
A little while ago, Microsoft released an update which partially disables some autorun functionality on Windows operating systems prior to Windows 7. The update, known as KB971029, is intended for Windows XP, Vista, Server 2003, and Server 2008. The autorun function is used to automatically start installation processes from CDs, DVDs, and USB drives, as well as other types of removable media.
Autorun works by using a file named autorun.inf found in the root of the file system for removable drives. While this is a helpful process when used with a trusted resource, such as a software installer from a CD, it has long been a successful malware infection vector on rewritable drives.
At Kaspersky, we’ve frequently urged Microsoft to disable this process, as anything that automatically installs software or code without properly informing the user can and will be used maliciously. In the past we’ve discovered infected consumer devices, and the autorun function has been used to spread incredibly successful threats as Conficker (Kido). This listing gives you a partial idea of just how often “autorun” gets used as an infection vector.Early versions of Windows, including Windows XP Service Pack 1 and earlier, would automatically launch software on a rewritable drive with no notification. XP Service Pack 2 and later would automatically launch a window when the drive was inserted, and you could then choose to run an executable. In fact, you could check a box at the bottom to “Always do the selected action”. Malware creators often create an autorun.inf file on removable media when a malicious program launches, and this extends the attack vectors beyond network propagation. A shared USB drive becomes a threat to a network that may not even have Internet access.
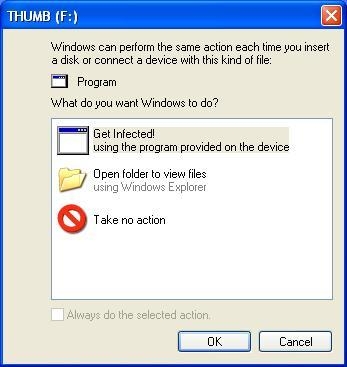
With Windows XP Service Pack 2, and in Vista and Server 2008, a new feature called Autoplay was introduced. The Autoplay function pops up a window when an autorun.inf file is detected and requests action from the user. The options are to install a program, which launches the intended executable, or to open the folder to view files. While this approach is better than automatically running an executable without user knowledge, it’s not exactly safe. Most casual computer users are conditioned to keep clicking until the file opens, so this just adds a step on the road to infection. The update mentioned above disables the autoplay function on writable media like USB drives, while leaving the autoplay function intact for CDs and DVDs.
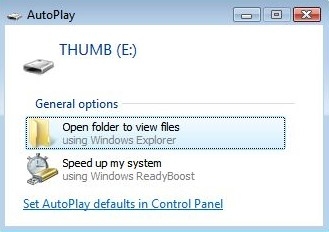
Windows 7 disables the function altogether on writable external drives by default. This is a much safer approach; although it makes it more difficult for the average person to find out what to do next when trying to install something new, there’s always a trade-off between security and usability. While we commend Microsoft for finally implementing this fix, it took far too long. Countless infections could have been avoided, and Conficker might have spread less widely if this simple fix had been pushed out earlier.




















Autorun no more