
 The recent shutdown of SilkRoad 2.0 was just a small part of the events affecting the Tor network that unfolded last week.
The recent shutdown of SilkRoad 2.0 was just a small part of the events affecting the Tor network that unfolded last week.
Tor-related communities, such as privacy enthusiasts, but also cybercriminals (of course!), expressed worry after a global law enforcement operation targeted a number of illegal services based on Tor.
Operation Onymous, coordinated by Europol’s European Cybercrime Centre (EC3), the FBI, the U.S. Immigration and Customs Enforcement’s (ICE), Homeland Security Investigations (HSI) and Eurojust, resulted in 17 arrests of vendors and administrators running these online marketplaces and more than 410 hidden services being taken down.
The official announcement about Operation Onymous is available on the Europol website.
Here’s an incomplete list of .onion services that were taken down during this operation: Alpaca, Black Market, Blue Sky, Bungee 54, CannabisUK, Cloud Nine, Dedope, Fake Real Plastic, FakeID, Farmer1, Fast Cash!, Flugsvamp, Golden Nugget, Hydra, Pablo Escobar Drugstore, Pandora, Pay Pal Center, Real Cards, Silk Road 2.0, Smokeables, Sol’s Unified USD Counterfeit’s, Super Note Counter, Tor Bazaar, Topix, The Green Machine, The Hidden Market and Zero Squad.
Examples of seized .onion sites
At the sametime , reports appeared about a number of Tor nodes being seized by authorities:
Over the last few days, we received and read reports saying that several Tor relays were seized by government officials. We do not know why the systems were seized, nor do we know anything about the methods of investigation which were used. Specifically, there are reports that three systems of Torservers.net disappeared and there is another report by an independent relay operator.
You can read more on The Tor Blog about their Thoughts and Concerns about Operation Onymous.
The current state of the Dark Web
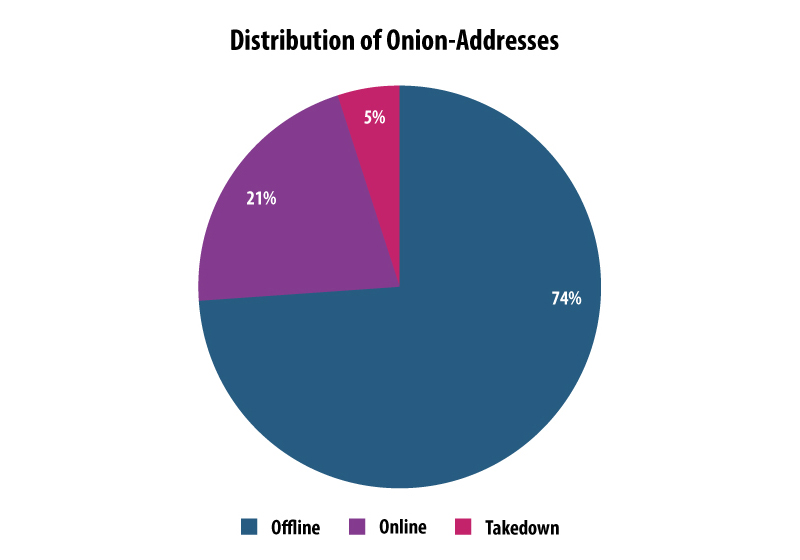
Of course, the takedown only affected some Onion sites – many are still alive. Right now there are 4 times more hidden websites online in the Tor network than those that were shutdown.
Cybercrime, just like any other illegal activity, is hard to eradicate completely. Whenever illegal services are taken down, the gap created will always be filled by other criminals willing to profit from the opportunity. The reality we have to accept is that there will always be demand for such services.
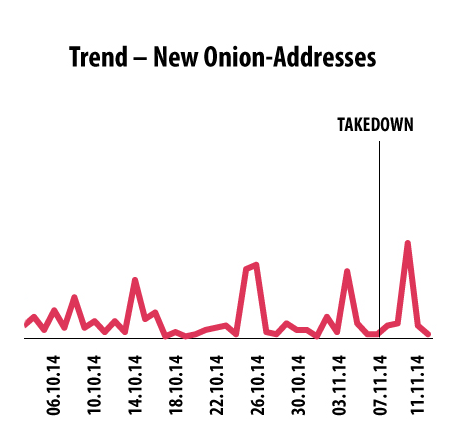
The following graph shows the amount of new .onion addresses appearing each day. After the takedown on November 7th, we noticed a higher than regular spike in the number of new hidden services being set-up.
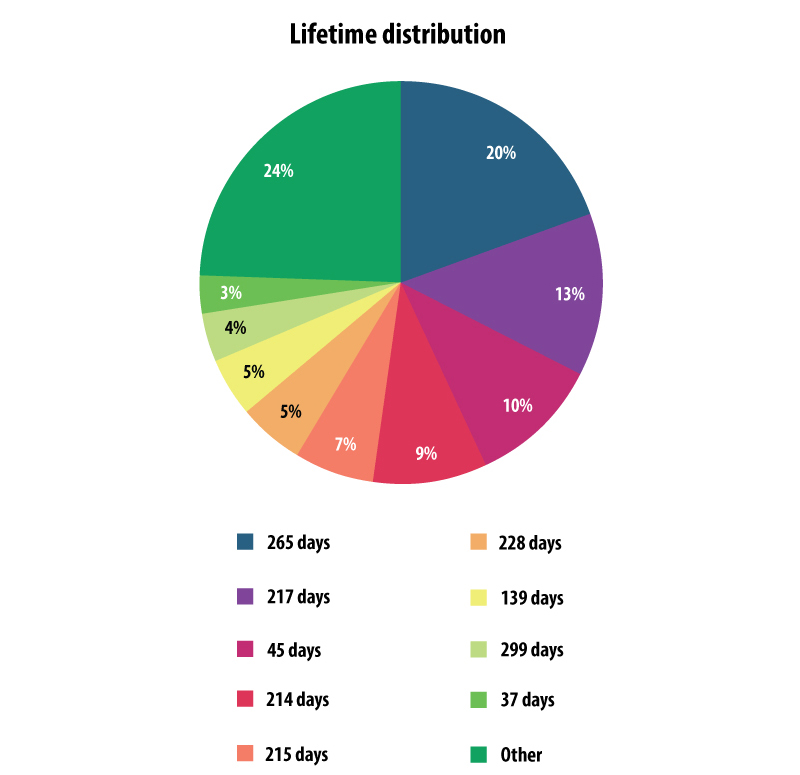
We’ve also analyzed the lifetime of the Onion-sites which were taken down last week. On average, most of them were alive for at least 200 days, but usually not more than 300 days – which the following graph shows. Just some were online for less than 2 months.
What does this mean for the Tor network and the Dark Web?
The most intriguing question which is raised by the media is – what exceptional tools one needs to compromise a hidden service? In theory, when you visit a hidden service, there is no way of knowing (either for you or for anyone else) the physical location of the web server behind it. For the theory to remain solid, three conditions must be met:
- The hidden service must be properly configured
- The web server should be impenetrable – no vulnerabilities or configuration errors
- The web application should have no flaws
If any of the 3 conditions is not met, it’s quite easy for a skilled person to essentially hack into that server and start to dig further.
Anyone familiar with Dark Net websites knows how poorly coded many of these websites can be. Just because a website’s physical location is obscured by Tor hidden services, it doesn’t mean this website’s security is bullet-proof. Vulnerabilities such as SQL injection will always be present if the coding isn’t done properly.
The first scenario to compromise a hidden service would be to successfully exploit such a bad coded application. It is then possible to compromise the real server where the hidden service is stored, get information about its physical location or, more preferable, install a backdoor that could collect information of what’s going on the server for weeks.
There is absolutely no need to try to and look for vulnerabilities in Tor itself, it’s much easier to find a misconfiguration of services or flaws in the web application. People who control illegal Dark Net sites usually rely on Tor capabilities for security, but this will never save them from bugs in 3rd party applications or their own mistakes.
Another possible scenario is to infect the administrator of an illegal site with spyware, get full access to his computer and from there get all the required information about his true identity.
This could be easier than it seems: for example, if a vulnerability is found in a hidden service, it is possible to rig it’s admin page with an exploit and wait for when the drug shop administrator will access his site. Then he would be infected with malware as a result of this highly targeted waterhole attack.
Another way is to infiltrate the illegal service posing as a regular customer, by creating an account and even buying something in there, to create reputation. When the time comes to do some communication with the hidden service’s support account (about the quality of the product, for instance), they can start using social engineering or even send a spearfishing message rigged with an exploit.
There are a lot of ways to compromise a hidden service, without attacking Tor’s architecture itself. Of course, the possibility of having a serious security vulnerability in Tor itself should not be completely excluded either.
Law enforcement agencies in Tor: impact over the Dark Web





















georgepugh
Hot stuff