
For the second day in a row the topic of Nigerian spammers has cropped up. And once again they have been sending their heart-rending messages to none other than KL employees.
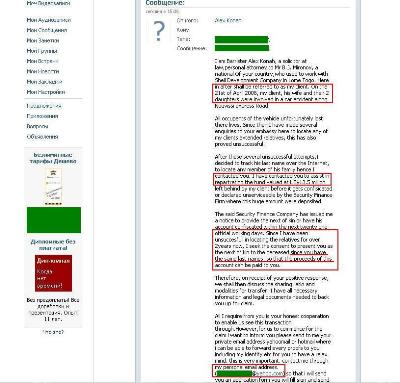
This time one of my colleagues received a message on the Russian-language social network Vkontakte which was a perfect example of the usual Nigerian scam letter:
It claims to be a message from the representative of a millionaire who died in an air crash with his family two years ago. Sounds familiar, right? 50 per cent of Nigerian letters start like this or in a similar vein. The “representative” goes on to talk about $13.5 million and how he has searched unsuccessfully for two years for any surviving relatives of the deceased. The letter claims that the lucky recipient has the same surname as the victim and therefore should inherit the $13.5 million, after the transaction costs have been covered. The “personal postal address” of the representative is attached of course.
So far, this is all pretty familiar. But apart from the fact it was sent to a KL employee there is another interesting aspect: it wasn’t received via e-mail as is usually the case for Nigerian letters, but on a Russian social networking site!
Virtually no information can be gleaned from the sender’s profile, except a name, city, school number and the year of graduation – amazingly, the “legal representative of the dead millionaire” only finished school this year.
That fact that this type of international spam found its way onto Vkontakte is, among other things, a sign of the gradual globalization of the resource. But the main conclusion to be drawn here is that Nigerian spammers have started to explore the vast world of Web 2.0.





















Continuing the Nigerian theme