
Introduction
Corporate network security is one of the most pressing issues for companies today. Malicious programs can cause substantial harm to a business, and a firm’s reputation is not the least of its worries. Companies specializing in IT security offer a variety of costly solutions, although in many cases, installing these solutions can actually lead to a steep increase in network maintenance costs. However, traditional security solutions cannot always provide guaranteed protection against unknown threats — especially when it comes to targeted attacks.
This article addresses an alternative approach to protecting corporate networks: the Allowlist Security Approach.
This approach continues the developments in launch control technologies (otherwise known as Application Control) which add Default Deny mode support and innovative new allowlisting technologies, or Dynamic Allowlist.
At Kaspersky Lab, we believe the Allowlist Security Approach is one of the key elements of protection for corporate networks of the future. Products that use this approach are capable not only of protecting a network against unknown threats but also offer network sysadmins and IT security engineers progressive means of accounting and managing software, including unwanted and unlicensed outside (i.e., non-work-related) programs.
What you need to know before searching for alternative security approaches
The amount of new software grows steadily each year. In order to provide users with quality protection, antivirus companies must quickly analyze the enormous inflow of information and process terabytes of data on a daily basis, classifying tens of millions of files. In terms of classification, software can basically be divided into three main categories: known malware, known to be safe, and status unknown.
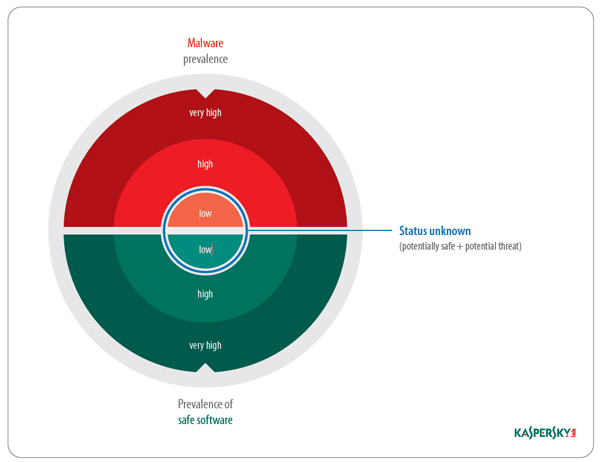
Software that is not clearly classified as safe or a threat by an antivirus company is placed in the “status unknown” category.
Some unknown software contains malicious code, and these types of programs are the most dangerous for users, as well as the most challenging for antivirus products to detect. It is these programs that post the greatest threat, since virus writers continue to hone their skills as more and more new malicious programs are produced.
In most cases, antivirus companies must remain on the frontlines of this ongoing battle: each time virus writers develop a new malicious technology, antivirus companies respond by developing a new form of protection against it. As well as traditional signature-based technologies antivirus companies currently employ an entire arsenal of modern security technologies to boost security. These include proactive heuristic methods (both statistics-based and dynamic) and cloud technologies which respond instantly to new threats and also expand standard out-of-the-box security capabilities that were previously unavailable within the online service infrastructure.
The traditional approach to security involves blocking known threats, including known malicious behavior templates. However, the stories behind the Stuxnet, Duqu, and Flame Trojans all show that the traditional means of protection available on the market is more or less powerless against some new threats and targeted attacks. As a result, corporate network security faces ever-growing demands.
Given today’s situation, software developers working in IT security are faced with the task of finding alternative solutions capable of substantially boosting the security of corporate networks. The alternative approach addressed in this article – Allowlist Security — not only meets today’s security needs, it also allows antivirus companies to focus on more than just fighting off new malicious technologies.
The Allowlist Security Approach is based on a combination of our knowledge of the principles of development and proliferation of corporate threats, as well as a strong understanding of our customer’s business needs and which forms of protection are needed to provide a reliable, balanced solution. The solution addressed below is different in that it is simple to integrate and manage, in addition to having a relatively low total cost of ownership (TCO) while providing a high level of data security.
Implementing this approach not only required a thorough rethink of the decade-old “pursuit paradigm” but has also laid the groundwork for a fundamentally new stage in the development of application control technologies.
The components of modern security products
Reliable data security requires a comprehensive approach. Modern means of protection are comprised of several components, each of which performs specific tasks.
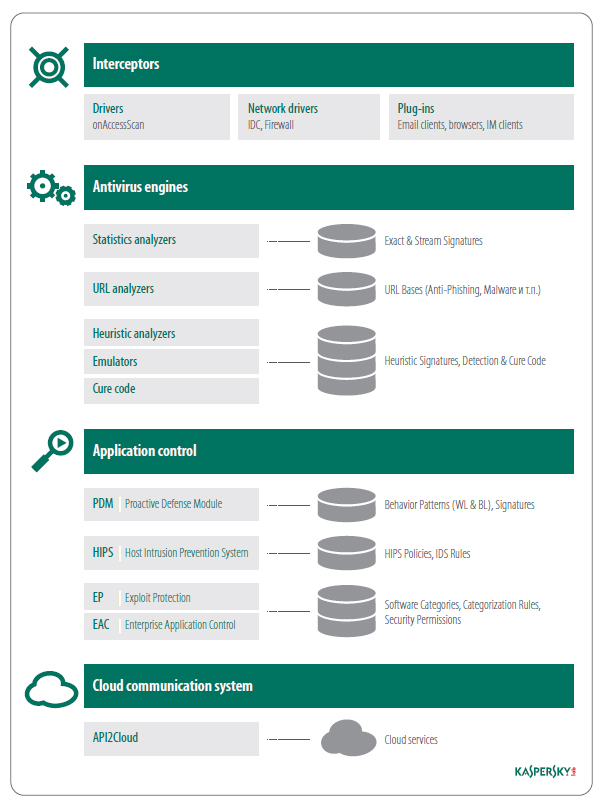
A components-based model of modern data security
In this model, we can see four main groups of components: interceptors, antivirus engines, application controls, and cloud services.
Let us take a look at the functions of each component.
Interceptors act like sensors to help antivirus products plug into a running operating system process, so that other antivirus protection components are able to scan objects and events as necessary.
The following serve as interceptors:
- Driver – intercepts requests made by applications for files. When a file request is intercepted, an antivirus product can scan the file for malicious code, or verify the permissions of this operation in line with the host-based intrusion prevention system (HIPS). If an application’s actions lead to the detection of malicious code or unauthorized access, a driver can either block the file request, or prevent the application from launching.
- Network driver – helps maintain control over application operations within a network (preventing data leakages within a network, blocking network attacks, and so on).
- Plug-ins – libraries (modules) that can be added on to common applications (email clients, browsers, IM clients, etc.), and scan transferred data.
Engines are product modules designed to scan potentially malicious objects. There can be several scanning methods in one engine, and each antivirus developer may have their own list of and names for the methods they use.
The main types of engines are:
- Statistics analyzers that work to detect malicious objects according to certain statistics (more often than not, this is related to the structure of files in a particular format).
- URL analyzers that check to see whether or not a web address that a user is going to or that has been sent by email is in a malware, phishing, or other specific category of database (such as, for example, parental controls).
- Heuristic analyzers – a technology that makes it possible to use just one signature to detect numerous malicious files, including previously unknown modifications of malicious software. At the same time, it also boosts the quality of detection and reduces the volume of antivirus databases.
- Emulators – modules that execute program code in an isolated environment for subsequent behavior analysis.
In most antivirus products today, one data security component is a bundle of technologies that are part of the Application Control component. The latter works by using events from the interceptors, and then processing those events with help from other components:
- Proactive defense module (PDM). The search for and detection of known malicious program behaviors (sequences, patterns) using malicious behavior pattern databases.
- Host-based intrusion prevention system (HIPS). HIPS scans each potentially threatening program action (most often atomic actions) against a list of rules which define whether or not those actions are permissible for a particular program. What’s more, these rules can be customized for different types of software. For example, “trusted” software can do “everything”, while “unknown and suspicious” programs may be prevented from executing certain actions.
- Exploit protection is meant to protect computers against malicious programs that exploit vulnerabilities in software and operating systems.
Currently, exploit protection is included in just a handful of antivirus products, but at Kaspersky Lab, we believe this type of protection is critical. Kaspersky Lab’s exploit protection module is called Automatic Exploit Prevention (AEP). It uses an analysis of exploit behavior and gives users extra control over applications that are more susceptible to malicious user attacks. AEP prevents exploits from launching. If an exploit does somehow launch, AEP blocks them from carrying out any malicious behaviors. - Enterprise Application Control (EAC). This module controls the launch of different categories and/or versions of software in line with different sets of rules and permissions.
Cloud services help expand the abilities of both engines and application controls. The cloud makes it possible to hide some of the scanning logic (in order to make it more difficult for malicious users to reverse-engineer the process and subsequently evade scanning). It also helps reduce the amount of signature and behavior template database updates for users and clients.
Application control as a key tool for securing corporate networks
The Application Control module described above allows users to regulate application activity using HIPS policies that are initially set by the developers of antivirus product. Applications reviewed within the Application Control context are divided into four categories: safe, threatening, strong restrictions, and low restrictions. These categories are used to define the level of restrictions that can be assigned to different applications (HIPS policies). Each category of applications is assigned a set of rules regulating application access to different resources (files, folders, registries, and network addresses). For example, if an application requests access to a specific resource, Application Control will check to see if that application has access rights to that resource, and will then act in line with the assigned rules.
Application Control also logs application launch records. This data can be used when investigating incidents and conducting various scans. An IT security professional or system administrator with this functionality at hand can promptly receive answers to the following questions in a standardized format:
- Which applications were launched and when over a specified period of time?
- On which computers and under which accounts did an application launch?
- How long has any given program been used?
These are the component functions (capabilities and ease of use) that determine how effectively a system administrator can put into place and maintain various security policies.
The balance between freedom of action and security
When selecting a data security model, it’s very important to achieve a reasonable balance between freedom of action and security.
Home users value the ability to install and use any software without limitations. Although the risk of infection is then higher than with a strict set of restrictions, a home user stores only his own personal information and can make his own decision about the risks of his data being disclosed or leaked.
In contrast, corporate users handle information that is not their own. The more stringent the control, the lower the data security risks: the leakage or loss of data that is critical to a business could lead to a standstill in a company’s business processes and, as a result, financial and reputation damages.
For companies, the balance between security and user freedom means a balance between potential risk and the level of convenience for corporate users. Smaller companies tend to prioritize user convenience and, as a result, they minimize restrictions for them. Meanwhile, larger corporate networks make security a top priority. Large companies use centralized security policies — standard rules for using corporate data resources. The ease of use is seen as less important than standardized software and maximum process transparency for sysadmins.
Typically, using a certain set of programs is sufficient for the needs of company employees. The ability to restrict software use to just those applications specified in rules set by an administrator and to block the remaining unwanted programs (unauthorized, illegitimate, or non-essential software) is a critically important option for corporate networks, not to mention command centers, industrial facilities, financial organizations, military agencies, and special purpose machines (such as ATMs and other types of terminals).
Maximum user convenience is offered in Default Allow, while Default Deny mode provides maximum security.
The traditional approach to protection: Default Allow
With Default Allow, the traditional choice for personal and corporate products, users can launch any applications except those that are blocked or those for which limitations have been put into place. This approach focuses on maximum user convenience.
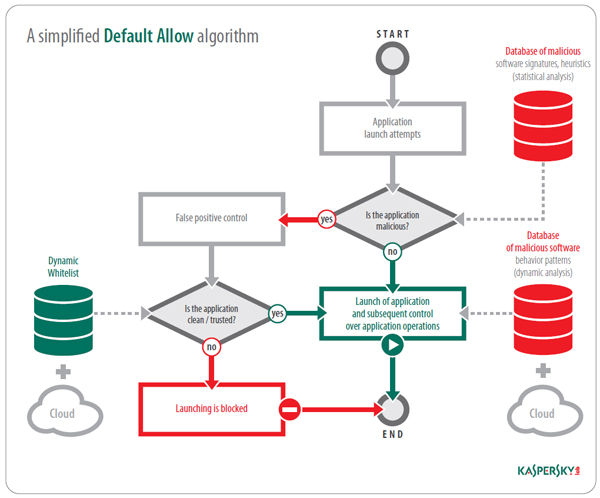
Clearly, the ability to launch any application will require high quality detection technologies. In the Default Allow mode, all of the security components noted above play a role in the analysis of the executed programs. This helps detect both known and unknown threats. At the same time, detection quality will depend on the developer of the antivirus solution being used.
However, as noted above, antivirus companies more often than not are working to counteract virus writers; in other words, there is always some kind of malicious program that has not yet been detected by antivirus security. Furthermore, with the Default Allow mode, if a program is not on the denylist, then its launch and execution will be, by default, permitted. That means that Default Allow mode presumes a certain degree of risk: code that is allowed to launch could pose an as-of-yet unidentified threat.
In addition to malicious programs, there are also legitimate programs that qualify as unwanted for certain networks. This type of program will not fall within the blocking policy, because in Default Allow if there is no special policy to block a program, the program will be able to launch on the corporate network without any restrictions.
Let us take a look at two examples of how a program that is not affected by security policies can lead to problems for a company.
An employee might install an instant messaging client on his computer — Skype, for example. One of the distinguishing characteristics of Skype is the encryption of data transferred via communication channels. That means that the DLP (data loss prevention) system is not capable of tracking the transfer of confidential information beyond the boundaries of a secured perimeter or identifying that information for the recipient. Antivirus technologies do not block the use of this application, as it is not a malicious program. However, a malicious user conspiring with a company employee could potentially gain confidential information from that employee using Skype as a means of data transfer.
Here is another example: Kaspersky Lab experts assisted in an investigation of an incident that took place at one company. No malicious programs were detected, but the reason behind the incident involved an IT staff member who had installed a legitimate remote administration utility on several workstations. The staff member had been fired over a year ago, but no one knew about the utility, which was still running and allowed the fired employee unauthorized access to the entire corporate network and all of the data stored on it.
As a result, the maximum user convenience offered by the Default Allow mode leaves corporate networks vulnerable to unknown threats and unwanted software. Moreover, control over all executables requires considerable resources.
However, in most cases, in order to perform their tasks, company employees really only need a restricted, specific set of programs. That means that a simple solution is the most logical one: only necessary, clean software should be put on a allowlist, and the launch of all other programs can then be denied by default. That application control mode is called Default Deny.
Default Deny mode
In contrast to Default Allow mode, Default Deny blocks the execution of any software that has not been pre-approved, i.e., on a allowlist. As a result, no unknown or unwanted software is permitted to launch.
Basically, when in Default Deny mode, a corporate network operates in an isolated software environment permitting only the launch of programs that are essential and sufficient for the company’s business needs.
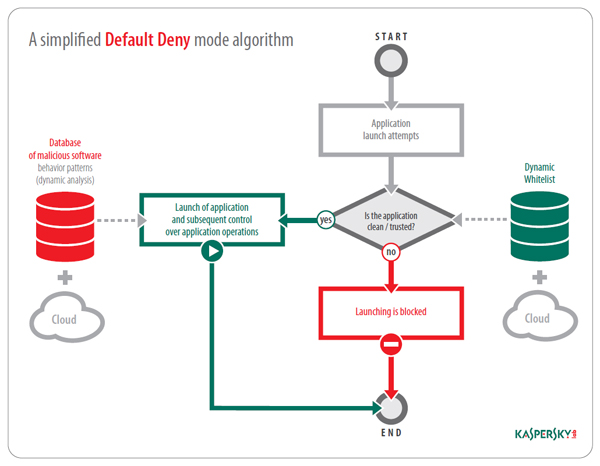
In addition, Default Deny also blocks the launch of malicious, non-essential, unlicensed, and unknown software, which reduces the costs of analyzing these types of programs, and which the Default Allow mode would permit. When working in Default Deny mode, performance requirements for the systems under sysadmin control and for the resources required for analysis are substantially lower. As a result, the security system has an overall lower impact on network performance.
As can be seen in the graphic, unlike the traditional security model, Default Deny mode application control is carried out when permitted programs are launched, rather than during the execution process. Thus, data security risks are minimized at the earliest possible stages.
The main advantages of Default Deny:
- The risk of malicious and unwanted software launching is minimized:
- Unknown applications are blocked, including new modifications of malicious programs and those used in targeted attacks. As a result, a secure environment is maintained.
- The ability to block the installation, launch, and execution of illegitimate / unlicensed and non-essential software, such as a variety of chat clients, games, software versions with known vulnerabilities, and system “performance enhancers”. As a result, employees are able to stay more focused on their jobs and their performance improves.
- Application analysis requires far fewer resources. As a result, the security system has a much lower impact on network performance.
- Last but not least: Default Deny mode also pushes down costs, and essentially lowers the overall total cost of ownership of a security system: there are fewer bugs, fewer complaints, and a more manageable workload for TechSupport staff.
As a result, using this alternative approach with its powerful application control, a company can substantially boost the level of corporate network data security while considerably lowering costs for security system maintenance. As we mentioned above, this is a fundamentally different and more proactive method which, in the opinion of Kaspersky Lab experts, could change the traditional perception of corporate network security.
The authors would like to thank Vladislav Martynenko for his contribution to the section ‘The components of modern security products’.

















Application Control: the key to a secure network. Part 1