
Overview
The third quarter of 2010 turned out to be more eventful than the preceding quarter. Over 600 million attempts to infect users’ computers with malicious and potentially unwanted programs were blocked during this period; an increase of 10% on the second quarter of this year. Out of all of the objects detected, over 534million were malicious programs. There was an emergence of ultra- sophisticated malware in this quarter too. This was the first time we have seen malware which used not one, but five vulnerabilities at once to penetrate a system. It seems that the design specification for this malware included a self-protection mechanism that radically increased the likelihood of it being able to infect the target.
Malware writers have been actively investigating anti-hacker technologies, which resulted in new methods for evading protection being discovered. This has led to an escalation in the arms race between the cybercriminals and the IT security companies, causing the antivirus industry to actively create and develop new technologies for detection and disinfection in order to balance the threat.
In turn, this has increased competition in the underground segments traditionally targeted by cybercriminals which has subsequently diminished their profits and pushed ‘professionals’ to search for new sources of illegal income. It seems that the cybercriminal community are gradually shifting their focus towards targeted attacks on organizations. These attacks are designed to disrupt the work of an organization for the purposes of blackmail and industrial espionage – anything which will bring significant profits for those conducting the attacks.
Cyber-hooligans, cyber-blackmailers, cyber-spies – what’s next?
One of the most significant events of the quarter for the IT security industry could have come straight out of a scene from ‘Die Hard 4’: it was the Stuxnet worm attack.
The worm was first detected at the beginning of June and instantly attracted the attention of IT security specialists from around the world. There were several reasons for this. Firstly, the worm’s components included valid digital certificates. This meant that malware writers had, by nefarious means, managed to acquire private keys for digital certificates from reputable companies. Secondly, the worm used a zero-day vulnerability in LNK files in order to spread. This was apparent at first glance. However, researchers made many more interesting discoveries, including the fact that Stuxnet targeted three other zero-day vulnerabilities.
Once the worm’s code had been analysed, it became clear that it was designed to target Windows environments running very specific software, including SIMATIC, WinCC and PCS7 from Siemens AG. No malware had previous targeted such software, which is normally used to manage SCADA-based industrial control systems. Additionally, Stuxnet does not indiscriminately attack systems running WinCC. It targets only those that use Simatec programmable logic controllers and inverters from specific manufacturers.
So, what is the worm component which carries the malicious payload designed to do? It attempts to connect to WinCC using the default vendor password. The DLL file which the worm installs hooks some system functions and consequently influences operations in the management system of the industrial installation. Clearly, this malware is designed to perform industrial espionage rather than steal passwords, but theoretically, it could be used to create a diversion. Further analysis of the worm has shown that its main goal is to change the logic within Simatec PLCs embedded into inverters which are used to control the rotation speed of electric motors. These PLCs operate with very high speed motors that have limited applications, such as those in centrifuges.
Although the data obtained gives grounds for making assumptions as to the actual purpose of the attack, no solid proof exists. It should be noted that, as with the Aurora attack which we covered in the Q1 report, the attack by the Stuxnet worm is a targeted attack, even if the target still remains unclear. The question remains: ‘Why?’ The fact is that organizations which are subjected to such attacks very rarely publish information about them as it could negatively influence their reputation. According to Siemens’ official data, fifteen client systems around the world were known to have been infected at the beginning of September 2010.
The very fact that organizations rarely make information about attacks public knowledge affects the work of the antivirus companies. In order to successfully combat targeted attacks, antivirus companies need information about how the malware behaves in the system, as signature-based detection methods against such attacks are relatively ineffective. Firstly, cybercriminals can always modify the malware using encryption and obfuscation in such a way that the malware can no longer be detected by signature alone. Secondly, antivirus companies may never actually get their hands on a sample of the malware, meaning that a precise signature will never be created. It is however, impossible to hide the malware’s payload completely. Once the worm or the Trojan has reached its target, it will do exactly what it was designed to do: deliver its payload. This is when antivirus companies will be able to detect such malware through the use of behavioural analysis, the most important approach in the case of targeted attacks.
All of this indicates that the creators of Stuxnet are highly skilled. Stuxnet is a worm aimed at interfering with the operation of PLCs used within large enterprises. The worm exploits four zero-day vulnerabilities and contains a rootkit signed by certificates stolen from Realtec Semiconductors and JMicron. Further on we will discuss the details of these certificates. Such complex malware must have been designed with a significant target in mind, as large sums of money must have gone into its creation.
Digital certificates and malware
Digital certificates and signatures are the main methods used to ensure trust in the digital world. Digital signatures for executable files were first used in Windows NT: since then, Microsoft has actively promoted the use of digital signatures. A digital certificate makes it possible to confirm that a program is legitimate and to determine its source.
Naturally, whether or not a file is signed is very significant to antivirus companies. Files which are signed by a trusted vendor are, de facto, judged to be clean. This technology enables antivirus developers to not only keep the number of false positives to a minimum, but also effectively allocate resources when scanning a computer for infection.
Unfortunately, digital signatures present a whole range of problems. The certificate can be ‘cut’ from a legally signed file. Microsoft certificates are the most frequently ‘cut’. The trick is not new and is often used by virus writers. This quarter, for instance, the trick was performed by Zbot’s distributers, who ‘cut’ the certificate from a legal file and joined it to the Zbot component. At first sight, such files appear to be legitimate. However, that is just first impressions. To sign a file, its hash-sum is used, which is unique for every object. When certificates are ‘cut’ as described above, the hash-sums of the file and the signature no longer match, invalidating the certificate. This enables fake certificates to be recognized. Most commonly, the cybercriminals attempt to mislead virus analysts and users by employing the certificate from a legitimate file signed by a well-known vendor. Such tricks are not rare; therefore it is important that antivirus solutions not only check the certificate’s presence, but that it matches the file as well.
The second issue is more complex – the cybercriminals can obtain a digital certificate quite legally, as can any other software developer, for example, for officially developing ‘software for the remote management of computers without GUIs’, which is in essence, a backdoor. This kind of ‘defense’ against detection is most popular with the authors of adware, riskware and Rogue AVs. After receiving the necessary key from the certification center, the cybercriminals can sign any of their creations with little effort. However, such a scenario allows antivirus companies to discover these ‘black sheep’ quite easily, by enabling them to effectively detect all files using this certificate.
As mentioned above, digital certificates are used by most major software developers. The information necessary to create a file signature is stored on vendors’ computers connected to the Internet. Last year we saw the results of programmers’ workstations infected by the concept virus Virus.Win32.Induc, which was integrated into programs in the early stages of code linking and compilation. On the same day that this virus was detected by anti-malware tools, hundreds of legitimate programs were detected as well. The situation is even worse with regard to certificates. A closed key is in essence a file, and can therefore be stolen just like any other virtual property. The detected Stuxnet components were signed with the help of Realtec Semiconductors and JMicron certificates. It is unknown how exactly the closed key fell into the hands of the cybercriminals, but it is clear that it could have been one of several possible ways. The cybercriminals could have bought these files from insiders or stolen them using a backdoor or some other similar piece of malware. Currently, certificate theft is one of the key features of a very common Trojan: Zbot (aka ZeuS).
Legitimate signatures are one of the reasons that Stuxnet successfully escaped detection by antivirus programs for quite a long time. Malware signed by valid certificates can easily circumvent even the modern protection mechanisms built into Windows 7. Thus, when a signed malicious driver or an ActiveX component is installed on a system, no warning window appears. The growing popularity of Windows 7, which according to Net Applications statistics makes up about 16% of the market, and the gradual decline of Windows XP, will result in increased problems with digital certificates. Judging by today’s trends, this might become one of the major problems awaiting us in 2011.
TDSS – a new round of evolution. Now available in 64-bit as well
We shouldn’t forget that as well as everything that we have discussed so far, there are also other ways to evade integrated protection systems. In addition to the protective measures we have looked at, new versions of Windows have a mechanism to protect against the installation of unsigned drivers. However, the developers of Stuxnet were able to bypass the system, getting hold of well-known companies’ closed keys and signing all of the components of the rootkit. The virus writers that created the code for the TDSS Trojan, which our experts described in the second quarter of this year, took a different tack.
In August, a new version of this malicious program labeled TDL-4 was detected. The most interesting innovation is that the rootkit used to conceal the Trojan’s malicious actions can successfully run on 64-bit systems as well. The previous version, TDL-3, infected physical disk drivers, which allowed the rootkit to be downloaded immediately after the operating system launches. However, infecting drivers using such an approach results in a change of hash-sum, and consequently the digital signature does not correspond to the file anymore, which is detected by the protection tool embedded into 64-bit versions of Windows.
To evade this mechanism, the new version of TDSS infects the MBR area using technology similar to that used by the Sinowal bootkit. In this case the malicious code starts to execute even before the operating system is launched and can alter the system’s boot parameters, allowing unsigned drivers to be registered in the system. The rootkit loader determines under which system, 32-bit or 64-bit, the malicious program will be operating, writes the driver code to memory and registers it in the system. After this, the operating system containing the malicious code is booted up. The rootkit does not modify the nucleus areas, which are protected by a different PatchGuard technology integrated into the operating system.
Our forecast proved to be correct – infection and concealment technology has evidently become even more sophisticated, which in turn requires elaboration of any detection and treatment technologies for such malware. If malware and antivirus programs continue the struggle at still lower system levels, it is very probable that even the most daring of concepts for infecting BIOS’ and hypervisors will soon become an everyday reality.
Struggling with new and sophisticated malware is an arduous task for antivirus companies of any size, therefore, in addition to its main product range; Kaspersky Lab issued a new version of its free anti-rootkit utility, TDSSkiller, which among other things, detects and removes the most recent versions of TDSS. This protection utility is designed to complement Kaspersky Lab’s regular security products.
Hackers and the law
Last year we detailed the cybercriminals’ activities in the former soviet republics, where extorting money with the help of SMS-blockers has become especially popular. The scheme is very simple: the program, which is downloaded to users’ computers, prevents the operating system or the browser from working. To remove the program, the user is asked to send an SMS to a short number at the cost of anything up to one thousand rubles. In view of the huge number of victim users, Kaspersky Lab, along with several other antivirus companies, launched an unblocking service.
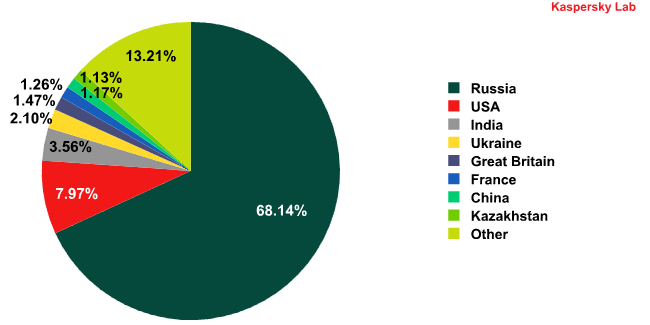
Percentage of KSN users, on whose computers samples of the most widespread
SMS-blocker families were intercepted
While antivirus vendors struggle to get to grips with the results of the cybercriminals’ illegal activities, the perpetrators themselves are being dealt with by law enforcement authorities: this quarter, a huge criminal group involved in the illegal use of SMS-blockers were arrested and detained. During late August 2010, ten people were arrested in Moscow and accused of creating SMS-blockers. According to information provided by the Russian Federation’s Ministry of Internal Affairs, the illegal profit that the gang made is estimated to be around 500million rubles.
A criminal case was initiated, but what it most important is that the accused parties will not only be tried under Article 273 of the Russian Federation Criminal Code, which is known to every hacker in Russia and which seldom results in imprisonment (“Development, use and dissemination of malicious computer programs”), but also under Article 159 (“Fraud”). The sum of 500million rubles is sufficient to be considered grand larceny, and if proved guilty, the accused might be sentenced to a far more severe punishment.
Such news cannot fail to make antivirus experts and representatives of law enforcement authorities that hunt for the cybercriminals happy. However, there is a down side to it. Last year, the organizers of an unprecedentedly large attack were arrested. They had illegally transferred over $9million from 2,100 ATMs in over 280 countries. (https://securelist.ru/amerika-xochet-vernut-9-millionov/3578/). Some members of the criminal group were detained in the USA and are currently facing up to 20 years in jail and serious fines. Now let’s see what happened to one of organizers of the attack who was tried in Russia. The investigation has shown that this person is responsible for hacking into RBS Worldpay and copying credit card numbers and PIN-codes in order to make fake credit cards.
He was convicted of grand larceny, illegal access to computer information and stealing the bank’s confidential data. But here is the most interesting thing: though guilty of all of these crimes, he was given a suspended sentence and put on probation for 4 years. It turns out that in Russia you can get away with just a suspended sentence for the crime of stealing vast sums of money via the Internet. The same is very likely to happen with those involved in the SMS-blocker case, though we hope to be proven wrong.
In the money-stealing scheme described above, a key role was played by the people involved in laundering the stolen money: the accounts were set up in their names and they were the ones who withdrew the stolen money from the ATMs. These are often called ‘money mules’, and in last quarter’s report we revealed how the cybercriminals tried to recruit such people via a group on Facebook, which was 224 thousand people strong.
By the end of September, twenty people had been arrested in the USA – these were money mules who laundered money stolen using the Zbot Trojan (ZeuS). At the same time, a group of people were arrested in Great Britain for a similar money laundering scheme in which the criminals used information stolen by ZeuS. It should be noted that during the first few days of October, the ZeuS Trojan’s distributors became less active.
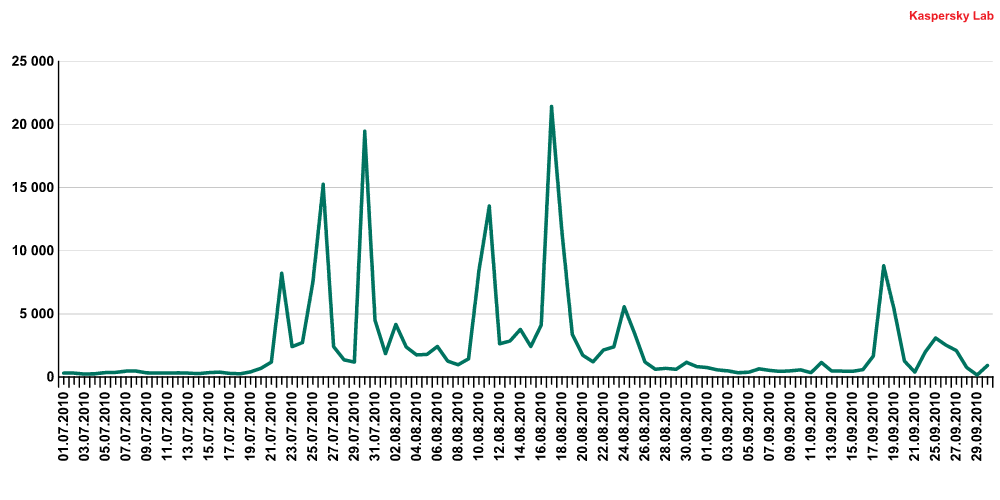
The percentage of Zbot Trojans detected daily, compared to the total volume of malware
If law enforcement authorities continue to arrest cybercriminal gangs as they have been, we will face an intriguing autumn, with many newbie hackers having to think seriously about whether to follow their chosen career path.
Statistics
Below we will look at the statistics concerning how various anti-malware components performed. All of the statistical data used in this report was collected via the distributed antivirus network Kaspersky Security Network (KSN). Information on malicious activity is continually being exchanged on a global basis by millions of users of Kaspersky Lab products located in 213 countries.
Exploits and vulnerabilities
Exploits
In the third quarter of 2010, Kaspersky Lab detected over 16.5 million exploits. This does not include modules with the functionality of exploits which were embedded inside worms and Trojan programs.
Let us examine the exploits used by the cybercriminals during the third quarter of 2010.
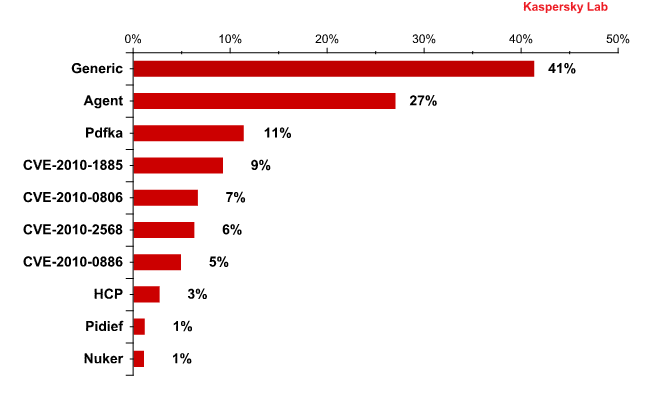
Distribution of detected OAS, WAV and MAV objects according to exploit families
The two clear leaders are the exploits detected using heuristic methods, including proactive technologies. Exploits that take advantage of vulnerabilities in different versions of Adobe Reader are in third and ninth positions, and when combined, represent 12,5% of all detected exploits. Just as we expected, the exploits for the vulnerability CVE-2010-1885 in Windows Help and Support Center have rapidly become popular with virus writers. These exploits are in 4th and 8th positions and account for 12% of all exploits. A family of exploits using the Java vulnerability CVE-2010-0886 (4,8%) also made it into the Top 10.
Exploits for the CVE-2010-2568 vulnerability in LNK-files are the most interesting. Stuxnet pioneered this group. The vulnerability was detected around the end of July and a patch was released by Microsoft on 2 August. The vulnerability enables malicious programs to be distributed quite easily via removable media, primarily USB flash-drives. Until recently, to distribute malware via flash-drives, the cybercriminals resorted to specially created autorun.inf files. Such files can be detected quite readily by current antivirus technologies.
The vulnerability in LNK-files enables executables to be launched from a flash-drive without any action on the part of the user. The cybercriminals have created a special LNK-file for this purpose, which when displayed in the file manager, e.g. in Microsoft Explorer, will run the malicious code. The computer is infected as soon as a user opens the folder to view the contents of the infected device.
After the cybercriminals got to know about this wondrous opportunity, other virus writers also started to actively use it. In particular, we recorded Sality and Zbot (ZeuS) making use of the exploit for the vulnerability in LNK-files. This quarter, 6% of KSN users faced exploit attacks via the CVE-2010-2568 vulnerability.
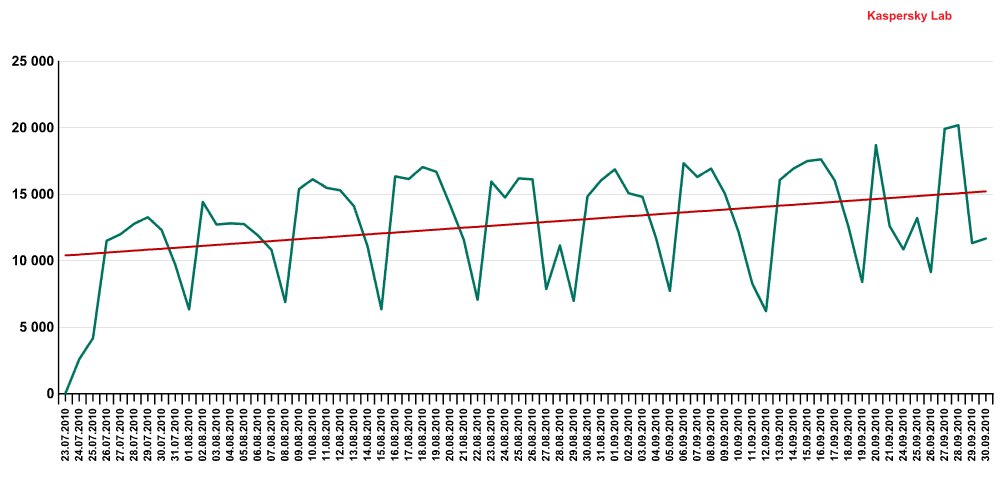
The number of detected exploits distributed on removable media
via the CVE-2010-2568 vulnerability
Vulnerabilities
In the third quarter of 2010, Kaspersky Lab detected over 31.4 million unpatched vulnerable applications and sites.
The Top 10 most common software vulnerabilities found on users’ computers are listed in the table below.
Latest PostsLatest WebinarsReportsHoneyMyte updates CoolClient and deploys multiple stealers in recent campaignsKaspersky researchers analyze updated CoolClient backdoor and new tools and scripts used in HoneyMyte (aka Mustang Panda or Bronze President) APT campaigns, including three variants of a browser data stealer. The HoneyMyte APT evolves with a kernel-mode rootkit and a ToneShell backdoorKaspersky discloses a 2025 HoneyMyte (aka Mustang Panda or Bronze President) APT campaign, which uses a kernel-mode rootkit to deliver and protect a ToneShell backdoor. Evasive Panda APT poisons DNS requests to deliver MgBotKaspersky GReAT experts analyze the Evasive Panda APT’s infection chain, including shellcode encrypted with DPAPI and RC5, as well as the MgBot implant. Cloud Atlas activity in the first half of 2025: what changedKaspersky expert describes new malicious tools employed by the Cloud Atlas APT, including implants of their signature backdoors VBShower, VBCloud, PowerShower, and CloudAtlas. |


















IT Threat Evolution for Q3-2010