
Two weeks ago we recorded a surge in Koobface, the highly prolific worm infecting social networking sites. It targets sites such as Facebook and Twitter and uses compromised legitimate websites as proxies for its main command and control server.
From the beginning of March the live Koobface C&C servers, which are used to send out commands and updates to all the computers infected by the worm, were shut down or cleaned on average three times per day.
The number of C&C servers dropped steadily from 107 on February 25, to as low as 71 on March 8. Then, in just 48 hours, the number doubled. As you can see in the graph, 10 March was the peak, with 142 active Koobface C&C servers. After that, the number started to drop constantly. We witnessed an average of 5 servers being taken down every day.
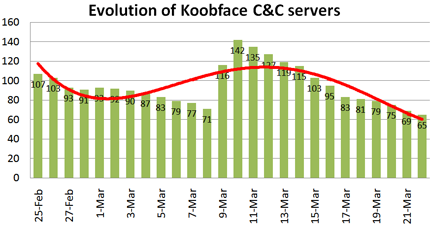
Right now, the number is just below 70, the lowest it has been in over a month.
Cybercriminals don’t want the number of C&C servers to drop too much, as that would mean losing their control over the botnet. So, if the earlier strategy of the Koobface gang is anything to go by, we should be seeing new servers being added to control the botnet soon, most probably this week.
We will continue to monitor the situation and let you know if there are any important developments.
Kaspersky Lab would like to provide a few tips for users:
- Be cautious when opening links in suspicious messages, even if the sender is one of your trusted Facebook friends.
- Use an up-to-date, modern browser: Firefox 3.x, Internet Explorer 8, Google Chrome, Opera 10 etc.
- Divulge as little personal information as possible. Do not give out your home address, telephone number or other private details.
- Keep your antivirus software updated to prevent new versions of malware from attacking your computer.
Kaspersky Lab users running any of the Company’s current anti-malware products are fully protected from all known variants of Koobface.




















Koobface C&C servers steadily dropping – new spike coming soon?