
As was predicted by many, email scams soliciting donations for Japan are appearing in user’s inboxes. We took a closer look at one of these messages and identified the following details:
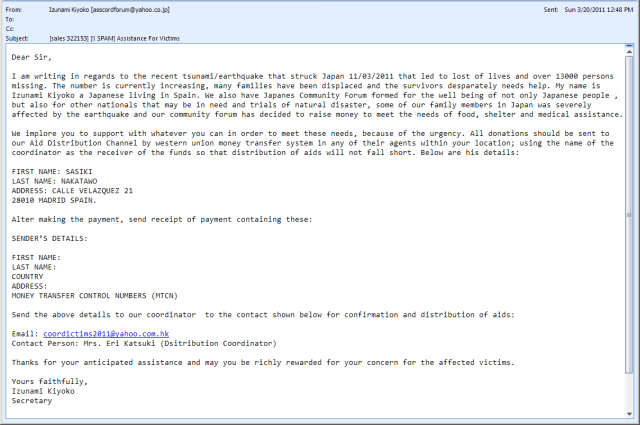
This email was apparently sent from an IP address in Canada via a mail server in Spain. The “From” and “Reply To” fields show a Japanese mail address and are most probably spoofed, while the message body mentions “Sasiki Nakatawo”, a very uncommon, if not totally fictitious name, as the recipient of funds sent by Western Union money transfers. Potential victims are then requested to send their data and Money Transfer Control Number to a mail address in Hong Kong. By the way, the character setting of the mailer used to compose the message was set to “Windows-1251” (Cyrillic).
As we can see, there are a number of different locations around the world linked to this scheme. However, Kaspersky Lab’s mail filtering products put this kind of stuff where it really belongs – the SPAM folder.






















Japan Quake Spam (II)