
If you’re reading this, you’re probably not a cat, so curiosity won’t kill you. But it can result in someone getting hold of your confidential data.
In my blog about Michael Jackson, I mentioned that Britney Spears had her Twitter account hacked and news of her death posted on her own site. The vulnerability which was exploited has been fixed, the post was deleted, and Britney (or one of her staffers!) has posted saying the singer is alive and well. (I was glad to see that message, because Britney is giving a concert in Russia soon, and tickets are selling fast!)
Britney’s post hasn’t stopped the spammers though – we just picked up the message shown below:
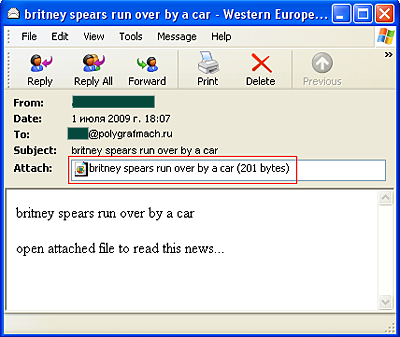
Another prime example of spammers exploiting that vulnerability called “curiosity”. Anyone who’s foolish enough to open the attachment is going to find themselves saddled with Trojan-Spy.Win32.Zbot, a program designed to steal personal data.
Patching technical vulnerabilities is easy; eliminating human vulnerabilities is a lot more difficult.






















Curiosity killed the cat