
New techniques for obfuscating malicious code on websites are a good way to mislead both users and protection software alike. Recently, I came across an interesting attack against the osCommerce online shopping platform in which malicious script was injected into PHP files by exploiting a Remote File Inclusion vulnerability in osCommerce software.
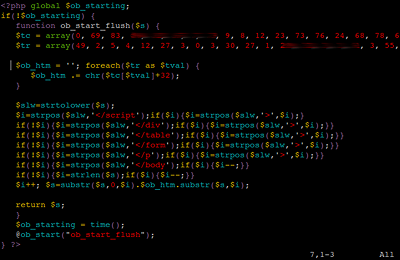
This PHP script works as an infector and is used to add the following code just after specified tags in HTML files and at the top of JavaScript files:
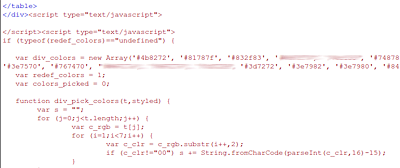
At first glance, this code doesn’t look as suspicious as it usually does – there is nothing that stands out: no tag, no unescape() function, nor is there an eval(). Instead, we just have a function which seems somehow related to colours displayed on the web page and an array filled with values pretending to be a hex representation of these colours. Unwary users could overlook this code assuming that it’s legitimate and belongs to the page, but if we follow it, we can see what it really does. The code takes the values from the array, converts them in some way and builds an ASCII string, so it can then use either the document.write or document.createElement method to append text to the web page source code. It the latter case, the created element has a type of text/javascript.
Now does it look suspicious enough to you? 🙂
If the second parameter of the div_pick_colours() function is specified, the function returns:
in which the last value always differs and depends on the current date and time. Otherwise, it returns the same URL but without tags. The given address is not active anymore, so we couldn’t tell what kind of threat it used to lead to.
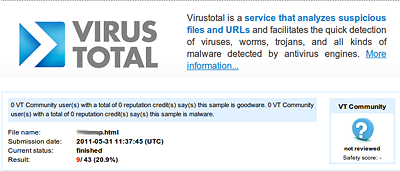
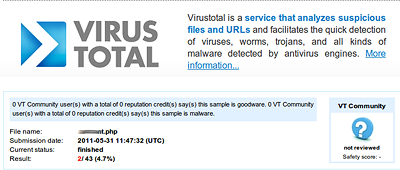
Kaspersky Lab detects this malware as Trojan-Downloader.PHP.JScript.a and Trojan.JS.Redirector.px. According to Virus Total, at the time of writing only one other AV vendor was able to detect the PHP part of this malware. For script injected into JS and HTML the ratio was as low as 20%.
How to secure your website from being infected with such malware and what to do in case of infection?
Two most important things are backup copies and regular scanning of all the files on the server. If you are using osCommerce or any other e-Commerce solution, you should always check for the software updates and install them as soon as they’re being released. Sometimes the time between disclosing a vulnerability and publishing patch can be shamefully long, so maybe it’s worth considering to reject some buggy features and delete vulnerable files from the server. Setting up password on the root directory is also a very good idea, as it prevent malware from modifying core files.





















Dangerous colours