
Last September, in partnership with Microsoft’s Digital Crimes Unit (DCU), SurfNET and Kyrus Tech, Inc., Kaspersky Lab successfully disabled the dangerous Hlux/Kelihos botnet by sinkholing the infected machines to a host under our control.
A few months later, our researchers stumbled upon a new version of the malware with significant changes in the communication protocol and new “features” like flash-drive infection, bitcoin-mining wallet theft.
Now, we are pleased to announce that we have partnered with the CrowdStrike Intelligence Team, the Honeynet Project and Dell SecureWorks to disable this new botnet.
Last week, we set up worldwide distributed machines for this sinkholing operation and on Wednesday, March 21, we finally began the synchronized propagation of our sinkhole IP-adress to the peer-to-peer network.
After a short time, our sinkhole-machine increased its “popularity” in the network – which means that big part of the botnet only talks to a box under our control:
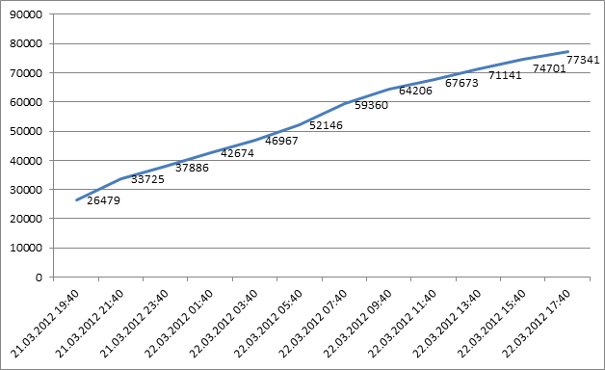
Number of unique bots after 24h
We also distributed a specially crafted list of job servers. This prevents the bots from requesting new commands from the malicious bot-herders. At this point, the bots can no longer be controlled by the bad guys.
However, a few hours after we started our takedown operation, the bot-herders tried to take countermeasures by rolling out a new version of their bot. We also noticed that the bot-herders stopped their network from sending out spam and DDoS-attacks. Also the botnets’ fast-flux-network list remains empty since a few hours.
After six days, we now have more than 116,000 bots connecting to our sinkhole.
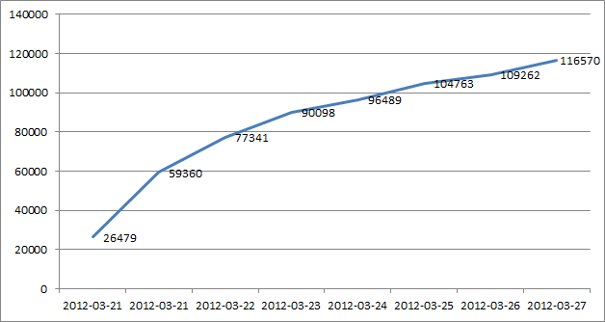
Number of unique bots after 6 days
Here’s a snapshot of the OS versions:
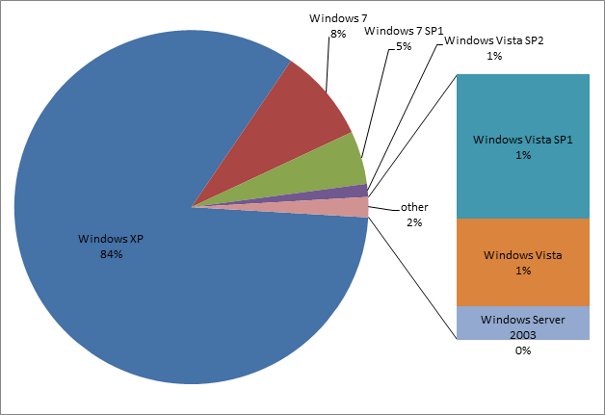
OS Versions
Most of the bots are located in Poland and the US:
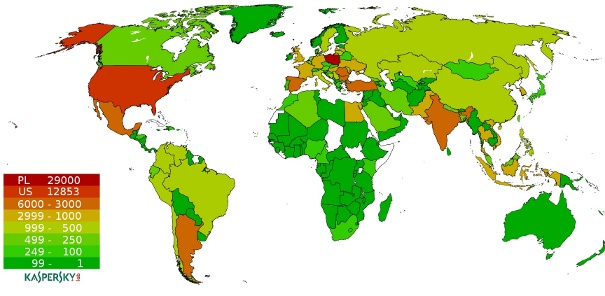
Countries with new Hlux/Kelihos infections
BACKGROUND
For the new take-down, the most important changes are located in the communication protocol. In the lowest layer the malicous creators changed the order of encryption and packing methods.
| № | Old Hlux | New Hlux |
| 1 | Blowfish with key1 | Blowfish with new key1 |
| 2 | 3DES with key2 | Decompression with Zlib |
| 3 | Blowfish with key3 | 3DES with new key2 |
| 4 | Decompression with Zlib | Blowfish with new key3 |
Taken from Marias blog post
Of course, the authors of that malware changed the encryption keys as well as the RSA keys used for signing parts of the message sent through the p2p-network.
| Old Hlux | New Hlux | |
| Controllers’ IP | RSA key1 | New RSA key1 |
| Update/Exec urls1 | RSA key1 | New RSA key1 |
| Update/Exec urls2 | RSA key2 | New RSA key2 |
Taken from Marias blog post
Last but not least, the hashing of the messages’ fieldnames is no longer used.
Please see also FAQ: Disabling the new Hlux/Kelihos Botnet




















Botnet Shutdown Success Story – again: Disabling the new Hlux/Kelihos Botnet