
The internet is full of infected hosts. Let’s just make a conservative guesstimate that there are more than 40 million infected victim hosts and malware serving “hosts” connected to the internet at any one time, including both traditional computing devices, network devices and smartphones. That’s a lot of resources churning out cybercrime, viruses, worms, exploits, spyware. There have been many suggestions about how to go about cleaning up the mess, the challenges are complex, and current cleanups taking longer than expected.
Mass exploitation continues to be an ongoing effort for cybercriminals and a major problem – it’s partly a numbers game for them. Although exploiting and infecting millions of machines may attract LE attention at some point, it’s a risk some are willing to take in pursuit of millions of dollars that could probably be better made elsewhere with the same effort. So take, for example, the current DNSChanger cleanup. Here is a traditional profit motivated 4 million PC and Mac node malware case worked by the Fbi, finishing with a successful set of arrests and server takedown.
When DNSChanger was “taken down”, only the “Rove Digital” DNS servers were handled, even though the statement read: “Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise”. While victims might not commonly be seen as a part of an enterprise, leaving the 4 million DNSChanger infected hosts connected to the internet, with many failing to download Windows updates, may leave open a window of opportunity for other cybercriminals. And even though past botnets have been partly handled by communicating with the malicious bot code itself from usurped C2 servers, those steps are being avoided again. Bredolab (approximately 3 million or more infected hosts), Coreflood/Afcore (infected over 2 million hosts) are probably the two largest recent examples of LE sending down commands to help effectively remediate botnets. Without this type of intervention, how is the cleanup going four months later?
Not all that well, it would seem. Approximately a half million hosts of the 4 million were infected in the US and they are not being cleaned up as planned. Meanwhile, there is a looming early March deadline for the DNSChanger Working Group to remove their Fbi/ISC DNS server replacements for the Estonian cybercrime managed malicious DNS servers. One ISP alone requested more time for the remaining 50k infected hosts on their networks. And the Fbi foresees enough of a problem that they requested the judge setting the original March 8th cutoff date to move the DNS server cutoff to July 9th, effectively doubling the amount of time allowed to clean up DNSChanger infected hosts.
A variety of voices claim that around half of the Fortune 500, hundreds of businesses, and many government agencies all maintain systems that would simply not be able to resolve domain names and become unusable if the replacement DNS servers were taken down in early March.
Which leaves the dangling question, is this extension really all that great an idea? Rick Wanner over at the SANS desk questions its value…”Frankly I am on the fence about whether or not an extension is a good idea. I certainly don’t want to entertain the possibility that the companies that I do business with, and entrust my personal information to, may take more than 4 months to cleanup a known malware infection.”
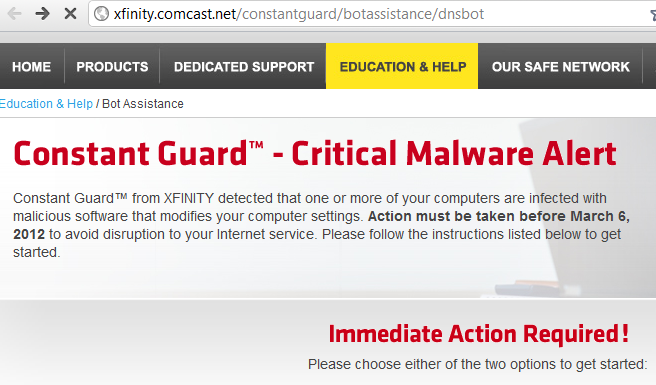
If places of business and government organizations can’t clean up their systems, what is being done to remediate residential systems? Well, DNS requests to the replacement servers are being monitored and the source IPs logged. These source IPs are distributed to the ISPs owning those IP addresses. From there, the ISPs are supposed to be able to track down the customers using the originating IP address and provide notification, who will then perform cleanup. The Comcast notification here:
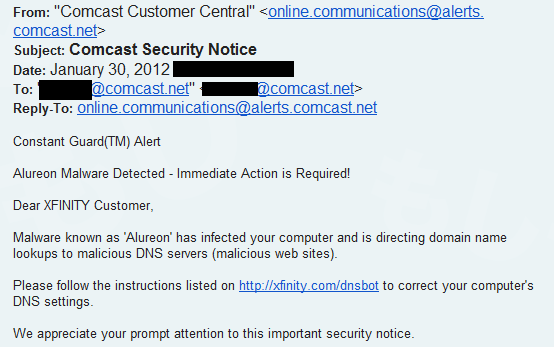
As you see, the link directs users to an urgent warning that immediate action is required. The individual can choose to attempt to clean it themselves for free, or they can choose a $100+ service to help them clean it up:
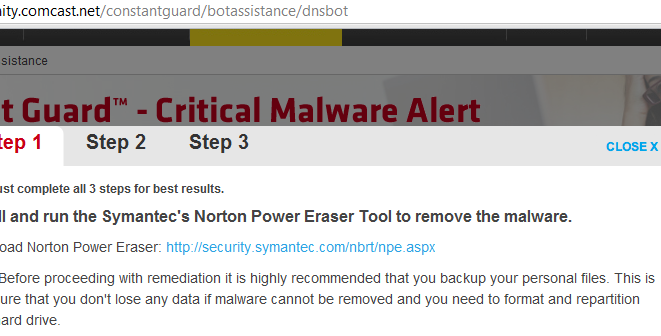
This tool is supposed to help users identify DNSChanger and remove it for free. Well, it does identify and remove variants of DNSChanger. On my system, it also annoyingly identified ImmunityDebugger, a fairly well-known debugger, as a potentially malicious software package to remove. It seems that this Eraser puts together a number of factors when rating the legitimacy of a given piece of software on a system, including “load points” it enumerates on the system and reputation scoring, and notes that changes made with the tool can be rolled back. In a way, this can be helpful for folks that know what they are doing and what they can ignore. It will help clean up more infections than just DNSChanger too as more of a general cleanup tool, which is a good thing. Maybe it doesn’t seem to be for everyone, but it’s great to see the ISP providing tools for cleaning up, because they are the contact point and the tools exist. It would be great to see universal tools and more specialized tools suggested to remove DNSChnager and other infections, giving choice to customers as to what company he or she entrusts with a remediation. For example, from our side we offer TDSSKiller and our scanning tools can be downloaded with full functionality as trials.
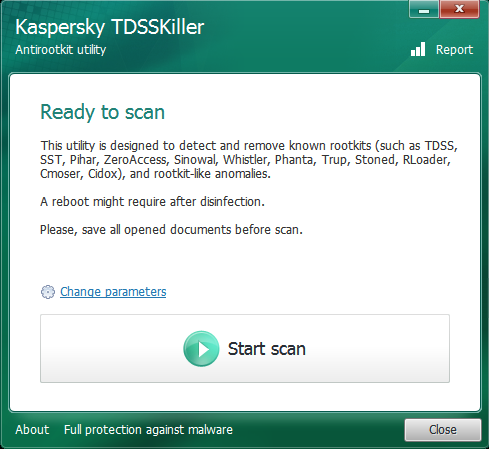
For more complex infections related to DNSChanger, the best toolset out there probably should include TDSSKiller. Continuously updated, run it and it cleans up the latest versions of Tdss among other rootkits. Tdss is a platform of its own that has been used to distribute DNSChanger alongside other malware known to disable updates and kill AV on systems, all making cleanup extremely difficult. From there, folks can use other scanners or tools to finish DNSChanger cleanup. Any way you look at it, underestimations and misunderstanding of infections, cleanup, and the need for effective anti-malware solutions are glaringly apparent because of Operation GhostClick remediation efforts.





















DNSChanger – Cleaning Up 4 Million Infected Hosts