
Exploit kits are packs containing malicious programs that are mainly used to carry out automated ‘drive-by’ attacks in order to spread malware. These kits are sold on the black market, where prices ranging from several hundred to over a thousand dollars are paid. Nowadays, it is also quite common to rent hosted exploit kits. Because of this, it is a competitive market with lots of players and many different authors.
Appearing several years ago, MPack was one of the first examples of this kind of ‘tool’. This was followed shortly after by ICE-Pack, Fire-Pack and a lot of others. Today’s well-known exploit kits are, for example, Eleonore, the YES Exploit Pack and Crimepack. A lot of research papers have been written and information published about exploit packs on different blogs and websites.
During our research we examined many different aspects of these kits, one of which we present here.
Exploit kits by numbers
What makes a kit successful? What is the key to a kit’s popularity? First of all, let’s take a look at the evolution of different exploit kits found in the wild since January 2009. (Courtesy of MalwareDomainLists)
The first thing that catches our eye is how different the distribution pattern is among different exploit kits! The major players here are Phoenix and Eleonore, with Neosploit just behind them. We can see this better in the following chart, showing the top 5 exploit kits of all time:
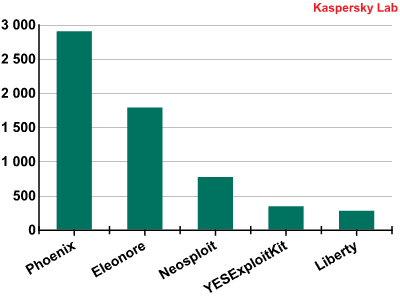
Even though the top 3 exploit kits have not changed lately, we can see new kits emerging. Let’s look at the top 5 exploit kits of the last 6 months:
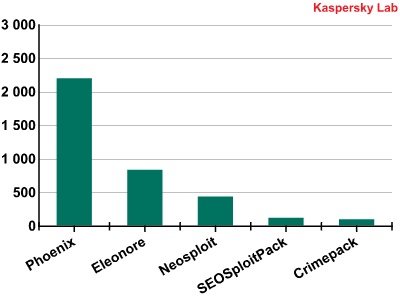
Here we can see the emergence of the SEO Sploit Pack and Crimepack as new players.
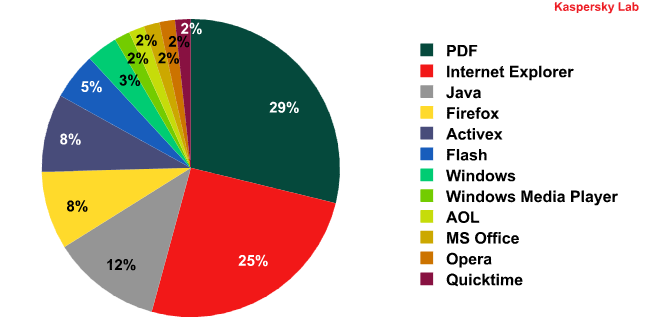
Ok, now let’s take a look at the vulnerabilities that these exploit kits target:
Internet explorer, PDF and Java vulnerabilities together represent 66% of the attack vector used by most popular exploit kits. How old are these vulnerabilities? The following graph shows the distribution of the years in which each vulnerability was reported:
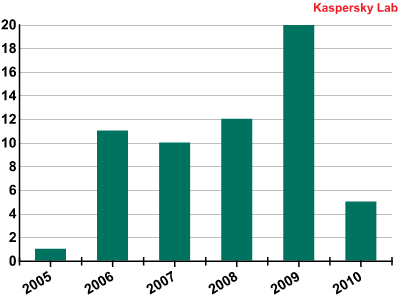
Most of the vulnerabilities exploited are old and all of them have patches available. However, they continue to be used successfully.
It is interesting to note that the reuse ratio of vulnerabilities is 41% (the same vulnerabilities exploited by different exploit kits).
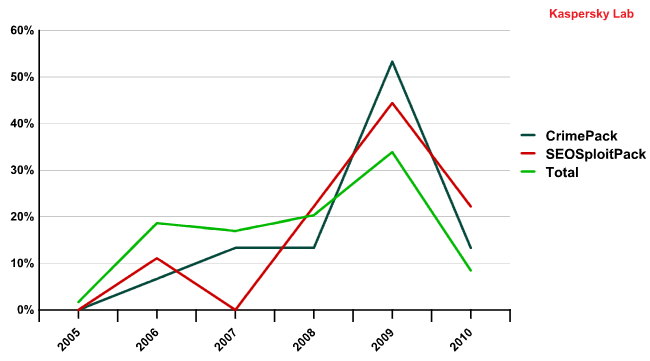
Finally, why are Crimepack and the SEO Sploit Packs gaining popularity in the last few months? Of course, there could be a lot of reasons, and their exploitation capability is only one of them. So let’s see if we can find any other attributes:
Newer exploits
If we check the percentage distribution of vulnerabilities exploited by year of disclosure against the median of the top 5 exploit packs, we see that both Crimepack and SEO Sploit Pack use newer exploits.
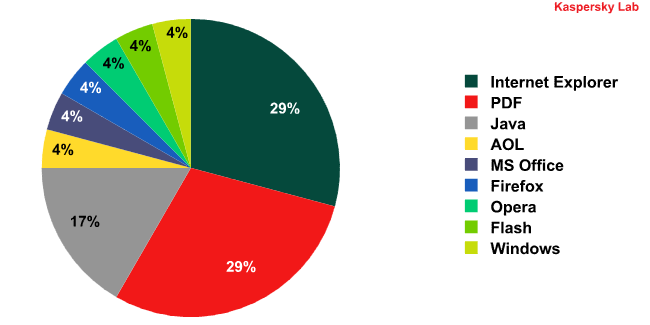
Target distribution
Again PDF, Internet Explorer and Java are the top 3 targets, but in this case, the combined percentage represents more than 75% of the total. This means that they are exploiting the most popular programs found on victims’ systems.
Exploit kits behind the scenes
To obtain the following results, we took several different exploit kits and versions and analyzed them in detail. Over 16 thousand files were processed.
Graphics and design
In addition to integrated exploits, the kits also contained an interface that allows the cybercriminals to see various statistics about the pack.

Login page for Crimepack
During file-processing, different kinds of image files used in the web front end came to light. Generally speaking, they can be separated into GIFs (older format) and PNGs (newer format). The more widely used packs contained larger images, for example, the YES exploit pack, Crimepack, MySploitsKit and Fragus. The date of creation seems to have no influence. One of the oldest, MPack, has very small images, whereas ICE-Pack (2007) and Siberia (2009) both have much larger images.
The quality of the graphics and design of each exploit kit depends on the efforts of its creator. Eleonore, for example, uses a freely available CSS-template, while others create their own.
Geneology, theft and copy
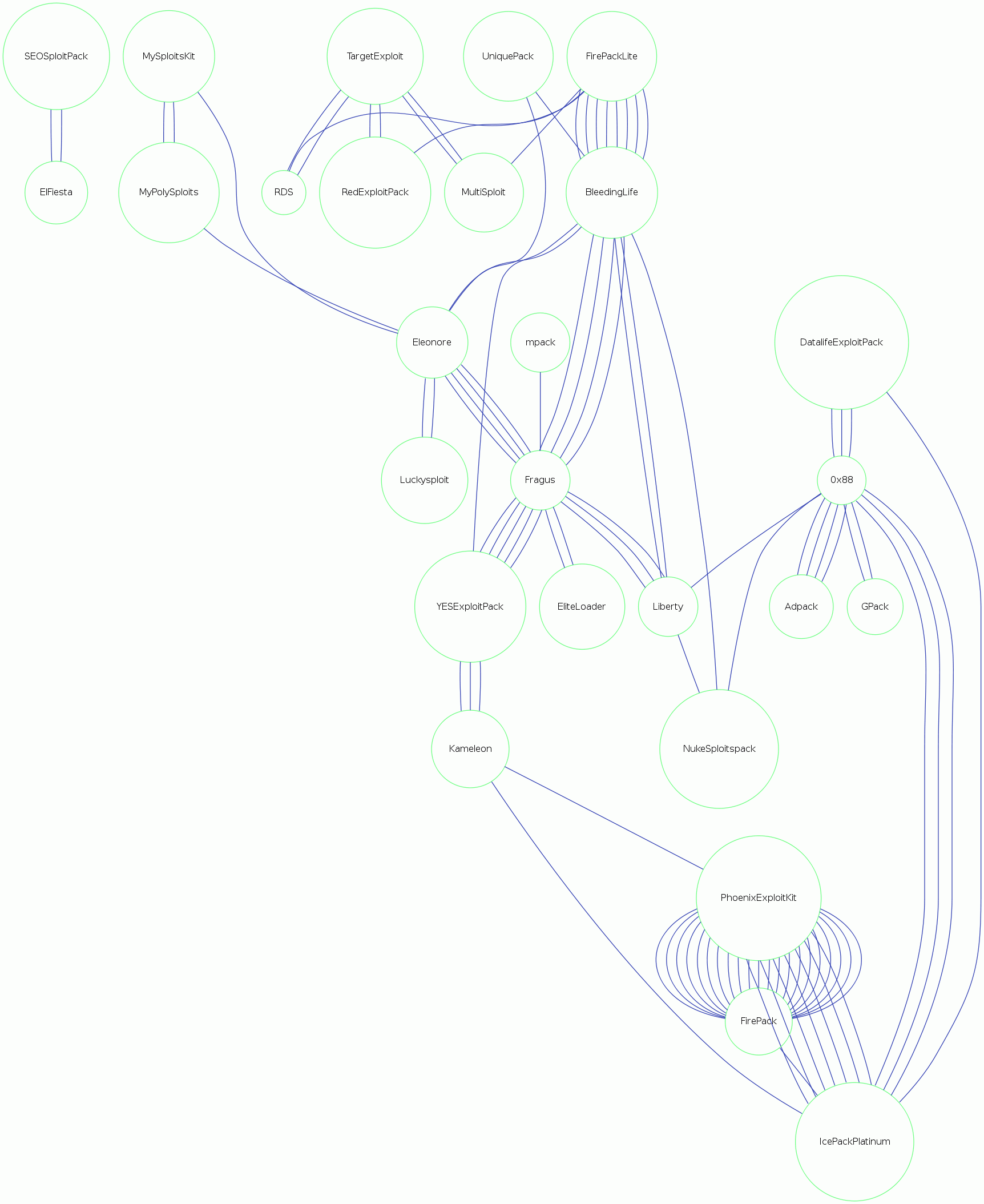
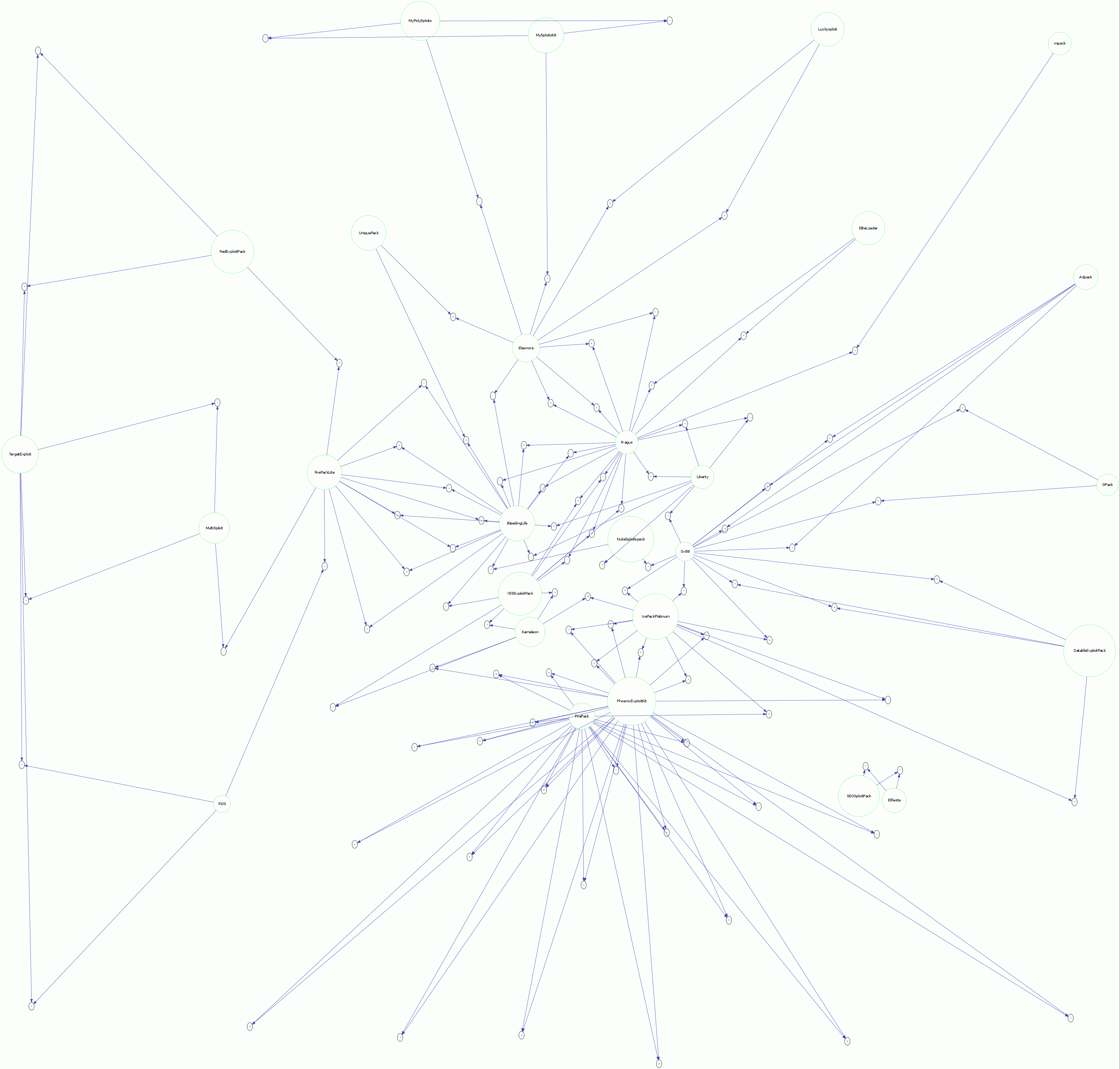
From the quantity of files we examined, we can create some interesting statistics. During processing, we compared the files against each other. This is useful within each kit’s family as it allows the tracking of changes for different versions and reveals the exploit kit’s evolution. We also compared all of the exploit kits’ files to each other in order to identify any possible commonalities, which did indeed exist; as shown by the following map:
You can easily track which kit uses code from another kit or which kit influenced another kit. This is particularly true of the Phoenix Exploit Kit, which uses a lot of the material from the much older Fire-Pack and ICE-Pack kits. FirePackLite and BleedingLife also share a lot of similarities. Only SEO Sploit Pack and ElFiesta displayed an exclusive connection to each other. The rest of the samples had connections to several other packs. The following map is an extension of this, within which similar files have been added:
Conclusion

Ultimately, everything is about money, as the pictures above from the creators of BlackHole demonstrate. If an exploit kit becomes very popular, its creator earns more money through higher sales volumes.
There is one thing an exploit kit must offer to gain popularity in this strongly competitive market: a high infection rate. Newcomers to the creation of exploit packs therefore often use existing, proven methods, and this may well explain the amount of similarities between packs.
However, with the amount of publicity the topic of exploit kits gets, other things have to be considered by the creators e.g. security, as vulnerabilities within exploit kits have been identified.
We at Kaspersky Lab will keep a close watch on the situation in order to provide complete protection against threats such as these.

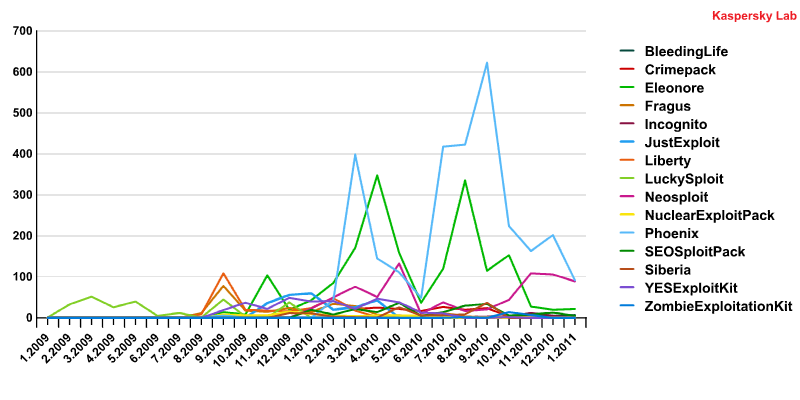






















Exploit Kits – A Different View