
Brazilian internet users are being attacked this week with an interesting phishing scheme: the message is showing real personal data of the victim, in a clear attempt to trick users into installing a trojan banker on his machine.
The message is sent to the victim using the name of a big Brazilian bank and in the body it shows the complete name of the user and his CPF – the Natural Persons Register, the equivalent of a Social Security Number used by Brazilian government to identify each citizen:
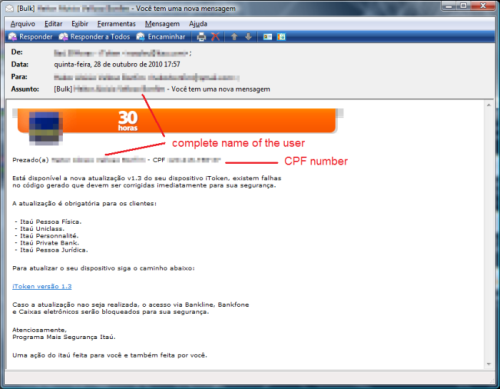
The CPF is one of the most important documents for anyone living in Brazil. The number is unique and is a prerequisite for a series of tasks like opening bank accounts, to get or renew a driver’s license, buying or selling real estate, receiving loans, applying for jobs (especially public ones), getting a passport or credit cards. Using such data it is possible to for a cybercriminal to impersonate the victim and steal his identity in order to access resources or obtain credit and other benefits in that person’s name.
This is a case when a data leak incident meets phishers. This kind of accurate information can only be obtained in data leak incidents. Not surprisingly it’s common that the Brazilian media notices criminals selling CDs with the full data of Brazilian IRS system where you can find a lot of sensitive data, including the CPF numbers. In a simple search you can find people in Brazil selling CDs of possible IRS and CPF numbers costing only $ 190.00.
This is not the first time Brazilians have been a target of phishing using real data: last year customers of an important airline company were victims of a phishing attack using their real names and the number of their rewards program.
Kaspersky detects the malware involved in this attack as Trojan-Downloader.Win32.Delf.agkm.
When receiving e-mails, even e-mails showing your personal data, you can’t be too careful.





















Data Leaks and Phishing: an explosive combination