
- Kaspersky Security Bulletin 2009. Malware Evolution 2009
- Kaspersky Security Bulletin 2009. Statistics, 2009
- Kaspersky Security Bulletin: Spam Evolution 2009
Annual overview
- The percentage of spam in email traffic averaged 85.2% in 2009
- The biggest source of spam (16%) was the US. Asian countries were also major sources of spam in 2009.
- The percentage of phishing messages in email traffic amounted to 0.86%.
- Malicious attachments were found in 0.85% of emails.
- The economic crisis had a major impact on the various categories of spam in 2009.
- SMS scams remained a widespread feature in spam.
- For the first time, spam contained links to spammer videos on YouTube.
- Spammers continued to improve the use of HTML to disguise links in spam emails.
- Spammers once again used image distortion in order to bypass filters.
- Spammers continued to exploit the latest news stories and celebrity names in order to catch the attention of Internet users.
- Spammers took advantage of the popularity of social networking sites.
Spam in mail traffic
The percentage of spam in mail traffic in 2009 came to an average of 85.2%, or 3.1% higher than in 2008. The highest percentage of spam recorded was 93% on 22 February, while the low for the year was 72.8% on 26 April.
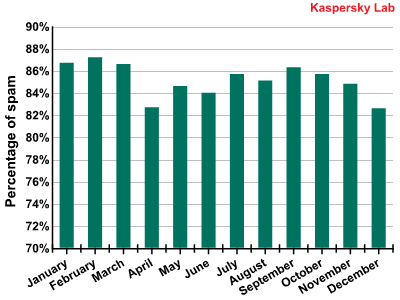
The percentage of spam in mail traffic in 2009
Over the year, fluctuations in the monthly percentage of spam in mail traffic remained within a 5% range. The average monthly percentage ranged from 82.6% (December) up to 87.2% (February). In the second half of the year, the percentage of spam was more stable and throughout July and August the figure changed no more than 2.5%. Just like the previous year, there was a decrease in spam in December. In 2008, the spread was much wider, with the percentage of spam ranging from 73.7% to 90.7% over various months. Whether or not this means the level of spam in mail traffic has stabilized around the 85% mark, only time will tell.
Sources of spam
Sources of spam
In 2009, the US was the leading source of spam on the Russian Internet. Russia was ranked second and Brazil was third. In 2008, the top three sources of spam were Russia, the US and Spain. As we have already mentioned in our article Spam evolution: January – June 2009, we saw much less spam coming from Western Europe in 2009 and more from Asian and Latin American countries.
The changes in the spam distribution trends from various countries in 2009 are shown in the graph below.
Sources of spam (spam trends by quarter)
The graph shows a sharp increase in the number of messages sent from the US. It should be noted that this increase took place at the same time as a jump in the number of infected American domains, which was addressed in Kaspersky Lab’s third quarter report.
Spam by category
A breakdown of spam by category, 2009
The top five spam cateogries in 2009 were:
- Medications and health-related goods and services — 18.9% (-4.7% compared to 2008)
- Education — 15.9% (+3.9%)
- E-advertising services — 11.7% (+6.8%)
- Other goods and services — 11.2% (-4.9%)
- Fake luxury goods — 8.5% (-0.6%)
Unlike the percentage of spam, the different categories of spam underwent some major changes throughout the year.
A breakdown of spam categories in the first half of 2009
A breakdown of spam categories in the second half of 2009
As you can see from the pie charts, the Education category more than doubled its share in the last six months of the year, Travel and tourism grew more than 2.5 times, while the leaders from the first half of the year lost ground.
Spam in times of crisis
It is possible to track the development of the economic crisis based on the fluctuations in different spam categories in 2009. We have already written about the decline in the amount of spam advertising goods and services for SMBs since the start of the crisis, and the simultaneous increase in the amount of criminalized spam and advertising of spammer services.
The percentage of spam in the real economic sector began to drop in August 2008 and (although there were some spikes throughout the year) continued to fall until May 2009 — the peak of the crisis. This was related to the fact that the clients of this type of spam — representatives of small and medium-sized businesses — were either forced out of business by the crisis, or cut back on advertising and stopped ordering spam. The spammers themselves began to actively seek out new clients. The amount of spammer advertising in unsolicited mass mailings rose sharply and by April 2009 reached a high of 19.7%, having previously never exceeded 4-5% of all spam.
Until those former clients start to renew their orders the spammers had to find a way of paying for things such as server maintenance and botnet fees. They managed to do this with the help of so-called affiliate or partner programs.
Internet partner programs are a form of Internet marketing that is commonly used in SEO (search engine optimization — a series of steps taken to improve a website’s position in search engine results) and in the promotion of goods and services. The idea behind partner programs is to attract customers and clients from third-party websites. It works in the following way: a partner puts a banner or a link to a client’s site on his own website. If a customer who visits the partner site uses the link and ends up making a purchase, then the partner receives a percentage of the store’s profit. In some cases, partners will make a payment even if a potential customer simply visits the client’s website.
Partner arrangements are very popular today among criminal Internet businesses. Using partner programs, they sell prescription-only medications without a prescription as well as counterfeit luxury goods and cheap software. This marketing approach is also commonplace in the pornography industry, where a partner will receive a profit for each user that visits the website. Furthermore, scammers use similar methods to lure Internet users to websites with fake antivirus programs and websites whose owners make money via text messaging scams.
A spammer who is involved in a partner program does not get paid for every million emails sent but for every customer who makes a purchase after receiving a spam email.
The chart below displays a clear relation between the amount of spam generated as part of partner programs (in the following categories: Medications and health-related goods and services, Fake designer goods, Adult content, and Computers and the Internet) and traditional spam, for which a client pays spammers for mailings advertising his goods or services (for the following spam categories: Education, Other goods and services, Travel and tourism, Real estate, Legal and audit services, and Printing services). Furthermore, we can also see that the spammers advertised their own services when orders fell short of ideal numbers.
The percentages of traditional spam, spam generated under partner programs, and spam advertising spammer services
The processes shown on the chart can easily be matched against the development of the financial crisis. As a rule, companies that order spam through a partner program are large criminal structures, as opposed to SMBs, which tend to place direct orders for spam mailings. As you can see from the chart, from February through to May, the amount of traditional spam fell, reaching its lowest point in May. May also happens to be the month in which the crisis “hit bottom”, according to the experts. As of May 2009, the amount of spam advertising goods and services offered by SMBs began to rise, while the amount of spam generated through partner programs began to decline, together with the amount of advertising for spammer services. By December, all of these indicators had more or less returned to their pre-crisis levels.
Fraudulent spam
In the second half of 2009, the amount of spam in the Computer fraud category rose considerably.
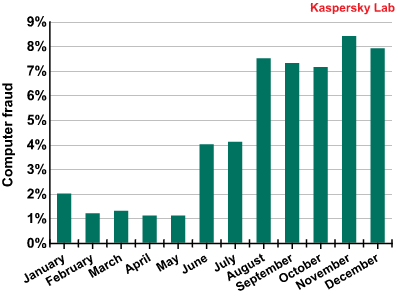
The Computer fraud spam category in 2009
This category includes phishing spam, so-called Nigerian scam letters, fake notifications of lottery wins, text message scams, and other types of fraud.
Phishing
In 2009, the amount of emails containing phishing links decreased markedly in the spring. Expert assessments suggest that the crisis bottomed out in the spring. The rise in the amount of phishing emails came just as the world economy started to come out of the crisis in August 2009. The amount of phishing messages in email traffic averaged 0.86%. Our expectation that the difficult economic climate would make phishers more active turned out to be wrong. Instead, it looks like the social engineers came to the conclusion that during times of financial difficulties, users are likely to be more careful about risking their savings. As the crisis began to wane, people probably had more disposable income and would not be so cautious. Of course, there is also the fact that each phishing project requires a certain amount of expenditure and, correspondingly, is easier to launch under more favorable economic conditions.
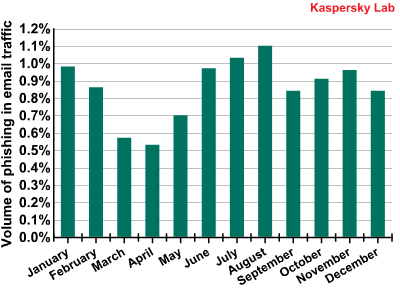
The amount of emails with phishing links in email traffic
In 2009, PayPal was once again the most frequently attacked organization. Malicious users continued to focus their efforts against the electronic payment system throughout the year. The online auction system eBay was the second most frequently attacked resource.
Major US banks such as Bank of America and Chase came third and four, respectively. Readers should note that for the second year in a row, Chase was among the top five most frequently attacked organizations due to very large, albeit short-lived attacks by malicious users. In 2009, this organization was subjected to the most attacks in August, but didn’t always make the top ten during the rest of the year.
Organizations attacked by phishers in 2009
It is interesting to note the appearance of the Internal Revenue Service — the US’s tax authorities — on the list of most frequently attacked organizations. Malicious users began attacks against the IRS in September 2009, not long before the last deadline for submitting tax declarations. Over the course of three months in autumn, the IRS was among the top ten most frequently attacked organizations.
Starting in late summer, we observed a number of different types of phishing emails aimed at users of the popular MMORPG World of Warcraft. The accounts of social networking sites have also drawn the interest of malicious users. At the end of the year, Facebook became a primary target for phishers.
The last few months of 2009 saw levels of phishing in email traffic almost return to those seen in January.
Text message scams in spam
In addition to phishing, so-called Nigerian scam letters and fake notices of lottery wins, the Computer fraud category has also included messages in which the recipient is urged to send a costly text message to a short premium number. The user, from whom a hefty sum is unexpectedly debited, usually does not receive the promised services in return. This type of spam is typical for Russia and Ukraine, but not other countries. In other countries, the process of leasing or otherwise obtaining short numbers is much more complicated. The parties applying for a short number are required to submit detailed information about themselves, which makes it possible to filter out the scammers and hold them responsible.
The previous year, when this trick was just starting to make an appearance, scammers used classic social engineering methods: they would either inform recipients that they had won something, threaten to close an account, or offer “cheap” porn. In 2009, we saw more creative tactics employed to persuade users to send text messages, with some bizarre subject lines.
Some of the hottest topics were “audio narcotics” and the ability to locate people via their mobile phones.
The former lures users with an mp3 file that can allegedly put the listener into an altered state of consciousness, similar to that produced by drugs. In the latter case, the scammers promise to find out a person’s location based on their mobile telephone number.
For each of these services, the spammers suggest that users pay via a text message. However, the cost of the message is significantly higher than they claim (which is typical for text message scams).
Upon closer inspection, both of these services turn out to be fakes. The press warned gullible users in a number of reports that the mp3 files could not put people into altered states of consciousness. It is difficult to hold the culprits accountable, since their websites include a special “Rules” section (usually difficult to locate and with very small text in light colors that is difficult to read) that includes information about the services or their absence, and the real costs involved of sending text messages.
This is what a typical spam email offering services to locate people looks like:
[text in img above:
Welcome! We have launched a new project that can help you track any cell phone subscriber using the Internet. Click to learn more!
[link] Yours, YANDEX&RAMBLER]
This is what you will likely find in the Rules section of a scammer’s site:
Disclaimer (a) The User uses this service at his own risk. Services are made available to the User as-is. Services do not presume any liability on the part of the service provider, including but not limited to the correspondence of results with the User’s search query; (b) The Website is a game meant to be used for entertainment purposes. All of the information presented on the Website is fictional and is not to be taken seriously;
The Rules section also goes on to say that the text messages sent to pay for these services cost nearly USD 10.
In some cases, spammers ask users to send not one, but three costly text messages, providing paid resources in exchange. After the user sends the messages, he receives a link to websites that turn out to be free.
Right now, many cell phone providers are making information available about the costs of sending a text message to any premium number upon request. This service could help protect people against fraud. However, only cautious users take advantage of it — the type of users that are unlikely to fall for these scams in the first place. As it is, cellular service providers are only just beginning to take a stand against fraud.
For now, users will have to rely on themselves, be careful and check the costs of text messages sent to short numbers before sending them. And of course, users should never believe anything written in a spam email.
Types and size of spam emails
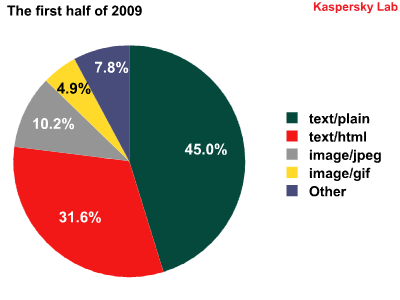
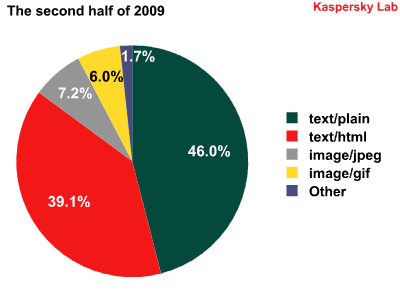
The distribution of different types of spam emails in the first and second halves of 2009
The balance among different types of spam emails was relatively constant. As before, emails using plain text were predominant, at an almost unchanging 45-46% throughout the year.
Spam using text/HTML came in at a strong second, and strengthened its position even further in the second half of the year, rising from 31.6% to 39.1%.
There were some changes when it came to graphical attachments. During the first half of the year, emails using JPEG images were the indisputable leader among the various types of graphical spam. At mid-year, the percentage of spam emails using JPEG images began to fall, and eventually gave way to the GIF image format.
This can be explained by the fact that spammers often prefer the GIF image format for graphics that contain text only.
For example, the image below is comprised of three graphical attachments: the first one is a photo of a sportsman and the pills, which are in JPEG format, while the next two — using black text (“We respect your rights…”) and grey text (“If you wish…”) — are in GIF format.
There were no major changes to the distribution of spam emails according to their size:
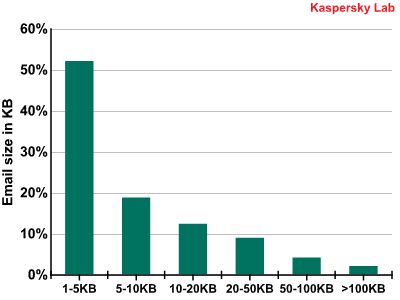
The size of spam emails
Nearly one-half of all spam is still comprised of small spam emails that are no more than 5 KB. The overwhelming majority of these are brief emails in plain text or HTML. They also include a handful of spam emails with graphics that are 5KB or less, such as the following image:
[img text:
A team of experienced workmen for your apartment renovations! From cosmetic work to full European-style renovation, any level of difficulty. All types of repair, renovation, and construction work.
Electrics, plumbing, painting, doors, tiling, flooring, etc.
Guaranteed quality, reasonable prices.
All types of work are guaranteed for one year.
Call: [number]]
Spammer methods and tricks
The main innovation in spam in 2009 was the use of YouTube for video spam. In October, several mailings were found with links to advertisements uploaded to YouTube. These mailings all promoted spammer services.
In spite of that fact that this was a new technique, spam filters had no problem weeding out these mailings. There were only a handful of links to various commercials used in a mass mailing (we detected no more than 10) and it is not difficult to block mailings that use one and the same URL.
At the end of the year, spammers used another interesting trick – although it wasn’t exactly new – that involved attaching mp3 files to spam emails. The audio file featured a pleasant female voice reading out the name of a website that sells Viagra. The name and producer of the track also pointed to the spammer’s website. The spammers also used the sound of a woman breathing heavily in the background.
Spammers continued to use and considerably improve some of the tactics used in previous years.
One of these tricks was a recording of a promotional offer and/or contact information using HTML only — without any letters or images. This isn’t a new method, but it was improved in 2009. The message includes a table with a large number of cells. Some of the cells are empty, while others are filled with a dark color. The spammers used a combination of empty and colored cells to produce the text they wanted.
Previously, spammers used tables with relatively large cells, which resulted in bulky, odd-looking letters and numbers:
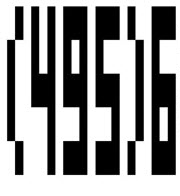
In 2009, spammers figured out that if they used tables with tiny cells, the text becomes much clearer and produces text like that shown in the following email:
Another technique that was modified in 2009 was the use of images with alternating backgrounds. To prevent spam filters from recognizing the messages used in spam mailings as identical advertisements and identifying the text used in the images as typical key words used in spam, in 2006 spammers began using “noisy” backgrounds in images with dark spots, splotches, and sometimes geometric shapes in different locations. The appearance of the message suffered, as did its readability. Back then, these types of messages often looked like this:
In 2009, spammers combined “noisy” images with more care for the appearance of the message itself. Instead of a messy backdrop, they began using attractive women in the background. In order to reach a large number of different options for the same picture, the image was broken up into several pieces. When viewed in a browser, these pieces came together and the user would see one attractive image:

At first, this method was used in English-language advertisements for medical treatments, although it was soon being used in Russian-language adult content spam:

Similar methods were used back in 2006, and are being used again after being abandoned for some time.
Another tactic used in graphical spam is to distort the text of the advertisement so that it appears in waves.
This method was also first tested and widely used in English-language advertisements for medications, and then a few months later it appeared in Russian-language spam as well:
Spammers also like to use attention-grabbing subject lines that mention hot topics and the names of well known public figures.
In 2009, the person most frequently referenced by spammers was US President Barack Obama. His name was commonly used after his inauguration on 20 January 2009, and remained a frequent topic for spammers throughout the entire year. His name was mentioned in connection with sensational headlines, blackmail, and Nigerian scams.
The email below is entitled “Terrible Obama’s disease” and advertises the much-talked-about Viagra:
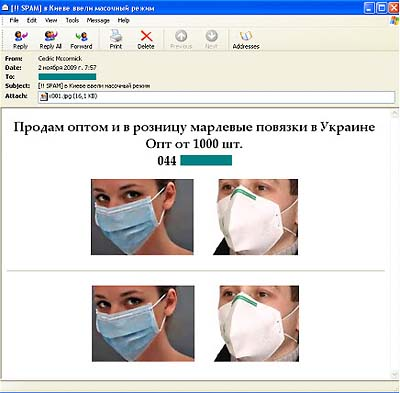
The spammers did not pass up the chance of exploiting the theme of swine flu either. Messages with startling email subject lines offering remedies actually contained links to Canadian Pharmacy stores selling Viagra. With all of the panic surrounding the virus, which peaked in September 2009, spammers came up with more interesting offers, such as a vaccine that didn’t exist, and flu masks.
The email below offered wholesale lots of medical masks:
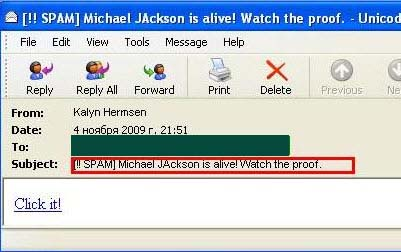
Spam mailings began to use the theme of Michael Jackson immediately after his death on 25 June. These mailings contained links to sites infected with malware. Spam campaigns making use of Michael Jackson’s name continued throughout the summer and beyond.
Internet users are still receiving spam with offers to buy one of Michael Jackson’s costumes, or to purchase a posthumously released video. Even as late as November, Kaspersky Lab received a spam message claiming “Michael Jackson is alive! Watch the proof”, with only a link to a website contained in the body of the message:
The link led users to Trojan.Script.Iframer.
Naturally there were numerous other topics that spammers used as well: holidays (starting from 8 March in Russia and ending with Thanksgiving Day in the US and Canada), qualifying matches for the 2010 World Cup, and the premiers of blockbuster movies. Nevertheless, the subjects addressed above were the most prominent in spam for long periods of time.
Spam and social networking sites
Spam is now very common on social networking websites and blogs. If a community is not moderated, or if the anonymous comment feature is not disabled, then the amount of spam received through blogs and social networks can be overwhelming.
Even email-based spam is getting on the social networking bandwagon. First of all, we receive various notifications via email that contain spam. Secondly, spammers use social networking websites and blogs as just another arena for posting the same ads that are in the email links. These spam messages advertise new, unknown social networks that often turn out to be dating sites. The term “social network” is used as a ruse.
Spammers also use the name of prominent networks and blogger services in order to bypass filters and attract user attention — a fake notification from a social network will seem more trustworthy. Furthermore, phishing attacks against social network sites in order to gain access to user accounts are also fairly common. As a rule, these attacks are targeted at the most popular websites, including Facebook and Twitter in 2009.
The phishing email below asks the recipient to update his Facebook account by clicking on the link provided. But the link actually leads to a website run by malicious users, and asks visitors to enter their account login and password:
In addition to phishing scams, fake messages from the wildly popular Twitter have also been used to spread viruses.
This fake Twitter invitation features an attached ZIP file that contains a virus:
As you can see, email-based spam and spam on social networking websites are closely related. By using email-based spam (with malware and phishing scams), a user’s account on a social network could be hacked. Or, if a user clicks on a malicious link, his computer may be infected and become part of a botnet that is used to send even more spam through social networking sites. Email-based spam uses the names of well known social networks, and also takes advantage of them as a platform to promote their goods and services.
Malware in email traffic
In 2009, 0.85% of emails contained a malicious attachment, which is just 0.04% less than in 2008.
The chart below shows the activity of spam mailings with malicious attachments over the past two years. As you can see, there was a surge in activity towards the end of the year in both 2008 and 2009. There was another big spurt in activity in March 2008, but from February through August 2009, the amount of spam with malicious attachments stayed at or below 0.4%.
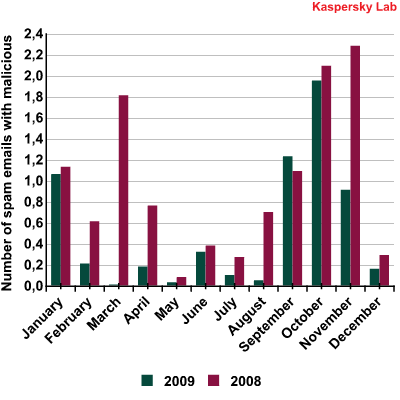
The amount of spam emails with malicious attachments in 2008 and 2009
In 2009, we saw an upswing in malicious spam in the autumn, which was primarily related to emails containing Zbot (a spyware Trojan meant to steal confidential user information) disguised as a notice from tax authorities, and emails via which malicious users spread the FraudLoad family of Trojans. FraudLoad Trojans install various rogue antivirus solutions (FraudTools) on a user’s computer using. Malicious users then extort money from unsuspecting victims by offering to repair or delete alleged malware on their computers.
The Top 10 malicious programs spread via email in 2009 are shown in the chart below:
The Top 10 malicious programs in 2009
In 2009, just like in 2008, the Iframe family took a big lead in the Top 10. Trojan-Clicker.HTML.IFrame.abn is a malicious program that is an HTML document containing a script that executes unauthorized requests to an infected website at http://ddhj.2288.org/d[****]2.htm directly from the HTML version of the email, or from an HTML attachment. Notably, Trojan-Clicker.HTML.IFrame.abn is the only representative of the HTML platform in 2009, while all of the other malicious programs execute in the more popular Win32 platform.
Second and seventh places in the Top 10 are representatives of the FraudLoad family: Trojan-Downloader.Win32.FraudLoad.epb and Trojan-Downloader.Win32.FraudLoad.wspk. In September, over half of all malicious programs that spread via spam were part of the FraudLoad family.
Third and sixth spots were occupied by malicious programs that were packed using two variants of the Krap packer: Packed.Win32.Krap.ah and Packed.Win32.Krap.w, usually used to pack Zbot and FraudTools. Packed.Win32.Krap.w is also used to pack Iksmas and Bredolab.
The notorious Trojan-Downloader.Win32.Murlo.cba. ranked fourth overall in 2009, having held first place in September’s Top 10.
As expected, the Top 10 also included two variants of Zbot: Trojan-Spy.Win32.Zbot.zur and Trojan-Spy.Win32.Zbot.gen.
Finally, eighth and ninth places were taken by variants of the Small backdoor: Backdoor.Win32.Small.zs and Backdoor.Win32.Small.zо.
The most striking trends in the spread of malware this year were fake emails allegedly sent as official notifications with ZIP archives as attachments. The largest of these campaigns were designed to look like notices from DHL and UPS.
However, these mail organizations were not the only large companies whose names were used by spammers to spread malicious programs. “Official notifications” also came from spammers claiming to represent Western Union and FedEx, in addition to a number of online stores where users had allegedly purchased various costly items in the past.
The emails were similar in structure, which suggested they may have come from the same author. Our suspicions grew even stronger when we received the following email:
Here, the spammer made a sloppy mistake by failing to match up the organization mentioned in his subject line with the one in the body of the text.
Fake e-greeting cards allegedly from the well known company Hallmark and other greeting card services were also used by social engineers to trick users into downloading malicious programs.
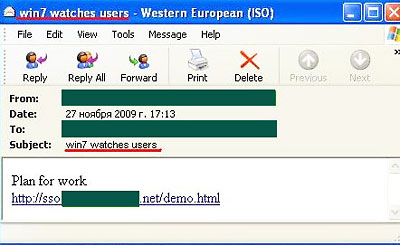
Naturally, spammers used hot topics in the subject lines of emails used to spread malware, such as the death of the “King of Pop”, the launch of the Large Hadron Collider, and the debut of Windows 7. Most often, malicious emails contained a link to a site infected with malware, rather than an attachment.
The email shown below, for example, features a “sensational” subject line that makes accusations about Microsoft’s latest release. The body of the email contains a malicious link that leads users to a Trojan downloader:
Conclusion
2009 was a year of financial crisis and was a difficult one for many businesses. Spammers also felt the squeeze, as the number of orders dropped significantly mid-year. However, the amount of spam in email traffic did not decrease, since spammers changed tactics by actively participating in partner programs. Furthermore, throughout the course of the year, the amount of spam in email traffic served as a kind of indicator of the crisis, allowing us to make some predictions about spam in the future.
The amount of spam advertising spammer services was particularly high this year, reaching 20% of all spam traffic over certain periods. This was how the spammers attempted to attract new clients during the crisis.
Surprisingly, there were only a few phishing messages in email traffic: at the peak of the crisis, the amount of this type of spam fell considerably.
The amount of malicious programs in spam did not undergo any major changes from 2008, but the different types of malicious email did change somewhat. Trojans that download fake antivirus programs were one of the most commonly used types of malware.
Over the year, spammers actively worked on the quality of their advertising and tried to make things more difficult for spam filters, while producing attractive advertisements for Internet users. In addition to traditional methods, they also used multimedia technologies such as audio files and links to video clips on YouTube.
The biggest source of spam in 2009 was the US, although there was a clear migration of spam sources towards Asian and Latin American countries. This can be easily explained by the fact that the number of computers and broadband Internet connections in these areas are steadily on the rise, and not all users in those countries are literate in Internet security. As a result, their computers are easier to infect with malicious programs and incorporate into a botnet.
2010 will most probably be a much less eventful year for the spam business. The amount of spam in total email traffic will remain at approximately the same level it is now or increase slightly. The text message scams which were so widespread in 2009 may become less common in 2010, especially if cellular service providers take a proactive stance in battling them. However, it will only be a matter of time before we see new scams emerge.
Methods such as using video and audio files in spam probably won’t become too common: the balance between message size, bypassing filters and making emails attractive for users clearly does not work in the spammers’ favor in this case. They will continue to use tried and tested tactics. Users can also expect spammers to continue to take advantage of social networking sites, where the amount of spam may well increase.








































Kaspersky Security Bulletin: Spam Evolution 2009