
Yesterday it was a dark day for many companies in Europe, but especially in the Netherlands. A piece of malware known as Worm.Win32.Dorifel infected over 3000 machines globally, and 90% of infected users were both from public and business sector organizations based in the Netherlands. We have seen government departments and hospitals being victims. The other countries with a large amount of infections were detected in Denmark, the Philippines, Germany, the United States and Spain. All users running Kaspersky Labs Products are protected from this threat.
The malware is initially distributed via email to victims. It uses a Right To Left vulnerability to hide its original file extension. The malware then downloads another malware which encrypts documents and executes them on the infected computer. Dorifel also attempts to encrypt files found on network shares.
When I was sitting down and investigating the Dorifel malware I noticed that the servers hosting the Dorifel malware was not configured properly and allowed for example directory listing in certain directories. This triggered me to search for more interesting directories, which I did and to my surprise I noticed that the server was hosting a lot more malicious components and not just the Dorifel malware. It is very difficult to say if this scam is complex and advanced since it uses many different components with different complexity level. Some of the interesting things I found includes:
- Log files containing financial information (Credit card numbers, CCV and names)
- Undetected Java exploits (Now detected as: Exploit.Java.CVE-2012-0507.oq and Exploit.Java.Agent.hl)
- Rogue antivirus (Detected as Trojan-FakeAV.Win32.SmartFortress2012.ctq)
- Additional malware including Trojan.Win32.TDSS.isql and others which is still under analysis.
- Infection statistics for the Dorifel malware (Still active)
- Webinjects used for launching phishing sites
- Administrative panels for Exploit Kits and Statistics.
This is a very strong indication that the gang behind the Dorifel malware was also doing some other really nasty scams. We were also able to download other samples of various malware which is still being investigated by the malware analysts at Kaspersky Lab. As soon as we have more information we will publish it here on Securelist.
The server also contains infection statistics, and at the time of writing even more victims than before has been identified in even more countries. We can now see new countries such as Canada, China and Poland. The infection rate in the Netherlands has gone up to 3113 which is an increase of over 1100 computers in just a few hours. This indicates that not all computers are either running an updated anti virus software or worst case scenario, no anti virus solution at all.
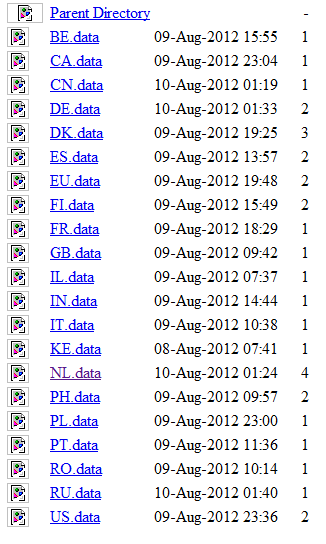
One question that we have asked our selfs during this research is if this attack is a targeted attack against governments and high profile companies in the Netherlands. This is nothing that we confirm, but for some reason the vast majority of all the victims comes from Netherlands. I decided to investigate this further to see if I could find more information and the first logical step was to start investigating the C&C server infrastructure.
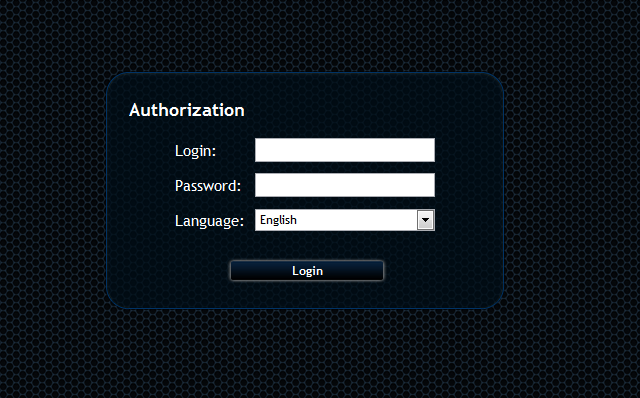
At this time we were both analyzing the samples and looking into the servers. This is not the first time we have encountered servers used in malware scams with a poor configuration so we knew what to start looking for. I do not know why we often see servers with a poor configuration, but it might be an indication that the gangs behind this are not extremely technical, and the people who wrote the malware are not the same people who actually used the malware
Last but not least, we were also able to find several control panels. These control panels contain statistics of infections, and maybe also information about the stolen data. We also found installations of PHPMyAdmin
I want to highlight that we found tons of new malicious files on the server hosting the Dorifel malware and also a lot of exploits which could be an indication that computers infected with Dorifel also have additional malware installed on the computer. All samples that we have collected have been sent to the malware analysts and we have already published several new signatures that will help us to protect our customers from these threats. We are also working closely with various law enforcement agencies to shut these guys down.
As mentioned before, we did find some interesting financial information, which could be an indication that this malware scam is related to for example ZeuS / Citadel, but since we have not yet identified any malware related to ZeuS/Citadel we cannot confirm it. All we can confirm is that the same server does store stolen financial information. We are still investigating this.
Some of the pieces in the puzzle that does not make sense is that on the same server we also identified new Java exploits, which was detected by our Heuristic engine, but at first we did not have a full verdict. The exploits are now identified as Exploit.Java.CVE-2012-0507.oq and Exploit.Java.Agent.hl. But why the server is hosting exploits is still unknown but we think that the exploits is used in drive-by-download attacks to download additional malware, for example malware stealing financial information.
Since we have not identified all the components, or figured out who is behind this scam we will continue investigate the found samples. But at the moment we have components that will cause a lot of damage on the infected computer. If you get infected you might loose financial information, have your files encrypted and also have backdoors installed on your computer. We will keep updating our blog with new information as soon as we can. I do want to warn everyone who is reading this blog, please be aware of suspicious files, so for example dont open attachments in emails from organizations that have been affected by the virus. Make sure that your computer is protected with the latest signatures from Kaspersky and that all security patches, not only for Windows but also third party software such as Java is installed because we might see more attacks like this coming.
Additinally we also recommend that you block access t othe following IP addresses 184.82.162.163 and 184.22.103.202. If you see network traffic to these addresses it might be a strong indication that you are infected, and the trojan downloaders seems to download additional malware from these hosts.
For users who are not customers of Kaspersky we also recommend that you download our free removal tool from our website. http://www.kaspersky.com/virusscanner




















Dorifel is much bigger than expected and it’s still active and growing!