
Q1 in figures
- According to KSN data, Kaspersky Lab products detected and neutralized a total of 2,205,858,791 malicious attacks on computers and mobile devices in the first quarter of 2015.
- Kaspersky Lab solutions repelled 469,220,213 attacks launched from online resources located all over the world.
- Kaspersky Lab’s web antivirus detected 28,483,783 unique malicious objects: scripts, exploits, executable files, etc.
- 93,473,068 unique URLs were recognized as malicious by web antivirus components.
- 40% of web attacks neutralized by Kaspersky Lab products were carried out using malicious web resources located in Russia.
- Kaspersky Lab’s antivirus solutions detected a total of 253,560,227 unique malicious and potentially unwanted objects.
- Kaspersky Lab mobile security products detected
- 147,835 installation packages;
- 103,072 new malicious mobile programs;
- 1,527 mobile banking Trojans.
Overview
Equation APT – the most sophisticated attacks
The story of the powerful Equation cyberespionage group was perhaps the most talked-about news story of Q1. The group has interacted with other influential groups, such as Stuxnet and Flame, for many years. Attacks carried out by Equation are arguably the most sophisticated of all: one of the group’s modules can be used to modify hard drive firmware. Since 2001, Equation has successfully infected the computers of thousands of victims in Iran, Russia, Syria, Afghanistan, the US and other countries. Its victims come from sectors such as government and diplomatic institutions, telecommunications, energy, etc.
The group uses a variety of malware, some of which is even more sophisticated than the infamous Regin platform. Known methods of dissemination and infection include using the Fanny USB worm (its arsenal included two zero-day vulnerabilities that were later used in Stuxnet), malicious installers on CDROMs, and web exploits.
Carbanak – the most successful cyber campaign
In spring 2014, Kaspersky Lab got involved in a forensic investigation: a bank’s ATMs dispensed cash without the recipient physically interacting with the ATM. This was the start of our investigation into the Carbanak campaign and an analysis of the eponymous malicious program.
Carbanak is a backdoor originally based on Carberp code. It is designed for espionage, data exfiltration and remote control of any computer infected with it. Once the attackers were inside the victim´s network, they performed a reconnaissance of that network with a view to performing lateral movement and compromising critically important systems – processing systems, accounting systems and ATMs.
Kaspersky Lab products detected a total of 2.2 bln malicious attacks in the Q1 2015
Tweet
Three methods of cashing out have been identified:
- via ATMs,
- by transferring money to cybercriminals’ accounts using the SWIFT network,
- by altering databases to create fake accounts and subsequently using mule services to collect the money.
Infections were carried out using typical APT-style methods – via spearphishing emails with documents containing exploits. The emails were constructed in such a way as to avoid raising suspicions, in some cases coming from the addresses of employees working for the company under attack.
Kaspersky Lab estimates that about 100 financial organizations, most of them in Eastern Europe, have been hit by the group, with total financial losses approaching $1 billion. This makes Carbanak by far the most successful criminal cyber campaign we have ever seen.
Desert Falcons – attacks in the Middle East
While investigating an incident in the Middle East, Kaspersky Lab experts came across the activity of a previously unknown group carrying out targeted attacks. The group was given the name Desert Falcons. It is the first Arabic speaking group seen conducting full-scale cyberespionage operations, and its work is apparently connected with the political situation in the region.
The first signs of Desert Falcons’ activity were seen in 2011 and the first known infections were carried out in 2013. The group’s activity peaked in late 2014 and early 2015. The group’s members are clearly no newbies: they developed Windows and Android malware from scratch; they also skillfully organized attacks which relied on phishing emails, fake websites and fake social network accounts.
Kaspersky Lab solutions repelled 470 mln attacks launched from online resources located all over the world
Tweet
The group’s victims are located primarily in Palestine, Egypt, Israel and Jordan. Victims include political activists and leaders, military and governmental organizations, mass media, financial institutions and other organizations. The group has currently claimed more than 3,000 victims; the attackers have succeeded in stealing over a million files and documents.
In addition to highly sophisticated and carefully planned distribution of spear phishing emails designed to infect the victims, Desert Falcons used social engineering on Facebook. The attackers created dedicated accounts to begin communicating with their intended victims, gain their trust and then use the chat facility to send each victim a malicious program disguised as an image. For infections on a bigger scale, the group used posts containing malicious links, created using compromised or fake accounts of political leaders.
Animal Farm APT
In March 2014 the French newspaper Le Monde published an article on a cyberespionage toolset identified by Communications Security Establishment Canada (CSEC). The toolset described was used in the Snowglobe operation, which targeted francophone Canadian media, as well as Greece, France, Norway and some African countries. Based on the results of their analysis, CSEC believed that the operation might have been initiated by French intelligence agencies.
In early 2015, researchers published analyses of some malicious programs (1. http://www.cyphort.com/babar-suspected-nation-state-spyware-spotlight/, 2, 3) that had much in common with Snowglobe. In particular the research identified samples that contained the internal name Babar, which was the same as the name of the program mentioned in the CSEC slides.
Kaspersky Lab’s web antivirus detected 28,5 mln unique malicious objects in the Q1 2015
Tweet
After analyzing the malicious programs used in this campaign and identifying the connections between them, Kaspersky Lab experts gave the group behind them the name Animal Farm. It was discovered that two of the three zero-day vulnerabilities found by Kaspersky Lab in 2014 and used by cybercriminals in their attacks were present in the group’s arsenal. For example, an attack from the compromised website of the Syrian Ministry of Justice using exploits for CVE-2014-0515 led to an Animal Farm tool, known as Casper, being downloaded.
A curious feature of this campaign is that NBOT – one of the malicious programs used by the group – is designed to conduct DDoS attacks. This functionality is not commonly used by typical APT groups. In addition, one of the malicious ‘animals’ has the strange name of Tafacalou – possibly, a word in Occitan, a language spoken in France and some other places.
Upatre – active distribution of the Dyre/Dyreza banker
Last quarter, the most widespread example of a banker Trojan was Upatre – a downloader for the Dyre financial malware, also known as Dyreza. This banker Trojan first appeared in 2014. It targets users from various financial organizations. It uses a technique designed to bypass SSL protection in order to steal payment information. This malware can also be used as a remote administration tool (RAT), enabling attackers to manually carry out transactions on behalf of online banking users.
The Upatre downloader is delivered to users in spam emails, many of which look like legitimate messages from financial institutions. Banks attacked by the banker Trojan Dyre, which is downloaded by Upatre, include Bank of America, Natwest, Citibank, RBS and Ulsterbank. According to researchers, the bulk of Dyre activity is currently taking place in the UK.
PoSeidon – attacks on PoS terminals
A new banker Trojan which attacks PoS terminals has been detected. PoSeidon scans a PoS system’s memory for payment information stored in plain text and sends any information it finds to the attackers.
Researchers from Cisco Security Solutions have identified three malware components that are probably associated with PoSeidon: a keylogger, a loader and a memory scraper that also has keylogging functionality. The keylogger is designed to steal credentials for the LogMeIn remote access application. It deletes encrypted LogMeIn passwords and profiles that are stored in the system registry in order to force users to type them again. The researchers believe this keylogger is potentially used to steal the remote access credentials that are needed to compromise point-of-sale systems and install PoSeidon.
In the Q1 2015 Kaspersky Lab mobile products detected 103 072 new malicious mobile programs
Tweet
Once the PoSeidon attackers get access to a PoS terminal, they install a loader. This component downloads another file called FindStr from the group’s command-and-control (C&C) servers. FindStr is used to find strings that match payment card numbers in the memory of running processes. Curiously, the malware only looks for card numbers that begin with specific digits.
Statistics
All the statistics used in this report were obtained using Kaspersky Security Network (KSN), a distributed antivirus network that works with various anti-malware protection components. The data was collected from KSN users who agreed to provide it. Millions of Kaspersky Lab product users from 213 countries and territories worldwide participate in this global exchange of information about malicious activity.
Mobile threats
Mobile malware is evolving towards monetization – with malware writers trying to render their creations capable of obtaining money and users’ bank data using a variety of techniques.
More and more SMS Trojans are being enhanced with features that enable them to attack victims’ bank accounts. An example of this is Trojan-SMS.AndroidOS.OpFake.cc, which can now attack at least 29 banking and financial applications.
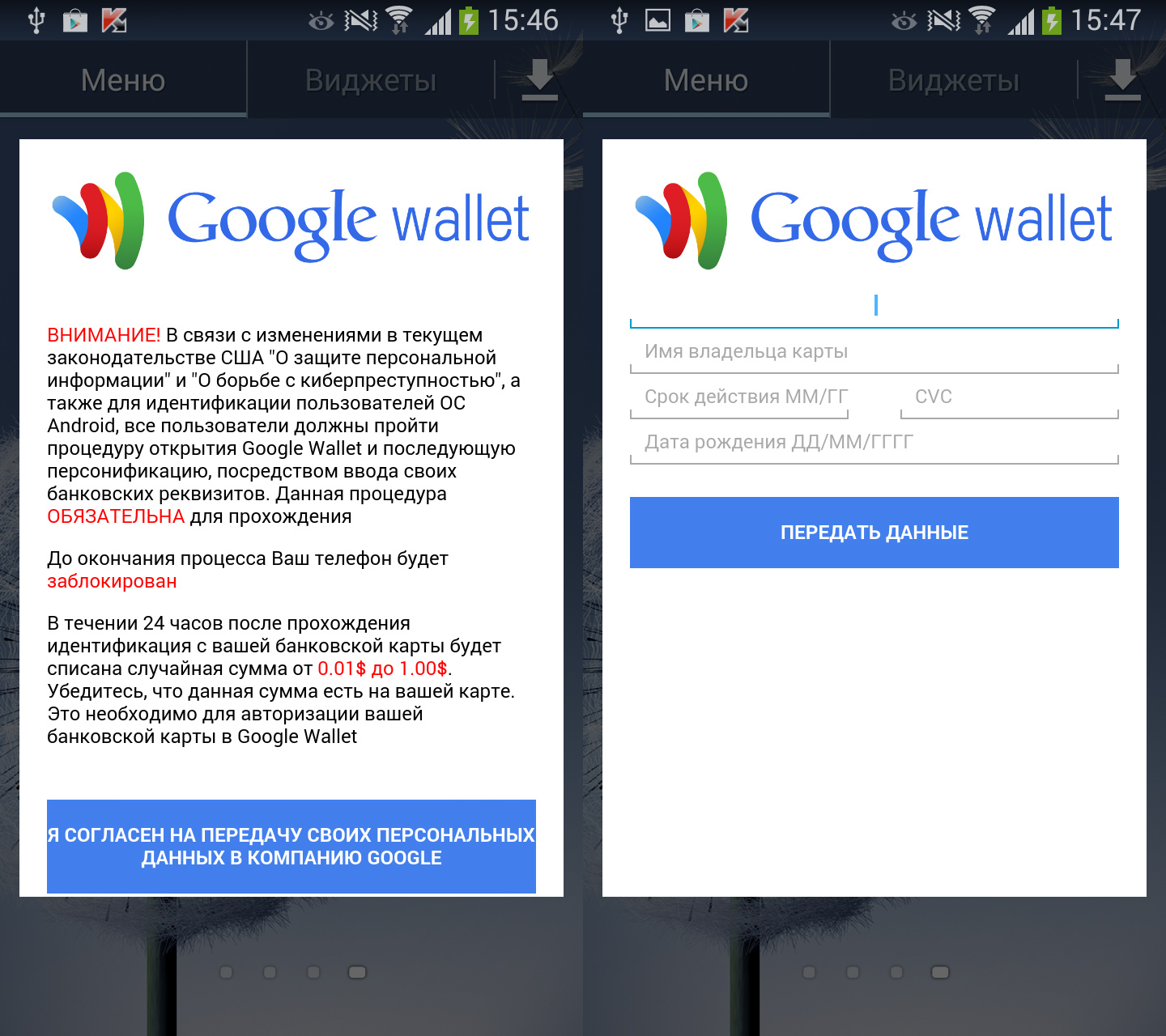
Malware writers are also beginning to build ransomware functionality into their SMS Trojans. For example, in order to obtain victims’ bank card data, Trojan-SMS.AndroidOS.FakeInst.ep uses techniques typical of ransomware programs: windows opened by the malware cannot be closed without entering the data.
What the user sees is a message, purportedly from Google, demanding that the user opens Google Wallet and goes through the ‘personification’ procedure by entering their credit card details (curiously, one of the justifications given for these actions is the need to combat cybercrime). The window cannot be removed until the victim enters credit card details.
Trojan-Spy programs, like SMS Trojans, are modified so that they can attack victims’ bank accounts. For example, Trojan-Spy.AndroidOS.SmsThief.ay is now capable of attacking five different banking and financial applications.
The upshot of this is that the mobile malware used by cybercriminals to hunt for their victims’ money is becoming increasingly versatile. Stealing money from users’ bank accounts by attacking banking applications is now something that can be done not only by dedicated Trojan-Bankers but also by some SMS Trojans and even Trojan-Spies. This may be one of the reasons why relatively few mobile banker Trojans were detected in Q1 2015.
In the Q1 2015 Kaspersky Lab mobile products detected 1,527 mobile banking Trojans
Tweet
Overall, mobile malware designed to steal or extort money from users (SMS Trojans, banker Trojans and ransomware Trojans) accounted for 23.2% of new mobile threats in Q1 2015. All three malware types are extremely dangerous and the malware writers’ interest in their victims’ money provides an incentive for their further development and evolution.
New developments from malware writers
- Trojan-Banker.AndroidOS.Binka.d, a banker Trojan, has evolved. Now it can ‘listen in’ to its victim. Sound is recorded using the device’s microphone and written to a file that is transferred to the cybercriminals’ server.
- A technique based on patching applications and embedding malicious code into them is now one of the main methods used to distribute Trojans. For example, Trojan-SMS.AndroidOS.Chyapo.a was embedded in the Unity Launcher Free app. The difference between clean and malicious applications is, in this case, manifested only by a new permission requirement – the malicious app requires access to the handling of incoming SMS messages. Another curious thing about this Trojan was that its command-and-control server was hosted on sites.google.com.
- The developers of Podec, an SMS Trojan, have mastered a new distribution technique – through the VKontakte social network. A malicious file was uploaded to the popular social network’s content storage servers. The Trojan made it into the Top Three malicious mobile programs based on the number of users attacked.
- Malware that can actively resist security solutions is not a new technology, but it is gaining in popularity. Trojan-Banker.AndroidOS.Svpeng.f, a banker Trojan first detected in Q1, tries to remove the applications of three antivirus vendors: Avast, Eset, and DrWeb.
Mobile threat statistics
In Q1 2015, Kaspersky Lab mobile security products detected 103,072 new malicious mobile programs, a 3.3 fold increase on Q4 2014.
The number of installation packages detected was 147,835 – this is 2.3 times as many as in the previous quarter.
Number of malicious installation packages
and new malicious mobile programs detected (Q3 2014 – Q1 2015)
We have lately seen the ratio of malicious installation packages to new malicious programs diminish. In Q3 2014, there was an average of 6.2 malicious installation packages per malicious program, in Q4 – there were about two installation packages per malicious program. In Q1 2015, the ratio was down to 1.4.
Distribution of mobile malware by type
Distribution of new mobile malware by type, Q1 2015
The ranking of malware objects for mobile devices for the first quarter of 2015 was headed by RiskTool (35.7%). These are legitimate applications that are potentially dangerous for the user – if used carelessly or manipulated by a cybercriminal, they could lead to financial losses.
SMS Trojans came second with 21%. As we wrote in our previous reports, in Q3 2014 the proportion of SMS Trojans to all new mobile threats fell from 22% to 14%. However, this type of malware regained lost ground by the end of 2014. In terms of growth rate, it is in third place: in Q1 2015 the total number of SMS Trojans in our collection increased by 18.7%.
Third place in the rankings was taken by potentially unwanted advertising apps (15.2%). The number of such applications in the overall stream of new mobile threats is gradually declining.
The share of banker Trojans among all the mobile malware first detected in Q1 has significantly declined compared to previous quarters and was down to 1.1%. The number of new mobile bankers in our collection grew by 6.5% during the quarter.
One other thing worth noting is that Trojan-Ransom malware, which has not been in the cybercriminals’ arsenal for very long, demonstrated the highest growth rate of all mobile threats. The number of new samples detected in Q1 was 1,113, resulting in a 65% increase in the number of mobile ransomware samples in our collection. This is a dangerous trend: since malware of this type is designed to extort money, it can damage personal data and block infected devices.
Another type of mobile threat which is showing a high growth rate is spyware (Trojan-Spy). The number of such programs in our collection increased by 35% in the first quarter of 2015.
Top 20 malicious mobile programs
| Name | % of attacks * | |
| 1 | DangerousObject.Multi.Generic | 10.90% |
| 2 | AdWare.AndroidOS.Viser.a | 9.20% |
| 3 | Trojan-SMS.AndroidOS.Podec.a | 7.92% |
| 4 | RiskTool.AndroidOS.MimobSMS.a | 7.82% |
| 5 | Trojan-SMS.AndroidOS.OpFake.a | 6.44% |
| 6 | Trojan.AndroidOS.Mobtes.b | 6.09% |
| 7 | Adware.AndroidOS.MobiDash.a | 5.96% |
| 8 | Exploit.AndroidOS.Lotoor.be | 4.84% |
| 9 | RiskTool.AndroidOS.SMSreg.gc | 4.42% |
| 10 | AdWare.AndroidOS.Xynyin.a | 3.31% |
| 11 | AdWare.AndroidOS.Ganlet.a | 2.63% |
| 12 | Exploit.AndroidOS.Lotoor.a | 2.19% |
| 13 | AdWare.AndroidOS.Dowgin.l | 2.16% |
| 14 | Trojan-SMS.AndroidOS.Stealer.a | 2.08% |
| 15 | AdWare.AndroidOS.Kirko.a | 2.04% |
| 16 | Trojan.AndroidOS.Rootnik.a | 1.82% |
| 17 | Trojan.AndroidOS.Pawen.a | 1.81% |
| 18 | Trojan-SMS.AndroidOS.Gudex.f | 1.75% |
| 19 | RiskTool.AndroidOS.SMSreg.dd | 1.69% |
| 20 | AdWare.AndroidOS.Kemoge.a | 1.52% |
* Percentage of users attacked by the malware in question, relative to all users attacked
The top position in the rankings was occupied by DangerousObject.Multi.Generic (10.90%). This is how new malicious applications are detected by Kaspersky Security Network cloud technologies, which help our products to significantly shorten the response time to new and unknown threats.
Potentially unwanted advertising applications accounted for seven positions in the rankings, including second place, which was taken by AdWare.AndroidOS.Viser.a (9.2%).
SMS Trojans continue to lose ground in the Top 20 ranking of mobile threats: while in Q4 2014 they had nine positions in the rankings, in Q1 2015 they only had four.
Nevertheless, Trojan-SMS.AndroidOS.Podec.a (7.92%) has been among the Top Three malicious mobile programs for two quarters in a row due to its active dissemination. As we mentioned above, the malware was uploaded to the file storage servers of VKontakte, Russia’s largest social network. On top of everything else, this Trojan is known to use the most powerful commercial obfuscator available today.
RiskTool malware occupied six positions in the Top 20, with RiskTool.AndroidOS.MimobSMS.a (7.82% of users attacked) ranking fourth.
Mobile banker Trojans
In Q1 2015, we detected 1,527 mobile banker Trojans –a 4.4 fold decline on the previous quarter.
Number of mobile banker Trojans detected (Q1 2014 – Q1 2015)
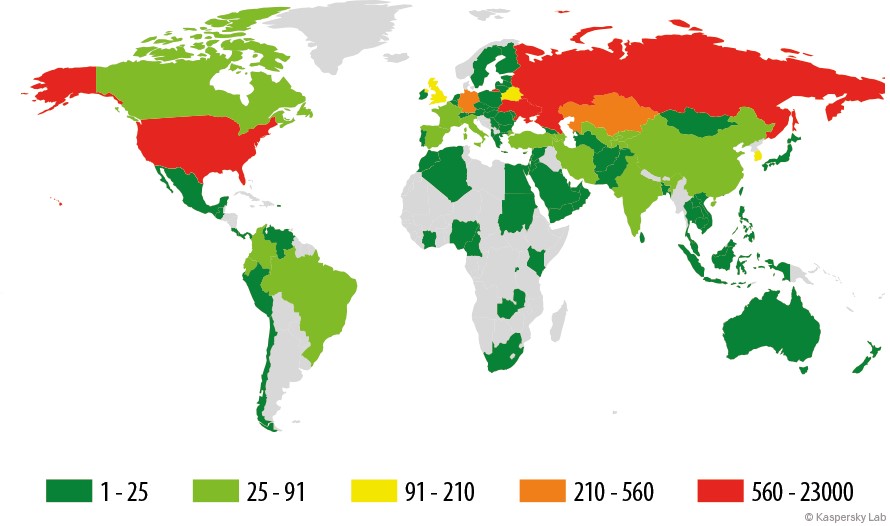
Geography of mobile banking threats in Q1 2015
(number of users attacked)
96% of attacks involving mobile banker Trojans were against users located in 10 countries.
Top 10 counties attacked by mobile banker Trojans:
| Country | % of all attacks* | |
| 1 | Russia | 86.66% |
| 2 | Ukraine | 2.27% |
| 3 | US | 2.21% |
| 4 | Kazakhstan | 1.87% |
| 5 | Germany | 0.97% |
| 6 | Republic of Korea | 0.70% |
| 7 | Belarus | 0.64% |
| 8 | UK | 0.37% |
| 9 | Uzbekistan | 0.34% |
| 10 | India | 0.21% |
* Percentage of users attacked per country, relative to all users attacked
Russia retained its traditional top position in the rankings. Ukraine moved up to second place, pushing the US and Kazakhstan down to the third and fourth positions, respectively. Belarus moved two notches down to seventh place.
The geography of mobile threats
In Q1 2015, mobile malicious attacks were detected at least once in 213 countries.
The geography of mobile malware infection attempts in Q1 2015
(percentage of all users attacked)
Top 10 countries attacked by mobile malware:
| Country | % of attacks* | |
| 1 | Russia | 41.92% |
| 2 | India | 7.55% |
| 3 | Germany | 4.37% |
| 4 | Brazil | 3.20% |
| 5 | Iran | 3.12% |
| 6 | Kazakhstan | 2.88% |
| 7 | US | 2.84% |
| 8 | Ukraine | 2.53% |
| 9 | Malaysia | 2.05% |
| 10 | Vietnam | 1.87% |
*Percentage of users attacked per country, relative to all users attacked
Russia (42%) remained at the top of this ranking, with the other countries lagging far behind. India (7.5%) was in second place.
Vulnerable applications exploited by cybercriminals
The ranking of vulnerable applications below is based on information about the exploits blocked by our products. These exploits were used by cybercriminals in Internet attacks and in attempts to compromise local applications, including those installed on mobile devices.
Distribution of exploits used in attacks by type of application attacked, Q1 2015
The top position in the Q1 2015 rankings was occupied by the Browsers category (64%), which includes exploits targeting Internet Explorer. This category was also at the top of the rankings in the last three quarters of 2014.
In Q1, we saw a significant fall in the number of exploits for Oracle Java (down seven percentage points (p.p.) from Q4 2014). This can be explained by the fact that exploits for these applications were almost completely removed from all exploit packs.
It is worth mentioning the growing number of exploits for Microsoft Office (up two p.p. from Q4 2014) and Adobe Flash Player (up by one p.p.) in Q1 2015.
The increase in the number of malicious flash objects was primarily due to the large number of vulnerabilities discovered in the first quarter of 2015. Virtually all exploit packs now include exploits for Adobe Flash Player vulnerabilities.
Online threats (Web-based attacks)
The statistics in this section were derived from web antivirus components that protect users from attempts to download malicious objects from a malicious/infected website. Malicious websites are created deliberately by malicious users; infected sites include those with user-contributed content (such as forums), as well as compromised legitimate resources.
Online threats in the banking sector
In the first quarter of 2015, Kaspersky Lab solutions blocked attempts to launch malware capable of stealing money via online banking on the computers of 929,082 users. This figure represents a 64.3% increase compared to the previous quarter (565,515).
Number of computers attacked by financial malware (Q1 2015)
Attacks using financial malware are on the rise. Note that there was a sharp increase in the number of such attacks in March 2015.
A total of 5,106,804 notifications of malicious activity by programs designed to steal money via online access to bank accounts were registered by Kaspersky Lab security solutions in Q1 2015.
Geography of attacks
Geography of banking malware attacks (Q1 2014)
Top 10 countries by the number of users attacked
| Countries | Number of users attacked | |
| 1 | Brazil | 91,893 |
| 2 | Russia | 85,828 |
| 3 | US | 66,699 |
| 4 | Germany | 51,670 |
| 5 | UK | 25,269 |
| 6 | India | 22,085 |
| 7 | Turkey | 21,397 |
| 8 | Australia | 18,997 |
| 9 | Italy | 17,663 |
| 10 | Spain | 17,416 |
Brazil continued to lead the ranking of countries most affected by banking malware, with the number of attacks increasing by 15% compared to the previous quarter (79,845).
The Top 10 banking malware families
The table below shows the top 10 programs most commonly used to attack online banking users in Q1 2015, based on the number of users attacked:
| Name | Number of notifications | Number of users attacked |
| Trojan-Downloader.Win32.Upatre | 3,127,365 | 349,574 |
| Trojan-Spy.Win32.Zbot | 865,873 | 182,966 |
| Trojan-Banker.Win32.ChePro | 355,735 | 91,809 |
| Trojan-Banker.Win32.Banbra | 35,182 | 16,363 |
| Trojan.Win32.Tinba | 94,972 | 15,719 |
| Trojan-Banker.Win32.Agent | 44,640 | 12,893 |
| Trojan-Banker.Win32.Shiotob | 60,868 | 12,283 |
| Trojan-Banker.Win32.Banker | 39,728 | 12,110 |
| Trojan-Spy.Win32.SpyEyes | 57,418 | 9,168 |
| Backdoor.Win32.Papras | 56,273 | 3,062 |
The vast majority of malicious programs in the Top 10 ranking use a technique based on injecting arbitrary HTML code into the web page displayed by the browser and intercepting payment credentials entered by the user in original and injected web forms.
In the first quarter of 2015, Zeus (Trojan-Spy.Win32.Zbot), which in 2014 was the most popular malicious program in this category, gave up its top position to Trojan-Downloader.Win32.Upatre. Malicious programs in this family are relatively simple and no larger than 3.5 KB. They usually download a Trojan-Banker belonging to a family known as Dyre/Dyzap/Dyreza. The list of financial institutions attacked by the banker Trojan depends on the configuration file that is downloaded from the command-and-control center.
The third specimen in the banker Trojan Top Three is Trojan-Banker.Win32.ChePro. This malware spreads via spam emails with online banking-related subject strings (e.g., messages can have “Invoice for online banking” as their subject). A word document with an embedded image is attached to such messages; upon clicking on the image, malicious code is executed.
Financial threats
Financial threats are not limited to banker malware that attacks online banking customers.
Financial malware: distribution by malware type
The second most widespread financial threat in Q1 2015 was Bitcoin wallet theft. Another cryptocurrency-related threat was Bitcoin mining, i.e., using victims’ computers to generate Bitcoins.
Top 20 malicious objects detected online
In the first quarter of 2015, Kaspersky Lab’s web antivirus detected 28,483,783 unique malicious objects: scripts, exploits, executable files, etc.
We identified the 20 most active malicious objects involved in online attacks against users’ computers. These 20 accounted for 95.9% of all attacks on the Internet.
Top 20 malicious objects detected online
| Name* | % of all attacks** | |
| 1 | Malicious URL | 37.55% |
| 2 | AdWare.JS.Agent.bg | 36.06% |
| 3 | AdWare.Script.Generic | 6.58% |
| 4 | Trojan.Script.Iframer | 4.49% |
| 5 | AdWare.NSIS.AnProt.b | 3.83% |
| 6 | Trojan.Script.Generic | 2.91% |
| 7 | AdWare.JS.Agent.an | 1.06% |
| 8 | AdWare.Win32.Yotoon.bfm | 0.81% |
| 9 | Trojan.JS.Redirector.ads | 0.47% |
| 10 | Exploit.Script.Blocker | 0.33% |
| 11 | AdWare.Win32.Eorezo.eod | 0.31% |
| 12 | Trojan.Win32.Generic | 0.24% |
| 13 | Trojan-Downloader.Win32.Generic | 0.22% |
| 14 | AdWare.Win32.ConvertAd.vo | 0.17% |
| 15 | Trojan-Downloader.Script.Generic | 0.16% |
| 16 | AdWare.NSIS.Agent.bx | 0.16% |
| 17 | AdWare.NSIS.Agent.cv | 0.13% |
| 18 | AdWare.AndroidOS.Xynyin.a | 0.13% |
| 19 | AdWare.Win32.Yotoon.heur | 0.12% |
| 20 | AdWare.Win32.SoftPulse.xvm | 0.12% |
*These statistics represent the detection verdicts of the web antivirus module. Information was provided by users of Kaspersky Lab products who consented to share their local statistical data.
**The percentage of all web attacks recorded on the computers of unique users.
The Top 20 is largely made up of objects used in drive-by attacks, as well as adware programs. 37.55% of all verdicts fell on links that are included in denylists.
Top 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of online resources that were used in attacks and blocked by antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command-and-control centers, etc.). Any unique host could be the source of one or more web attacks.
In order to determine the geographical source of web-based attacks, domain names were matched up against the actual domain IP addresses, and then the geographical locations of specific IP addresses (GEOIP) were established.
In Q1 2015, Kaspersky Lab solutions blocked 469,220,213 attacks launched from web resources located in various countries around the world. 90% of notifications on blocked web attacks were triggered by attacks coming from web resources located in 10 countries.
Distribution of web attack sources by country, Q1 2015
This Top 10 ranking typically remains unchanged for extended periods of time. However, Q1 2015 saw a change of leader. The top position is now occupied by Russia (with almost 40%), which rose from fourth position. The US, which headed the ranking in the previous quarter, is now in second position with 18%.
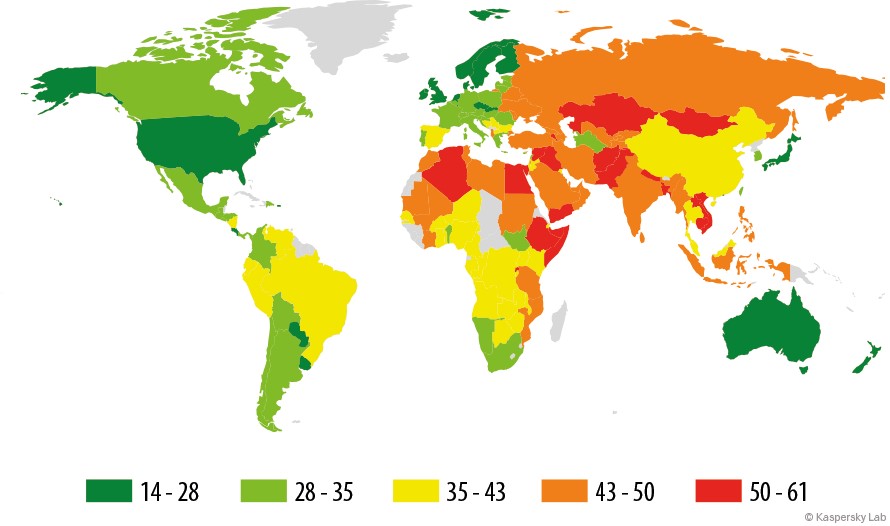
Countries where users faced the greatest risk of online infection
In order to assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users in each country who encountered detection verdicts on their machines during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers work in different countries.
| Country* | % of unique users attacked ** | |
| 1 | Kazakhstan | 42.37% |
| 2 | Russia | 41.48% |
| 3 | Azerbaijan | 38.43% |
| 4 | Ukraine | 37.03% |
| 5 | Croatia | 37.00% |
| 6 | Armenia | 35.74% |
| 7 | Mongolia | 33.54% |
| 8 | Moldova | 33.47% |
| 9 | Belarus | 33.36% |
| 10 | Kyrgyzstan | 32.20% |
| 11 | Algeria | 32.12% |
| 12 | Qatar | 31.15% |
| 13 | Georgia | 30.69% |
| 14 | UAE | 29.36% |
| 15 | Latvia | 28.69% |
| 16 | Tajikistan | 28.36% |
| 17 | Bosnia and Herzegovina | 28.00% |
| 18 | Greece | 27.55% |
| 19 | Tunisia | 27,54% |
| 20 | Bulgaria | 27,44% |
These statistics are based on the detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
*These calculations excluded countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
**Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In the first quarter of 2015, the top position in the rankings was occupied by Kazakhstan, which pushed Russia down to second place. Since the previous quarter, Vietnam and Portugal have left the Top 20. The rankings’ newcomers were Bosnia and Herzegovina (28.00%) and Greece (27.55%), which were in 17th and 18th positions, respectively.
The countries with the safest online surfing environments included Japan (12.4%), Denmark (12.7%), Singapore (14.3%), Finland (14.9%), South Africa (14.8%) and the Netherlands (15.2%).
On average, 26.3% of computers connected to the Internet globally were subjected to at least one web attack during the three months.
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems using means other than the Internet, email, or network ports.
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q1 2015, Kaspersky Lab’s file antivirus modules detected 253,560,227 unique malicious and potentially unwanted objects.
Top 20 malicious objects detected on user computers
| Name* | % of unique users attacked ** | |
| 1 | DangerousObject.Multi.Generic | 22.56% |
| 2 | Trojan.WinLNK.StartPage.gena | 17.05% |
| 3 | Trojan.Win32.Generic | 15.06% |
| 4 | AdWare.Script.Generic | 6.12% |
| 5 | WebToolbar.Win32.Agent.azm | 4.49% |
| 6 | WebToolbar.JS.Condonit.a | 4.20% |
| 7 | AdWare.Win32.Agent.heur | 4.15% |
| 8 | RiskTool.Win32.BackupMyPC.a | 3.83% |
| 9 | Downloader.Win32.Agent.bxib | 3.74% |
| 10 | Trojan.Win32.AutoRun.gen | 3.70% |
| 11 | Trojan.VBS.Agent.ue | 3.64% |
| 12 | Downloader.Win32.MediaGet.elo | 3.42% |
| 13 | AdWare.Win32.SearchProtect.ky | 3.34% |
| 14 | Worm.VBS.Dinihou.r | 3.31% |
| 15 | Virus.Win32.Sality.gen | 3.18% |
| 16 | AdWare.Win32.DealPly.brj | 2.86% |
| 17 | Trojan.Script.Generic | 2.74% |
| 18 | AdWare.Win32.NewNext.a | 2.70% |
| 19 | WebToolbar.JS.CroRi.b | 2.66% |
| 20 | AdWare.MSIL.Kranet.heur | 2.49% |
*These statistics are compiled from malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who have consented to submit their statistical data.
**The proportion of individual users on whose computers the antivirus module detected these objects as a percentage of all individual users of Kaspersky Lab products on whose computers a file antivirus detection was triggered.
This ranking usually includes verdicts issued to adware programs and their components (such as Trojan.VBS.Agent.ue,). In Q1 2015, such verdicts occupied thirteen places in the Top 20.
A newcomer to the rankings, Trojan.WinLNK.StartPage.gena, jumped straight into second position. This is a verdict given to LNK files containing a browser link which specifies the page to be opened. These pages usually have names similar to those of Internet search engines, but they actually redirect users to sites with questionable content. Some of these sites can be dangerous and are even detected by antivirus solutions. Detections of such LNK files peaked in January.
The only virus in the rankings – Virus.Win32.Sality.gen – continues to lose ground. The proportion of user machines infected by this virus has been diminishing for a long time. In Q1 2015, Sality was in 15th place with 3.18%.
Countries where users faced the highest risk of local infection
For each of the countries, we calculated the percentage of Kaspersky Lab product users on whose computers the file antivirus had been triggered during the quarter. These statistics reflect the level of personal computer infection in different countries.
Top 20 countries with the highest levels of computer infection
| Country* | % of unique users ** | |
| 1 | Vietnam | 60.68% |
| 2 | Bangladesh | 60.20% |
| 3 | Mongolia | 57.28% |
| 4 | Yemen | 55.91% |
| 5 | Somalia | 55.64% |
| 6 | Nepal | 55.01% |
| 7 | Afghanistan | 54.91% |
| 8 | Algeria | 54.83% |
| 9 | Iraq | 54.38% |
| 10 | Cambodia | 52.70% |
| 11 | Laos | 52.54% |
| 12 | Armenia | 52.44% |
| 13 | Pakistan | 51.95% |
| 14 | Kazakhstan | 51.54% |
| 15 | Ruanda | 51.36% |
| 16 | Ethiopia | 50.93% |
| 17 | Egypt | 50.60% |
| 18 | Syria | 50.11% |
| 19 | India | 50.00% |
| 20 | Tajikistan | 49.80% |
These statistics are based on the detection verdicts returned by OAS and ODS antivirus modules, received from users of Kaspersky Lab products who have consented to provide their statistical data. The data includes detections of malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives.
* These calculations excluded countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
**The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
For a long time, countries in Africa, the Middle East and South-East Asia took all the positions in this ranking. However, in Q1 2015, the rankings had such newcomers as Armenia (12th position), Kazakhstan (14th position) and Tajikistan (20th position).
Vietnam (60.68%) has headed the rankings for almost two years, while Bangladesh (60.2%) and Mongolia (57.3%) have kept their positions for the third quarter in a row.
In Russia, local threats in Q1 2015 were detected on computers of 49.6% of users.
The safest countries in terms of local infection risks were: Japan (14.7%), Denmark (20.1%), Sweden (21.4%), Hong Kong (21.5%), and Finland (21.6%).
An average of 39.8% of computers globally faced at least one local threat during Q1 2015, which is two p.p. more than in Q4 2014.
IT threat evolution in Q1 2015



























markhong
Why do not spam related information?
Vytautas
Thanks for the report but, something seems missing. The report seems very “consumer” or public user oriented (emphasis on banking, mobile phones.). Perhaps this is because you were limited to data obtained from your AV products? What about threats to industrial control systems or the manufacturing sectors? Last December we heard about Sandworm that was looking for locations of control systems made by Siemens and General Electric (HMI was targetted). German Fed Govt’s IT security department BSI issued a report (just before Christmas last year) about a cyber intrusion at a steel plant which caused physical damage. When one reads your report it seems that these other matters do not exist. Will you also prepare a separate report about cyber-malware threats to sectors of critical infrastrcuture