
Introduction
The geopolitical conflicts in the Middle East have deepened in the last few years. Syria is no exception, with the crisis there taking many forms, and the cyberspace conflict is intensifying as sides try to tilt the struggle in their favor by exploiting cyber intelligence and using distortion.
The Global Research & Analysis Team (GReAT) at Kaspersky Lab has discovered new malware attacks in Syria, using some techniques to hide and operate malware, in addition to proficient social engineering tricks to deliver malware by tricking and tempting victims to open and launch malicious files. The malware files were found on activist sites and social networking forums, some other files were also reported by local organizations like CyberArabs and Technicians for Freedom.
The full report detailing the attacks and related activities can be found here.
A glance at what was discovered
The number of attacks and malicious files being distributed is constantly increasing as the attackers become more organized and proficient. The samples are all based on Remote Administration Trojan Tools (RATs)
The number of malicious files found: 110
The number of domains linked to the attacks: 20
The number of IP addresses linked to the attacks: 47
The National Security Program – what the malware attacks look like
Masquerading as a reportedly “Government leaked program” that has the names of all wanted people in Syria, the National Security Program conceals a full featured RAT client to steal all sorts of information under one of its buttons.
برنامج الأمن الوطني.exe (The national security program)
Using shockingly disturbing videos to distribute malware
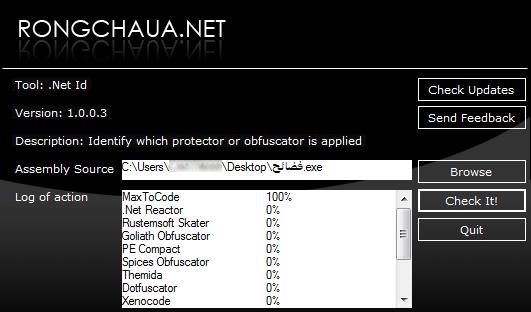
A disturbing video showing injured victims of recent bombings was used on YouTube to appeal to people’s fear and prompt them to download a malicious application available on a public file sharing website. After initial analysis, the file named “فضائح.exe” (Scandals.exe) proved to be heavily obfuscated with the commercial utility “MaxToCode” for .NET in order to avoid early detection by antivirus solutions.
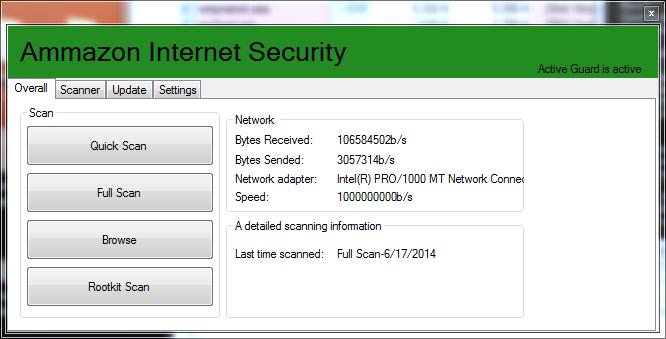
Did you install your “Ammazon” Security Suite?
If you thought the era of fake antiviruses was over, here comes this newly developed Syrian sample to challenge your beliefs. With the innocent title of “Ammazon Internet Security”, this malicious application tries to mimic a security scanner, even including a quite thorough graphical user interface and some interactive functionality.
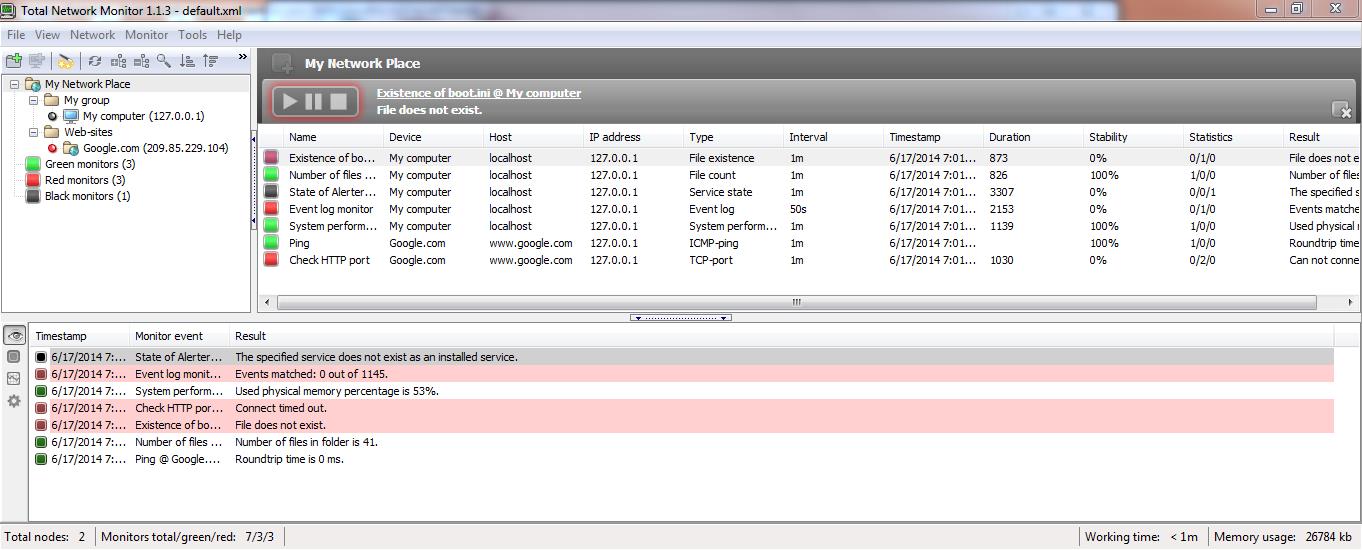
Your “Ammazon” is now secure, what about the rest of your network?
Total Network Monitor (which is a legitimate application) is inside another sample found, being used with embedded malware for spying purposes. Offering security applications to protect against surveillance is one of the many techniques used by malware writing groups to get users desperate for privacy to execute these dubious programs.
Instant messaging, instant infection
It’s also the case with other samples, where social engineering does all the heavy work. Instant messaging applications for desktop operating systems have been used in the past to spread malware and it seems Syrian malware authors have jumped on the bandwagon.
Beware of Chemical Attacks
Another of the attacks using social engineering tricks, the sample named Kimawi.exe (Arabic for Chemicals) with a JPG icon, is a RAT file bound to the image Kimawi.jpg. The picture is a previously leaked paper supposedly from the regime in Syria warning military units to prepare for Chemical Attacks. The file is being sent by email to selected victims.
FAQ
What is new?
The threat actors are becoming more organized, the number of attacks is increasing and the samples being used are becoming more sophisticated, while also relying extensively on powerful social engineering tricks that many people fall for.
Where are the victims and the attackers?
The victims infected when accessing the hacked forums and social networking sites tend to be ordinary users or activistshey were, or specific targets if they receive the malware via email, Skype, or messages on social networking sites.
The victims are also located outside Syria. We have seen victims of Syrian-based malware in:
- Turkey
- Saudi Arabia
- Lebanon
- Palestine
- United Arab Emirates
- Israel
- Morocco
- France
- United States
The attackers’ command and control centers were tracked to IP addresses in Syria, Russia, Lebanon, the US and Brazil.
How many have fallen victim?
We believe the number of victims exceeds 10,000, with some of the files being downloaded more than 2000 times.
The attackers’ malware samples and variations have increased dramatically from only a few in Q1 2013 to around 40 in Q2 2014.
What is the impact on victims?
Remote Administration Trojans tools are used to fully compromise the system on victim devices. RATs are capable of stealing user credentials in addition to activating camera and microphone functionalities…
Are users protected?
Kaspersky detects and blocks all the samples that have been found. They are detected as follows:
- Trojan.MSIL.Zapchast
- Backdoor.Win32.Bifrose
- Backdoor.Win32.Fynloski
- Backdoor.Win32.Xtreme
More details and analysis of the attacks and malware samples can be found in the full report here.
Further reading
If you’d like to read more on the subject, CitizenLab and EFF have published several other good analyses of related malware and attacks:
- The Internet is Back in Syria and So is Malware Targeting Syrian Activists
- A Call to Harm: New Malware Attacks Target the Syrian Opposition
- Syrian Activists Targeted with BlackShades Spy Software
- How to Find and Protect Yourself Against the Pro-Syrian-Government Malware on Your Computer
- Fake YouTube Site Targets Syrian Activists With Malware
- Quantum of Surveillance: Familiar Actors and Possible False Flags in Syrian Malware Campaigns
The Syrian Malware House of Cards






















mohandas mv
extreemly thankfull for the informations provided