
Brands leaking your information open the door to effective spearphishing
A few months ago, I requested an online quote for some home repairs. The recipient was a very well-known company here in US. The service I got actually was very good. Under my explicit approval the company kept my email address and has been sending me several promotions that I had signed up to.
However, the latest one was unusual – it arrived with at least 20 recipients explicitly exposed including my full email address in the list.
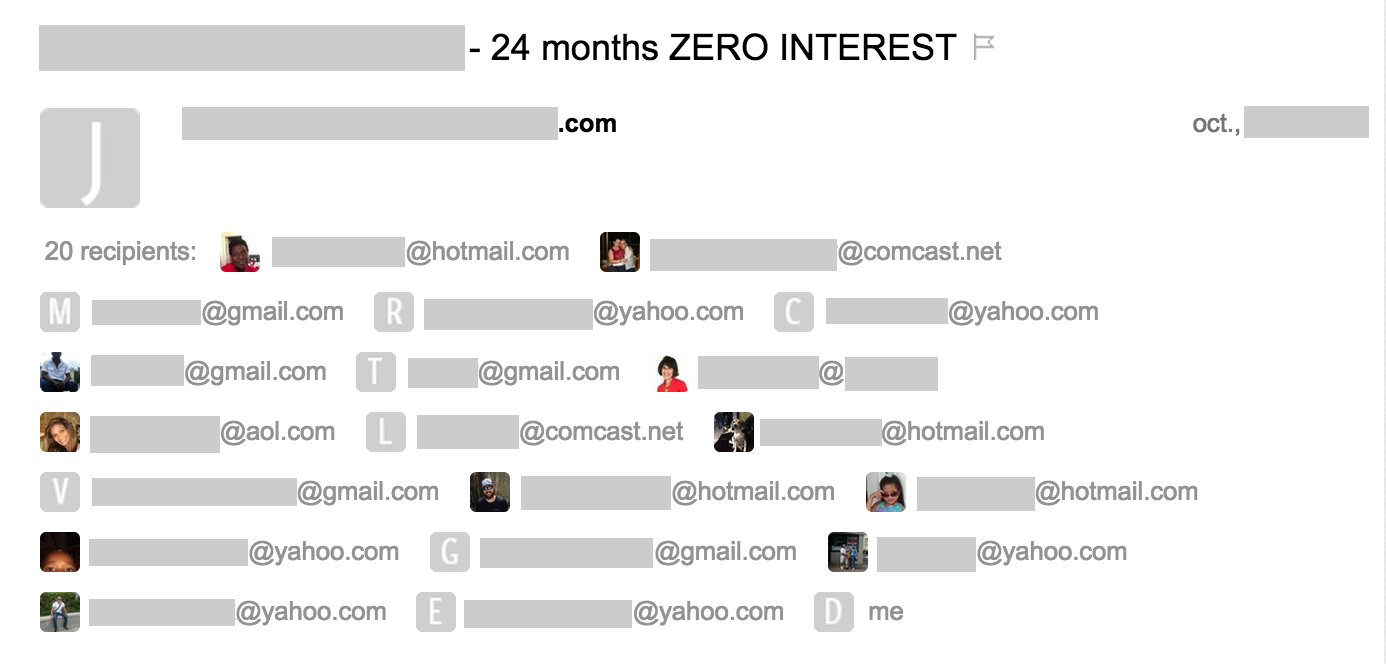
Cybercriminals and other threat actors also have normal lives – they shop at the same places we do, they eat the same food we eat, and they hire the same services we do. So, imagine what happens when a malicious actor receives one of these emails! It’s a perfect source of information for spearphishing attacks.
I say this because the attacker would have enough information to know the potential victims are customers or potential customers of that particular brand, knowing the benefits of abusing the brand to launch attacks in the name of that store.
Since the advertisement I get is customized, meaning it refers to a very specific part of town, then the attacker would also know his victims live in a particular city. This also brings a lot of advantages when preparing the attack.
Finally, the attacker even knows how the store legitimately promotes their services. And I mean which format the store uses:
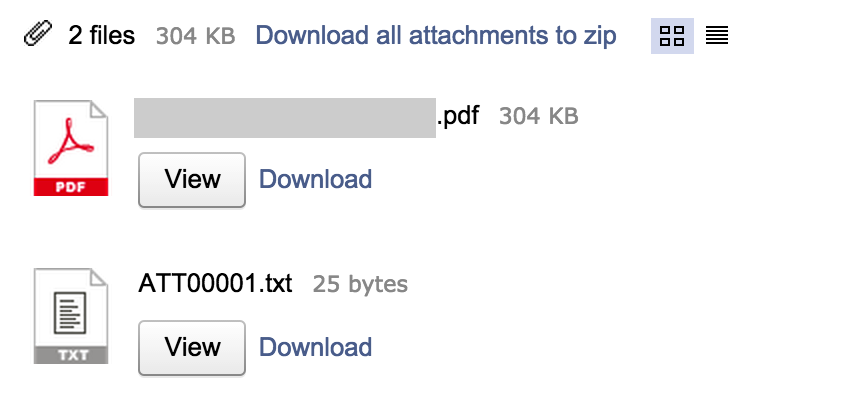
In my case, I got a PDF file attachment. So, in case the attacker launches a spear phishing campaign with a malicious file, the victims wouldn’t suspect anything malicious since nothing is out of the ordinary.
So who might abuse this technique and what can we do about it?
The most likely actor would be a classic cyber-criminal. However, any threat actor in need can resort to the same scheme.
What is the best practice when you get such advertisement emails? I prefer to use online viewers, embedded into many modern Webmail providers. Instead of downloading the file to the disk and then opening it locally, you can visualize it online:
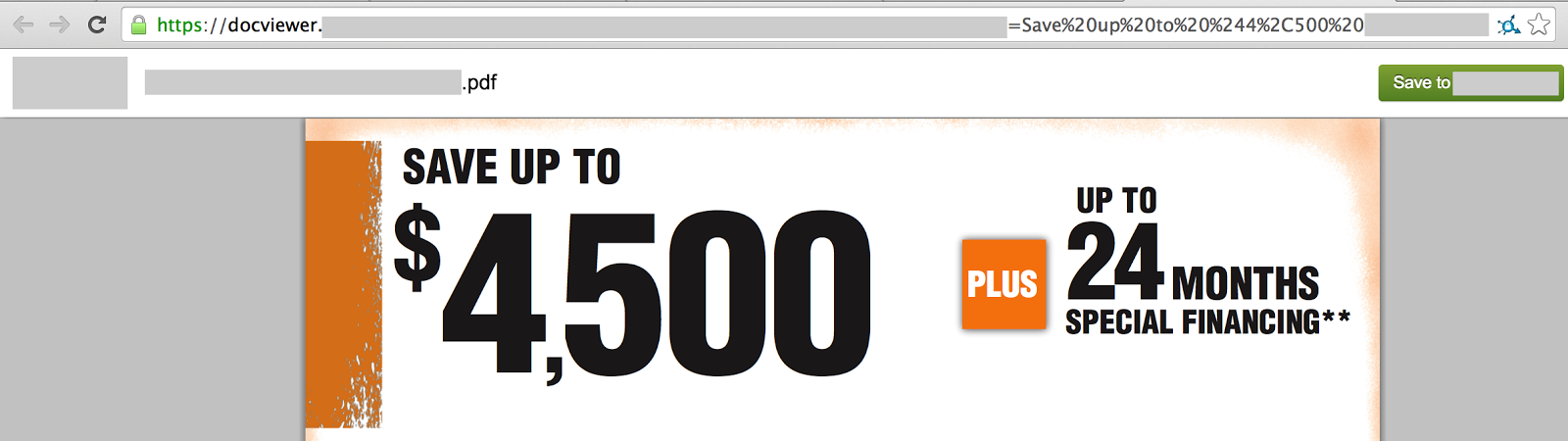
So in case of any local app exploit, let’s say for Adobe Reader, the exploit won’t work and you will still be able to read the document.
Certainly leaks like the aforementioned, despite not being particularly big, definitely expose people to become victims of new spear-phishing campaigns.
You may follow me on twitter: @dimitribest






















From the horse’s mouth