
In the first part of this article, we examined attacks on individual users’ and investigated what motivates cybercriminals, what personal data they steal and why. We include both descriptive material and statistics relating to such attacks.
The second part of this article aims to provide an overview of criminal attacks on organizations, companies, and institutions. These attacks can be divided into two categories: attacks on the organization’s resources, and attacks which target the organization’s clients. This section includes statistical data to give readers an idea of the scale of the problem.
Attacks targeting an organization’s clients
An attack on clients will lead to a lack of trust in the organization, company or insitution. Clients, not surprisingly, want a reliable system to perform whatever tasks they may have, and not a system which will cause headaches and potentially place data at risk.
For a long time, targeting clients to steal their data has been the most common type of attack on organizations. Exactly how such attacks are carried out, which malicious programs are used, and how users can be infected was examined in detail in the first half of this article. Here we will simply summarize the sequence of events followed to steal user data or other virtual property.
Currently, this type of crime is carried out according to a well-defined scenario. During the first stage, a remote malicious user gets the client’s account details in order to gain access to the account. Account details can be harvested by conducting mass mailing phishing emails, which will lure the user to the malicious user’s web site, or by infecting the user’s machine with a malicious program which will forward the data to a remote malicious user without the victim’s knowledge. Once a malicious user has account details, s/he will access the account and steal the property – whether it be money or something else – which s/he has set his sights on.
In the overwhelming majority of cases, the target will be an account which is related in some way to finance. The graph below shows the increase in the number of financial organizations whose clients were targeted between 2003 and 2006 (fig. 1):
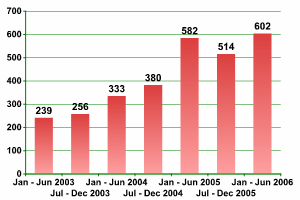
Fig 1: Growth in the number of financial insitutions whose clients were targetted using malicious programs designed to steal data
Source: Kaspersky Lab
As the graph shows, the number of victims is increasing every year. In addition to this, the number of attacks will increase in correlation to the increasing popularity of a particular bank, electronic currency exchange, e-payment or other online financial system.
Many organizations and institutions (banks above all) were so concerned about the unrelenting attacks on their clients that in the middle of 2005, they started taking steps to prevent data from being used once it had been stolen. One such measure was introducing two part authentification. Some companies even went so far as to place restrictions on the size and number of transactions which could be conducted with a specific period. The home page of many banks and institutions active in the area of finance also often display warnings about cybercriminals. (see fig.2)

Fig 2: Warning on a site relating to financial institutions
It remains to be seen how long such measures will continue to provide effective protection for users. However, the initial results seem to have been positive: during the first half of 2006, the overall percentage of malicious programs used for financial gain decreased for the first time in 3 years (see fig. 3).
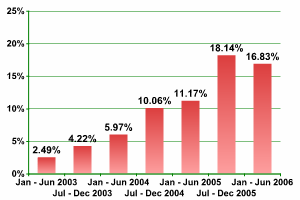
Fig. 3 Decrease in the percentage of malicous programs used to steal financial data (percentage of overall malicious traffic)
Source: Kaspersky Lab
Cyber criminals are constantly searching for new ways to surmount the obstacles placed in their way. In spite of the fact that the percentage of malicious programs targeting the users of online financial services has dropped slightly, their total number continues to increase, as does the number of malicious programs overall.
In addition to this, over the last year the number of malicious programs capable of attacking the users of several payment systems at the same time has risen (see fig. 4). One example is Trojan-Spy.Win32.Banker.asq, which targets almost 50 financial systems and insitutions at the same time, including paypal, caixabank, Postbank (Germany), and many other institutions around the world.
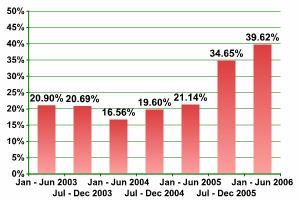
Fig 4: Increase in the percentage of malicious programs which attack several financial institutions/ payment systems at once (percentage of malicious programs targeting financial data)
Source: Kaspersky Lab
This tactic of targetting several payment systems and institutions at once naturally increases the likelihood of successfully finding victims.
We have chosen to use this part of the article to highlight attacks on clients of financial institutions and online financial services because these attacks are more common than attacks on the users of any other company or organization. However, cyber criminals cast their net widely. There are companies and insitutions which are not connected to finance, but they do accept online payment for their services. Such organizations will also naturally be of interest to cyber criminals. Kaspersky Lab virus analysts have detected malicious programs which target the clients of tour firms and transport companies, pawn shops and e-commerce sites, as well as a range of other companies.
Unfortunately, there’s no reason to think that the number of malicious programs used to commit such crimes is going to decrease. The first half of this article contains recommendations on how users can protect themselves, and these recommendations are also applicable to the clients and users of online banks, payment systems, and other companies and organizations.
Attacks on companies and institutions
Scams, blackmail and ransom demands imposed by cybercriminals on insitutions take place relatively frequently. However, the most common type of cyber crime which institutions fall victim to is the theft of confidential data.
Theft
Recently scammers have shown more and more interest in users’ personal data: email addresses, social security numbers, accounts for online games, and even PIN codes which, it seems, a great number of institutions store in internal databases. It’s not difficult to make a profit from stolen databases: there’s certainly a demand for them, which enables malicious users to make a good profit, spurring them on to commit further similar crimes.
Russia can be used as an example of how widespread data theft is, and this example shows that data can be stolen even from organizations that it’s hard to gain access to, such as the tax and customs services. Credit histories, databases containing customs declarations, car registration details, mobile phone numbers with addresses attached, and databases containing passport data are all freely available on the Russian black market. In some cases, the volume of data is so great that it won’t fit on to removable storage media, so instead it is sold on hard disk. The cost varies from tens of dollars to several thousand dollars, and the price varies according to how valuable the data could be, and also how recent it is.
However, such information isn’t only available in Russia. There is demand for data like this in other countries, as the scandals over stolen credit card numbers and social security numbers which took place in a number of other countries in 2006 show. One of these took place in the U.K., when malicious users managed to steal Mastercard details from 2,000 clients of an e-commerce site.
Naturally, those who buy stolen data are themselves criminals, who go on to use the information they have bought for financial gain in the real world.
Employees who aren’t overburdened with a conscience play an important role in data theft. Kaspersky Lab analysts are encountering spy programs written with the aid of insider information more and more frequently. For instance, there have been malicious programs created where malicious users have used internal logins and passwords from the organization under attack, as well as knowledge of the internal database structure of a specific organization. Withstanding an attack conducted using insider knowledge is extremely difficult, but it is possible.
It’s possible to protect users to some extent by implementing a few simple measures to reduce the risk of data theft. Organizations should take a holistic approach to protection, utilizing antivirus software, firewalls, spam filters, and monitoring and auditing the network infrastructure using appropriate tools.
Recently, the number of users infected via the Internet has risen. It’s very simple to do this: a remote malicious user hacks a web site, and installs a malicious program, which will then be downloaded onto the machines of users visiting the site, without their knowledge. Given this, organizations and companies should install an antivirus solution which contains a web component, or a separate product to monitor web content for the presence of malicious code.
In conclusion, we can only say that it seems likely data theft will continue to increase.
Blackmail, scams and ransom
Whereas scammers mostly target rank and file users rather than organizations, blackmailers act in the opposite way, targeting organizations rather than individuals.
The most common method used by cyber blackmailers is DDoS attacks. Specific demands are made in conjunction with the threat that an attack will be conducted: a specific sum is usually demanded, and failure to pay by the specified date will result in access to network resources being blocked. Conducting such an attack via the Internet enables remote malicious users to maintain anonymity without too much difficulty.
E-commerce and bookmaking sites are popular targets for blackmailers, along with any other organizations which would suffer significant losses if their access to resources is blocked.
The increase in the number of such attacks is partly due to the fact that victims often agrees to pay up. Surely, reasons the victim, it makes more sense to fulfil the conditions imposed by the malicious user? However, as research from IBM shows, those who pay are more often attacked than those who refuse to do so.
DDoS attacks, however, aren’t the only method which is used by cyber blackmailers. In the first part of this article, we looked at malicious programs which encrypt data on the victim machine. The authors of such programs demand a specific sum for restoring the data which is being ‘held hostage’. Organizations can also fall victim to such attacks. And while the majority of users wait for antivirus companies to provide a solution, organizations whose key business data has been encrypted may be unable to wait. They may decide to fulfil the criminal’s demands, leading to a vicious cycle of more attacks, and the creation of new modifications of malicious programs.
Other
The sections above have focussed on the loss of data. However, organizations naturally have other valuables, which may not be physically quantifiable. For instance, how much does a damaged reputation cost the company?
There have been cases where malicious users first hack a site, and then install dedicated malicious programs to mass mail spam. Spam will be sent in the victim’s name, who of course will be totally unconscious of this, and result in a loss of trust of both users and clients. The company’s reputation will suffer, and it will be difficult to fully recover from such a blow.
Over the past couple of years, the number of portals being hacked and malicious programs subsequently being downloaded to victim machines has increased dramatically. And here we’re not talking about small companies. Major commercial and governmental structures are at risk: malicious code has been injected into Microsoft sites, security, defence and law enforcement sites and others. This shows that although companies, organizations and institutions may be well acquainted with the risks, they do not necessarily take appropriate action.
Conclusion
Data clearly shows that the number of attacks and the range of malicious code utilized by cyber criminals is increasing.
Cyber criminals are constantly honing their methods and recruiting highly qualified people to join their ranks. The number of attacks and victims is increasing year by year, and new financial institutions also fall victim to such attacks. The consequences are not only financial losses: an organization’s reputation can be severely damanged, as can its IT infrastructure.
A holistic approach is needed when approaching the issue of security, with an appropriate focus on the issue, and the use of antivirus solutions, spam filters, firewalls, network monitoring and auditing tools. Such an approach is the only thing that will enable companies, organizations and institutions to effectively withstand the growing rise of cyber criminality.






















Computers, Networks and Theft: Part 2