
When we’re traveling we tend to bring lots of smart devices with us. It’s great to be able to share a beautiful photo, let people know where you are or put your latest news on Twitter or Facebook. It’s also a good way to find info about restaurants, hotels and transport connections. But to do all this you need an Internet connection.
Unfortunately, the cellphone data roaming plans are generally very expensive, so many travelers just go for free available Wi-Fi access points at the places they are, seeking them out and using them without any concern about security. However, this is a very risky approach because all the data you send or receive on open Wi-Fi networks could be intercepted. If this happens all your passwords, PINs and other sensitive data could fall šinto a cybercriminal’s hands. Indeed some cybercriminals install fake Access Points, specially configured to steer all traffic through a host which can control it, perhaps even functioning as a ‘man-in-the-middle’ machine that intercepts and reads encrypted traffic. There’s a serious danger of losing all your sensitive data, and with it all of your funds. When traveling far from home, this is a disaster waiting to happen.
Having this in mind, we looked into Wi-Fi access in Sao Paulo. We drove 100 km around the city and checked out more than 5,000 different access points. We focused on places that tourists visit – parks, malls, airports and other tourist attractions. So, how safe – or not – are Sao Paulo’s Wi-Fi networks? Let’s take a look.
Wi-Fi study in Sao Paulo
The study took place by the middle of May 2014. We found more than 5,000 different Access Points in the city and some of them are clearly not secured at all. First let’s look at the details so you can make up your own mind about safeguarding credentials and sensitive data in Brazil.
SSID
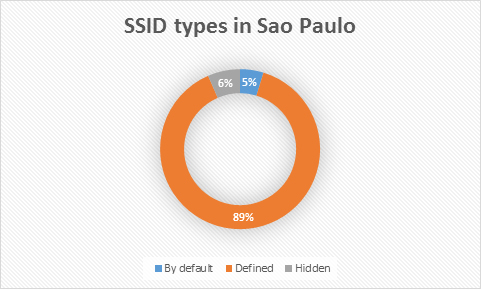
SSID is the name that a Wi-Fi network access point is assigned when you connect to it. Some Access Point’s owners leave it with the default configuration, others define a new customized name and only a few of them define a new specific name and then proceed to hide it, so it’s not broadcast to the public.
As you can see only 6% of all Wi-Fi access points are hidden. At the same time 5% of available wireless networks manage the SSID configuration by default, which means that attackers can easily figure out the origins of the network and find a proper vulnerability to get full administrator access to the access point. In general, it is bad practice to leave the SSID by default; it does not improve security but makes cybercriminal’s life easier. The best practice would be to define the SSID and then keep it hidden. Unfortunately few establishments anywhere in the world use this approach.
Wi-Fi network types
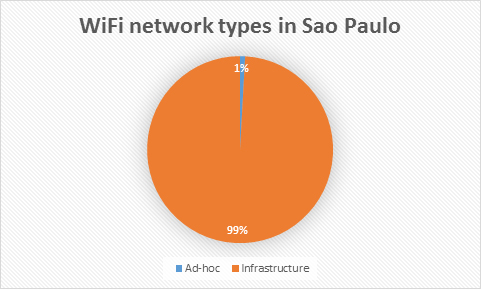
Most of the access points we found in Sao Paulo are managed, however 1% of networks are ad-hoc:
What does this mean? If you are connected to an ad-hoc network, everything you send and receive goes through a host or computer. This could be managed by anyone, with good or bad intentions. In other words, you data passes through hands of unknown individuals who may do nothing – or may collect it and extract sensitive data. If you don’t want to lose your data it’s better not to use such networks.
Wi-Fi security in Sao Paulo
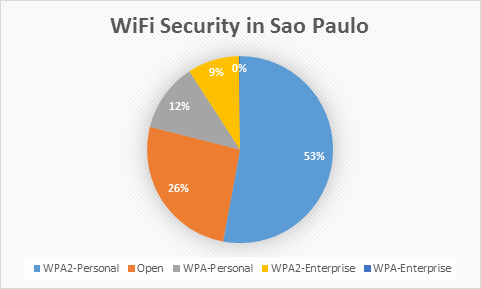
After analyzing more than 5000 different access points, we found that at least 53% of them have the WPA2 authentication, which is good. However the really worry comes from the fact that 26% of all networks are completely open and don’t use any encryption. These open networks usually offer free Internet access, so they are very popular among visitors. There’s a big risk when you connect to one of these networks. You data is transmitted in clear text, unless the server you are connecting to manages SSL encryption. If you say, “Right, I’m ok because all Websites I used to browse have SSL”, you may still be wrong. The issue is not all Websites have a full SSL encryption, I mean some Websites only use it for the authentication process when your credentials are transmitted to the server but all subsequent data goes in plain text. What does that mean? Let’s say you’re signing in to your Email. The server establishes a SSL connection and transmits your user name and the password securely. Once you are inside your email and start writing an email and send it, this goes as plain text. An attacker on the same Wi-Fi network could intercept it and read it as easily as you can on your own screen. So if you send an email that includes sensitive data – where you are staying, your passport number etc – all this information goes straight to the cybercriminal.
That’s not the only danger. An attacker using the same Wi-Fi network could launch a ‘man-in-the-middle’ attack. Suddenly, anyone using the network to login to email, social networks, online banking or other websites get a popup claiming the SSL certificate is out of date. Most people automatically accept the proposed new certificate, only to discover it is a malicious ploy to encrypt your traffic and decrypt it again before it reaches its intended destination server. Cybercriminals prefer to use open Wi-Fi networks, so please stay alert and don’t just click on any popup message. Read the warning messages and then decide. If you feel something is going wrong or the connection is not behaving normally, log off and look for somewhere else to get online.
A further security concern is related to WPA protected networks. You may think they are protected but in reality, the WPA is a weak implementation nowadays and can be broken in a few minutes by attackers. These networks should be also considered as potentially unsecured and it is better to avoid using them.
Wi-Fi vendors in Sao Paulo
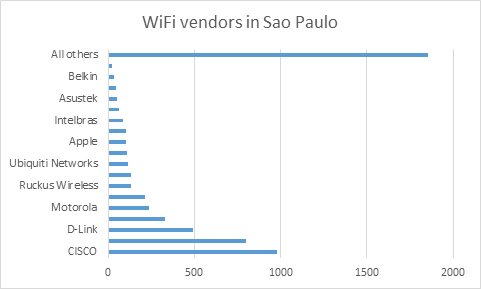
Our statistics show that the most popular vendors in Sao Paulo now are CISCO and then D-Link.
Most vendors manage Access Point security and especially the firmware upgrade processes as an on-demand user dependent action. That means even if there is a publicly known vulnerability that allows remote attackers to get full administration access to the device, it can’t be patched automatically, unless users go to the vendor site, download that patch and then proceed with the upgrade process by uploading the new firmware to their end-points via an Ethernet cable.
Most Wi-Fi users find this a complicated process; many don’t even know how to check if their device is vulnerable. So many access points remain unpatched and vulnerable to remote attackers. The attackers can get full access and then to change the ISP DNS setting to malicious ones. After that, anyone browsing from that particular access point will have their traffic routed through malicious DNS servers that redirect them to fake sites whenever they try to access banking or payment services. This is a scary and very nasty technique since even quiet experienced security users could easily lose their money. The phishing attack happens on the DNS layer when your end-point makes a name request, but the server you’re redirected to is a completely malicious one.
Recommendations
One of the golden rules when working on any Wi-Fi network is to always access it through a VPN connection! If you do not have any, please get one and install it on all your devices – smartphones, tablets, laptops, etc. Sometimes you may find Wi-Fi networks where you VPN is blocked. That’s something of a red flag. If possible, avoid using that network. If you have no choice it’s probably better to use the Internet via TOR Browser together with your own DNSCrypt settings right on your device.
If you own an Access Point, please check if your firmware is the latest one. If not, upgrade it. Don’t leave your Access Point with vendor default settings, change them and also define new strong passwords, so attackers couldn’t easily compromise them. Check the encryption your Access Point has now. If it’s WPA or WEP, change it to WPA2 with AES settings. Disable SSID broadcasting and make sure your network password is strong.
Remember that just one mistake may lead to the leak of sensitive data. Sacrifice time but not security. If there is no really secure network in your place, don’t worry about posting your pictures right away; wait until you find a secure place to work.
Fake AC/DC charging points
It is so sad when your battery is dying and the day has just started. It’s an even bigger problem when you’re away from home and need your smartphone to access maps, routes and all kinds of information to make your journey easier. In these circumstances people tend to use any available charger, even if only for a few minutes.
Modern smartphones and tablets demand a lot of energy. Sometimes, especially if the battery is not a new one, your devices discharge too fast. Of course, leaving the battery drained it is not an option.
That is why many travelers look to charge their devices at every opportunity. Even if it is a bus stop, a waiting room or any public place. However, they forget about a very important detail: nobody knows if the charger they plug into is a malicious one or not.
What exactly is a malicious AC/DC charger? It will still charge your battery, but at the same time it will silently steal information from your smartphone when recharging via a USB port. In some cases fake charges can also install malware capable of tracking your location even when you leave the area, of stealing your notes, your contacts, your pictures, your messages and call records, your saved passwords and even your browser’s cookies.
Recommendations
Never use unknown chargers but look for trusted places. Use your battery responsibly and try to keep a spare with you, so you can use it if the primary battery dies. In case of the iOS devices there are covers with an extra charging battery, which may also be a good solution.
Try to optimize battery life by shutting down unnecessary processes and entering flight safe mode when a cellphone network is not available. You can also disable sounds, vibrate tones and other resource-hungry features, like animated wallpapers etc.
You can follow me on twitter: @dimitribest
Wi-Fi security and fake ac/dc charges threaten your data at the 2014 World Cup






















Henry
Mr. Bestuzhev,
Thanks for your article. One suggestion I’d add is the recommendation for cell phone users to always carry at least one USB cable which is for charging only, that is, it only contains two wires connected to only two pins on each USB connector at the ends, so only DC can go through. If such cables aren’t ready-made, we have to customize a fully-populated (all pins wired) cable so that only the minimum two go through. (And have an extra as backup in case one fails.) That should foil potential snoops trying to enter via USB.