
Computers have become an integral part of our lives. Every day more and more users and organizations use them to store data which is a type of property. Although most people take great care of their physical property, this is often not the case where virtual property is concerned.
The majority of users are still oblivious to the fact that someone somewhere may be interested in what they are doing. They still believe that there is nothing on their computers that is of value to cybercriminals and that they are invulnerable to malware. This article takes a look at the issue from the other side i.e. from the cyber criminals’ point of view.
Cybercrime has evolved considerably over the past few years with new technologies being created and applied. As a result, cybercrime is no longer committed by individual amateurs; it’s become a lucrative business run by highly organized groups.
It’s been variously estimated that during 2005 cyber criminals made from tens to hundreds of billions of dollars, a sum that far exceeds the revenue of the entire antivirus industry. Of course, not all this money was “earned” by attacking users and organizations, but such attacks account for a significant proportion of cyber criminals’ income.
In this two part report, the first part will examine attacks on users and the second part will discuss attacks on organizations. This first part includes an analysis of what kind of virtual property is attractive to cyber criminals and what methods are used to obtain user data.
Theft
What is Stolen
So what kind of virtual property is of interest to a cyber thief?
A study of malicious programs conducted by Kaspersky Lab virus analysts shows that four types of virtual property are most often stolen. It should be stressed that cyber scammers do not limit themselves to stealing the information listed below.
Information most frequently stolen from users includes:
- data needed to access a range of financial services (online banking, card services, e-money), online auction sites such as eBay, etc.;
- instant messaging (IM) and website passwords
- passwords to mailboxes linked to ICQ accounts, as well as all email addresses found on the computer;
- passwords to online games, the most popular of which are Legend of Mir, Gamania, Lineage and World of Warcraft.
If you store any of the information above on your machine, then your data is of interest to cybercriminals.
We’ll take a look at why such data is stolen and what happens to it once it has been stolen later in this article (Dealing in Stolen Goods). The following section provides an overview of how the information is stolen.
How it’s Stolen
In most cases, cyber criminals use dedicated malicious programs or social engineering methods to steal data. A combination of the two methods may be used for increased effectiveness.
Let’s start by taking a look at malicious programs which are designed to spy on users’ actions (e.g. to record all keys pressed by the user) or to search for certain data in user files or the system registry. The data collected by such malicious programs is eventually sent to the author or user of the malicious program, who can then, of course, do what s/he wants with the information.
Kaspersky Lab classifies such programs as Trojan-Spy or Trojan-PSW. The graph below shows the increase in the number of modifications in this category:
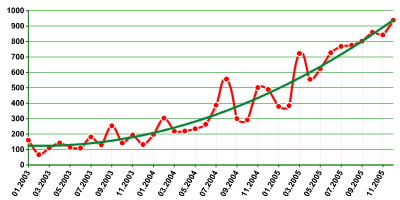
Figure 1. Growth in the number of malicious programs designed to steal data
Spy programs arrive on victim machines in a number of ways: when the user visits a malicious website, via email, via online chat, via message boards, via instant messaging programs etc. In most cases, social engineering methods are used in addition to malicious programs so that users behave as cyber criminals want them to. One example is one of the variants of Trojan-PSW.Win32.LdPinch, a common Trojan that steals passwords to instant messaging applications, mailboxes, FTP resources and other information. After making its way onto the computer, the malicious program sends messages such as:
Great stuff 🙂
Most recipients click on the link and launch the Trojan. This is due to the fact that most people trust messages sent by ICQ, and don’t doubt that the link was sent by a friend. And this is how the Trojan spreads – after infecting your friend’s computer, the Trojan will send itself on to all addresses in your friend’s contact list, and at the same time will be delivering stolen data to its author.
One particular cause for concern is that nowadays even inexperienced virus writers can write such programs and use them in combination with social engineering methods. Below is an example: a program written by someone who is not very proficient in English – Trojan-Spy.Win32.Agent.ih. When launched, the Trojan causes the dialogue window shown below to be displayed
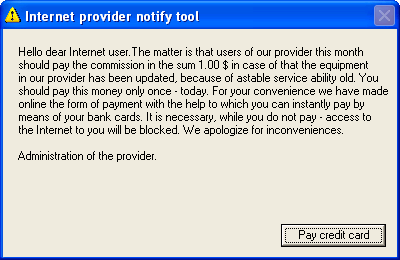
Figure 2. Dialog window displayed by Trojan-Spy.Win32.Agent.ih
The user is asked to pay just $1 for Internet services – a classic case of social engineering:
- the user is given no time to consider the matter; payment must be made the day the user sees the message
- the user is asked to pay a very small sum (in this case $1). This significantly increases the number of people who will pay. Few people will make the effort to try and get additional information if they are only asked for one dollar;
- deception is used to motivate the user to pay: in this case, the user is told that Internet access will be cut off unless payment is made;
- in order to minimize suspicion, the message appears to come from the ISP’s administrators. The user is expected to think that it is the administrators which have written a program via which payment can be made in order to save users time and effort. Additionally, it would be logical for the ISP to know the user’s email address.
The first thing that the program does is leave the user with no choice but to enter his/ her credit card data. As no other option is available, an obedient user will click on “Pay credit card”. The dialog box shown below in Figure 3 will then be displayed:
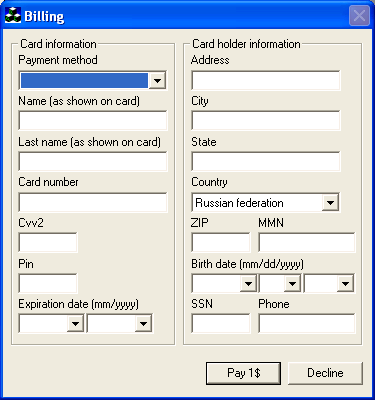
Figure 3. Credit card information dialog displayed by Trojan-Spy.Win32.Agent.ih
Of course, even when the user fills in all the fields and clicks on “Pay 1$” no money will be deducted. Instead, the credit card information is sent via email to the cybercriminals.
Social engineering methods are also often used independently of malicious programs, especially in phishing attacks (i.e. attacks targeting customers of banks that offer online banking services). Users receive emails supposedly sent by the bank. Such messages state that the customer’s account has been blocked (this is, of course, untrue) and that the customer should follow the link in the message and enter his/ her account details in order to unblock the account. The link is specially designed to look exactly like the Internet address of the bank’s website. In reality, the link leads to a cyber criminal’s website. If account details are entered, the cyber criminal will then have access to the account. Figure 4 gives an example of a phishing email:
Similar messages are also sent on behalf of various other organizations and bodies such as support services, social services etc.
However, cyber criminals aren’t only interested in credit card information. They are also interested in the email addresses which victim machines contain. How are these addresses stolen? Here, a crucial role is played by malicious programs which Kaspersky Lab classifies as SpamTools. These programs scan victim machines for email addresses, and the addresses harvested can be instantly filtered according to predefined criteria, e.g. the program can be configured to ignore addresses which clearly belong to antivirus companies. The harvested addresses are then sent to the author/ user of the malicious program.
There are other ways of planting Trojans on user computers, some of which are extremely brazen. There are cases where cyber criminals offered to pay website owners for loading malicious programs onto the machines of users who visited their websites. One example of this is the iframeDOLLARS.biz website: it offered webmasters a “partner program” that involved putting exploits on their websites so that malicious programs would be downloaded to the machines of those who viewed the sites. (Of course, this was done without the users’ knowledge). These “partners” were offered $61 per 1,000 infections.
Dealing in Stolen Goods
Unquestionably, the main motivation for stealing data is the desire to make money. Ultimately, all the information stolen is either sold or directly used to access accounts and get funds in this way. But who needs credit card data and email addresses?
The actual data theft is only the first step. Following this, cyber criminals either need to withdraw money from the account, or sell the information received. If an attack yields details which are used to access an online banking system or an e-payment system, the money can be obtained in a variety of ways: via a chain of electronic exchange offices that change one e-currency (i.e. money from one payment system) into another, using similar services offered by other cybercriminals, or buying goods in online stores.
In many cases, legalizing or laundering the stolen money is the most dangerous stage of the whole affair for the cyber criminals, as they will be required to provide some sort of identifying information e.g. a delivery address for goods, an account number etc. To address this problem, cyber criminals use individuals who are called “money mules”, or “drops” in Russian cyber criminal jargon. “Drops” are used for routine work in order to avoid exposure, e.g. for receiving money or goods. The “drops” themselves are often unaware of the purposes for which they are used. They are often hired by supposedly international companies via job-search websites. A “drop” may even have a signed, stamped contract which appears perfectly legal. However, if a “drop” is detained and questioned by law-enforcement agencies, s/he is usually unable to provide any meaningful information about his/ her employer. The contracts and bank details always turn out to be fake, as do the corporate websites with the postal addresses and telephone numbers used to contact the “drops”.
Now that the cybercrime business has matured, cyber criminals no longer have to look for “drops” themselves. They are supplied by people known as “drop handlers” in Russian cyber criminal jargon. Of course, each link in the chain takes a certain percentage for services rendered. However, cyber criminals believe that the additional security is worth the cost, especially as they haven’t had to earn the money themselves.
As for stolen email addresses, they can be sold for substantial amounts of money to spammers, who will then use them for future mass mailings.
A few words about online games. An average player may find what can happen to his/ her gaming account very interesting. Players often buy virtual weapons, charms, protection and other things for e-money. There have been cases where virtual resources have been sold for thousands of very real dollars. Cybercriminals can get access to all these riches without having to pay for them and can then sell them on at significantly reduced prices. This explains the growing popularity of malicious programs that steal virtual property used in online games. For example, by the end of July 2006 the number of known modifications of malicious programs that steal passwords for the well-known game Legend of Mir exceeded 1,300. Moreover, lately our analysts have started seeing malicious programs that attack not just one game but several at once.
Scams
Scams are designed to get users to part with their money willingly. In most cases scams take advantage of people’s love of getting something for nothing.
Business is continually expanding into new areas; more and more goods and services are being made available online, with new offers appearing every day.
Criminals have been quick to follow legitimate business into the online world and are now implementing online versions of real-world scams. As a rule, such schemes attract buyers or customers by offering goods at prices which are much lower than those offered legitimate vendors. Figure 5 below shows a fragment of the web page of one such Russian e-store:
As Figure 5 shows, the prices are impossibly low. Such low prices should arouse user suspicion, and make them think twice about buying things from such a website. In order to get around this problem, cyber criminals may give the following justifications:
- the sale of confiscated items;
- the sale of goods purchased with stolen credit cards;
- the sale of goods which were purchased on credit using fake names.
Such explanations are, of course, extremely questionable. However, many people choose to believe them: they think it’s all right to sell goods cheaply if the vendor didn’t have to pay for them.
When ordering, customers are asked to make a down payment or sometimes even prepay the full price. Naturally, once payment has been made, there will be no response from the cyber criminals’ phone numbers or email addresses. And of course, the purchaser won’t get his/ her money back. This scheme can be adapted for different locations. For example, in Russia goods purchased online are commonly delivered by courier. In this case cybercriminals may require an advance payment to cover delivery, explaining that couriers are often sent to addresses where no goods have been ordered, but the e-store owners still have to pay the courier. The cyber criminals then receive the delivery charge, while the customer receives nothing.
Bogus online stores are not the only trap for users. Nearly all criminal schemes which occur in the real world are reflected in equivalent scams in the cyber world. One more example of criminal online schemes is a “project” which offers users the opportunity to invest their money at a very attractive rate – so attractive that it is hard to resist. Figure 6 shows part of one of such “investment” website:
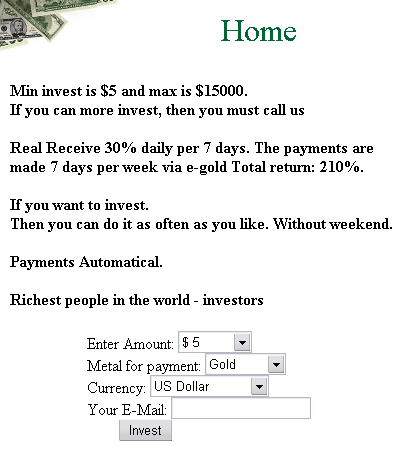
Figure 6. A scam “investment” website
Of course, there’s no need to comment on the interest rate offered. In spite of the ludicrous nature of such schemes, there are people who trust such “projects”, invest, and lose their money.
The list is endless: new bogus e-money exchange websites, new online financial pyramids (similar to real-world pyramid scams), spam which describes special secret electronic wallets that double or triple the amounts received and other similar schemes are surfacing all the time. As mentioned above, all these scams are designed to play on people’s desire to get something for nothing.
Extortion
In 2006 a dangerous trend became clear: cyber extortion is evolving rapidly in Russia and other CIS countries. In January 2006 a new Trojan program, Trojan.Win32.Krotten, appeared; this Trojan modified the system registry of the victim computer in such a way as to make it impossible for the user to use the computer. After the computer was rebooted, Krotten displayed a message demanding that 25 hrivnia (about $5) should be transferred to the author’s bank account, and the computer would be restored to normal. Computer literate users would be able to revert the modifications on their own, or re-install the operating system, thereby getting rid of the malicious program. However, most other families of malicious programs designed with extortion in mind are not so easy to get rid of, and the question “to pay or not to pay” was more often than not answered in the affirmative.
Krotten was distributed via online chat and on message boards in the guise of a sensational program that provides free VoIP, free Internet access, free access to cellular networks etc.
On January 25, 2006 Trojan.Win32.Krotten was followed by the first modification of Virus.Win32.GpCode. This malicious program was mass mailed and encrypted data files stored on the hard drive in such a way that the user could not decrypt them. Consequently, the user would have to pay for the data to be decrypted. Folders with encrypted data contained a readme.txt file with the following content:
|
1 2 3 |
Some files are coded by RSA method. To buy decoder mail: xxxxxxx@yandex.ru with subject: RSA 5 68251593176899861 |
In spite of the information that encryption was performed using an RSA algorithm, the author of the program had actually used standard symmetrical encryption. This made restoring data easier.
In the course of just 6 months, GpCode evolved considerably, using different, more complex encryption algorithms. Different variants of the program demanded different sums for decrypting data: the price varied from $30 to $70.
These programs were only the beginning. The number of families of programs designed for extortion increased during the year (Daideneg, Schoolboys, Cryzip, MayArchive and others appeared), and the programs also increased their geographical reach. By the middle of the year, such malicious programs had been detected in Great Britain, Germany and other countries.
However, other methods of extortion continued to be used as extensively as before. One example of this was the attack on Alex Tew, 21, a British student who created a website where he sold advertising space in the form of squares a few pixels across. Tew managed to make $1 million in four months with this unusual idea. Cybercriminals demanded that the successful student pay them a large amount of money, and threatened to organize a DDoS attack on his website if payment was not made. Three days after receiving the threat the student’s website underwent a DDoS attack. To his credit, he refused to pay.
But why is extortion and blackmail so popular among cybercriminals? The answer is simple: such crimes are facilitated by the victims themselves, who are ready to yield to any demands in order to have their lost or damaged data restored.
How to Avoid Falling Victim to Cybercriminals
The reader may get the impression that this article aims to scare users, and conclude that only an antivirus program can save their data. In actual fact, there is no antivirus solution that will help Internet users who don’t take elementary precautions. Below is a list of recommendations to help you avoid being easy prey for cyber criminals:
- Before making any payment or entering any personal data, find out what other users think of the relevant website. However, do not trust comments left on that site, as they may have been written by a cybercriminal. It’s best to get the opinions of people you know personally.
- Avoid giving any details of your bank cards over the Internet. If you need to make a payment over the Internet, get a separate card or e-money account and transfer the necessary amount to the card or account just before making a purchase.
- If an online store, investment fund or other organization has a website on a third-level domain, especially one provided by a free hosting service, this should arouse suspicion. A self-respecting organization will always find the small sum needed to register a second-level domain.
- Check where and when the domain used by the online shop was registered, where the shop itself is located, and whether the addresses and telephone numbers provided are genuine. A simple telephone call can solve several problems at once by confirming or dispelling your doubts. If the domain name was registered a month ago and you are told that the company has been in the market for several years, this warrants more detailed investigation.
- Do not pay money up front, even for courier delivery. Pay for all services only once you have received the goods. If you are told that people often order goods to be delivered to wrong addresses, meaning that couriers can’t deliver them, don’t believe this. It’s better to err on the side of caution and choose a different store than risk being swindled.
- Never reply to mailings made by banks, investment funds and other financial organizations: such organizations never make mass mailings. If in doubt, use the telephone to check whether mail really does come from the alleged sender. But don’t use the telephone number given in the message: if the message was sent by cybercriminals, the number given will also belong to them.
Conclusion
This first part of our article gives an overview of the most common ways to steal virtual property from Internet users. If you don’t secure your property, nobody else will. As the saying goes, forewarned is forearmed, and hopefully the information provided here has been useful.
The second part of this article will cover similar attacks on organizations, provide statistical information and look at the evolution of trends in the information black market.




















Computers, Networks and Theft