
Many mobile bankers can block a device in order to extort money from its user. But we have discovered a modification of the mobile banking Trojan Trojan-Banker.AndroidOS.Faketoken that went even further – it can encrypt user data. In addition to that, this modification is attacking more than 2,000 financial apps around the world.
We have managed to detect several thousand Faketoken installation packages capable of encrypting data, the earliest of which dates back to July 2016. According to our information, the number of this banker’s victims exceeds 16,000 users in 27 countries, with most located in Russia, Ukraine, Germany and Thailand.
Trojan-Banker.AndroidOS.Faketoken is distributed under the guise of various programs and games, often imitating Adobe Flash Player.
Preparing the groundwork
The Trojan is capable of interacting with protection mechanisms in the operating system. For example, it requests rights to overlay other apps or the right to be a default SMS application. This allows Faketoken to steal user data even in the latest versions of Android.
Once the Trojan becomes active, it requests administrator rights. If the user denies the request, Faketoken repeatedly refreshes the window asking for these rights, which leaves the victim with little choice.
The Trojan imitating “Yandex.Navigator” to request administrator rights
Once it has received administrator rights, Faketoken starts requesting the necessary permissions: to access the user’s text messages, files and contacts, to send text messages and make calls. These requests will also be repeatedly displayed until the user agrees to provide access.
The Trojan then requests the right to display its windows on top of other applications. This is necessary to block the device and steal user data by displaying phishing pages.
The Trojan requesting the right to display its windows on top of other applications
The final request at the preparatory stage is for the right to be the default SMS application – this allows Faketoken to covertly steal text messages on the latest versions of Android. The Trojan integrates the options necessary for the user to work with SMS. However, on some Android devices and versions when the user attempts to send an SMS via Faketoken it returns an error. As a result, the user cannot send SMS messages until they manually change the SMS application. The Trojan doesn’t like that, and will start requesting the right again.
Manipulations with application shortcuts can also be added to the preparatory stage. After launching, Faketoken starts downloading an archive containing file icons of several applications (the version being analyzed here has eight) related to social networks, instant messengers and browsers. Then it tries to delete the previous shortcuts to these applications and create new ones.
On the test devices the Trojan failed to remove the previous shortcuts which eventually led to the appearance of duplicates
It is not clear why it does this because the shortcuts created by Faketoken lead to the original applications.
Data theft
Once the shortcuts are installed, the next stage of the Trojan’s work begins – the theft of user data. Faketoken downloads a database from the server containing phrases in 77 languages for different device localizations.
Screenshot of the database with phrases in different languages
Using these or other phrases from the database, depending on the operating system language, the Trojan will show the user various phishing messages.
Examples of phishing messages displayed by the Trojan
If the user clicks on the message, the Trojan opens a phishing page designed to steal passwords from Gmail accounts. In addition to that, the Trojan overlays the original Gmail application with this page for the same purpose – to steal the password.
Phishing page imitating the login page of the Gmail mail service
However, the Trojan doesn’t limit itself to Gmail. Like most modern mobile Trojans, Faketoken overlays the original Google Play app with its phishing window to steal the victim’s bank card details.
Phishing page used by the Trojan to steal credit card details
The Trojan can also get the list of applications for attack and an HTML template page to generate phishing pages for the attacked applications from the C&C server. In our case, Faketoken received a list of 2,249 financial applications from around the world.
Example of the Trojan’s phishing pages designed for different applications
It should be noted that the Trojan integrates functionality enabling it to call some of the methods from the HTML page it received from the C&C server. As a result, in addition to the phishing functionality, the pages described above can get certain information about the device including the address of the Gmail account and, even worse, reset the device to factory settings.
What’s more, Faketoken can perform the following actions upon command from the C&C server:
- Change masks to intercept incoming text messages;
- Send text messages to a specified number with a specified text;
- Send text messages with a specified text to a specified list of recipients;
- Send a specified text message to all contacts;
- Upload all text messages from the device to the malicious server;
- Upload all the contacts from the device to the malicious server;
- Upload the list of installed applications to the malicious server;
- Reset the device to factory settings;
- Make a call to a specified number;
- Download a file to the device following a specified link;
- Remove specified applications;
- Create a notification on the phone to open a specified page or run a specified application;
- Start overlaying specified applications with a specified phishing window;
- Open a specified link in its own window;
- Run an application;
- Block the device in order to extort money for unblocking it. This command may include an option indicating the need to encrypt files.
Ransomware banker
As mentioned above, the ransomware functionality in mobile banking Trojans is now commonplace, after being pioneered by Svpeng in early 2014. However, the new Faketoken version can not only extort money by blocking the screen but also by encrypting user files.
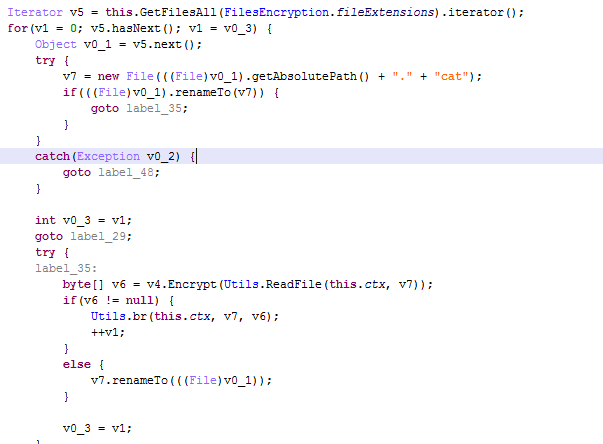
Screenshot of the Trojan code that renames and then encrypts files.
Once the relevant command is received, the Trojan compiles a list of files located on the device (external memory, memory card) corresponding to the given list of 89 extensions and encrypts them. The AES symmetric encryption algorithm is used, which leaves the user with a chance of decrypting files without paying a ransom. The Trojan receives the encryption key and the initialization vector from the C&C server. The encrypted files include both media files (pictures, music, videos) and documents. The Trojan changes the extension of the encrypted files to .cat.
In conclusion, we would like to note that file encryption is not that popular with the developers of mobile ransomware (at least currently), which may be because most files stored on a mobile device are copied to the cloud. In other words, demanding a ransom in return for decrypting them is pointless.
MD5
7faec9e6e630478ea5faa4a35f999c9f
64d59186e4f7af1bf06b3321fed00712
The banker that encrypted files































tom
Do yo have by any chance a list of the affected entities? if so, could you mail it to me?