What’s it all about?
In March 2017, a group of hackers calling themselves “the Shadow Brokers” published a chunk of stolen data that included two frameworks: DanderSpritz and FuzzBunch. The Fuzzbunch framework contains various types of plugins designed to analyze victims, exploit vulnerabilities, schedule tasks, etc. The DanderSpritz framework is designed to examine already controlled machines and gather intelligence. In pair, it is a very powerful platform for cyber-espionage.
How was this implant discovered?
We always analyze all leaks containing malicious software to provide the best detection. The same happened after the “Lost in Translation” leak was revealed. We noticed that this leak contained a tool in the “implants” category called DarkPulsar. We analyzed this tool and understood that it is not a backdoor itself, but the administrative part only. We also noticed some magic constants in this administrative module, and having created some special signatures based on them, were able to catch the implant itself.
What exactly can this implant be used for?
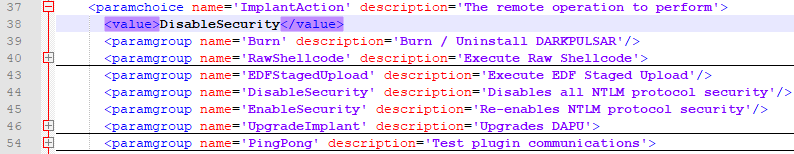
This implant supports 7 commands:
The most interesting are DisableSecurity and EnableSecurity.
- Burn – for self-deletion.
- RawShellcode – to execute arbitrary base-independent code.
- EDFStageUpload – Exploit Development Framework Stage Upload. Step by step it deploys DanderSpritz payloads to the victim’s memory without touching the drive. After this command is executed, the administrator can send to the victim any of the multiple DanderSpritz commands. (View details in the technical part of this report)
- DisableSecurity – for disabling NTLM protocol security. With help of this command, the malware administrator does not need to know a valid victim username and password to successfully pass authentication – the system will interpret any arbitrary pair as valid. (View details in the technical part of this report)
- EnableSecurite – the opposite of DisableSecurity.
- UpgradeImplant – for installing a new version of the backdoor.
- PingPong – for test communication.
How many victims?
We found around 50 victims, but believe that the figure was much higher when the Fuzzbunch and DanderSpritz frameworks were actively used. We think so because of the DanderSpritz interface, which allows many victims to be managed at the same time. The second point proving this suggestion is that after stopping their cyber-espionage campaign, the malware owners often delete their malware from victim computers, so the 50 victims are very probably just ones that the attackers have simply forgotten.
Which countries?
All victims were located in Russia, Iran, and Egypt, and typically Windows 2003/2008 Server was infected. Targets were related to nuclear energy, telecommunications, IT, aerospace, and R&D
What about the attack duration? Does it last long?
DarkPulsar’s creators did not skimp on resources in developing such an advanced mechanism of persistence. They also included functionality to disable NTLM protocol security for bypassing the need to enter a valid username and password during authentication. This indicates that victims infected with DarkPulsar were the targets of a long-term espionage attack.
Is the attack still active?
We think that after the “Lost In Translation” leakage the espionage campaign was stopped, but that doesn’t mean that all computers are rid of this backdoor infection. We cured all our users. As for users without our protection, we have several tips on how to check whether your system is infected and how to cure it by yourself. Note that to exploit this backdoor on infected victims, the attackers need to know the private RSA key which pairs to the public key embedded in the backdoor. It means that no one except real DarkPulsar’s managers can exploit compromised systems.
How to protect against this threat?
We can detect this threat with different technologies.
However, the standard recommendations remain the same:
- Keep your security products up to date
- Do not turn security product components off
- Keep your OS updated
- Install all security patches asap
- Use special traffic analysis tools and pay attention to all encrypted traffic
- Do not use weak passwords or the same password for several endpoints
- Use complex passwords
- Do not allow remote connections to endpoints with administration rights
- Do not allow domain administrators to be local administrators with the same credentials
Additional mitigation strategies can be found here:
- https://encyclopedia.kaspersky.com/knowledge/strategies-for-mitigating-advanced-persistent-threats-apts/
- https://encyclopedia.kaspersky.com/knowledge/strategies-for-mitigating-advanced-persistent-threats-apts-2/
- https://encyclopedia.kaspersky.com/knowledge/strategies-for-mitigating-advanced-persistent-threats-apts-3/
- https://encyclopedia.kaspersky.com/knowledge/strategies-for-mitigating-advanced-persistent-threats-apts-4/
Which proactive technologies do you have to protect users against such threats?
We use machine learning, cloud technologies, emulation, and behavioral analysis in combination with anti-exploit protection to provide the best proactive protection for our clients.
Who is behind this threat?
We never engage in attribution. Our purpose is to counteract all threats, regardless of their source or destination.
How was this implant used? Was it created for stealing money or just information?
We have not seen any techniques for stealing money in this implant, but it is worth keeping in mind that this implant can run any executable code, so its functionality can be increased significantly.




















DarkPulsar FAQ