
- Malware Evolution
- Malware for non Win32 platforms
- Internet Attacks
- Malicious programs for mobile devices
- Spam Report
This latest half-yearly report covers the most significant changes in malicious code evolution over the last six months and included a number of predictions as to how the situation may develop based on the statistics we have today.
This report is primarily aimed at IT professionals who specialize in malicious programs, and it will also be of interest to users interested in malware.
Malware Evolution: Results of the First Half of 2006
The first six months of 2006 have brought considerable changes. The number of new malicious programs (including modifications) each month increased by an average of 8% compared to the same period in 2005 (see Diagram 1).
 Diagram 1. The number of new modifications made to malicious programs found over one month’s time. |
Diagram 1 shows that Trojans represent the lion’s share of malicious programs. Trojans are the only kind of malicious program that demonstrated growth in the number of new modifications over the first six months of this year (9%). The increased number of Trojans plays a large role in determining the growth of malware as a whole.
The figures for viruses and worms show a slight decline of 1.1%, which was to be expected. The MalWare class showed the largest decline of all, falling 2.3% compared to the same period in 2005.
We will examine the recent developments in all three categories in more detail below.
Trojans
Trojan programs are developing faster than any other class of malicious code. As mentioned above, the increase in the number of new modifications of Trojans hit 9% during the first half of 2006.
 Diagram 2. The number of new modifications made to Trojan programs found in one month’s time. |
A breakdown of Trojans by category is shown in Diagram 3.
 Diagram 3. A breakdown of Trojan programs by category. |
Of the many different types of Trojan programs, the most common are Backdoor (30%), Trojan-Downloader (26%), Trojan-PSW (12%) and Trojan-Spy (13%). How do these Trojans differ from others? The answer is actually much simpler than it would seem at first glance: it all depends on money. These Trojans are the key element when it comes to stealing personal data or creating a botnet. This is the reason why these are the most popular among malicious users, who are increasingly profit oriented.
The popularity of Trojan-Downloader and Backdoor programs can be explained by the fact that they are frequently used to create botnets. In order to be gain control over a victim computer, a malicious user will infect it with a small, specialized malicious program: a Trojan-Downloader. This Trojan’s job is to install other malicious programs to the system: more often than not, this will be a Backdoor program, which will give full remote access to the victim machine.
Then there are Trojan-Spy and Trojan-PSW programs. As the names indicate, these Trojans steal personal information. They can be used to trawl for almost any type of personal data, from passwords to gaming, financial and other systems to information that might be used in marketing studies – all without the user suspecting a thing.
In contrast to malicious code which is able to replicate (such as viruses and worms), Trojan programs have to be delivered to the victim machine. Recently, either Trojans have been delivered via spam with attachments containing malicious code, or downloaded using a vulnerability exploit. It should be noted that malicious users are currently showing a preference for mass spamming over the use of exploits. This costs in the range of $40-60 for one thousand infections, although no one promises the client that “his” malicious program will be the only one on the infected computer.
In future, the growth in the number of Trojan programs is likely to remain relatively steady, although it may decrease slightly.
Viruses & Worms
Viruses and worms have, as a class, been experiencing a steady decline for more than a year. The graph below presents the number of new modifications of viruses and worms detected on a month by month basis.
 Diagram 4. The number of new modifications of viruses and worms per month. |
Based on the results of the first half of 2006, the number of new modifications of viruses and worms has fallen by 1.1%.
Diagram 5 (below) shows the different types of viruses and worms detected in the first half of 2006.
 Diagram 5. A breakdown of type of viruses and worms detected during the first half of 2006. |
The number of new modifications has fallen across the class, from viruses, to email and other worms. This decline is caused by simple economics; it is less expensive to develop a primitive Trojan program than to create self-replicating malicious code such as a worm.
Both statistics and a series of other factors testify to a drop in the number of worms. For example, the number of global epidemics over the past six months has decreased considerably compared with the same period in 2005. This proves that the declining trend noted a year ago is being maintained.
The drop in the number of epidemics will undoubtedly lead to decreased financial and other damager. However, there is still a risk that users will fail to exercise adequate caution, thus creating opportunities for malicious users.
Viruses and worms will continue to decrease in number in the future.
Other Malicious Programs
This section examines the last class of malicious code that is detected by our antivirus databases. The evolution of malicious code which falls into the MalWare class is shown in Diagram 7, below.
 Diagram 6. The number of modifications of programs in the MalWare class. |
The number of new modifications of programs in the MalWare class fell by 2.3% compared to the same period in 2005.
The pie chart in Diagram 8 shows the different types of MalWare according to the Kaspersky Lab classification system.
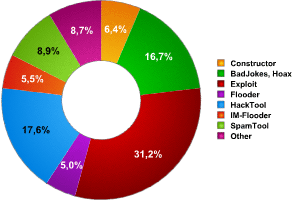 Diagram 7. A breakdown of different types of MalWare. |
Exploits, the most popular MalWare classification, represent 30% of this category of malicious code. They are an integral part of the mechanism used by other malicious programs to spread.
Extortion – A Dangerous Trend
One of the most dangerous trends seen over the past months is the growth in the number of incidents where malicious users use a program to modify data on a victim machine, and then blackmail the user. Many of these programs are very similar to one another, and are either designed to impair the victim machine’s functions, or to block access to data. The growth in the number of new modifications of such programs is illustrated in Diagram 8 below.
 Diagram 8. The number of programs which modified data and were used for blackmail. |
In January 2006, these types of program were basically represented by just one Trojan – Trojan.Win32.Krotten. The author of Krotten released 13 modifications of this malicious code in just two weeks, with enviable regularity. He constantly changed the code in an effort to prevent Krotten from being detected. This explains the jump at the very beginning of the first six months of this year, as shown in the diagram.
Starting in February 2006, computer blackmailers began to attract our attention with new kinds of malware from a range of different authors, although Krotten is still in the lead in terms of new modifications.
In late January, we saw the appearance of Virus.Win32.Gpcode, following right behind Krotten. Trojan.Win32.Krotten never modified user files (it modified the system registry so that the Trojan itself would be difficult to delete, and so that it would be difficult to use the infected machine), which meant that it would be possible, in theory, to return the victim machine to its original, pre-infected, state. However, Gpcode denied the user this possibility. Over the first six months of 2006, this malicious program evolved rapidly: the author moved from initially using a a typical symmetrical encryption algorithm to an asymmetric one, extending the length of the key used from 56 bits to 64, 260, 330 and so on up to 660.
During the first half of this year, the number of Trojans used for blackmail increased from two to six (Krotten, Daideneg, Schoolboys, Cryzip, MayArchive, Gpcode). At the peak of their development, their attacks were limited mainly to Russia and the CIS. However by the end of the July, the authors or users of these programs had clearly branched out – similar blackmail cases were seen in Germany, the UK and several other countries.
There is nothing to prevent these types of malicious code from developing further, a fact which gives cause for particular concern. We have already addressed instances in which beginners who yesterday barely knew how to use the mouse are now trying their luck with cyber blackmail. Although some attempts are more absurd than others – there have been cases in which the malicious user dictates the amount of money, and how it should be transferred, but forgets to include contact details. One example of this kind of Trojan would be Trojan.WinREG.Schoolboys.a.
Conclusion
Unfortunately, the future does not look particularly bright, as the techniques used by cyber criminals will continue to evolve, and the number of malicious programs will continue to rise.
The number of new modifications of malicious programs is growing at a steady pace: there was an increase of 8% over the first half of the year alone.
The most common malicious programs are currently Trojan-Spy, Trojan-PSW, Trojan-Downloader and Backdoor: in other words, all the malicious programs used to construct botnets and stealing users’ personal data and cyber property. The most noticeable was in the number of programs which can be used to make a profit.
Using malicious programs to conduct targeted attacks is also becoming increasingly common.
In the first half of 2006, malicious users demonstrated an obvious preference for infecting victim machines using exploits via malicious users’ websites. This method is so popular because the malicious program is more or less undetectable on the user’s computer, i.e. the malicious code does not require a person to activate it.
Although the above conclusions seem grim, the situation is not all bad. If you update your antivirus databases and install software patches on a regular basis, this will help protect your machine or systems from the majority of the threats mentioned above.






















Kaspersky Security Bulletin, January – June 2006: Malware Evolution