
- Malware Evolution
- Malware for non Win32 platforms
- Internet Attacks
- Malicious programs for mobile devices
- Spam Report
This section of the half-yearly report will discuss malicious programs and the vulnerabilities in Unix-type operating systems. As Mac OS X is effectively Unix, it will also be reviewed in this section. OS X is actually of great interest to security researchers today, more so than other Unix-type operating systems.
Main Results of the First Half of the Year
On the one hand, Unix is slowly but surely winning back the market from Windows, both in terms of servers and among end users. Yet Unix is still far from attaining the kind of popularity that could stimulate the masterminds behind computer viruses to produce the same number of malicious programs that have been made for Win32. OS X may prove to be the channel through which more and more computer users become familiar with Unix-type operating systems – and the consequence of this will be an increased number of malicious programs.
The very fact that freebsd and mach are are the heart of OS X makes it possible to implement Unix technologies.
The results from the first half of this year in terms of malware targeting Unix-type operating systems are shown in the diagram below (table 1).
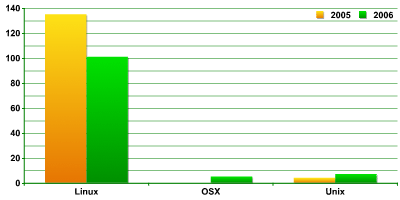 Diagram 1. Number of malicious programs for Unix-type operating systems |
The diagram demonstrates an increased interest from malware writers in OS X on the one hand, and a slight drop in other Unix-type operating systems.
Mac OS X
Even before it made its debut, Mac OS X for x86 had the undivided attention of security experts.
Interest continued to gather after Apple announced that it would be moving to popular Intel processors, which led to a more active search for vulnerabilities, both in the operating system itself and in the applications made for it. For example, the web browser Safari, which is popular among Mac users, has been identified more than once as being a vulnerable application.
Michale Lehn found a vulnerability in Safari which allows the launch of random code from a zip archive.
Fulldisclosure, an authoritative security mailing list, published examples of the code launched via the Safari vulnerability. When Safari loads a page containing the code, the user will see the SRCOD (Spinning Rainbow Cursor of Death). Safari will then crash.
It should be stressedthat other popular browsers, such as FireFox, Opera and IE have just as many problems as Safari. Vulnerabilities of varying severity are constantly being detected in all of these browsers, and some of them can even be exploited via specially written Trojans.
But Safari is far from the only application in OS X in which errors have been found. Apple has already released several updates for OS X to eliminate vulnerabilities in various applications.
Furthermore, a number of proof of concept malicious programs for OS X appeared in early February.
Leap. This is an IM-Worm for OS X which appeared in February 2006. The worm spreads via the OS X instant messaging client iChat, and sends itself to all contacts listed in the address book.
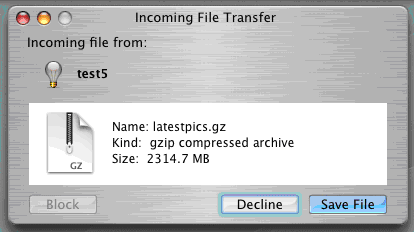 Diagram 2. A dialogue window appears as the worm spreads. |
Inqtana. This Java-based worm appeared almost at the same time as Leap. It spreads via Bluetooth and uses an old vulnerability (Bugtraq ID 13491), which was first publicized back in May 2005.
Both of these programs are proof of concept worms: their existence demonstrates that it is possible to create such a program. In future, users should expect to see these in the wild, while OS X developers will have to stay on their toes when it comes to security issues.
Linux
Now to focus on more traditional Unix systems. While the multiple vulnerabilities identified in the Linux kernel are driving developers to sound the alarms, there is a slight drop in the number of malicious programs for this operating system, which is one of the most popular of all Unix-type systems.
The appearance of yet another cross-platform virus, Virus.Multi.Bi, also deserves a mention. Attempts to create such a malicious program have already been made, and this virus is just another variation on an old theme. Other viruses such as Virus.Multi.Etapux and Virus.Multi.Pelf fall into the same category.
These three viruses (Virus.Multi.Bi, Virus.Multi.Etapux, and Virus.Multi.Pelf) are proof of concept viruses. Their chief objective is to demonstrate the ability to create programs which can infect both Linux and Win32 system.s In general, Unix is predominantly targeted by backdoor programs and a range of utilities classified as hacktools. This can be explained by the fact that compromized Unix machines are normally used as as a platform for further attacks. Once an account on a Unix machine is breached, it can be used to launch sniffers, DoSes and backdoors.
A breakdown of these malicious programs is shown in the diagram below.
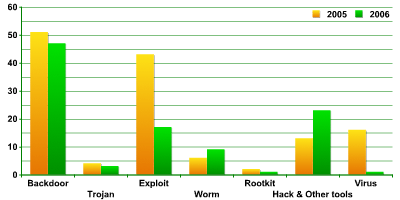 Diagram 3. A breakdown of malware aimed at Unix. |
Trends and Forecasts
The evolution of malicious programs reflect the evolution of the computer industry as a whole. This is why, when assessing the security of non-Windows operating systems, few people could realistically deny that not only is it possible to create malicious programs for non-Windows platforms, but that a number of such programs already exist. Moreover, integrating different technologies encourages malicious users to search for solutions that will work on various platforms.
The conclusions below are based on the information above, with two main areas of activity.
1. As OS X gains in popularity, the number of attacks on this operating system and on its applications will increase. If OS X accumulates a ‘critical mass,’ malicious users will become more interested in OS X machines, which will result in the appearance of OS X malware in the wild.
2. Another potential target is the 64-bit platform. On the one hand, new technologies create additional complexity, but innovation is always a source of interest to die-hard security researchers. We should expect to see malware for Unix-type operating systems for 64-bit Intel processors.
In conclusion, a small number of malicious programs in any environment does not necessarily mean that security issues should be taken lightly. Ultimately, neither Linux, nor OS X, nor any other operating system is inherently any more secure than Windows, and users should be careful to take appropriate precautions, no matter how secure they may feel.





















Kaspersky Security Bulletin, January – June 2006: Malware for non Win32 platforms