
Introduction
Today we got a spam message with a fake e-card in Portuguese leading to an interesting piece of malware:
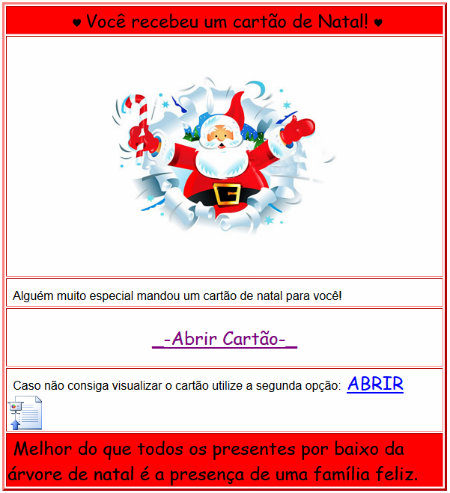
Header translation: You got a Christmas e-card. Somebody very special has sent this Christmas e-card for you. In case you are not able to visualize it, click here. Much better than any present is a happy family.
Malware behind it
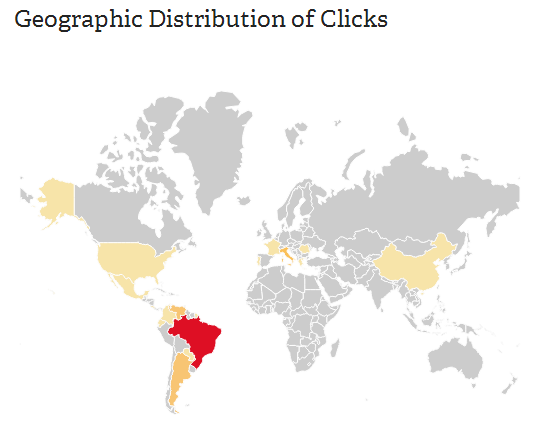
The link is a bit.ly short URL and shows that the campaign began today at 1 pm (December 20, 2013) with 628 clicks so far (6:15 pm ET). Most of the people who clicked on it live in Brazil:
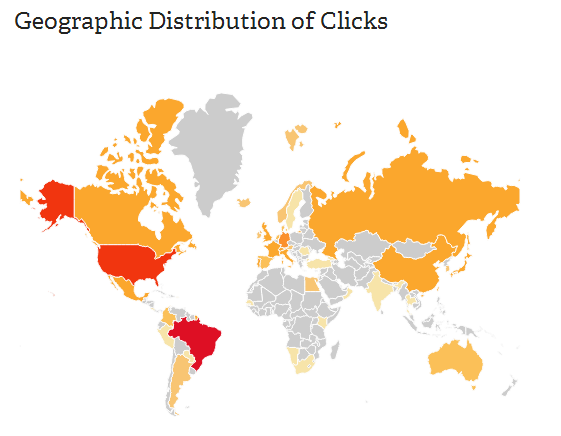
However if you check all statistics of the same Bit.ly user you may find another URLs leading to the same malware but on different domains with a total click number of 619 being USA this time the 2nd country with the most potential victims:
In both cases the malware is the same and it is:
CartaodeNatal (1).zip========================= 281e25d7a5041bb911d95b937b953d6d
CartaodeNatal.zip============================= 281e25d7a5041bb911d95b937b953d6d
The criminal behind it just prepared 2 different links: one of them is hosted on a purely cybercriminals server and the other one is located on a legitimate hacked Brazilian company web site.
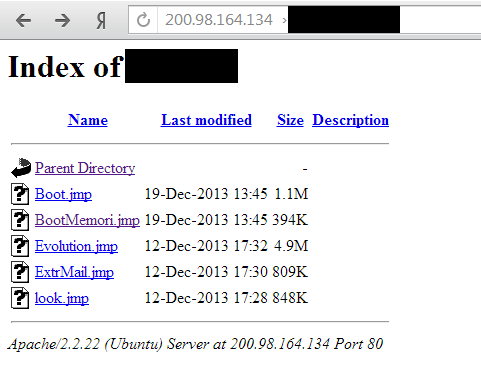
So what does 281e25d7a5041bb911d95b937b953d6d do? It-s a .cpl file detected as Trojan-Downloader.Win32.Banload.cpph and downloading other malicious and non-malicious files from Internet. All files are downloaded from a server located in Brazil:
The files are encrypted and can-t be run if you download them right from the server:
Once the initial Banloader .cpl is executed it will try to launch Mozilla Firefox from the command line, showing a Java update page (legitimate) even though by double clicking on it we have already given it permission to start its malicious activities. Disguised as a regular application update it will execute several command line processes in the background and it will create copies in the system to make the task of system cleanup much harder.
We can see from the dependency analysis and network traffic that this file has nothing to do with Java and it?s injecting the malicious code into the memory address of commonly used Windows-processes.
After all the actions have been performed in the victim-s system the user is asked to reboot the environment.
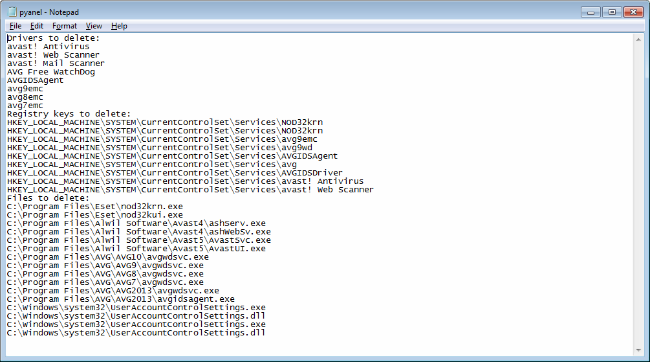
The initial Banloader downloads and executes The Avenger anti-rootkit in order to remove some AV products from the recently infected system. This the list of the files to be removed from the system during the reboot:
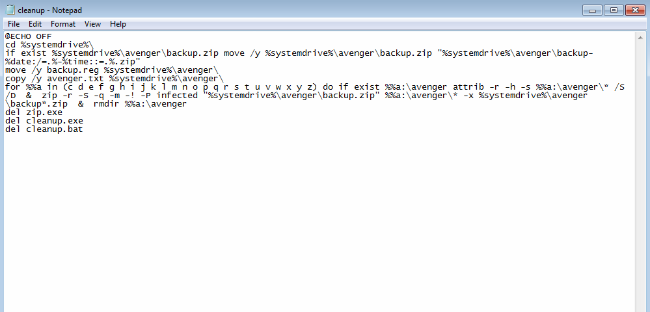
The cleanup Avenger batch file is the next one:
Finally the newly download banker itself is downloaded to the system as rundll32.cpl and executed via CurrentVersionRun key.
Who’s behind it and other interesting data?
It-s certainly somebody from Brazil. We found traces indicating that this criminal likes to play online games. Also an identical profile the same day posted on bit.ly 7 different URLs. Judging by the time he posted it seems to correspond to a normal work day shift, the activity begins around 9 am and finishes around 2 pm and today is Friday v a working day. That means this is his main ?job? v to code, to infect victim-s machine and to steal their money.
Another interesting data is the Santa Claus embedded into the original email is also shortlinked via bit.ly and pointing to a legitimate Brazilian government Web site. The bit.ly statistics shows there are 5707 clicks on it. In reality they are not real clicks but the previsualization made by potential victims via email providers. In other words if the email is configured to show external images in the emails, it will automatically open the original bit.ly url producing a click for the counter. So what’s interesting here? We-ve seen that total number of people who clicked on the mentioned fake e-card is 1247, while the total number of clicks on the Santa-s image is 5707. That means that 21.8% percent of people are very susceptible to the social engineering attacks, still making click while others are more careful and probably won-t click at all.






















Brazilian “Feliz Natal” – Give Me Your Money Now!