
The earthquake and tsunami related crisis in Japan is still far from over – so is the appearance of new cyber threats trying to exploit that same crisis.
Tens of thousands of people in Japan have lost their homes, and many their loved ones too. On top of that, radiation leaks are still a major concern for the country and its observers , while new tremors remind everyone of nature’s power on an almost daily basis. (At time of writing, a Magnitude 6.2 quake shook the place!).
Today we investigated another malicious webpage. This one states in Portuguese: “Novo tsunami atinge a regio de Sendai e Japo declara estado de emegncia em usina nuclear”, which roughly translated means “New tsunami reaches the area of Sendai, Japan declares state of emergency at nuclear power plant”.
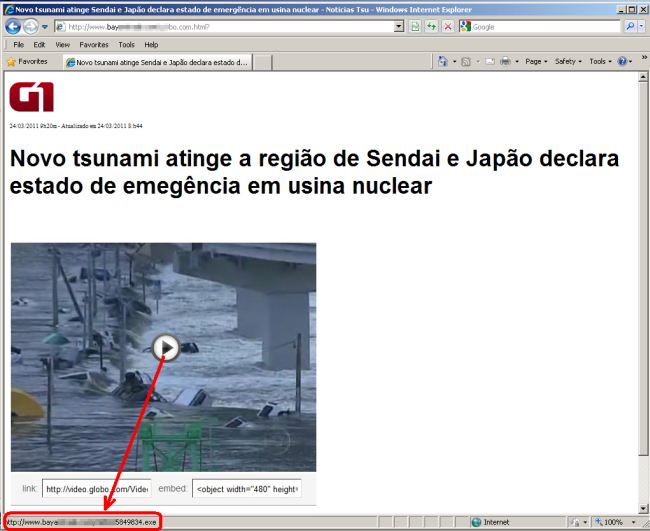
Clicking on the page content results in the download of an executable file which we detect as “Trojan-Downloader.Win32.AutoIt.po”.
When executed, three additional binaries are downloaded from a compromised site in Brazil.
After successful execution, the computer tries to connect to several locations; some are named “wab.php” and “contador.php”. Currently, we can confirm that this activity has also resulted in access to ‘www.visa.com.br’ and another location, producing ‘404’ errors because the files were hosted on – yet another – compromised site, which has apparently already been cleared of the intrusion.
Our Incident Research and Response Team have of course tried to contact the owners/ISPs of the compromised sites to draw their attention to this incident.
So far, we have received only one reply in response to our email to abuse@, but it looks to be of little help to the Internet community:
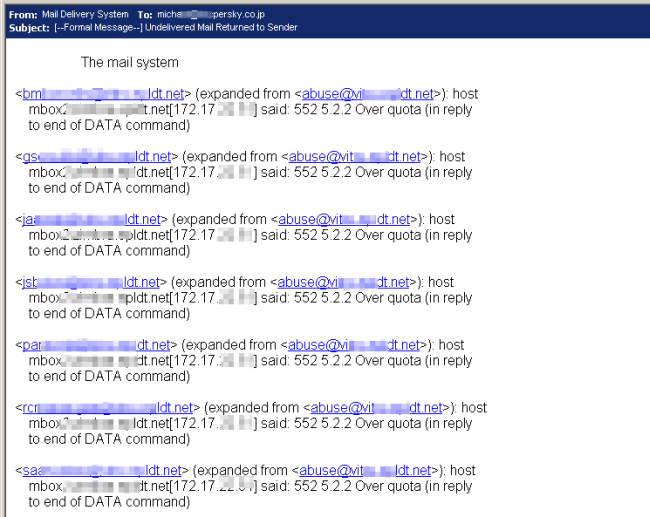
There seem to be other problems on their side and we don’t know if our alert actually reached anybody. However, users of Kaspersky Lab’s products are protected from this threat as our solutions currently detect all parts of this attack.






















Japan Quake Malware Again