
The Pornography category in the Parental Control system of Kaspersky Lab’s home user products is triggered over 4 million times a day. In other words, there are about 3,000 attempts to access adult content sites by minors every minute. This is confirmed by data collected worldwide using Kaspersky Security Network technology.
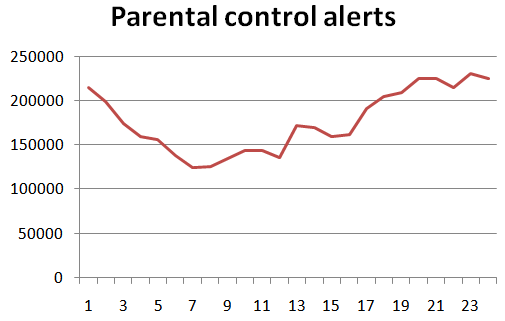
Number of times the Pornography category was triggered in the Parental Control module
As can be seen from the graph compiled by the Web Content Analysis Group at Kaspersky Lab, the majority of attempts to enter porn sites are made in the evening with a peak of activity at 11 pm.
The Parental Control module implemented in Kaspersky PURE and Kaspersky Internet Security 2011 allows parents to restrict the time that children are permitted to use the Internet and the computer. They can also restrict the download of inappropriate files from the Internet, regulate access to specific programs and sites and log their children’s instant messaging and social networking communications on ICQ, MSN and other similar sites.




















Curious kids: 3,000 attempts to visit porn sites every minute