
Yesterday, one of our users contacted us to tell us about the strange behaviour of his browser. He’d been looking at www.5755.ru – his browser opened a second web page, and his Web anti-virus warned him that a Trojan program was being downloaded.
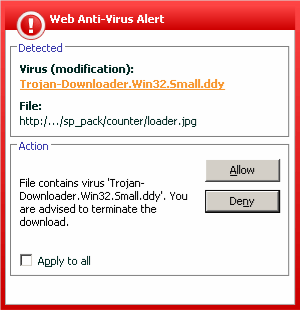
The user went to this site after he’d seen it advertized on television. He almost fell victim to a malicious attack – the site’s homepage contained a script that downloads Trojan-Downloader.JS.Psyme.ct, which in turn downloads Trojan-Downloader.Win32.Tiny.eo. Of course, the malicious programs placed on the site change from day to day, but happyily, the Web anti-virus module in Kaspersky Anti-Virus 6.0 prevented this user from getting infected.
After investigating this a bit further, it turned out that at least 470 other servers had been subject to the same hacker attack. We found this out by entering a string from the script which had been injected into the site into Google.
All these servers had one thing in common – they were all hosted by Valuehost, the biggest hosting provider in Russia, which offers a home to more than 60,000 Russian web sites. Of course, the Valuehost administrators have been informed of the problem.


















Infected Valuehost servers