
While the legal status of cryptocurrencies and laws to regulate them continue to be hammered out, scammers are busy exploiting the digital gold rush. Besides hacking cryptocurrency exchanges, exploiting smart-contract vulnerabilities, and deploying malicious miners, cybercriminals are also resorting to more traditional social-engineering methods that can reap millions of dollars. Their targets are not just the owners of cryptocurrency wallets, but basically anyone with an interest in the subject.
To understand how scammers can access victims’ money, it helps to remember how cryptocurrencies work and what it means when we talk about the address and private key of a cryptocurrency wallet.
Cryptocurrencies are based on asymmetric encryption with public and private keys. The wallet address, which anyone can transfer money to, can be generated from a public key, which in turn can be obtained from a private one. The private key is required for all wallet transactions, hence scammers’ interest in it. Note, however, that attackers are not always after the victim’s private key— the goal is often to get people to transfer funds into the scammers’ accounts all by themselves. But one thing at a time.
Classic phishing
Authentication on cryptocurrency exchanges and wallets
Cryptocurrencies are bought and sold through specialized services known, like their physical counterparts, as exchanges. They also provide crypto storage services, issuing a wallet for each currency held and storing private keys on users’ behalf. Naturally, if the scammers manage to get hold of the authentication data for a crypto exchange account, they will gain access to the user’s money. This explains the abundance of phishing pages mimicking the authorization pages of popular crypto exchanges. Such sites are usually very convincing and virtually indistinguishable from the originals, except for the URL. In the first half of the year, our security solutions prevented more than 100,000 attempts to redirect users to such resources.
Another method of stealing money is to hack the service itself and siphon off funds from user accounts. A recent example of such a heist comes from South Korea, where the country’s largest exchange Bithumb was forced to cease trading following the theft of $32 million worth of virtual coins. And at the end of last year, having had 17% of all its assets swiped by cyber thieves, another crypto exchange, Youbit, also called time on trading.
Therefore, many users prefer to keep cryptocurrencies in their “own” wallets, of which there are two types: online and offline (desktop, hardware, paper). Online wallets are no safer than the ones held on exchanges: the private key is entrusted to a third party and the owner has no control over it. Hardware crypto wallets are considered the most secure. These are physical devices that generate and internally store a non-recoverable private key for the wallet. When performing a transaction, all operations take place inside the wallet, and only the electronic signature is issued externally.

A phishing email, supposedly from the Luno team, alerting the user to suspicious activity on their account and inviting them to click on a link to secure the account
The methods used to access online wallets are indistinguishable from classic phishing techniques: scammers create pages that mimic the authentication page of the target website. Links to fake resources are most often distributed via email with typical scare stories about accounts being blocked or unusual activity on them. The hook is to persuade users that they must go through identification to prevent losing funds.
Delving deeper into phishing site scripts, it’s clear that in addition to logins and passwords, scammers also harvest information about IP addresses and user agents. Using this data, cybercriminals can get round some anti-fraud systems by using this information to masquerade as the account owner.

Example of a phishing page imitating a BLOCKCHAIN.INFO wallet, and a snippet of code generating a message with data to be sent to the scammers
Fake registration
For the wallet-less, scammers have a separate scheme that involves luring them to fake crypto wallet sites, promising all sorts of registration “bonuses,” including, for example, a sum of cryptocurrency.
The simplest phishing pages simply collect users’ personal data, and then redirect them to the real site of the service. The more dangerous ones really do open wallets for the victim using the data they specify. As a result, the victim receives a confirmation message at the email address they provided and a personal account on the real online resource, lulling them into a false sense of security. But the wallet is compromised from the start, so as soon as any money appears there, it is quickly siphoned off.
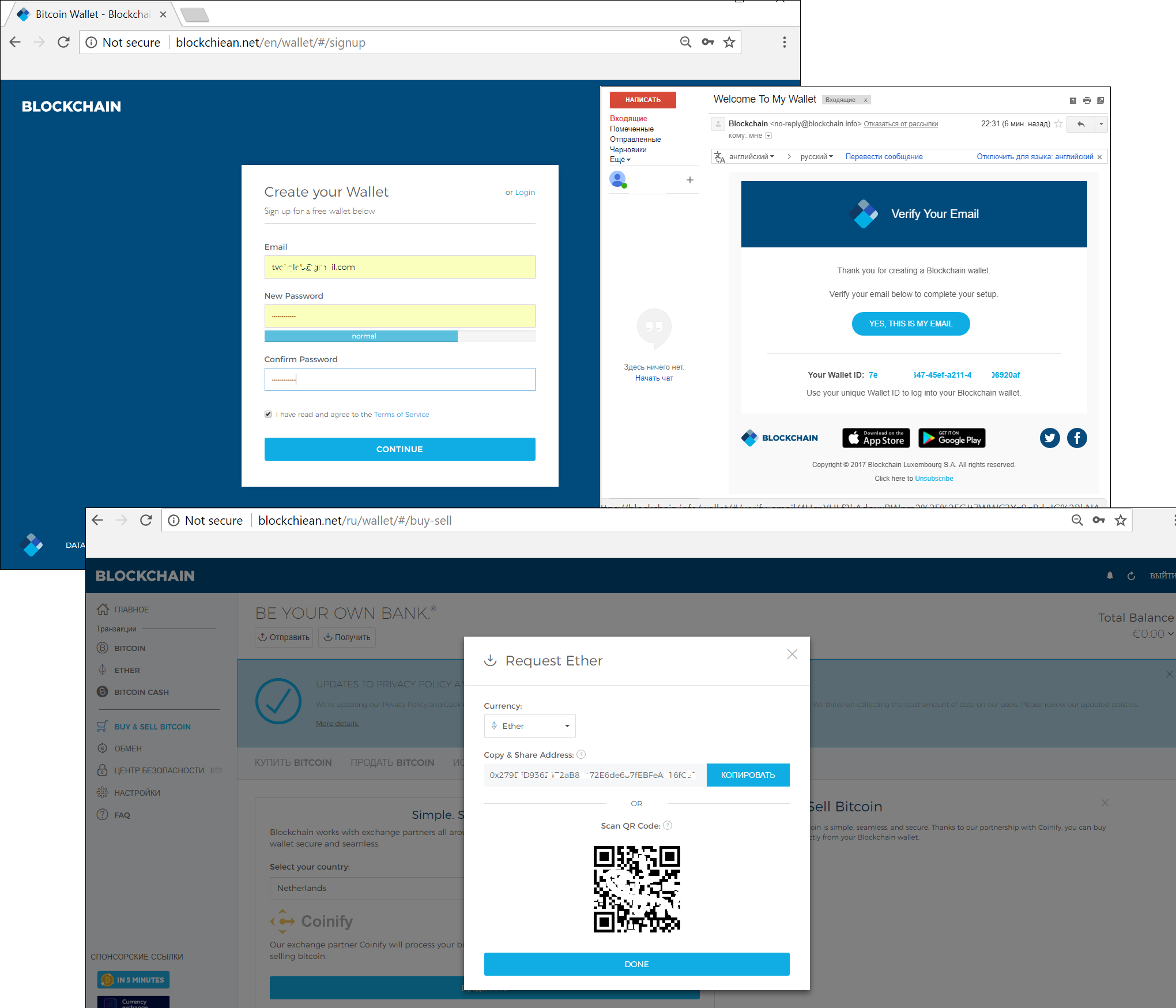
A fake BLOCKCHAIN.INFO wallet registration form, the original confirmation letter of registration, and the fake personal account that the victim is redirected to after registration
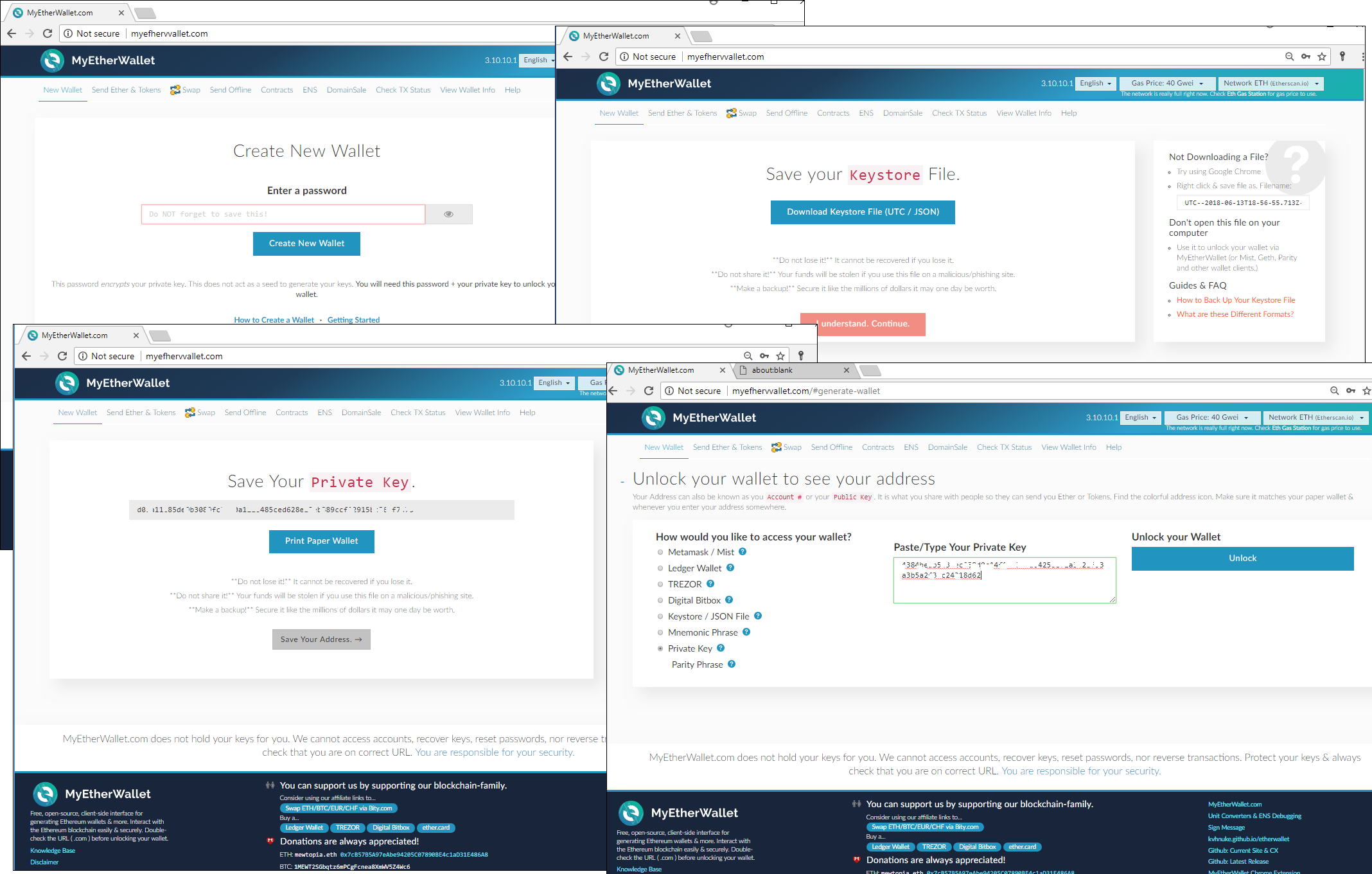
It might seem that only online wallets and exchanges are targeted by phishers, but that’s not the case. For instance, fakes of MyEtherWallet, a solution that facilitates transactions with digital coins stored on users’ local PCs, are very popular.
The registration procedure is exactly the same as the original, including downloading the Keystore file, required to access the funds. The private key, which the victim receives after such registration, is already compromised, and any money transferred to the wallet ends up in the hands of the scammers.
Fake mobile apps
Another attack vector is fake crypto storage software distributed through official app stores. Such programs often top the downloads, as in the case of a fake MyEtherWallet mobile app that became the third most popular finance app in the App Store.
This is NOT US. We have file reports and emailed and reported. Would appreciate the communities assistance in getting these scamtards out of our lives.
PS: We are #Foss4Lyfe https://t.co/SmI8cqNvxA
— MyEtherWallet | MEW (@myetherwallet) December 10, 2017
Investments
According to CoinSchedule stats for 2018, when this article went to press, 427 ICOs (initial coin offerings) had been held and funds totaling more than $10 billion raised. The huge sums, the hype, and the lack of legislative control in many countries make ICOs a natural target for scammers.
One of the most common ways to steal funds is by sending phishing emails to potential investors. When an ICO is announced, email addresses of interested persons are often collected in order to notify them, for instance, about the start of the token selling. But the database of potential investors’ details could fall into the wrong hands. In this case, shortly before the actual start date, scammers send out emails saying that sales (or a preliminary round) have already begun and containing the number of the wallet to which funds should be transferred.

The Bee Token ICO: scammers managed to get hold of the emails of potential investors and send out a perfectly timed invitation specifying an e-wallet for the transfer of Ether tokens. This wallet pocketed 123.3275 Ether (about $84,162.37). The scammers also created several phishing sites masquerading as the official platform
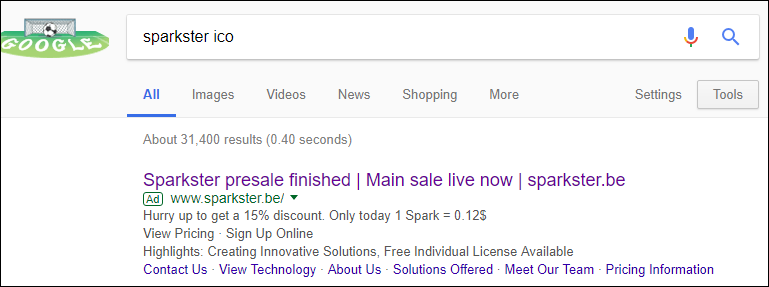
Another common method is to create fake sites that mimic official ICO projects.

Fake ICO projects: the first page is located on the domain fantom.pub and mimics fantom.foundation, the real site of the FANTOM project; the second—hosted on sparkster.be—is a fake version of sparkster.me, the website of the SPARKSTER project
Links to such resources are distributed not only by email, IM, and social networks, but through ads in major search engines.
The more popular the project, the greater the number and the higher the quality of the fakes. Telegram’s ICO currently holds the record for investments raised. We found dozens of phishing resources exploiting this event, some of which looked very professional indeed. What’s more, the wallet addresses for victims to transfer money were created individually for each “investor,” making it harder to track the funds.
Coin dispensing
Airdrop
A crypto airdrop is a way of popularizing new virtual coins that are not yet available on exchanges. Anyone can receive an “airdropped” sum of new cryptocurrency in exchange for doing something to promote the project. For example, the user may need to subscribe to a Twitter account, make a repost, or write a blogpost.
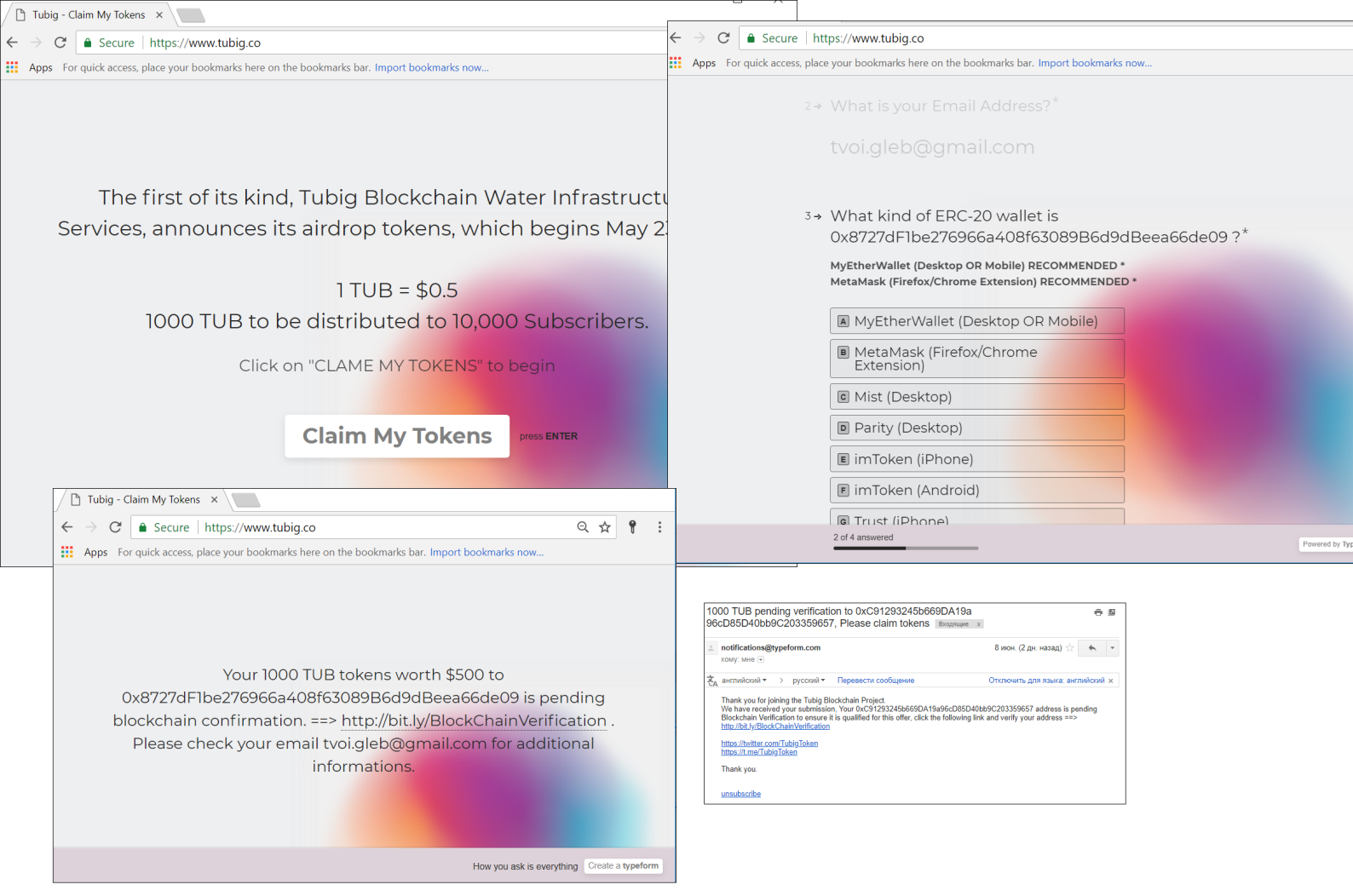
After registration, this Tubig Blockchain Water airdrop scheme steals funds through a wallet verification phishing page
Similar schemes are used by scammers to lure users to websites of non-existent airdrops. After registering on the site of a non-existent project, the victim is directed to a wallet verification phishing site where they are asked to enter their private key or other personal information that cybercriminals can use to gain access to money.

Phishing page mimicking a crypto wallet site. Note the use of an “ł” character to create a domain name barely distinguishable from the original
Ironically, victims themselves contribute to the spread of such scams by reposting information and subscribing to fake company accounts in social media.
Giveaway
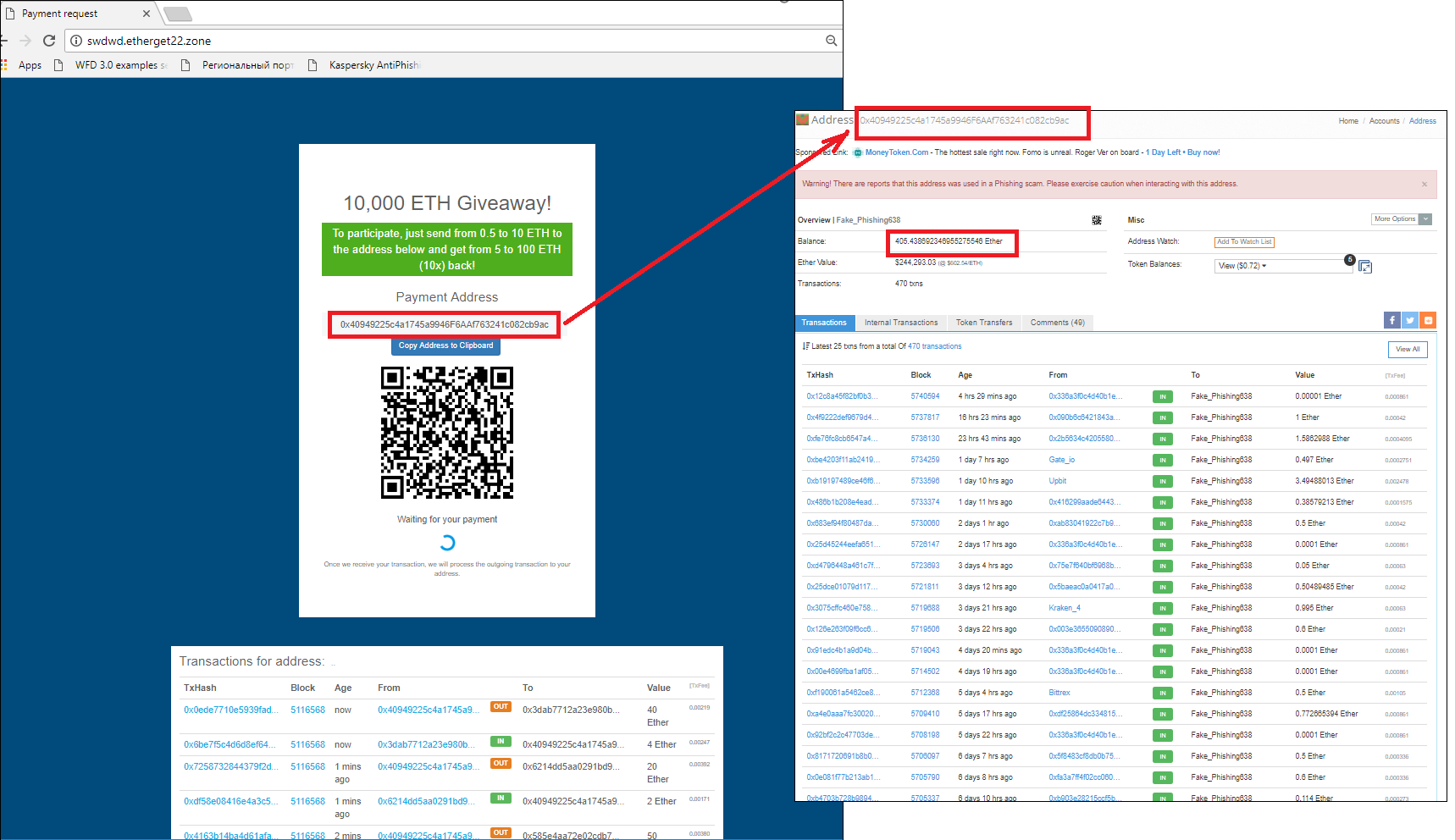
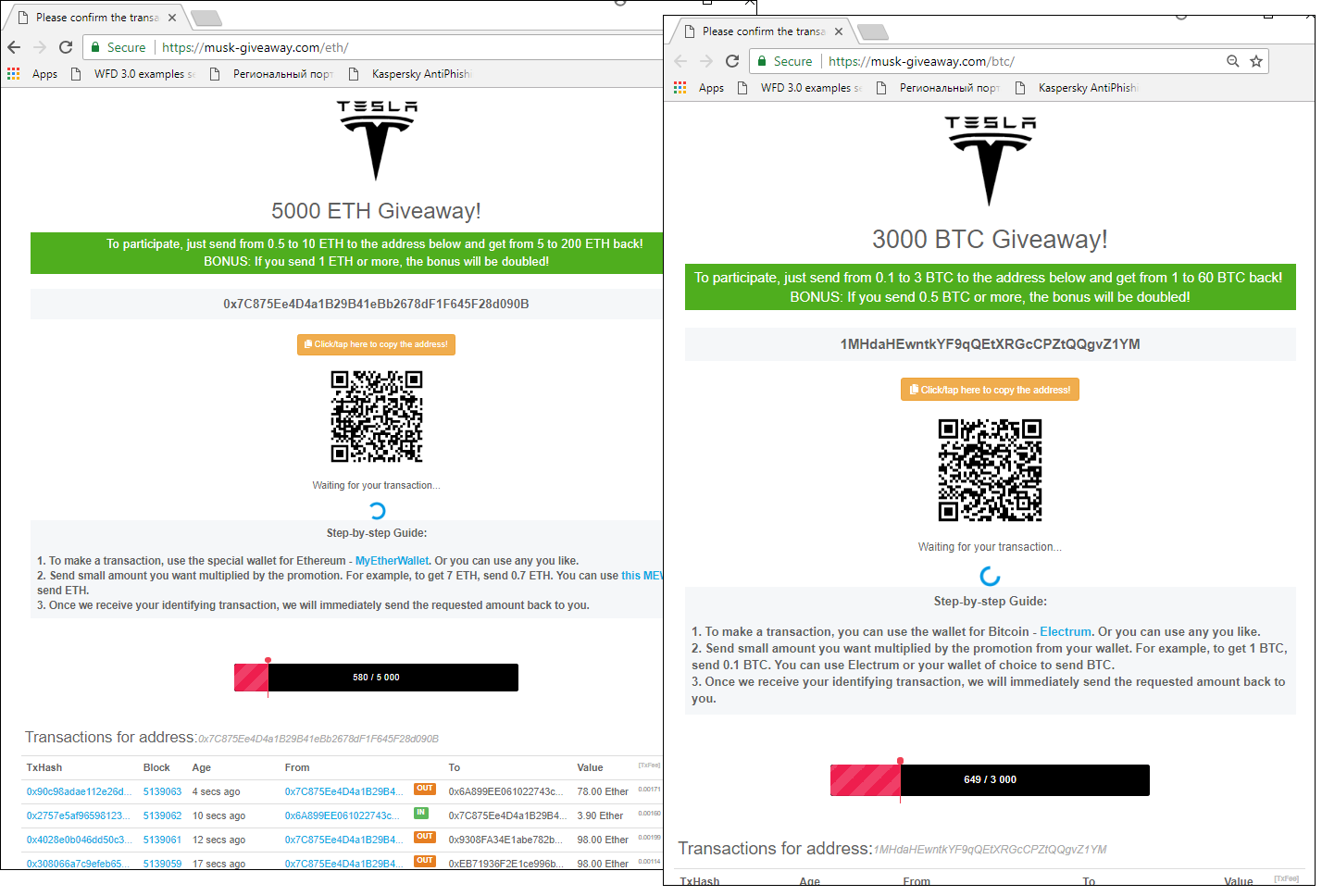
One of the most common baits is the promise of free coins under the “give a bit, get a lot” motto. The user’s initial contribution is supposedly required for wallet verification purposes. To make the cover story more convincing, a list of transactions is displayed showing how the funds of other users of the service have magically multiplied, but in fact it’s just a pretty picture.
In fact, all the transferred funds go the scammers, which is confirmed by a simple check of the transactions made with the wallet number. The scheme is simple yet there seems to be no lack of gullible users. One site alone (pictured above) received “contributions” worth 405.43 ETH, which at the current exchange rate is approximately $245,000.
Cybercriminals often mask such methods as bounty programs exploiting the names of well-known crypto wallets, exchanges, or ICOs:

A page offering coins seemingly on behalf of popular exchange Binance under the pretext of a bounty program. To receive the “reward,” users must verify their identity by transferring 0.3-5 ETH from their wallet to the one specified on the website, with the promise of a tenfold payback
Coin giveaways are sometimes announced as a thank you to users or to mark the company’s success; fake comments on the site about money received encourage victims to act rashly.
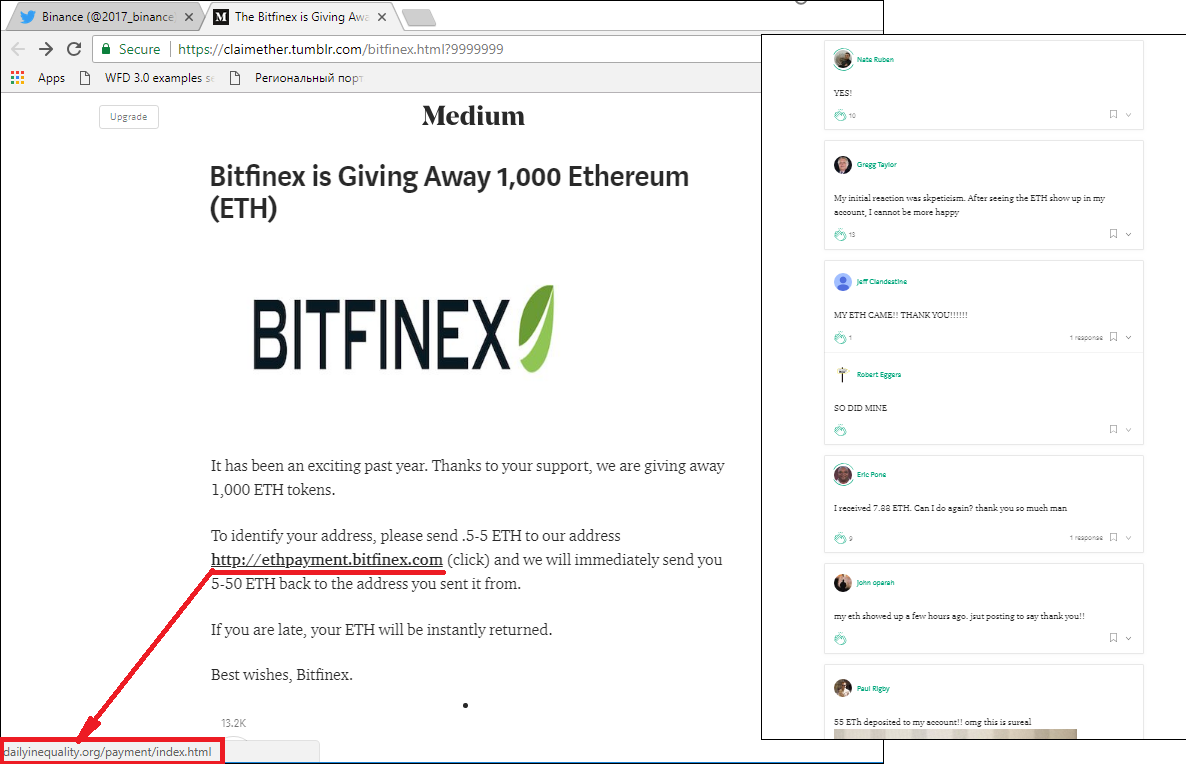
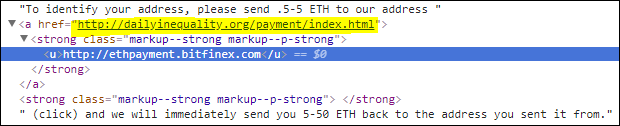
At first glance, the link in the image above points to the Bitfinex site, but the user is redirected to a phishing page:
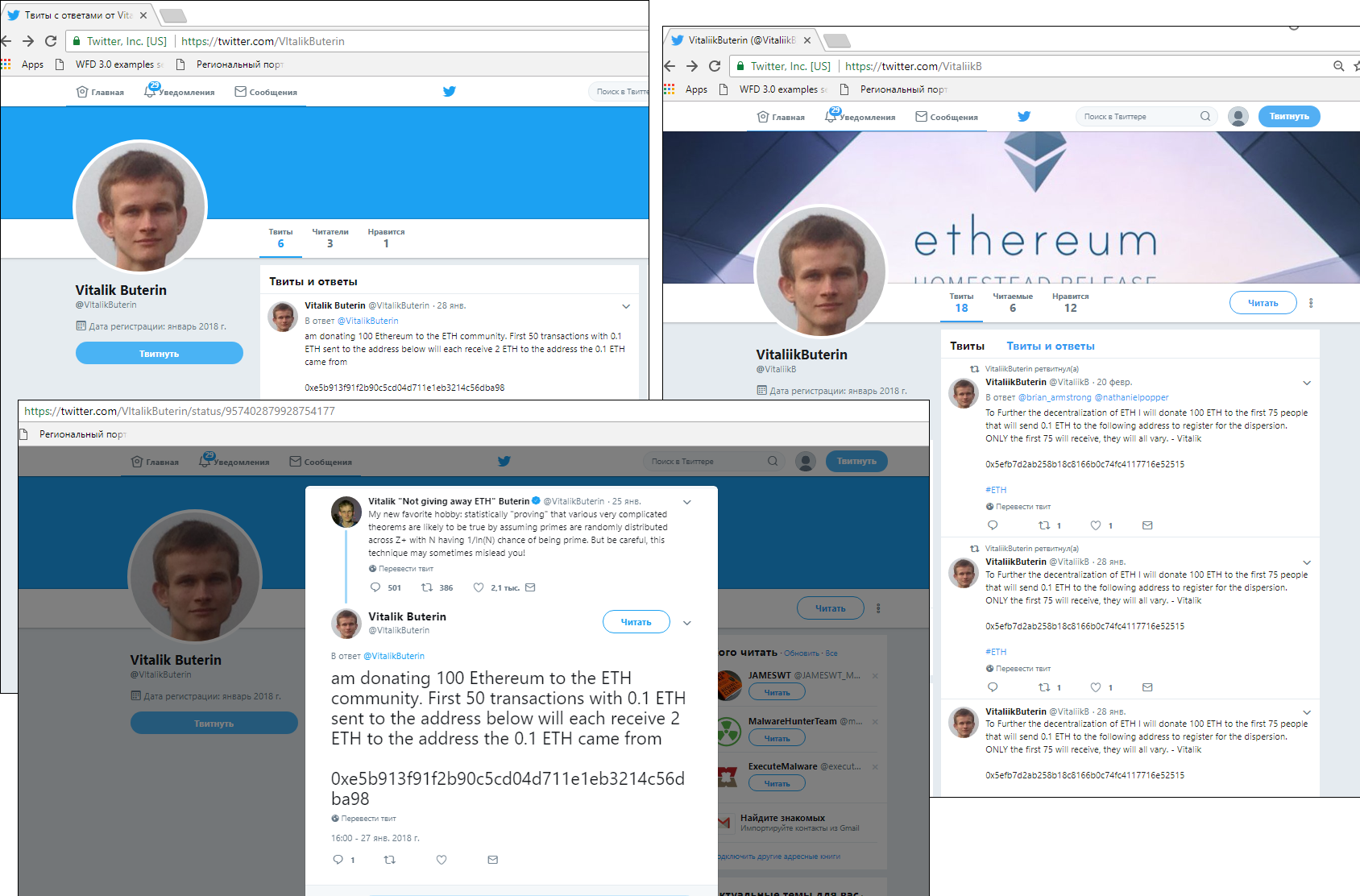
Fake giveaways also exploit famous names. In the last couple of years, for instance, Twitter has become a hotbed of fake accounts masquerading as profiles of well-known companies and people, often linked in some way to the cryptocurrency industry. For example, there are numerous fake accounts in the name of Vitalik Buterin (cofounder of Ethereum) with information about a 100 ETH giveaway for the Ethereum community. To receive the money, users are again asked to transfer a certain sum to a specific wallet. Scammers often spread this information in the form of replies to posts from the original account.
Buterin’s name is so commonly exploited by scammers that he himself changed his account name to Vitalik “Not giving away ETH” Buterin:
Fake accounts are generally spottable by the lack of a verification badge next to the name (issued by the administration of the social network), a small number of subscribers, and a recent registration date. But the mighty blue tick is not a cast-iron guarantee: there have been cases of cybercriminals buying verified accounts and changing the name (for example, to Pavel Durov, Telegram founder).
Attacks are more successful if accompanied by a news hook. For example, when Telegram suffered a blackout and Pavel Durov tweeted about it, a multitude of scam replies offered “compensation” in Pavel’s name. To obtain it, users had to go to a site and transfer a certain sum to the wallet number indicated, after which they could look forward to receiving 5-100 ETH in return.
Fairly large sums in various cryptocurrencies are also regularly offered on Twitter by phoney Elon Musks. Again, if 0.3-2 ETH is sent to a particular wallet, a payout ten times that amount is promised. Links in tweets point to sites similar to those described above, which specify a wallet number and show a constantly updated “list of transactions.” Scammers use bots to boost the number of likes for messages from fake accounts and leave gushingly positive comments.
According to some estimates, scammers en masse have managed to extract around $4.9 million from trusting users of the microblog.
https://twitter.com/backus/status/1005352462625079296
Don’t forget that scammers themselves sometimes transfer a certain sum to their wallets to assuage doubts about their legitimacy. However, the above examples show that a static image of a fake list of transactions is usually sufficient. Comments on the popular Etherscan token tracker contain heartfelt pleas either from duped users or from scammers looking to cash in on sympathizers:
Whatever the case, the number of instances of naive users sending scammers their last savings in the hope of a windfall is large and rising.
How to avoid getting hooked
The chances of scammers losing interest in cryptocurrencies are zero: the entry threshold for the “business” is too low and the potential pickings are too juicy. Our rather rough estimates (based on data from more than a thousand ETH wallets used by cybercriminals) show that this past year they managed to earn more than 21,000 ETH (nearly $10 million at the current exchange rate), and that’s not even counting classic phishing and cases of generating individual addresses for each victim. Given the sheer scale of fraud, if you’ve decided to try your hand as a crypto investor, always follow these simple rules:
- Remember that the only free cheese is in a mousetrap, so take tempting offers with a large pinch of salt.
- Check information about giveaways and “charitable” actions in official and independent sources.
- Use a third-party resource to verify the transactions on the wallet that you plan to entrust with your savings.
- Wallets that have been spotted in fraudulent schemes are often flagged in token trackers and block explorers (online tools for viewing detailed information about cryptocurrency transactions).
- Always check hyperlink addresses and URLs.
- Bookmark the address of your wallet and access it only from there.

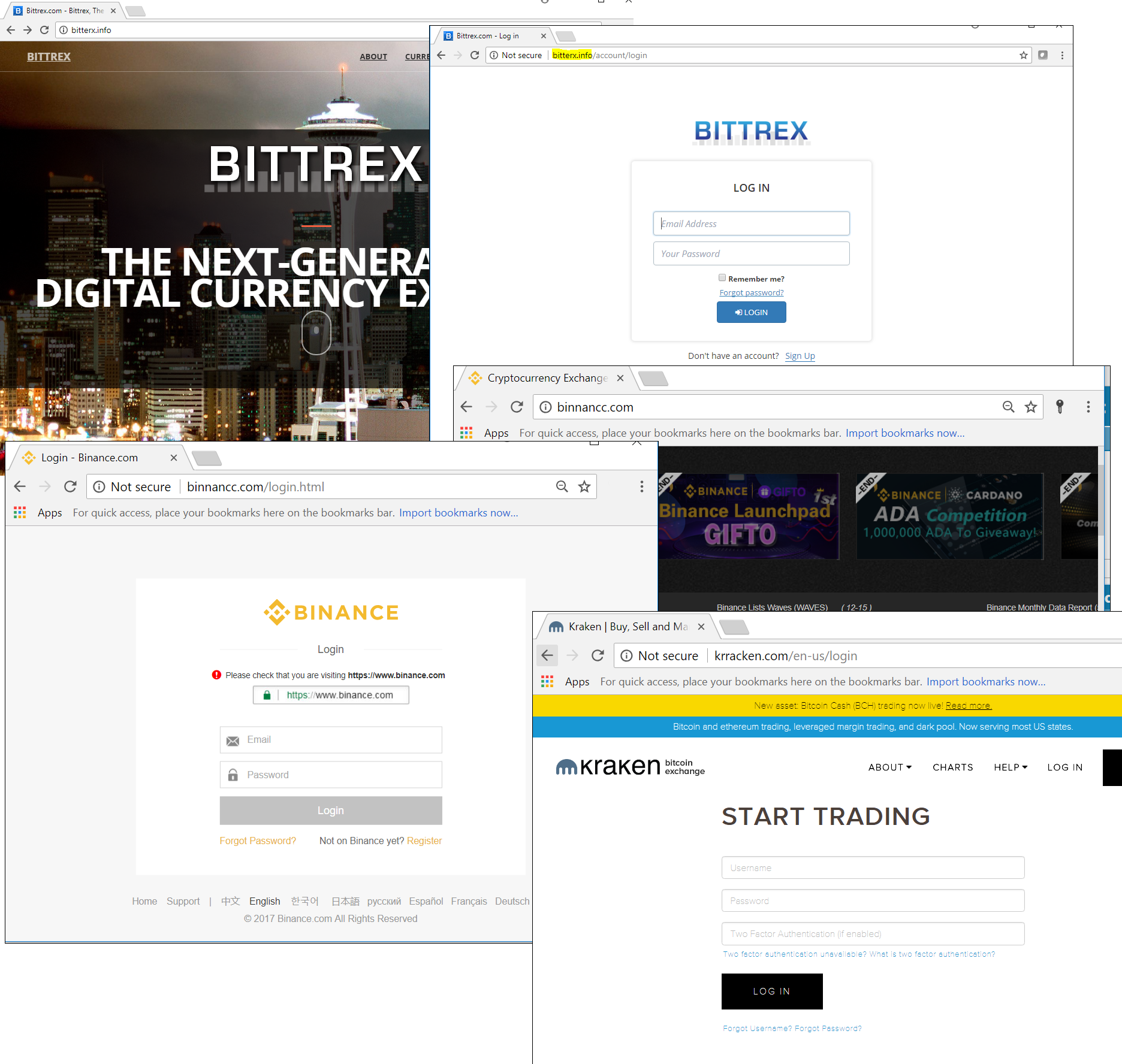
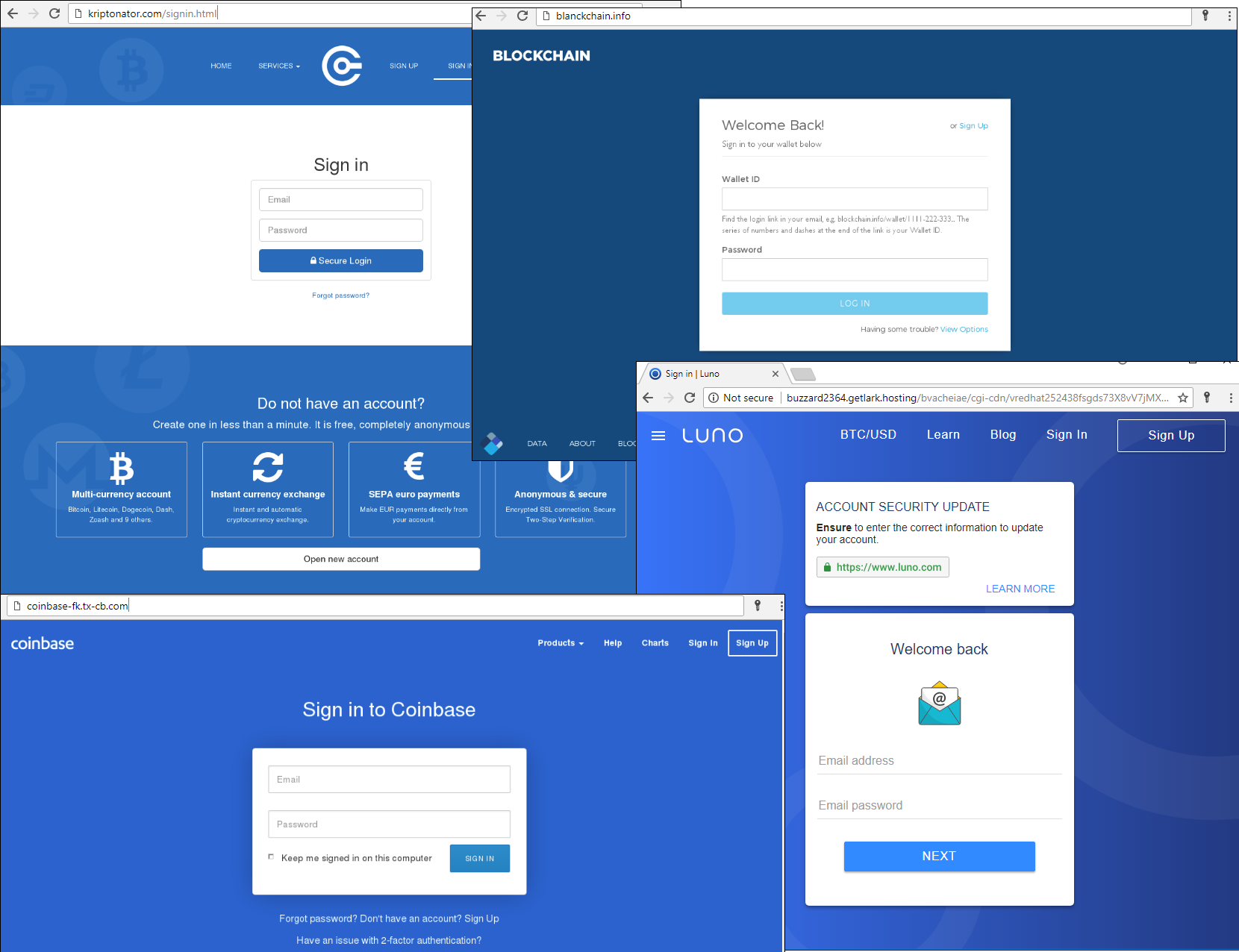
























In cryptoland, trust can be costly