
Thousands of dollars and tons of CO2
Brief summary:
We present the results of evaluating the positive economic and environmental impact of blocking web miners with Kaspersky products. The total power saving can be calculated with known accuracy using the formula <w>·N, where <w> is the average value of the increase in power consumption of the user device during web mining, and N is the number of blocked attempts according to Kaspersky Security Network (KSN) data for 2018. This figure is equal to 18.8±11.8 gigawatts (GW), which is twice the average power consumption rate of all Bitcoin miners in that same year. To assess the amount of saved energy based on this power consumption rate, this number is multiplied by the average time that user devices spend on web mining, that is, according to the formula <w>·N·t, where t is the average time that web miners would have been working had they not been blocked by our products. Since this value cannot be obtained from Kaspersky data, we used information from open sources provided by third-party researchers, according to which the estimated amount of electricity saved by users of our products ranges from 240 to 1,670 megawatt hours (MWh). Using the average prices for individual consumers, this amount of electricity could cost up to 200 thousand dollars for residents in North America or up to 250 thousand euros for residents in Europe.
So what’s our contribution to the fight against excess energy consumption?
Cryptocurrency mining is an energy-intensive business. According to some estimates, Bitcoin miners consume the same amount of energy as the Czech Republic, a country of more than 10 million people (around 67 terawatt hours per year). At the same time, as we already noted, they do this with multiple redundancy — but only as long as this is economically justified. But what about users that are forced to mine against their will — that is, systems affected by web miners (websites mining cryptocurrency)? Since this most often happens illicitly, such sites are detected by security solutions as malicious and blocked.
In 2018, Kaspersky products blocked 470 million attempts to download scripts and attempts to connect to mining resources on the computers and devices participating in Kaspersky Security Network. Is it possible to assess the economic (and environmental) impact of this undoubtedly positive activity? To answer this question, we had to tackle several issues.
1. How much does power consumption increase when the system is mining cryptocurrency?
We couldn’t find any open source data on this matter, since most researchers are interested in, so to speak, integral power consumption of cryptocurrency mining systems — that is, how much a particular hardware set up consumes in total and how much they’d spend to cover the electricity bill. Data on the most common mining systems can be found at the sites like miningbenchmark.net, which help to make an informed decision on economic viability and, accordingly, whether to mine or not to mine. We were interested in the question of what portion of a system’s total energy consumption is related specifically to web mining that happens without the user’s consent.
To get an answer, we used a measuring bench previously set up to study surges in mobile energy consumption during USB charging and data exchange.
Using the computers of 18 volunteers (a big thank-you to them once again), we were able to experimentally determine the rise in the power consumption of 21 different devices when mining Monero on CoinHive (the most common cryptocurrency mining service). In brief, here’s what we managed to figure out:
- Is there a dependence on the type of processor? Definitely.
- Is there a dependence on the amount and type of memory? Definitely not.
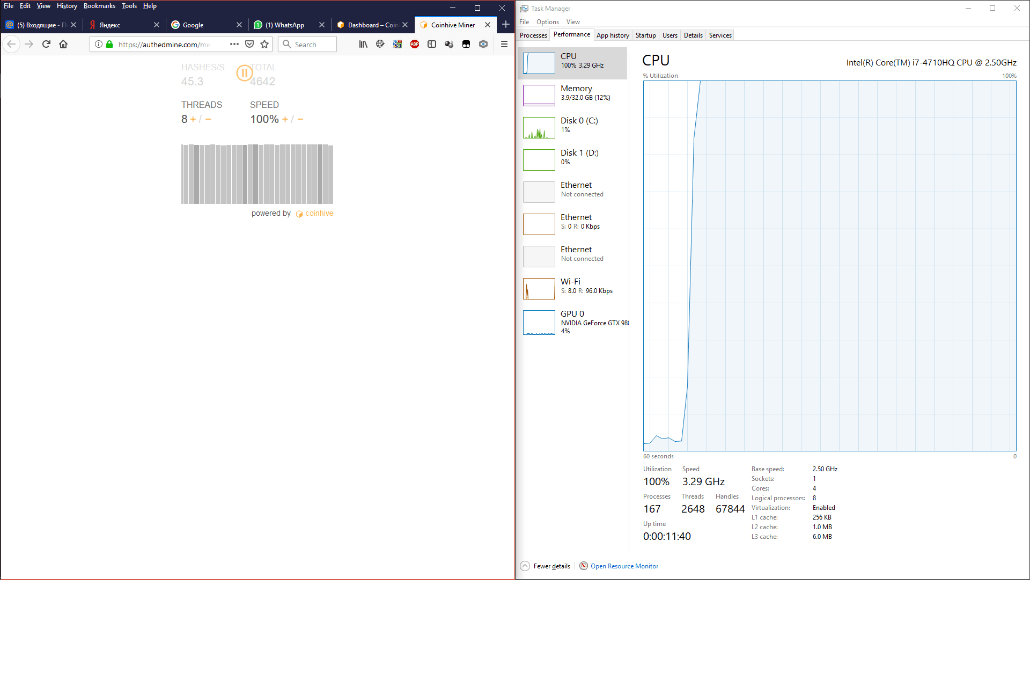
This is clear from this image showing the increase in CPU load when mining begins:
As can be seen, the amount of used memory used does not change and does not depend on the amount of processor load.
- Is there a dependence on Internet connection speed? We did not check this; in all experiments the connection speed was more or less the same.
- Is there a dependence on the browser? Definitely not.
- Is there a dependence on the type of operating system? Probably not.
It’s worth explaining here that we lack sufficient data to draw a definite conclusion regarding the operating system. We saw slightly different results for the same hardware running under different operating systems (namely, Mac OS and Windows); the difference falls within the boundaries of statistical error, and there are too few points for a reliable conclusion.
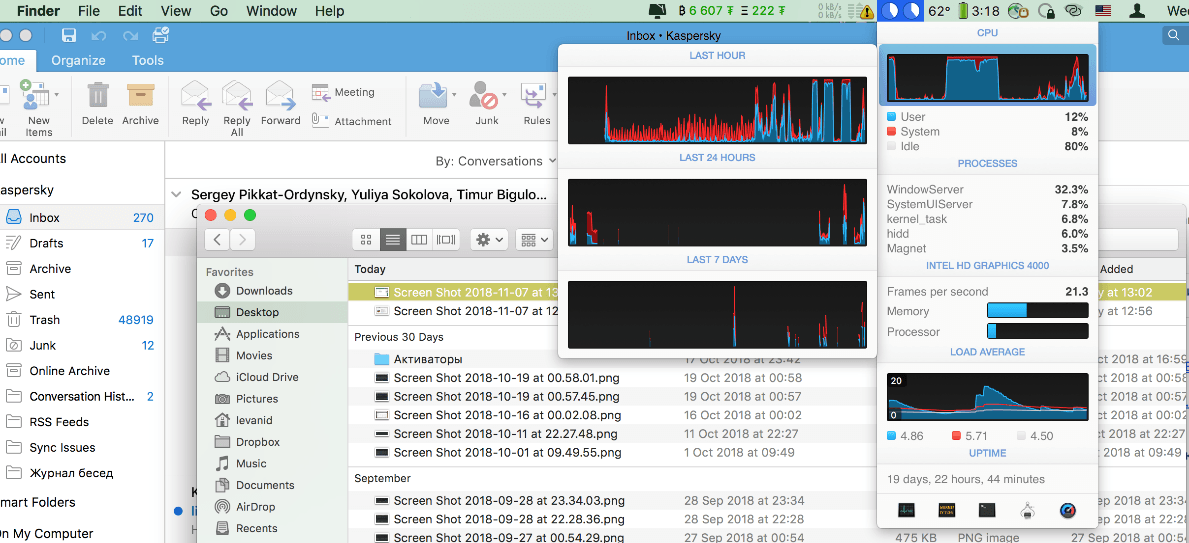
For comparison, the processor load under Mac OS looked something like this:
The situation is identical to the CPU load under Windows, not exceeding 10–12% in idle mode, and 100% during web mining.
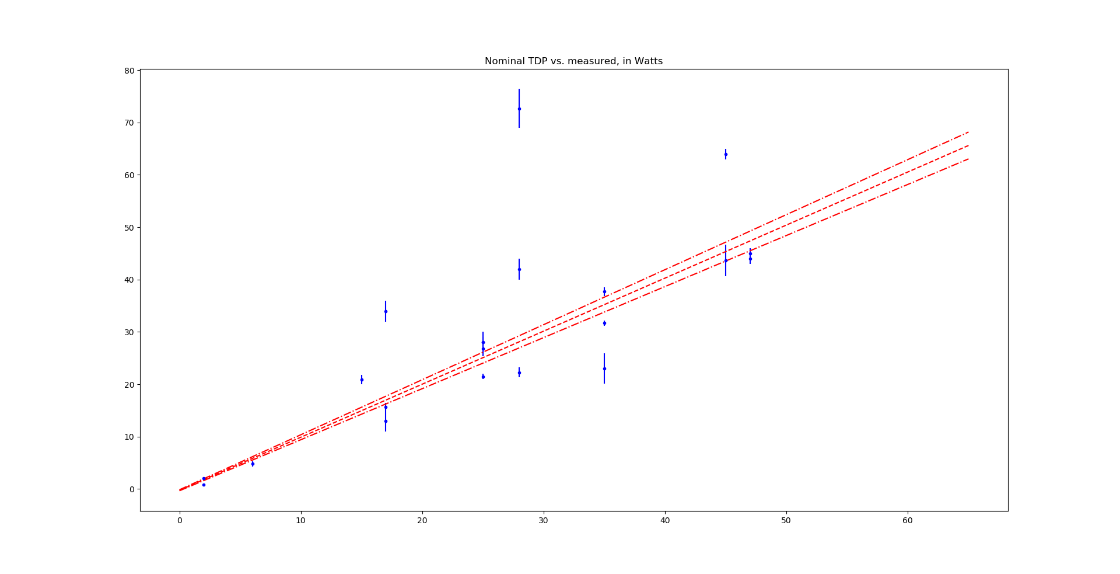
The graph showing the dependence of the measured increase in energy consumption on the processors’ nominal TDP (thermally dissipated power), taken from the manual, looks something like this:
The red line shows the result of a linear approximation in the ax + b form, where a = 1.013±0.017 and b = –0.237±0.044 (determined by the least squares method taking into account the measurement error at each point), as well as the range of values predicted by the model with 95% probability. There are slightly more outliers on this graph towards energy consumption exceeding TDP than those that energy consumption below TDP. Overall, however, for the purposes of further approximation, it is sufficient to use TDP as an estimate of the increase in energy consumption in web mining mode.
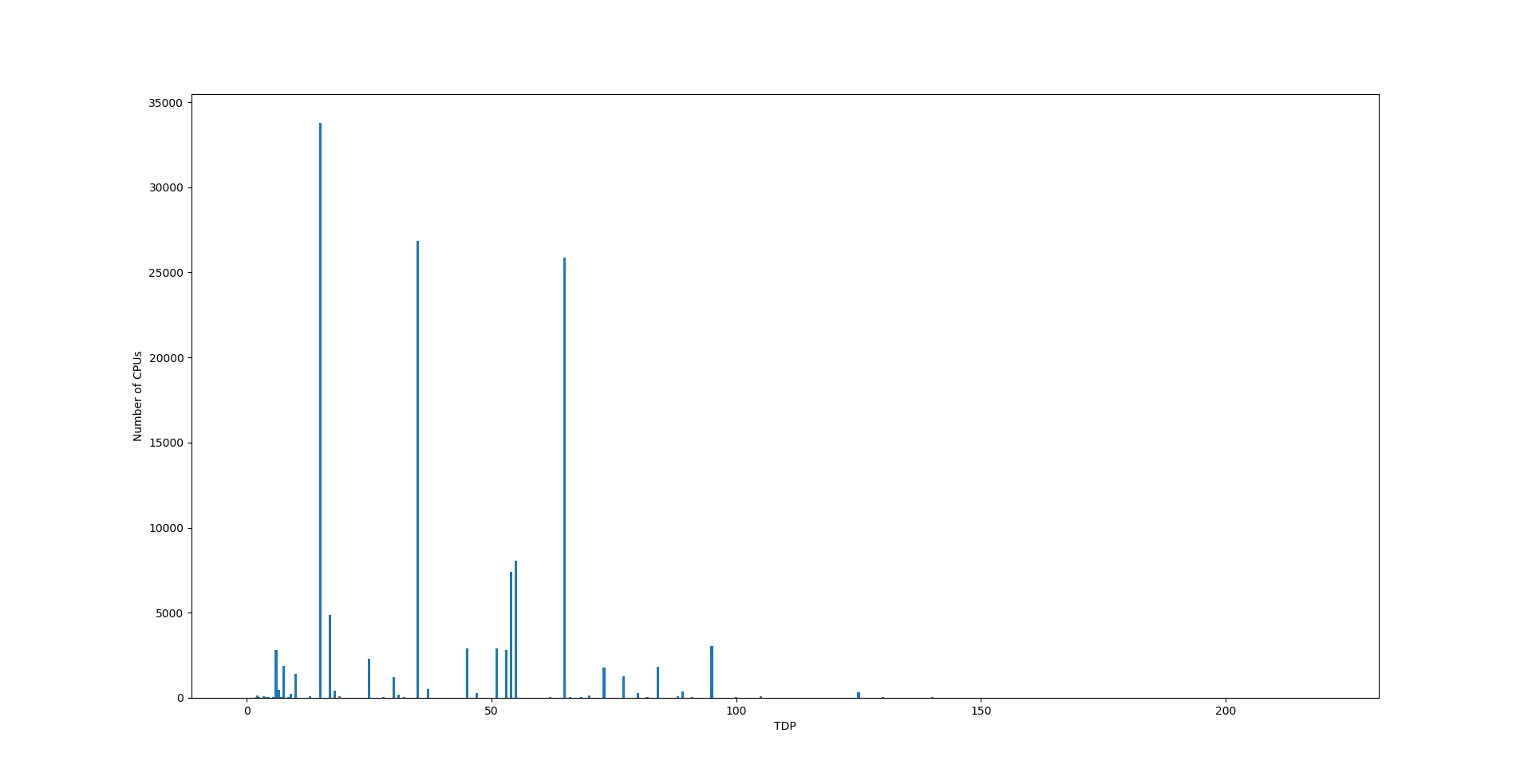
Question 2. But processors that are part of devices that block web miners have different TDPs. How to evaluate the contribution of each of them?
To analyze the distribution pattern of processors by TDP, we used a random sample containing about 1% of the total number of devices participating in KSN. In this sample, we managed to identify 2,497 CPU types. Reference data on 1,550 types of processors were pulled automatically by playing with regular expressions and scraping open sources, the most useful of which was PassMark CPU Benchmark. Information about the remaining 947 types of processors had to be added manually.
The weighted average TDP from this data was calculated as
where fi is the frequency of the i-th type of processor, and ni is the number of processors of the i-th type in the distribution of CPU’s TDP. However, the frequency distribution of CPU’s TDP is far from normal, so we will have to use a coarse estimate covering all TDP values from 15 to 65 W, that is, <w> = 40±25 W.
3. How to calculate the average working time of a web miner?
This is perhaps the most difficult question, since Kaspersky products are there to block web miners. A study by our colleagues from the Foundation for Research and Technology — Hellas (FORTH), a research center in Greece, gives an estimate of the average working time of web miners at 5.3 minutes. And a joint report by colleagues from the University of California, Santa Barbara, the University of Amsterdam, and the University of Utrecht estimates the average time that people spend on websites where web mining activity has been detected as approximately one minute.
At the time of writing this article, web analytics service SimilarWeb had calculated the average time of a visit to cnhv.co (a coinhive.com mirror) to be 46 seconds. As such, time is the most volatile parameter in our energy consumption formula Wtotal = <w>·N·t, where N is the number of detections and t is the time that the web miner would have been in operation had it not been blocked by our product. Substituting the corresponding values, we obtain an estimate of Wtotal: 240 to 1,670 megawatt hours (MWh). Being several orders of magnitude less than Bitcoin’s total energy consumption of 67 terawatt hours, this is still a serious amount of energy. It is comparable to the annual energy consumption of a city with a population of several hundred thousand.
Incidentally, the cost of the maximum amount of power that the miners we blocked could have consumed (1.67 GWh) varies around the world. If this amount of power were consumed entirely in Europe, European consumers would have to fork out €250,000, while for US residents the figure would be $200,000. The cheapest electricity of all would be available to residents of China and India, where negligence in the face of web miners would cost “only” $133,000. And in Japan, where electricity is the most expensive, that would cost half a million dollars.
As for the ecological impact, based on the IEA (International Energy Agency) global average value for carbon emission of 475 kg/MWh, we can assume that we have prevented the release from 115 to 800 tons of CO2 into the atmosphere.
As you can see, the confidence intervals that we have for energy estimates are quite wide. This is because we had to use the duration of time, which we could not estimate directly. If we remove it from equation, we get the “detection power” (<w>·N) – or the power consumption rate of all blocked attempts. For 470 million web mining attempts detected (and blocked) in 2018, this value is equal to 18.8±11.8 gigawatts (GW). To compare that with Bitcoin as a reference point, we can divide the known amount energy Bitcoin miners have consumed the same year by time – and we get roughly 7.647 GW, that is, half as much! Remember that the total power energy consumed Bitcoin miners was compared with electricity spent by residents of Czech Republic? Looking into IEA’s statistics for OECD countries, we found that 18.8 GW of power consumption rate is comparable to the power consumption rate (the amount of energy they consume within a unit of time) of such country as Poland, with almost three times as much residents as Czech Republic. We can also compare this with the infamous Chernobyl nuclear plant, whose four reactors before the accident produced around 4 GW of power in total. In other words, in one year Kaspersky products saved as much power as the output of four Chernobyl plants, or double the power consumption rate of all Bitcoin miners worldwide.
Conclusion
The ongoing fight against web mining has been quite successful, in both legal and technological aspects. However, as long as profit can be made, cyber criminals will find ways to utilize the CPUs of unsuspecting victims. For instance, we had no trouble finding the above-mentioned CoinHive mirror, and it’s not unlikely that owners of Coihhive and other web mining sites would continue their assaults on unsuspecting users in future as well — on the systems without information security solutions, of course.
The most effective constraint, in our view, is the situation on the cryptocurrency market as a whole: web miners will continue to exist as a threat as long as it remains possible to convert cryptoassets mined this way into fiat currency.
Which means that in order to make our foreseeable future greener, literally, security products would have to continue working for the good of their owners — and the entire world.
Notes
- We have been able to experimentally measure the dependence of increase in power consumption on nominal TPD for 21 types of processors, which amounts to 0.8% of the total number of processor types in the random sample of 1% CPUs in Kaspersky Security Network (2497 processor types). Given that, and also assuming that the list of CPU types evolves with time, we plan to study this matter in more detail going forward.
- The estimates above were made in the assumption that frequency distribution of CPU TDPs that were blocking web mining attempts, was similar to the frequency distribution of CPU TDPs determined from a random sampling of approximately 1% of the total number of devices participating in Kaspersky Security Network. This assumption may be incorrect, but there is no technical way of checking it, because Kaspersky Security Network operates only with depersonalized statistics and thus we cannot match data on processor types with data on detections.

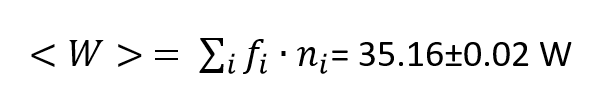


















Assessing the impact of protection from web miners