
Introduction
This article provides an analysis of recent developments regarding attacks launched by malicious programs against the clients of financial organizations. This article will focus primarily on the struggle for control between financial malware, also known as crimeware1, and the antivirus industry and will also examine the confrontation arising between crimeware and the financial sector as a whole.
This article will not stop to look at the methods employed to infect users’ computers, nor will it detail the other malign tactics, such as phishing and social engineering, etc. used by the cybercriminals against financial organizations. Whilst these topics remain as hot as ever, they have been addressed in detail elsewhere in previously published articles. For example, here is one such piece written by a colleague: Attacks on banks.
This article aims to answer the question – is it possible to effectively stem the tide of malware targeting the financial industry under present day conditions?
This article is aimed primarily at experts and specialists working in financial institutions, as well as IT professionals with an interest in this particular area.
Before we proceed any further, let me first emphasize that all of the financial organizations’ ratings included in this article do not in any way reflect their reliability (or lack thereof) and have no correlation whatsoever to their vulnerability relative to other market players. These ratings often depend on the popularity of the system that a user happens to be working with. It would be inappropriate to draw any conclusions about the reliability of a bank’s security system based on the materials referenced below.
Cybercriminals on the offensive
More and more frequently these days, we hear about successful attacks perpetrated by the cybercriminals against the clients of financial organizations. More often than not, these malware-based attacks follow a well-trodden path: the search for a suitable victim and the infection of their computer, the theft of their online banking login credentials, followed by the subsequent withdrawal of the victim’s funds.
One recent classic example comes from the Zbot-toolkit family , which is also known as ZeuS.
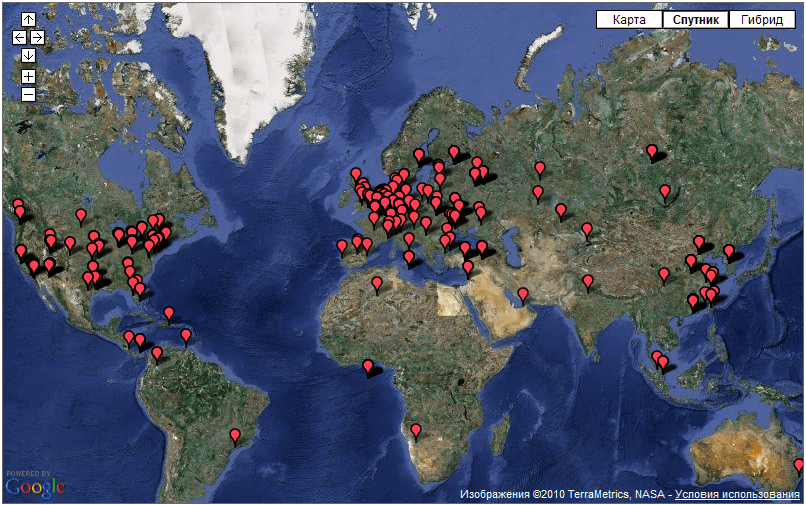
This is a malicious tool designed to steal the very data mentioned above – users’ login credentials for online banking accounts. ZeuS was very active throughout the whole of 2009 and continues to pose a considerable threat, seemingly laughing in the face of IT security professionals who have on many occasions attempted to shut down ZeuS botnets. More than 700 centers are still regularly up and running. Each command center controls an average of twenty to fifty thousand infected computers and based on those sorts of figures, one can only wonder at the number of potential victims out there. These command centers are spread right across the globe (see Figure 1):
Figure 1. The locations of ZBot/Zeus botnet command centers, from ZeuS Tracker data
Such widespread geographic diversity ensures the longevity of the botnet. As recent practice has shown, the botnet cannot be destroyed by merely closing down a few of the hosting sites. On 9 March, Roman Husse who was monitoring the botnet with the assistance of ZeuS Tracker noticed an abrupt decrease in the number of control centers and saw that it correlated with the disconnection of an Internet Service Provider by the name of Troyak. By 11 March the number of control centers had decreased to 104, however, two days later Troyak found a new teleservices provider and by 13 March the number of control centers had increased to more than 700 again, so the good news was short-lived.
The ZeuS family of malware is a long way from being the only toolkit that has been designed for stealing users’ login credentials with the aim of gaining access to their online finances. For example, the Spy Eye toolkit is not only capable of stealing the required data, but can also destroy its ZBot/Zeus competitor, meaning that there is a virtual war going on under our very noses. Equally notorious was the Mariposa botnet consisting of 13 million computers worldwide and which was shut down by Spanish police in December 2009.
On the control panel of the Spy Eye botnet, the cybercriminals have chosen icons in the style of little sacks of money to represent each user of an infected computer in the botnet.
Has the antivirus industry hit a technological brick wall?
These botnets act as greenhouses for the propagation of financial malware. It is with this kind of malware that the cybercriminals steal users’ money most readily, and they are constantly finding new victims. The numbers clearly show an increase in the quantity of malicious programs targeting the clients of banks and other financial organizations over the past few years (see Figure 2):

Figure 2. The increase in the number of unique malicious programs
used to steal money from Internet users
Source: Kaspersky Lab
The figures provided show an exponential quarterly increase in financial malware from the time when it first appeared to the present moment. What makes the situation worse is the fact that a large percentage of the malware in question is not detected by the antivirus programs of the majority of manufacturers when it first appears. For example, according to information provided by the ZeuS Tracker Center, during the middle of March more than half of the malware distributed by the ZBot/Zeus botnet has not been detected. That means that the malware attack was successful. By the time that users received adequate protection from the antivirus companies, the cybercriminals had already made off with all the information that they needed.
So why is this happening? For the sake of clarity, we will examine how the ‘treatment’ process works with typical antivirus databases. The process itself may differ somewhat from one antivirus developer to another, but in general, they all involve the same key steps (see Figure 3):
Figure 3. The update release process for signature databases
Now let’s take a closer look at each step:
- Step 1: From the moment that a cybercriminal launches a new piece of malware, an antivirus company’s number one task is to identify and obtain a sample of the malicious program. This goal can be achieved by a variety of means: the file is sent to victims, received by automatic interception or malware collection systems, or received as part of a file exchange with partners, etc. However, considering the proliferation methods used by malware, despite the large number of channels by which samples can be obtained, it is not always possible to promptly obtain an ITW (In-the-Wild) samples , or In-the-Wild, sample.
- Step 2: After a sample is obtained, the process of analysis begins. This stage can be performed by automatic systems and by virus analysts. This stage results in the addition of signatures to the antivirus database.
- Step 3: The testing process begins after a signature is added to the antivirus database. The objective of testing is to identify any potential errors in the entries that were added.
- Step 4: Once the testing phase is completed, the updates are delivered to the users of the antivirus program.
It can be several hours between the appearance of a malicious file and a user receiving an antivirus update. This delay is due to the time required for each step of the above process. Of course, at the end of the delay, the user will have reliable protection. But the paradox is that this protection is usually a case of shutting the stable door after the horse has bolted. If a user’s computer is infected, then the victim’s personal data will already have been stolen by the cybercriminal. In the end, the antivirus database might help to alert a user to the fact that their system has been compromised, but the loss of data is irredeemable.
The cybercriminals are all too familiar with the update release process, from start to finish. They know all about the time it takes to update a database, and they are well aware that it is only a matter of time before their creations are detected. That is why they often choose the following plan of attack: they release a malicious file, then a few hours later when the antivirus programs have started to detect it, they launch a new attack with another of their creations, each time gaining a small window of opportunity a few hours wide — and so on, and so on. As a result, even though the antivirus industry is capable of providing reliable threat detection, the good old antivirus technologies of yesteryear struggle to keep up, meaning that protection is not always as immediate as it really needs to be.
In summation:
- The response time of most antivirus technologies such as signature-based and generic detection do not meet today’s response time needs. Meaning that a malicious program will often steal users’ data and relay it to the cybercriminals even before a new entry is made to the antivirus database, and before the end-user receives an antivirus update;
- The number of crimeware attacks on the clients of financial organizations is growing exponentially.
Financial organizations and client protection
Given the situation described above, when antivirus updates lag noticeably behind the contemporary threat level, financial organizations try establishing and implementing their own methods of client authentication in order to minimize risk and maximize their resistance to the efforts of the cybercriminals.
It must be acknowledged that of late, many leading financial organizations have started to introduce additional solutions and methods for the electronic authentication of their clients. Some of them are listed below:
- The introduction of TAN codes (Transaction Authorization Numbers, a one-time password for transaction confirmation)
- Virtual keyboards
- Binding clients to a fixed IP address
- Secret questions and keywords
- The use of dongles or USB drives for additional authorization
- Biometric systems of authorization.
We are not going to stop and talk about the methods that the cybercriminals use to overcome these obstacles as this has already been covered in detail in the ‘Bank Attack’ article mentioned above. However, we ought to point out that they do know how to ‘cheat’ the protection systems in place and that their methods are indeed quite successful.
Certainly, the measures taken by the financial institutions have made life for the cybercriminals much more difficult, but at the same time, these measures have not become a panacea. News about such losses continues to flow in much the same way that reports continue to be received from any front line.
- FDIC: during the third quarter of 2009, American companies lost $120 million (almost all of these losses connected with malicious code) computerworld.com;
- UK Cards Association: losses from the online banking sector in the UK during 2009 have grown by 14%, totaling some 60 million UK pounds;
- FBI: in 2009 in the USA cybercriminals stole more than half a billion dollars from users, which is twice as much as in 2008 [PDF 4,77 Mb].
According to data from Kaspersky Lab based on the results for Q1 of 2010, the list of the most popular financial organizations targeted by the cybercriminals is as follows:
| Organization | Percent of total attacks |
| Bradesco group | 6.65% |
| Banco Santander group | 4.71% |
| Banco do Brasil | 3.92% |
| Citibank | 3.74% |
| Banco Itau | 3.33% |
| Caixa | 2.93% |
| Banco de Sergipe | 2.84% |
| Bank Of America | 2.36% |
| ABN AMRO banking group | 2.28% |
| Banco Nossa Caixa | 1.39% |
| Other | 14.51% |
Table 1. The top ten financial institutions targeted by malicious users (Kaspersky Lab)
This list has remained practically unchanged for the last few years.
Most of the targets are Brazilian banks. This trend is examined in Dmitri Bestuzhev’s article “Brazil: A country rich in banking Trojans“.
According to data provided by Kaspersky Lab, the number of banks that suffered from similar attacks during the first three months of 2010 is approaching one thousand.
Thus it is obvious that the cybercriminals are constantly finding new and more sophisticated ways of getting their hands on users’ information, despite the introduction of additional protective measures taken by the banking fraternity to protect their online clients.
In general:
- Financial institutions have introduced additional means of authorization, and cybercriminals have responded with new ways to bypass these updated security methods. The process will continue in this fashion: adding more security – finding another loophole – adding more security – finding another loophole, and so on.
- The amount of losses resulting from the actions of the cybercriminals is constantly on the rise.
Do viable solutions exist?
Now we will try to answer the main question: is it possible to counteract crimeware given today’s realities?
Let’s consider an overview of the problems outlined above that affect banks and other financial institutions and which need to be resolved as soon as possible.
- The delay in providing antivirus database updates. Quite simply, the time it takes for an end-user to obtain an update after the emergence of a new malicious ITW program does not meet today’s needs;
- The number of threats targeting the clients of financial institutions is growing exponentially;
- The security methods offered by financial organizations do not always resolve the problem of client fund losses in cases where a Trojan is used.
One could be forgiven for thinking that the picture looked very bleak indeed. The antivirus industry’s response time simply isn’t quick enough, malicious users remain at large and bank clients are not always sufficiently protected. However, all is not lost. Technologies are constantly developing and today’s leading antivirus companies do have solutions capable of repelling the attacks of the cybercriminals.
At this moment, some of the players in the antivirus market are already using in-the-cloud technologies. These assist greatly in detecting and blocking malware content, as well as limiting its sources. Here we are speaking about client-server technologies that analyze metadata containing information about malware activity on the users’ computers. However, the metadata can only be sent with the permission of the user and does not contain any private information.
This technology differs from antivirus database detection methods in how it analyses the sample. The antivirus engine can only analyze a sample according to fixed rules, such as recognizing odd behavioral patterns for example. The online analysis of metadata received from many users simultaneously allows the detection of ‘suspicious activity’ and the consequent blocking of the detected threat, thereby preventing the problem from spreading. In practice, users of such distributed networks can receive protection just a few minutes after the appearance of any threats.
As a result, using in-the-cloud antivirus technologies offers a number of advantages:
- Prompt detection within minutes after the emergence of a new threat, compared to the several hours required to update antivirus databases;
- A considerably increased level of detection for antivirus products, since new technologies are combined with tried and trusted methods; this approach is proven to be very effective at identifying new threats;
- Not only the immediate detection and blocking of the threats themselves, but limiting their spread as well;
- An added benefit to this technology is that it also reveals the big picture: at what time an attack took place, at what location, who launched the attack, the number of victims and the number of protected users, etc.
So what does it bring to the financial organizations? The solutions described can warn the financial institutions about the appearance of any new threats aimed at their clients automatically and in real-time. Such warnings may contain detailed information about the threats and instructions on how to fight them.
Also in demand is a service to provide financial organizations personal access to a so-called ‘situation room’. This is a type of web resource that requires a personal login name and password. Visitors can obtain a great deal more information than what is available in email notifications. For example, an online situation room would include reports and analyses relevant to an organization, its region, and the sources of attacks against an organization’s clients.
However, the result of introducing this kind of notification and reporting system may not be optimal for a number of reasons:
- Not all bank clients have antivirus programs installed on their computers, and that makes it difficult to get all the details of an attack.
- In order for information to be analyzed centrally and in full, all online banking clients would have to use the same antivirus program, which is simply impossible on a practical level.
- There is also a trust issue: financial institutions strictly forbid the sending of any client-related information to external companies due to the high risk of losing the valuable data or penetration of their networks.
All of these factors complicate the identification of targeted attacks.
To get a complete picture of the cybercriminals’ actions in relation to the banking world, the most opportune method is direct cooperation between the antivirus companies and the financial institutions.
- It is feasible to integrate a malware detection solution into the client side of online banking as no personal data would be required for this. The introduction of this kind of a service could be integrated into a security policy, which would reduce the banks’ outgoings on insurance compensation and fines in the future.
- Initial automatic threat analysis centers could be managed by a bank’s own security service, which would allow them to conduct analyses independently as needed. Large financial corporations typically have their own in-house IT departments these days, and with full control over the data it receives, an in-house security service could independently make decisions about what information gets sent to an antivirus company for analysis. Keep in mind, setting up this kind of analysis center within a financial company is only really advisable if the company wishes to control the flow of the data that is to be processed and wants to engage in the attack analysis process. This is an optimal solution for large market players for the reason mentioned above: the existence of an in-house IT department capable of conducting analyses into malware attacks.
- Users of online banking services would receive timely information from the analytical centers about of the neutralization of new threats and their sources
As a result, stronger collaboration among antivirus companies and financial institutions in the fight against crimeware could help kill two birds with one stone. Financial organizations could take this approach in an effort to minimize risks and reduce payments incurred from these types of incidents. Antivirus companies would be afforded the opportunity to more effectively combat targeted attacks.
Government support
Up to this point we have been looking at two parties who are locked in combat with the cybercriminals: the antivirus companies and the financial organizations. However, there is one more participant who despite all the opportunities it has to become involved is not playing anything like an active enough role – it is the government.
Without governmental support the possibility of defeating the cybercriminals is minimal. Countries have borders, but the Internet does not and this gives the cybercriminals complete freedom to act at will. For example, is it possible for a Korean bank to quickly shut down a Brazilian malware host, sticking strictly to all the procedures of state and respecting international law along the way? Or is it possible for a Brazilian bank to do the same in China? The answer is obvious, in both cases it is a resounding ‘No!’ To take the fight to the cybercriminals without any efficient mechanisms for the cooperation of the necessary authorities from the different countries is problematic to say the least. Such a struggle resembles a tug-of-war. As soon as any new technologies appear that target the cybercriminals activities, the cybercriminals respond by developing some new means to bypass it. The process then starts all over again, ad infinitum.
The table below identifies the geographical distribution of malicious hosting services spreading crimeware in the first quarter of 2010.
| Country | Percent of total attacks |
| Brazil | 30.28% |
| USA | 26.55% |
| China | 7.39% |
| Russia | 5.70% |
| Germany | 4.41% |
| France | 3.26% |
| Spain | 2.88% |
| Great Britain | 2.10% |
| South Korea | 1.53% |
| The Netherlands | 1.39% |
| Others | 14.51% |
Table 2. The top ten countries hosting resources to which crimeware is most often linked.
Source: Kaspersky Security Network (KSN)
Conclusion
We have touched on a number of difficulties that antivirus companies and financial institutions face today in the fight against cybercrime and the theft of money from online banking clients. We have also examined one potential solution to the problem.
This solution can be applied to other systems in addition to online banking. It could also be used to effectively monitor attacks against online gamers, e-money systems and exchange platforms. It is worth noting that these attacks are registered a great deal more often than attacks against online banking systems.
It is without doubt necessary to mention once again the major role that governments should be playing in this field. Without state support very little will ever be accomplished in the fight against cybercrime. The problem will remain unresolved until such times that effective and efficient mechanisms exist for the necessary communication and interaction to take place between the relevant authorities.























Crimeware: A new round of confrontation begins…