on/off button for a few seconds, but the Trojan immediately starts working as soon as the device is switched on again.
We managed to identify seven modifications of the new Svpeng, and all of them include a Cryptor class reference, but none of them makes any attempt to use it. It could mean that in the future the cybercriminals will use the Trojan to encrypt user data and demand a ransom to decrypt it.
As well as all the ransomware functionality, these versions have another distinguishing feature. The Trojan checks if the following apps are installed on the system:
- com.usaa.mobile.android.usaa
- com.citi.citimobile
- com.americanexpress.android.acctsvcs.us
- com.wf.wellsfargomobile
- com.tablet.bofa
- com.infonow.bofa
- com.tdbank
- com.chase.sig.android
- com.bbt.androidapp.activity
- com.regions.mobbanking
It then loads the results of the check to the cybercriminals’ server. As you can see, the list includes apps offered by major US banks for mobile banking. The cybercriminals are probably just gathering statistics about the use of these apps on infected devices. Considering that Svpeng is, first and foremost, a banking Trojan, we can expect to see attacks on the clients of these banks who use mobile apps to manage their accounts.

























Latest version of Svpeng targets users in US