
UPDATE (7/9/2012):
Thank you Barry Green and the DCWG. The DCWG-run DNS servers have been taken down:
“On 12:01 Eastern Time on Monday July 9th 2012, the DCWG stop responding to DNS queries from infected machines. This is in compliance with the US Justice Department Court Order authorizing the clean DNS servers.
At 12:23 Eastern Time on Monday July 9th 2012, the server started to reply to all DNS request with an ICMP Unreachable. This would help infected computers troubleshot their problem is they find they cannot access DNS servers.”
**************************************************
Here we are. It’s the last call on DNSChanger cleanup. On Monday, the Fbi-run replacement DNS servers are coming down because the court-ordered extension is coming to an end, and your systems may using these servers for resolution. There are a set of sites that may unreliably help you identify whether your machine or router continues to maintain DNS settings to the “DNSChanger” operators’ servers. This unreliability is partly because upstream major internet backbone providers have created unintended confusion, and partly because of poor/ineffective web-side detection implementations.
In the US, 60k hosts are reported to require that their DNS settings remain to be changed. How many of those systems are truly “infected”? No one knows. And, the number could be inflated. It could be that none of these systems are infected. Or all of them could be infected. Perhaps all LAN-side systems behind home and corporate routers, or systems cleaned of malware that may still maintain artifacts of this infection, continue to use Rove Digital servers for DNS resolution.
In other words, it doesn’t mean you have pneumonia, but you still have a cough. And it makes you extraordinarily more likely to get sick again. Some vendors’ products, like here at Kaspersky, have been detecting the artifact DNSChanger settings on effected machines and offering to reconfigure these settings to a set of “clean” DNS servers. This DNS reset routine is presented by Kaspersky Endpoint Security 8.0 and 2010+ home products with this popup for “Trojan.Multi.DNSChanger.Gen”:
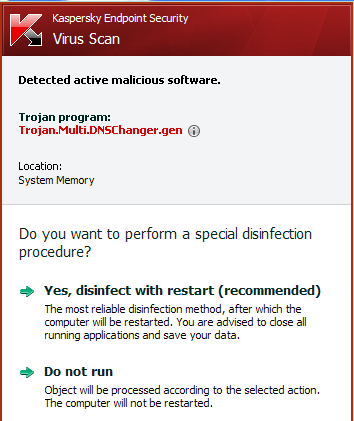
Just click on “Yes” and your system’s DNS settings will be reconfigured to use DHCP-assigned or clean, open DNS services. After host-side reconfiguration, it still would be interesting to visit the www.dns-ok.us sites to find out if your home router is still maliciously configured.
An interesting thing about this cleanup is that the operator companies’ assets already have been seized. So one might think that the story should end there. But the many variants of malware released over the past several years that made these DNS setting modifications supporting click-jacking efforts may have turned off AV and OS update functionality. And internet infrastructure operators have been trying their hardest to work within the law on the issue and notify network administrators of infected systems on customer networks. But that doesn’t mean systems get reconfigured and/or cleaned.
Heck, even the operators’ organizations have been simplified for the media. Most of the seized assets from the front companies have all been referred to as “Rove Digital”. But there are many more names that these operators worked under, out of New York, the Ukraine, Russia, California, Estonia, Denmark, and Cyprus. It’s a confusing list that you probably haven’t seen, but includes Furox, Tamme Arendus, SPB Group, Cernel, Internet Path, Promnet Limited, ProLite Limited, and Front Communications. While the finger is simply pointed at “Rove Digital”, millions of dollars “allegedly” were moved/wired through all of these organizations.
The clickjacking examples noted by prosecutors were redirections from all the major search engines’ (Google, Bing, Yahoo!) results that most everyone would recognize: from the real iTunes link to a spoofed iTunes store, from a Netflix link to a pretty bogus “BudgetMatch” gimmick, from the IRS link to “H&R Block” tax help.
If your upstream provider hasn’t modified your DNS resolution, you may visit sites like dns-ok.us and see this red, positive DNSChanger DNS modification detection:
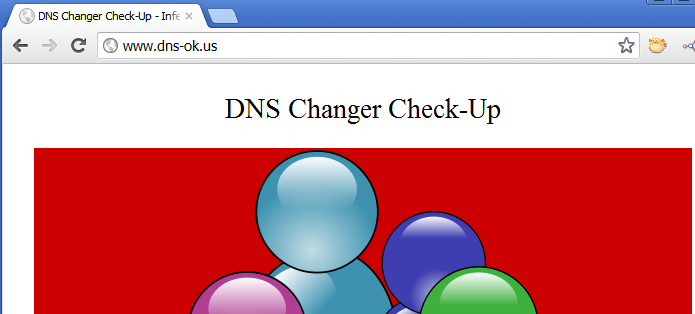
or this one here:
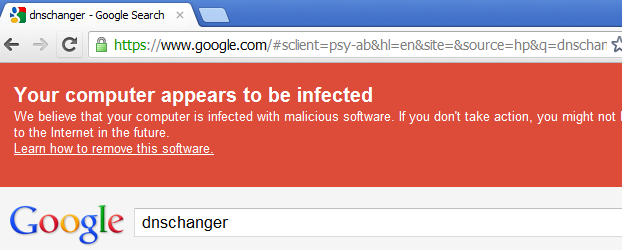
But, then again, you may see this on the same machine that had a DNSChanger infection and needs to be fully cleaned, having triggered the sites above:
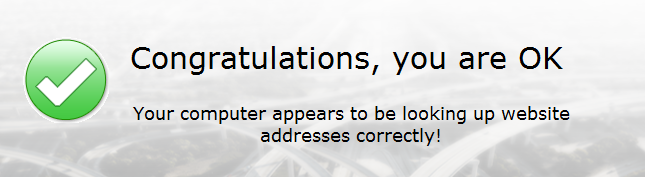
So, imho, working with software that performs checks for you, visiting the DCWG sites and then manually checking home/business routers is the best way to go if you are concerned that a DNSChanger variant infected your system and reconfigured DNS settings on your workstations or router.






















DNSChanger – Last Call on Cleanup