
These days, invites to the new social network created by Google are a popular subject among users that want to try it.
If a subject is popular it also can be used by cybercriminals as a trick to infect curious users – and Brazilian cybercriminals have already started sending fake invites with malicious links pointing to malware, specifically Trojan bankers.
Today we found one of them targeting Portuguese speakers:
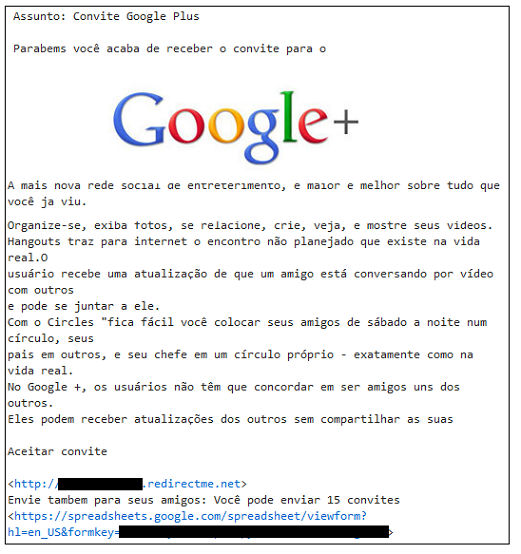
The fake invite has a link pointing to google****.redirectme.net. When accessed it redirects to a very common Brazilian trojan banker, a .cmd file hosted at Dropbox and already detected by our Heuristic engine.
The most interesting thing in that message is another link pointing to a form hosted at Google Docs. The message shows the link as “send the invitation to your friends” but it’s a fake form created to collect names and e-mail addresses of new victims:
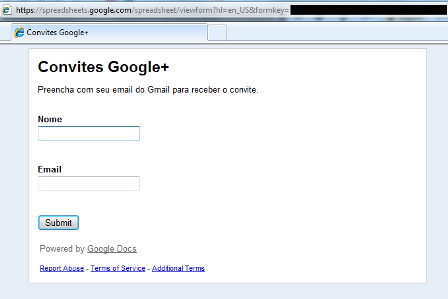
We already reported the malicious file to Dropbox team and also the fake webform to Google.
If you are interested in joining Google+, please be patient and not believe in supposed invites received in e-mails.





















Google+ fake invites = malware