
After an analysis of the encryption routine of the malware used in the Petya/ExPetr attacks, we have thought that the threat actor cannot decrypt victims’ disk, even if a payment was made.
This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware.
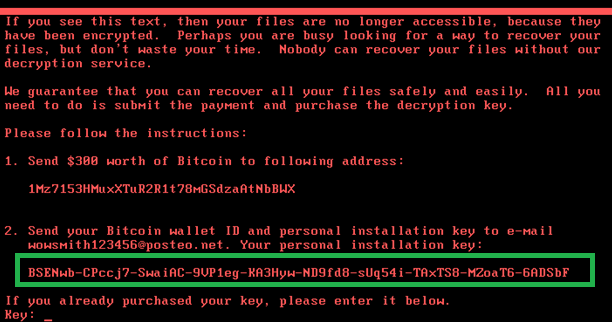
Below the technical details are presented. First, in order to decrypt victim’s disk the attackers need the installation ID:
In previous versions of “similar” ransomware like Petya/Mischa/GoldenEye, this installation ID contains crucial information for the key recovery. After sending this information to the attacker they can extract the decryption key using their private key.
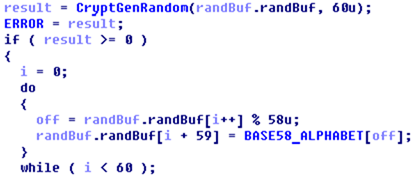
Here’s how this installation ID is generated in the ExPetr ransomware:
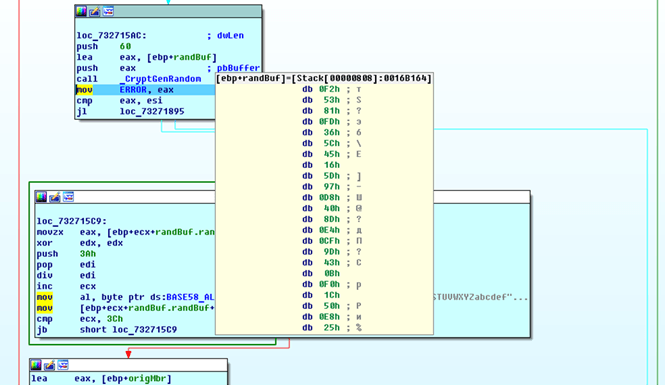
This installation ID in our test case is built using the CryptGenRandom function, which is basically generating random data.
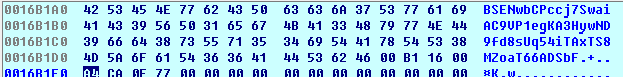
The following buffer contains the randomly generated data in an encoded “BASE58” format:
If we compare this randomly generated data and the final installation ID shown in the first screen, they are the same. In a normal setup, this string should contain encrypted information that will be used to restore the decryption key. For ExPetr, the ID shown in the ransom screen is just plain random data.
That means that the attacker cannot extract any decryption information from such a randomly generated string displayed on the victim, and as a result, the victims will not be able to decrypt any of the encrypted disks using the installation ID.
What does it mean? Well, first of all, this is the worst-case news for the victims – even if they pay the ransom they will not get their data back. Secondly, this reinforces the theory that the main goal of the ExPetr attack was not financially motivated, but destructive.
Our friend Matt Suiche from Comae Technologies independently came to the same conclusion.
ExPetr/Petya/NotPetya is a Wiper, Not Ransomware






















ramalingam
is the kaspersky update equipped to deal with the ExPetr/Petya/NotPetya wiper/
Arash Zangeneh
Yes, at least our KES 10, managed to block it.
Jo
I agree that this is a wiper and not a Ransomware however sometimes that actual Malware may not be the main motive behind the attack. This to me is either a currency manipulation on a large scale or simply cyber terrorism.
You can check out the theory below
http://www.securityweek.com/latest-wannacry-theory-currency-manipulation
Diazomethan
Weak reason to classify it as a wiper, in my opinion.
Wouldn’t it be possible that the author stores the key and the ID in a table? In this case, it is nothing more than something like a UUID, but it would be still possible for the attacker to decrypt the data.
Matt Suiche gives the better explanation why it is a wiper: Because it destroys some crucial data.
Janiko
I’d like more info about this : the ID is random, right ? And about the encryption key : is it generated elsewhere ? Is it sent with that random ID to a C&C ? And is it really a wiper or only a bad-written ransomware ?
Andrea
Hi
we have also this detailed analysis https://www.crowdstrike.com/blog/petrwrap-ransomware-technical-analysis-triple-threat-file-encryption-mft-encryption-credential-theft/
We have been able to retrieve most of the files of infected computers. However, as expetya does crypt some of them BEFORE actually being visible, those are encrypted. The TXT are safe, so that means that they’re not simply corrupted, but encrypted.
Given the key in the README.TXT file, do you think they can actually be decrypted? NOte that for many files we also have the same exact file BEFORE encryption.
Pete
Ok ID is random – so what?
Did you proove that the random ID has nothing to do with the encryption key?