
AZORult has its history. However, a few days ago, we discovered what appears to be one of its most unusual campaigns: abusing the ProtonVPN service and dropping malware via fake ProtonVPN installers for Windows.
The campaign started at the end of November 2019 when the threat actor behind it registered a new domain under the name protonvpn[.]store. The Registrar used for this campaign is from Russia.
We have found that at least one of the infection vectors is through affiliation banners networks (Malvertising).
When the victim visits a counterfeit website and downloads a fake ProtonVPN installer for Windows, they receive a copy of the Azorult botnet implant.
The Website is an HTTrack copy of the original ProtonVPN website as shown below.
Once the victim runs the implant, it collects the infected machine’s environment information and reports it to the C2, located on the same accounts[.]protonvpn[.]store server.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
{ "config: ": [ "MachineID :", "EXE_PATH :", "Windows :", "Computer(Username) :", "Screen:", "Layouts:", "LocalTime:", "Zone:", "[Soft]", "Host: User-Agent: Accept: ; charset=Content-Type: HTTP/1.0POST text/*utf-8text/htmlHTTP/Proxy-AuthenticateAcceptContent-TypeContent-Lengthrealmhttp::Connection::connect: using proxy %1%http::Connection::connect: testing %1% for proxy routing" ] } |
In their greed, the threat actors have designed the malware to steal cryptocurrency from locally available wallets (Electrum, Bitcoin, Etherium, etc.), FTP logins and passwords from FileZilla, email credentials, information from locally installed browsers (including cookies), credentials for WinSCP, Pidgin messenger and others.
We have been able to identify a few samples associated with the campaign:
| Filename | MD5 hash |
| ProtonVPN_win_v1.10.0.exe | cc2477cf4d596a88b349257cba3ef356 |
| ProtonVPN_win_v1.11.0.exe | 573ff02981a5c70ae6b2594b45aa7caa |
| ProtonVPN_win_v1.11.0.exe | c961a3e3bd646ed0732e867310333978 |
| ProtonVPN_win_v1.11.0.exe | 2a98e06c3310309c58fb149a8dc7392c |
| ProtonVPN_win_v1.11.0.exe | f21c21c2fceac5118ebf088653275b4f |
| ProtonVPN_win_v1.11.0.exe | 0ae37532a7bbce03e7686eee49441c41 |
| Unknown | 974b6559a6b45067b465050e5002214b |
Kaspersky products detect this threat as HEUR:Trojan-PSW.Win32.Azorult.gen

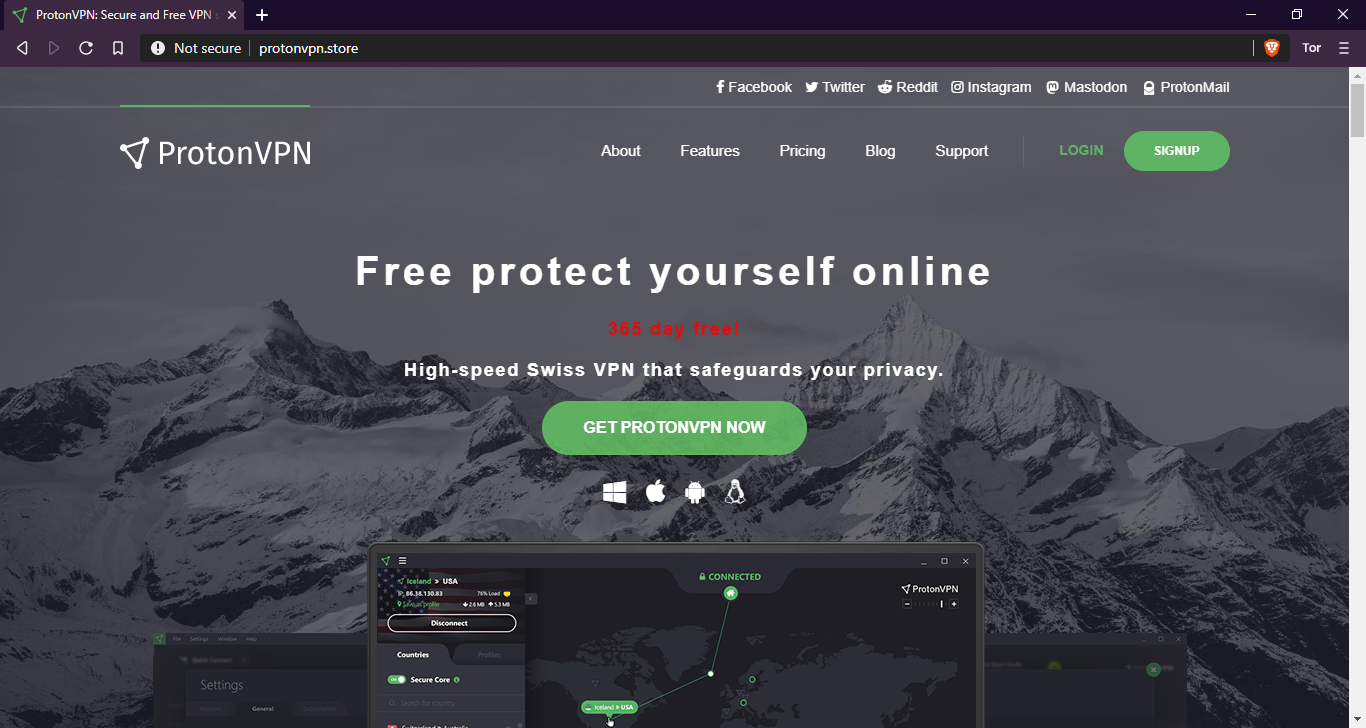

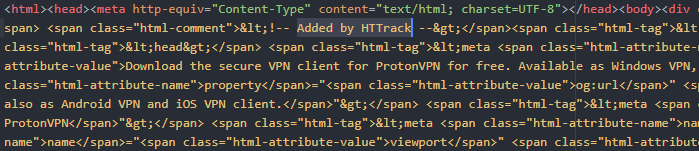
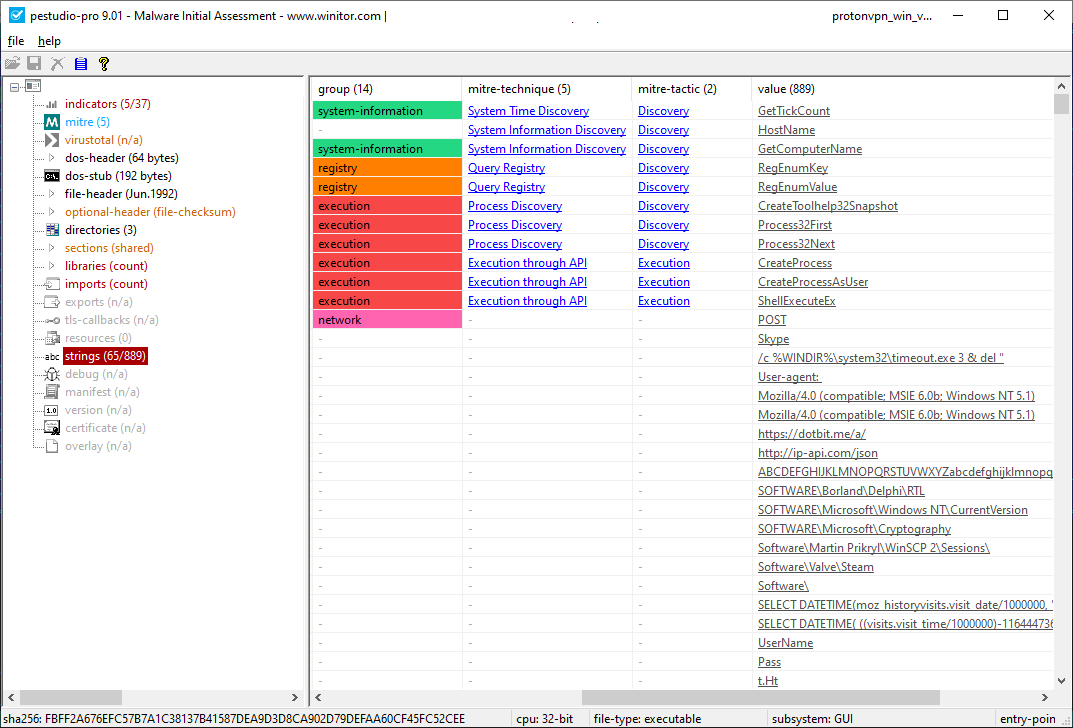






















AZORult spreads as a fake ProtonVPN installer