
During my recent research into PHP backdoors, bots and shells, I came across a few IRC servers which looked pretty suspicious. After lurking in these channels I noticed that most of them were all about controlling botnets, automated exploitation and credit card fraud. This isn’t news – channels and IRC servers like this have been a hot media topic for the last five years. The question is, though, how can we find them so we can shut them down?
Digging a bit deeper in some of the channels, and looking the websites people were talking about in these channels, I started to see patterns. For example, some of the websites use the same words, phrases and layout. By combining these terms and creating a simple rotation algorithm I could use search engines to find websites offering illegal stuff such as credit card data and skimming tools.
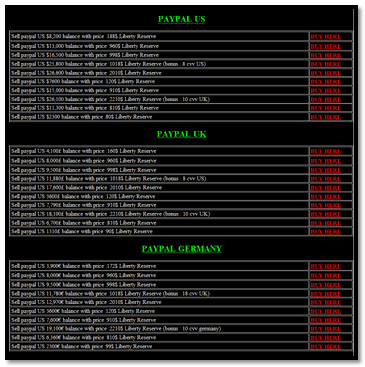
It’s not just the websites that use the same words and phrases. The IRC channels also use kind of the same information. Some IRC channel information actually gets indexed by bots, and if the owners of these websites use any semi-public IRC network, their channel will get indexed. Looking at, for example, the color schemes in channel topics, or specific words and phrases, it’s extremely easy to find these sites through simple search engine queries.
But I found out that instead of identifying the actual IRC server, you can identify the backdoor a hacker has installed on a compromised host. Most of the backdoors I identified were either written in PHP or Perl. The bots written in Perl were, in most cases, downloaded and executed by a PHP backdoor. Since the PHP backdoors are web based, even they are indexed by search engines 🙂 So through these search engines you can find the backdoors, and the backdoors have the function to read arbitrary files, which makes it pretty simple to read the source code of the backdoor or IRC-bot, which contains specific information about the relevant IRC server!
Looking at some backdoors, I noticed that they don’t just install other backdoors, they also install phishing websites. The backdoors led me on a trail which ended up at a website offering a complete archive of phishing websites – BankOfAmerica.com, WesternUnion.com, PayPal, CITY Bank etc.
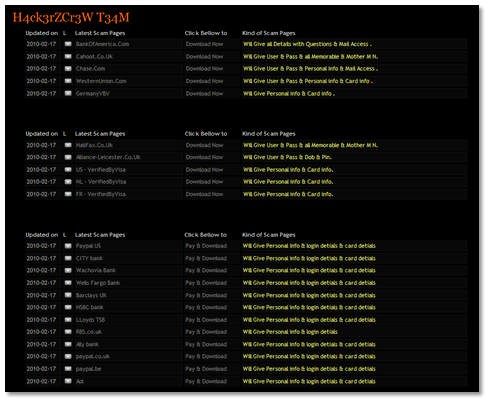
What’s quite ironic is that these hackers use something called “Google Dorks” to find vulnerable sites, but we can also use “Google Dorks” to find the attackers and their IRC channels.
And a funny footnote: while writing this, I was listening to a song by the drum ‘n’ bass band “The Qemists” where they sing: “If you play with fire, you will get burned” 🙂




















Google Dorks: fighting fire with fire