
Undoubtedly the cybercrime strategy is not just an eastern European matter. These attacks are committed through web applications like Malware Kits or Exploit Packs which look not only to centralize the stolen information, but also look to have a base platform that allows cybercriminals a place for rapid configuration (sometimes known as a Command and Control, or C&C).
Latin America has ceased to be a neglected region for cyber-attacks and has since become a suitable area for the local development of crimeware for managing botnets. This is further evidenced by the discovery of a criminal program, developed in Latin America (possibly from Peru), and called S.A.P.Z (Sistema de Administracin de PCs Zombi – Zombie PCs Administration System).

The botnet spreads malicious code that Kaspersky detects as Backdoor.Win32.SdBot.wtn which is designed to steal sensitive information from users via a phishing attack employing a methodology called local Pharming.
The local Pharming methodology modifies the “host” file that is in all operating systems to help manage redirection to certain web pages by their “host” name. In this attack, the “host” file is modified in order to redirect the victim to a fake website which is a clone of the an importante bank website of Peru.
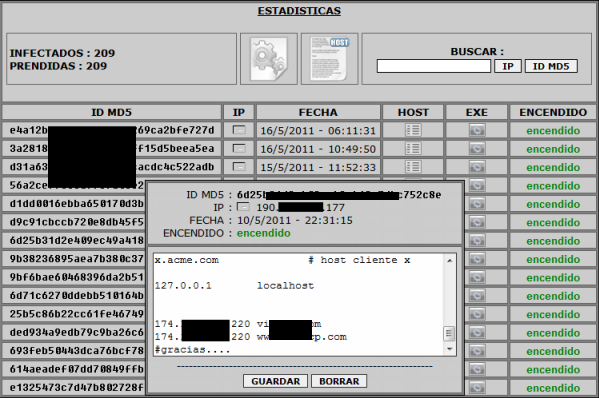
Despite the uncomplicated look of this system, the risk for the users is still very high. Using this strategy, criminals look to steal data from Peruvian users’ credit cards, but without limiting the infection strategy to just Peru.
The geographical distribution of this family of malware reveals the huge impact globally, where Latin America is not just in the margin.
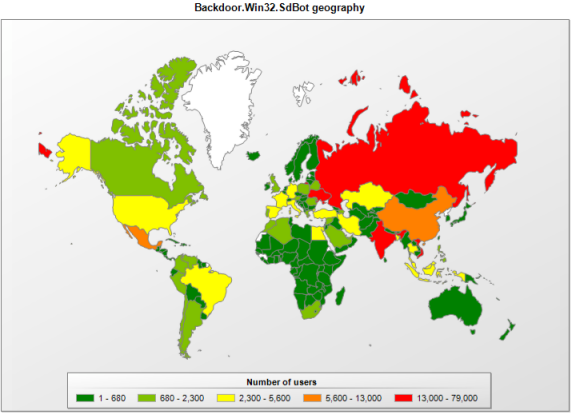
It is also clear that the underground market and economy has shifted to cover Latin America, too. Despite being relatively new, it is clearly on a quick path to maturity. This should be an alert for us to adopt security measures to avoid becoming victims.
We at Kaspersky Lab will continue to investigate and monitor the activities of this botnet.




















Botnet management from Peru